
In 2006, everything that revolved around my world shattered into tiny pieces as I learned that scientists had decided to rescind Pluto's planetary status. Given the ol' Jeff Probst treatment, Pluto was officially voted off our solar system in the blink of an eye, leaving us with only eight planets and a whole load of useless textbooks. The primary reason that Pluto was demoted down to a "dwarf planet" was due to Pluto's largest moon, Charon, being about half the size of Pluto; all the other p...
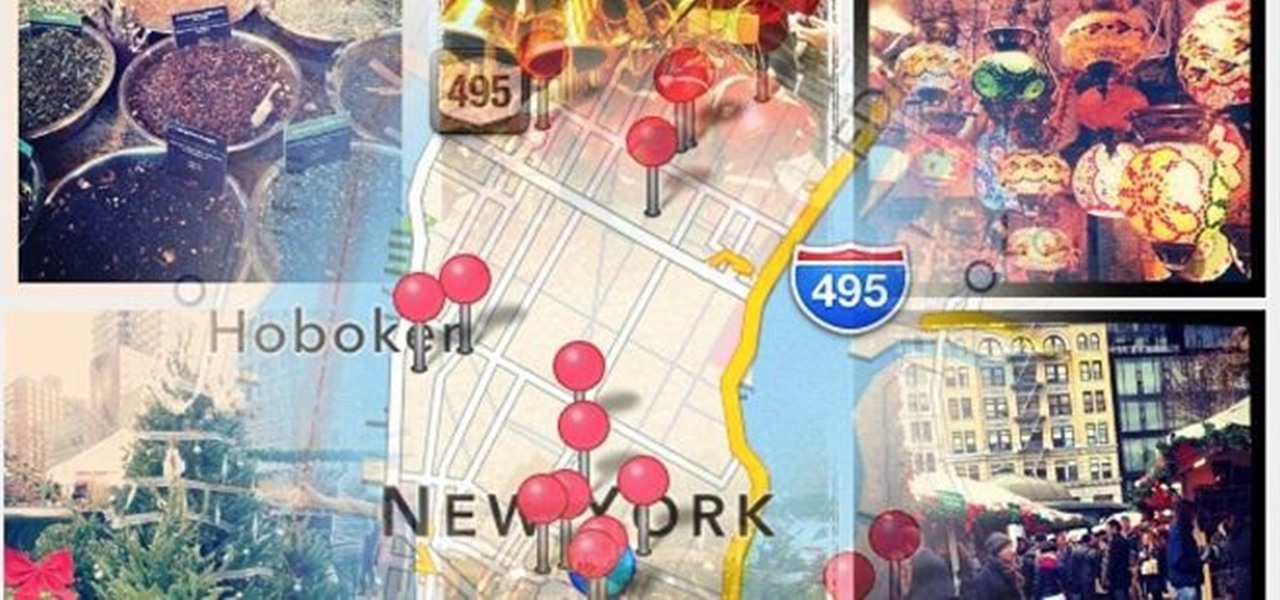
The only thing worse than not having any plans is not even knowing where to begin making them. Sure, you can check Yelp or one of countless other review sites to find a great spot, but there's no way of knowing what the vibe is like before you get there. Is it crowded? Are people having fun, or does it look pretty lame?
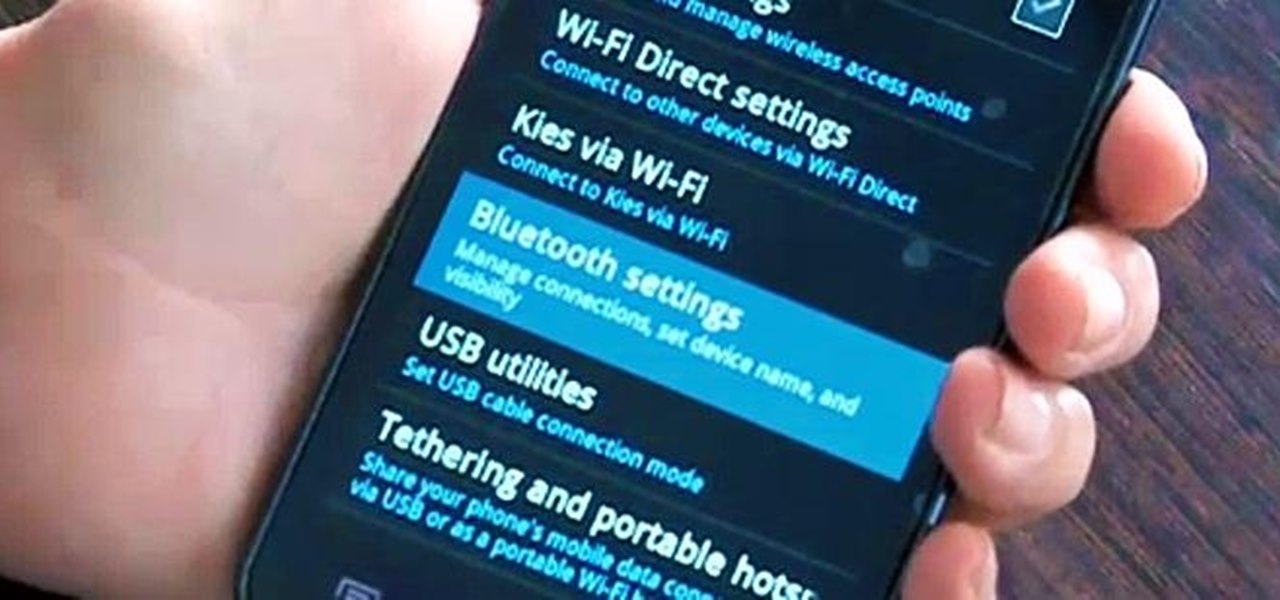
Google Now is an extremely intelligent personal assistant that automatically updates and prepares the most pertinent information for you on your Android device. Traffic updates, alternatives routes, weather conditions, and other important data is constantly being monitored and updated for you.

