When a stuffy nose hits, it feels like breathing clearly and easily may never come again. Allergies, colds, and even changes in weather can leave our sinuses blocked, with medicine seeming like the only option. But don't break out the medication just yet — relieving the pressure of a stuffy nose, a stuffy head, and stuffy ears can be as easy as touching a pressure point.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Only a handful of food products are impervious to spoilage—dried rice, salt, sugar—but even among those, honey is unique in that it remains edible without any preparation necessary. It's like this: if you came across honey in an Egyptian tomb, as archaeologists have, you could taste it and never guess it was thousands of years old.

There are a lot of people out there who don't like vegetables, but I would contend that that's because they haven't eaten any really good vegetables. I thought I hated tomatoes (okay, technically a fruit, but used mostly as a vegetable) until I ate some fresh from a garden. One bite of a juicy, ripe heirloom tomato made me realize that I love tomatoes—it's those bland, mealy supermarket tomatoes that I hate.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

We've all been there; waking up in the morning with a stiff, achy back. Maybe you overdid the yard work this weekend. Perhaps you were a bit too enthusiastic on the Nautilus circuit. Could be the long hours spent hunched over your computer are catching up with you. Perhaps your back pain is indicative of something more serious. Unfortunately, unless you've really injured your spine, your doctor isn't going to be much help; the best he can do is offer you pain medications and tell you to rest ...

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

In Minecraft, a large aspect of the game is PVP (Player vs. Player Combat). A hardcore Minecraft fan will remember that back in Beta 1.8, combat was switched up, and it really changed the game around. Here are some tips on what a two-year Minecraft player has to say.

Video: . Optimize your Marketing with a Mobile Website

When it comes to the future of AR smartglasses, DigiLens has one word for you. Just one word. Are you listening? Plastics.

One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again.

Continuity connects all of your Apple devices so that they all work seamlessly together. For instance, you can start tasks on one device and finish them on another, view and send text messages or make calls on your iPhone from your iPad, iPod touch, or Mac, and even use an iPad as a monitor for your Mac. Its Universal Clipboard feature is also really useful, but it can also be quite annoying in iOS 14.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.

Back when I worked in the music industry, I never imagined there would be a day that I'd be able to sit in a room surrounded by virtual album covers while listening to beats, but that day is really here.

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.

Magic Leap has done a great job of aggressively releasing new apps, software updates, and major franchise tie-ins. But aside from all the creative and entertainment apps, what's it like to use one of the apps the company hopes you'll use every day?

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

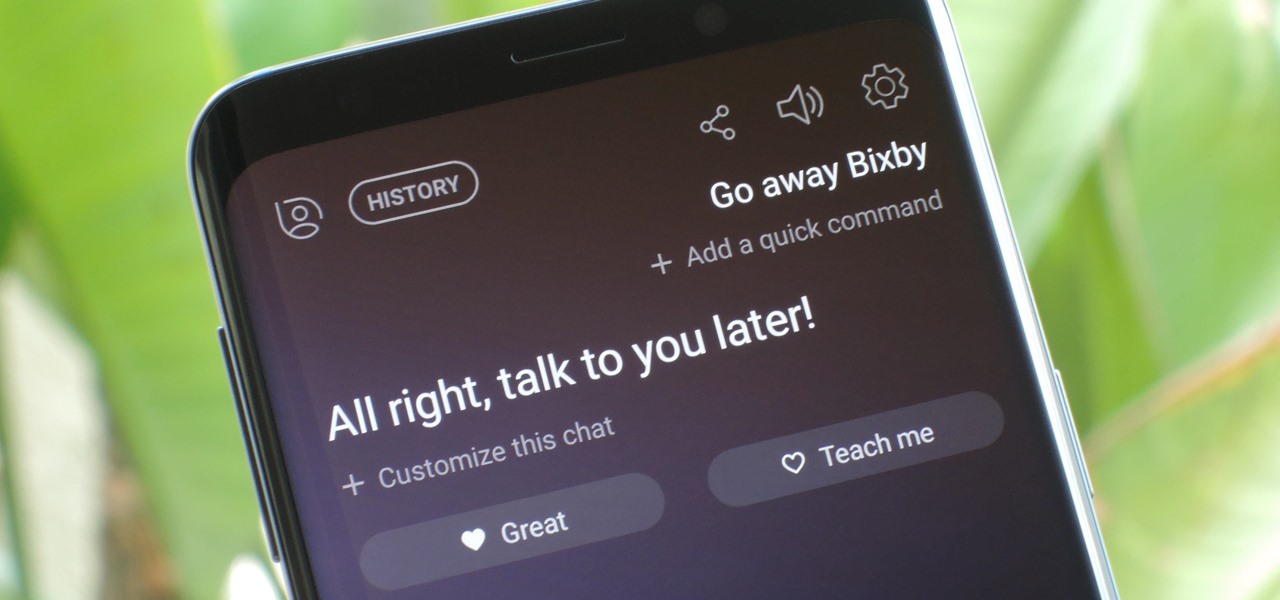
Sorry Samsung. I know you really wanted Bixby to be the next Siri, Google Assistant, or Alexa — but it just isn't. Burying the option to disable the app won't change that. Sure, Bixby has some redeeming qualities, but there are many of us who don't want it shoved down our throats. We'll show you how to disable the app to prevent it from launching every time you try to access just about anything.

