Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.
Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

If you've ever played the game of Would You Rather, you've probably been given the ultimatum between eating insects or doing something else that sounds absurd, like licking a cactus. I'm advising you to always choose the insects, and here's why:

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

These days, there are Android apps for every budget—forgive me if that sounds like a car commercial, but that's just the way things are in the age of the smartphone and tablet. You've got apps that require monthly subscriptions, paid apps that will run you a $30 one-time installation fee, and even games that start at 99 cents, but quickly skyrocket in price with in-app purchases.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

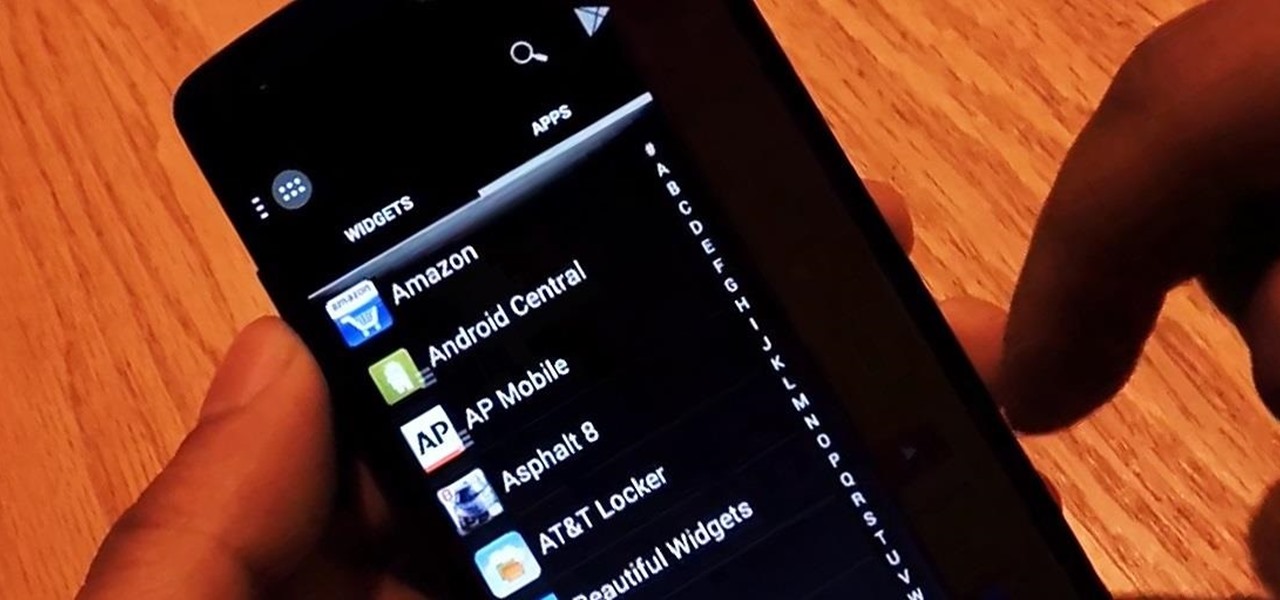
One thing almost every Android launcher has in common, from stocks to skins, is the way they handle organizing and launching apps and widgets. Tap an app icon to open the app. Drag apps together to create a folder. It's simple, it works, and it's what we know.

Attention all veterans and active-duty military personnel—this coming Tuesday, November 11th, is Veterans Day, that time of year where the whole country thanks us for our service. For the most part, a simple thanks will do, but some folks like to go above and beyond and give us veterans free or discounted meals and discounts on merchandise in stores.

Instagram is addicting — and that's done on purpose. To stop your Instagram habits, your smartphone likely has a built-in feature to curb the daily usage of a particular app, like Apple's Screen Time for iOS and Google's Digital Wellbeing for Android. But you don't need to mess with those complicated settings when Instagram itself can help you get some of your life back.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Nintendo may be developing cases that'll turn your iPhone into a gaming device like the Game Boy, but until something materializes there, you're stuck with cheap knockoffs on Amazon or a real Game Boy or Game Boy Color. But there's something else you can do to play eight-bit Nintendo games on your iPhone right now.

