The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.
This Sony Vegas 7 tutorial talks up about many topics such as: -Explorer

Cory Norlund, a person living with HIV, and his mother Diana Norlund discuss how their family dealt with the news that Cory was HIV positive. He and his mother now make individual or joint presentations about HIV/AIDS under the auspices of the not-for-profit organization He Intends Victory.
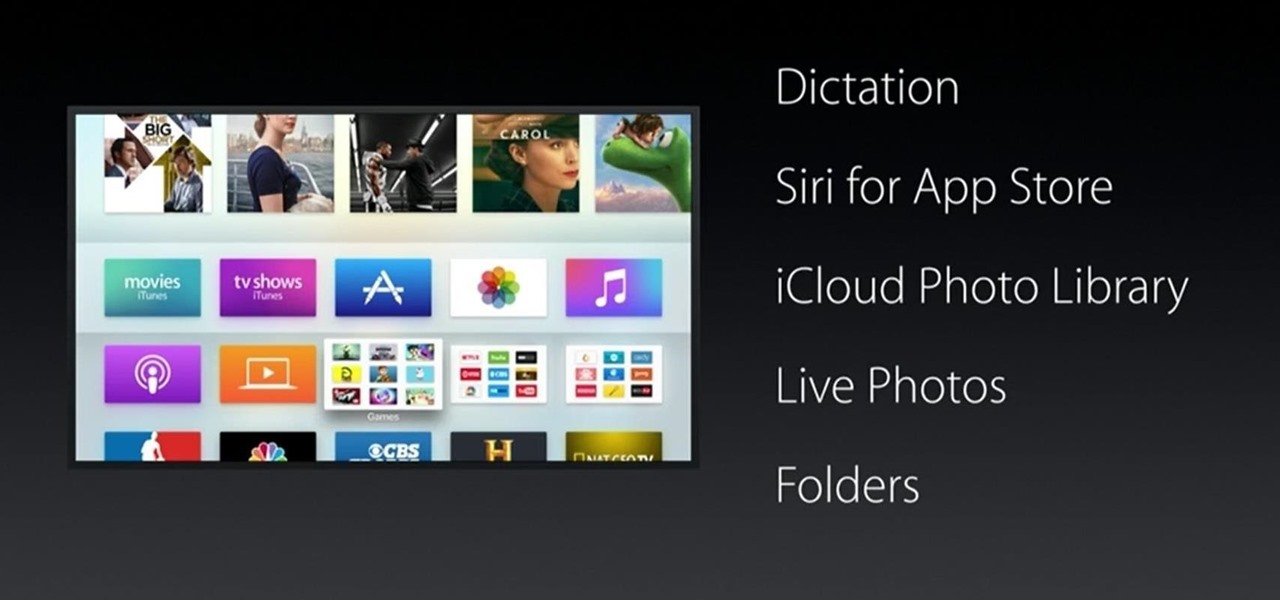
Apple will release tvOS 9.2 for the latest Apple TV today, bringing some major features to the streaming device. The software update, announced at today's Apple event, comes with Siri voice dictation, full iCloud photo viewing, and support for Bluetooth keyboards. Since Apple has already been beta-testing tvOS 9.2 for months, it's ready for a public rollout.

The internet is a great place to find information for pretty much anything you can think of. So why shouldn't it be a place for official higher learning? I'm not talking about a course in Wikipedia or SparkNotes, but real colleges offering real college courses completely online. And guess what—it's FREE.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

In recent years, Google's Arts & Culture project has been leading the way in terms of innovating the practice of using technology to preserve landmarks and great works of art via digital 3D copies. Increasingly, these efforts are also giving history buffs the chance to experience classic works and spaces with unparalleled intimacy through the wonders of augmented reality.

Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket item this year.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Next to things like natural disasters and disease, the specter of war is one of the only things that threatens to derail the 21st century's long stretch of technological innovation. Now a new app is using augmented reality to remind us of that by focusing on those most impacted by war — children.

In March, we wrote about the growing threat of yellow fever in Brazil. At the time, the disease had killed just over a 100 people. Unfortunately, the disease has only spread since then with many more people infected and more killed.