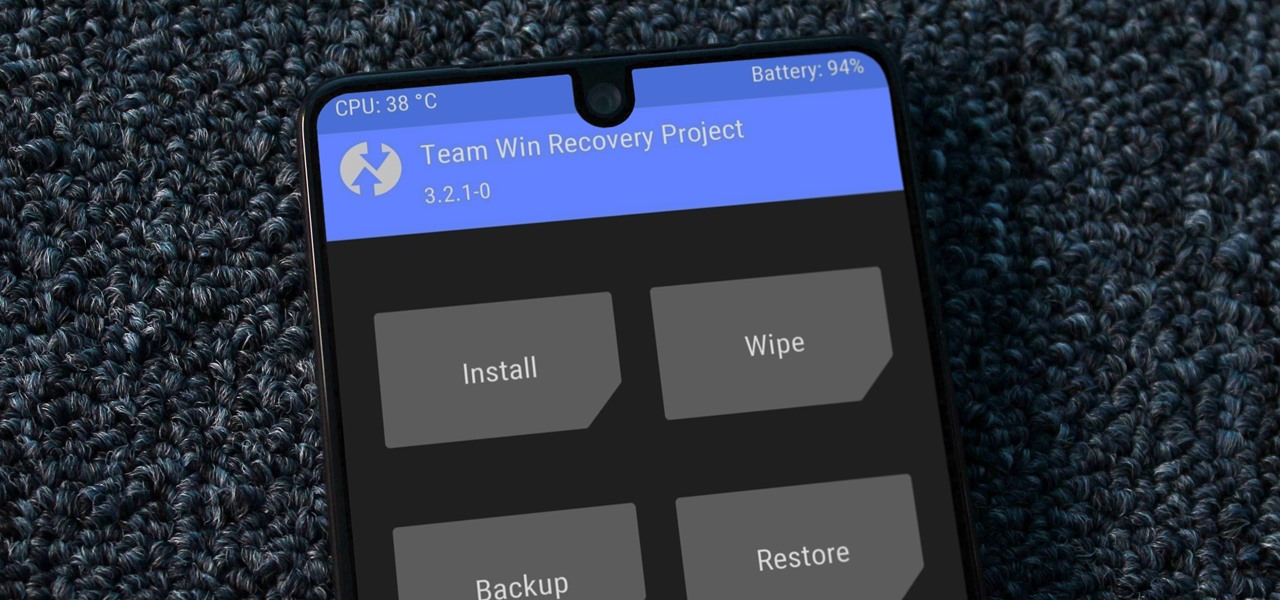
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

UPDATE: The P20 and its variants are officially available now. However, there's no official North American variant. You can purchase the international version of the P20 Pro or P20 Lite on Amazon, but be aware that it may not work perfectly on US carriers.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

The LG V30 has solid battery life. With its QHD P-OLED screen and 4 GB RAM, it's able to maintain all-day performance with average use. Heavier users might find that its 3,300 mAh battery isn't quite enough for a full day of work, though, but with a few software tweaks, you can squeeze out even more battery life.

The LG V30 is an amazing device that will contend for best smartphone of 2017. It has all the major features you'd expect from a high-end flagship, and it even includes what's become a rare commodity these days — a headphone jack. However, for the purists out there, the LG UX skin strays too far away from stock Android. Have no fear, for with the LG V30, you can have your cake and eat it, too.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.