The worst part of moving into a new place is, well...moving. It's tedious, a lot of hard labor, and it can take forever, and don't even get me started on all those labels. It's also one of the only times in your life when everything you own can be stolen at once, since it's sitting in a movable container. Rather than risk losing everything, try this DIY Moving Truck Alarm System by Tim Flint that lets you know when the loading door is opened so you can catch would-be thieves red handed.

Android has a new security feature that every Android smartphone user needs to start using — even you. It won't change how you use your phone, but it will make life harder for nearby thieves.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

Welcome back, my rookie hackers!

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Most of the free apps you'll find on the Play Store have ads. These ads are personalized — in other words, they're for products and services Google believes you might be interested in. The way Google knows about your interests is by collecting data from your smartphone, including your location and app usage. While personalized ads have their advantages, the collection of data is unsettling.

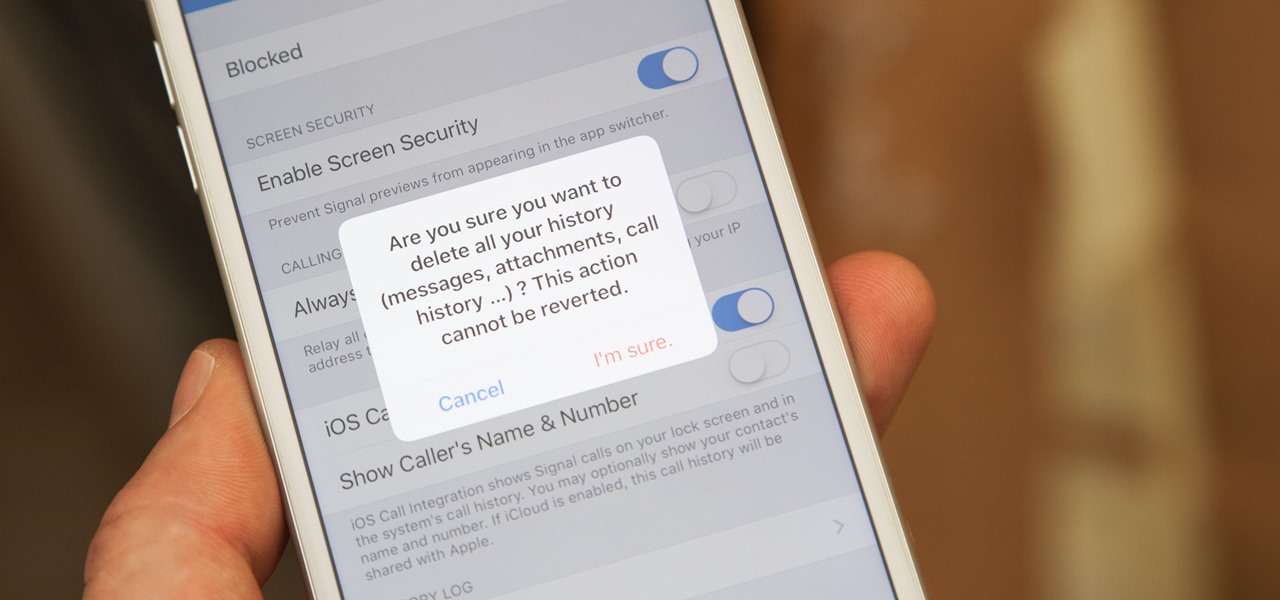
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

My least favorite aspect of the winter season is how my fingers always turn into stiff, numb digits, unfeeling and seemingly incapable of making even the slightest movement. Yes, that might sound overdramatic, but if you hate wearing gloves like I do, you probably know exactly what I mean.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

It's that time of year again. The month after we exchange gifts, most of us tend to exchange germs. Cold and flu season always seems to creep up on us, often leaving us ill-prepared to deal with the ailments.