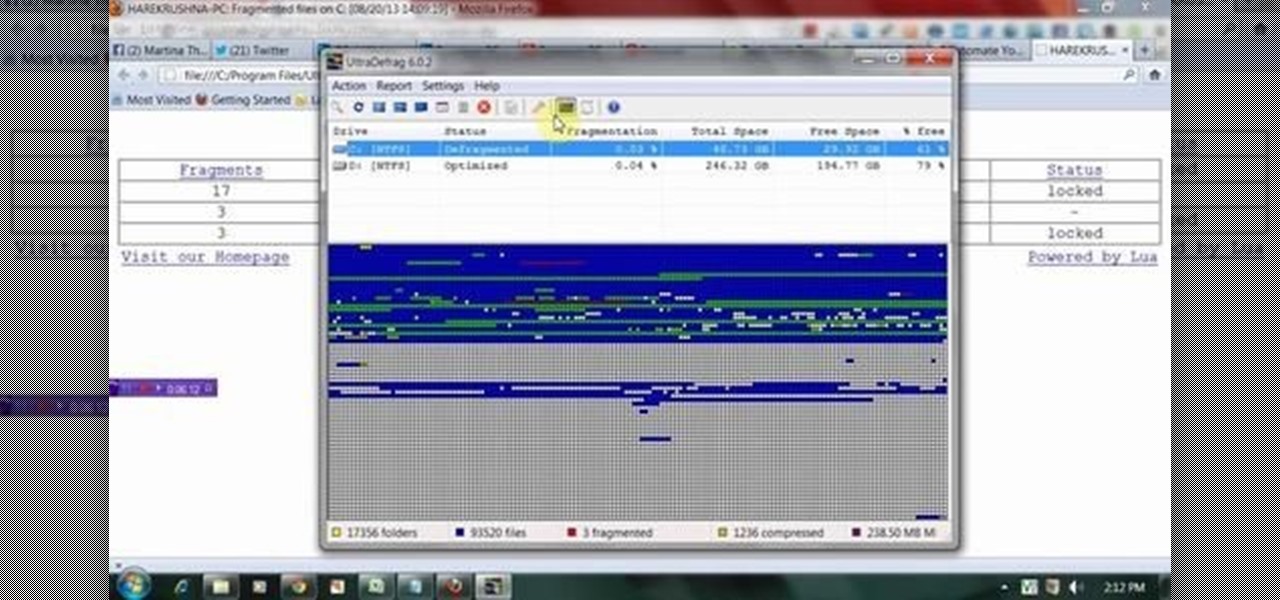
This Tutorial video will show you how to automate hard drive organization or defragmentation with ultradefrag software. UltraDefrag, PC utility software defrags your pc and speed up PC performance. So please watch the video and follow the steps to do it yourself.

Firstly, I'd like to say that I have nothing against iPhoto; it's a great application that works wonderfully in Mac OS X. Unfortunately, when you no longer have iPhoto on your MacBook—and you don't want to pay for it—looking for an alternative is a necessary endeavor. I could sit here and try to explain to you how I updated to Lion and then inexplicably dragged the iPhoto application into the trash—and proceeded to empty said trash. I could tell you guys that story, but I fear you might judge...

Wish you could flip in order to spice up that cheer you've been working on? Learn how to do both a front and back hand spring in this video tutorial.

Mastering your pike will add flare to any cheer. Learn how to do cheerleading pike jumps in this video tutorial.

Changing your leg position can create a beautiful variation to an already existing cheer. Learn some cheerleading leg variations in this video tutorial.

Knowing how to properly set up your mounts for cheerleading will help you execute your stunts safer and better. Learn how to do some stunt mounts in this video tutorial.

One of the most important things to do before practicing your cheerleading is to stretch properly. Learn some simple tips on stretching in this video tutorial.

Using stunts will ensure your cheers are visible to the crowd. Learn some shoulder height cheerleading stunts in this video tutorial.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

It's easy to find yourself drowning in a pile of papers and nick-nacks if you're not armed with a good organization system. By taking the time to set up a system where everything is condensed and has a place you'll find it much easier to keep it that way.

You have a purebred, make it official. With a few simple forms your purebred dog can be a member of the American Kennel Club and carry on the traditions of and gain access to this exclusive organization. Your dog can have an official pedigree.

Wedding insurance, vacation packages, travel discounts – the American Automobile Association offers its members more than free towing.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...

There are many hacks for increasing productivity, but so many depend on tricking your own mind or behavior. When it comes to motivation in the workplace, though, sometimes the space within which you work dictates how you behave and the work you produce. So if you want to increase your ability to get more done in a single workday while doing a better job, consider changing your surroundings in the following ways.

Keeping your computer organized and your desktop clutter-free can be pretty difficult. And with last week's official release of Windows 8, users have another screen they need to get used to organizing—the new Metro-style Start Screen. It uses large rectangular or square tiles in place of the standard icons you've seen on older Windows operating systems. For better organization and grouping, you can group similar items onto a page (similar to many smartphones), you increase or decrease the siz...
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

For years, Apple's Notes app has been a reliable way to jot down important ideas, tasks, plans, and more. While there are apps on the market that advertise themselves as being more feature-filled than the stock iOS option, Apple is now giving them a run for their money. Here are 14 new features and changes you'll see with Notes in iOS 13.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.