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

You can take some really awesome photos of water droplets if you've got a fast enough camera (and flash), but water drops aren't just spectacular as photographic subjects—you can also make them a part of the photographic process by using a water drop as a DIY projection microscope and even a macro lens for your iPhone. But as useful as a water drop can be, it's still way cooler when they're in front of the camera (as the subject). Recently, researchers from the National Autonomous University ...

Michael Faraday was awesome. He discovered electromagnetic induction, diamagnetism and electrolysis, and he invented the Bunsen burner (before it was the Bunsen burner). Because of his work, we can make suits that can withstand 1,000,000 volts of electricity and cases to protect our gadgets from nuclear attacks.

Wall Anchors. Drywall Wall Anchors. Plasterboard Wall Anchors. I discovered these plasterboard (drywall) anchors / plugs a few years ago and think they are fantastic. They are ridiculously easy to use and are extremely effective in attaching fixtures to walls. One of the main things to be aware of (as with all things that have fixtures hanging from them) is the recommended maximum weight loading of each size of anchor. What ever the packet says, adhere to it.

A spectrometer is a device that splits light into all of the different colors it's composed of that can't be seen with the naked eye. It does this by using a prism to refract or bend the light. Jeffrey Warren over at Public Labs created a tutorial showing how you can make your own video spectrometer and create spectra like the one pictured below. Any guesses as to what the subject is? Believe it or not, that's what whipped cream looks like when viewed through a spectrometer. You can do this w...

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

If you go to a lot of concerts and shows, you know that it can be easy to spend more on drinks than you spent on the ticket for the event itself. With this "vodka stash water bottle" you'll never have to pay for alcohol at a show again—assuming you like clear liquor, that is.

Helping to prove that science is way awesome, an 18-year old electrical engineering student has successfully made a light bulb float. His name is Chris Rieger, and he's been working on his "LevLight" project for about six months now, with pretty amazing results. This feat of ingenuity was accomplished by using magnetic levitation, although that over-simplification masks how considerably difficult this undertaking was.

If you're ever lost in a survival situation, here's a little trick you're going to be so glad to know. Normally, we'd think of using water to put OUT a fire, but in this video I show you how I use water to START THEM.

These videos will take you through the fifth episode in Alan Wake on the Xbox 360. You're almost to the point of discovering where Alan's missing wife is. Is she in Bright Falls or is she dead? Before you can find out, you have to defeat Episode 5 - The Clicker. Watch the gameplay on Nightmare Difficulty.

In the Xbox 360 game Darksiders, you'll eventually have to play the Iron Canopy level, which consists of The Seesaw, Webbed Floor, Two Lifts 1 Bomb, Loom Wardens, Broodmother, Silitha and Return Silitha's Heart. War will be ambushed and captured as he enters the Iron Canopy. When he comes to, you'll find him hanging from a spider web. Tap the Action button to break free. Make your way around to the left to discover a Soul Chest in hidden nook behind your starting location. Now cross the webbe...

There's nothing more maddening than opening the office fridge and discovering your lunch is gone. Put an end to the stealing with some of these strategies. This video will show you how to deter coworkers from stealing your lunch.

In this how to video, host Meghan Carter discovers the essential facts about outdoor ceiling fan that you need to know before buying one for you home.

Meghan Carter visits Chef Jason Hill to discover the secret to creating beautiful and delicious edible centerpieces. Jason, host of the YouTube Channel Chef Tips, shared the essential elements for an attractive green and purple grape centerpiece as well as how to make something your guests will want to eat. You can also try creating the olive tower.

Marble countertops look beautiful in any style kitchen or bathroom. To help you make the most of your money, host Meghan Carter visits Vermont Marble Museum to discover how to select the right marble countertops for you and how to protect them for staining.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

This video is about how to get rid of pimples. It's a nightmare to wake up and discover a big, red pimple right on your face. Here are some tips to help you out. 1. Do not touch, or try to squeeze or pop the pimple. This can cause pain, redness, swelling, and even infection. If you keep doing it another possible problem that can develop is scarring which can be permanent. 2. Wash your face gently with a mild, medicated soap and water (the water should be warm, but not too hot). Do this for 30...

Learn how to start seeds for planting. Start your own seeds to save money, grow different plant varieties, and extend your growing season.

Sound Like a Duck or a Fog Horn! All sounds are created by vibrations. You can discover this next time you're out at a fancy restaurant. All you need is that straw in your soda and a pair of scissors. Makes sure you flatten it out really good to make this work, then make sure you parent tip your server well.

Not sure how to size your golf club? Thanks to expert golf site Golf Link, here's your chance for a free lesson. The most critical part of a golf club's size is the shaft, and it's necessary for a person to find out about the flex point and torque of a club's shaft. Discover why golfers with higher handicaps will want a flex point that will kick the ball in the air more in this video.

There are many swings and hits you will learn once you begin to play golf. In this video, learn how to hit a ball flush. In order to hit a golf ball flush, the most important part of a swing is timing. Discover how to swing at a golf ball in the correct sequence in this helpful clip.









