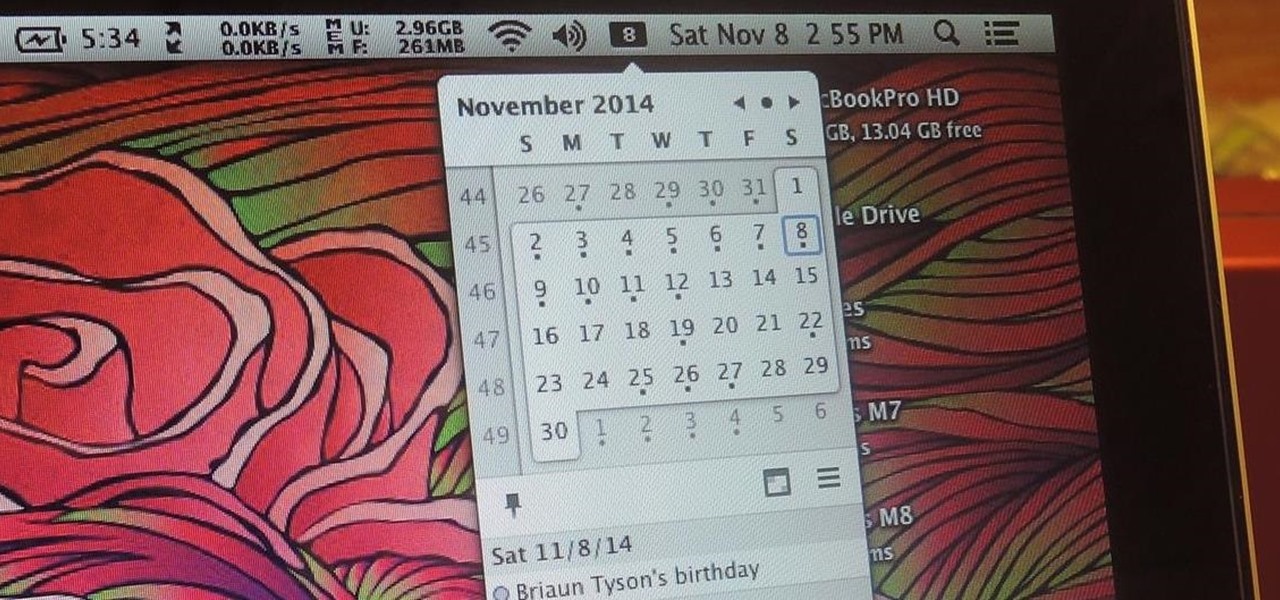
While it's much quicker in Yosemite, the Calendar app for Mac has never been as fast as I'd like. If my schedule is really full, it can sometimes hang when first opening the Calendar.

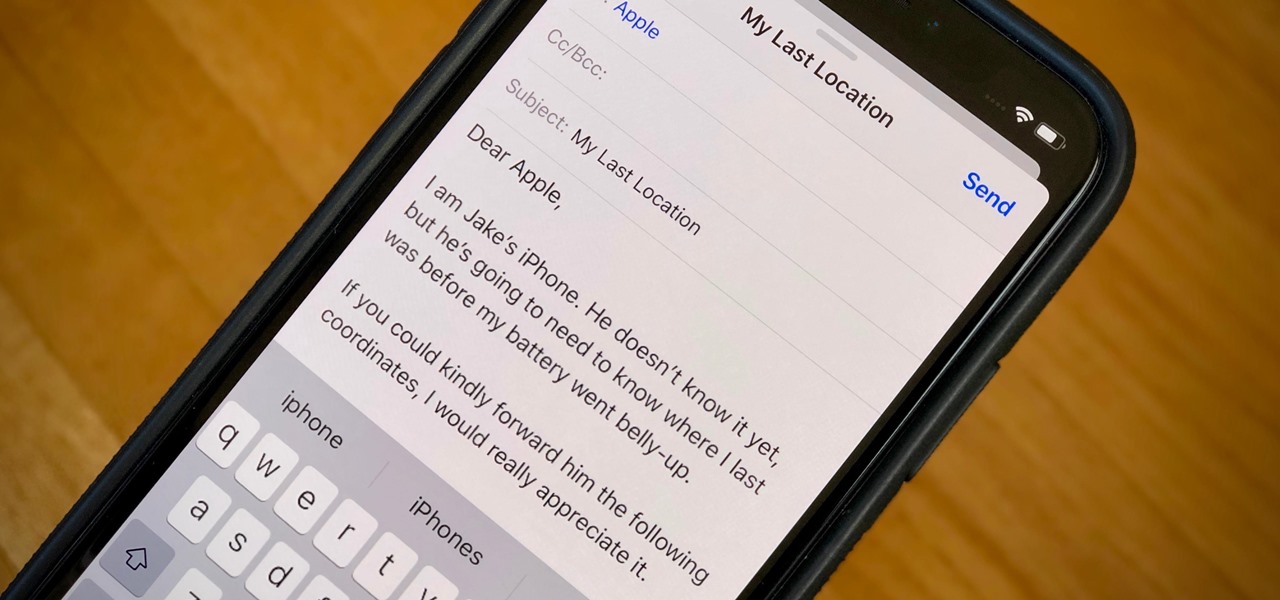
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.