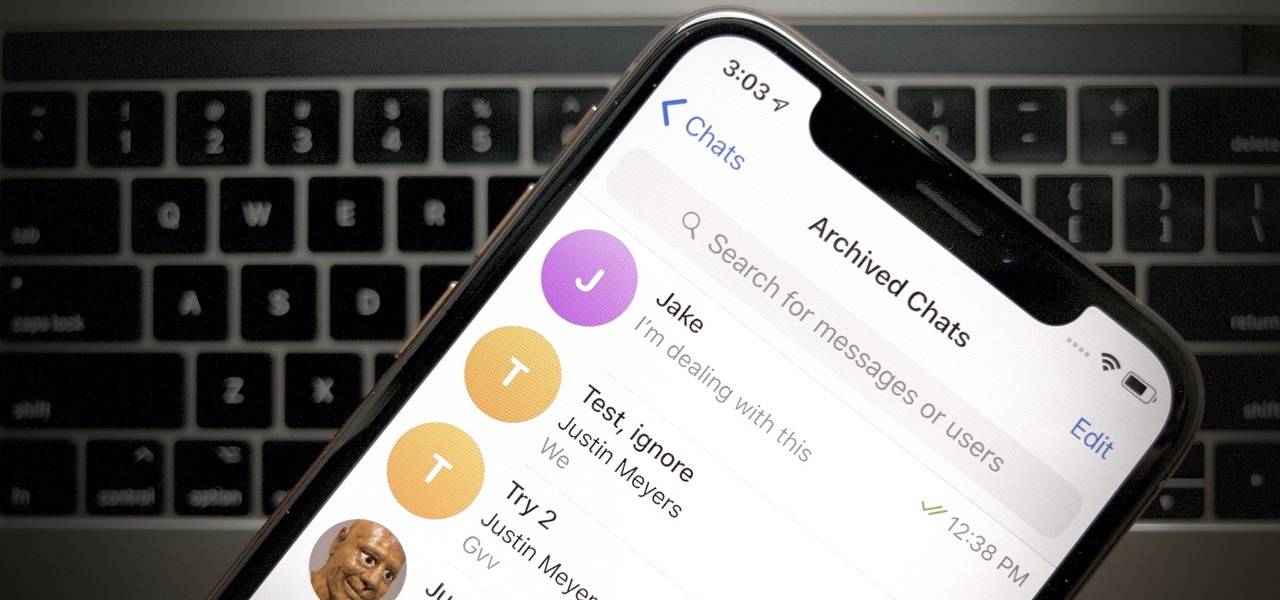
In Telegram — as with all instant-messaging apps — threads and conversations can pile up quickly. But you don't need to stare at all of your open chats on the main screen of the Android and iOS app. Instead, you can archive any conversation you like, keeping your main chats view relevant to your day-to-day communications without needing to delete any for good.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Mobile World Congress is a four-day event that is both a showcase and conference starring prominent figures in the mobile industry. Oftentimes, OEMs will use this event to announce new products for the upcoming year — and this year shouldn't be any different. Here are all the phones we expect to be announced.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Nova Launcher is one of the most popular apps on the Play Store thanks to its rich features and fluid navigation. But one downside that comes with this abundance of features is that much of Nova's functionality is lost on the masses. Fortunately, I've used Nova for several years and learned a few tricks along the way.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Dinner is meant to be enjoyed after a long day away from home—it shouldn't cause stress or fuss. But for many, that's exactly what a home-cooked meal represents, especially on a work night. The prep work, the steps involved in following the recipe, the numerous amount of bowls, pots, and pans you use, and... worst of all, a sink full of dishes to clean.

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?