Reddit user craigyboy2601 knows a thing or two about airline baggage handlers. After all, he is one. So, when he offers some tips on how to protect your luggage from loss or damage, you should probably pay attention! Here are the highlights from his post.

Doorbells are a great idea. They let you know when someone who's not a burglar is trying to enter your house, apartment, or squat. They eliminate the need for lots of noisy yelling and startling door pounding.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down.

Learn how to use a site: http://www.copyscape.com to check if people are stealing content from your website.

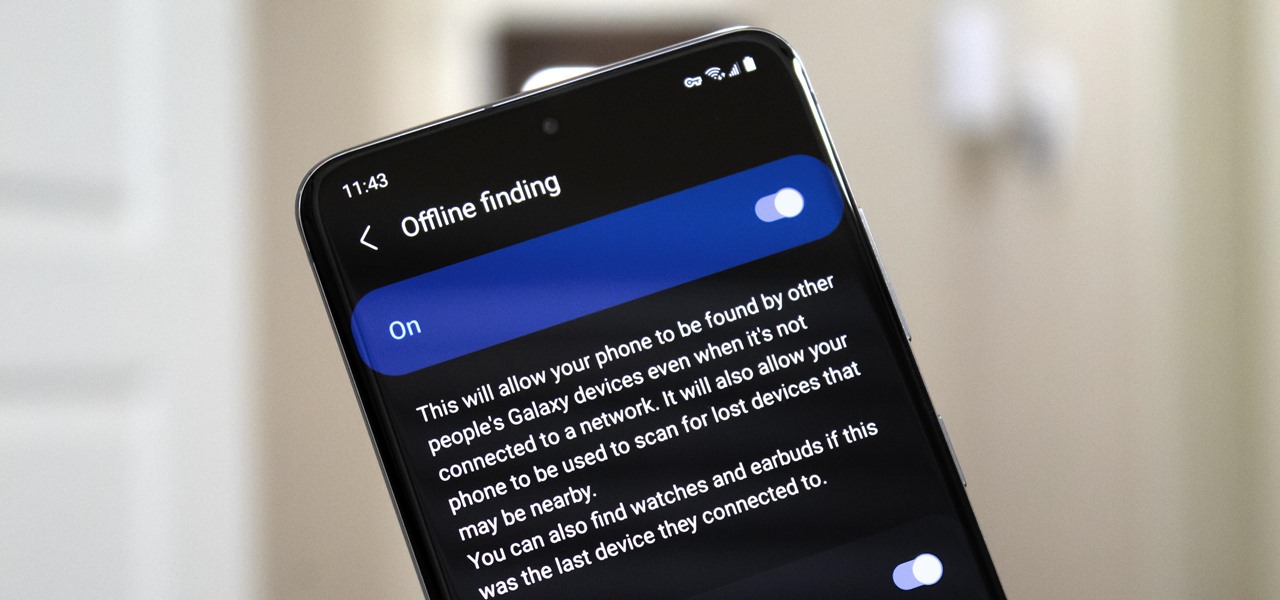
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

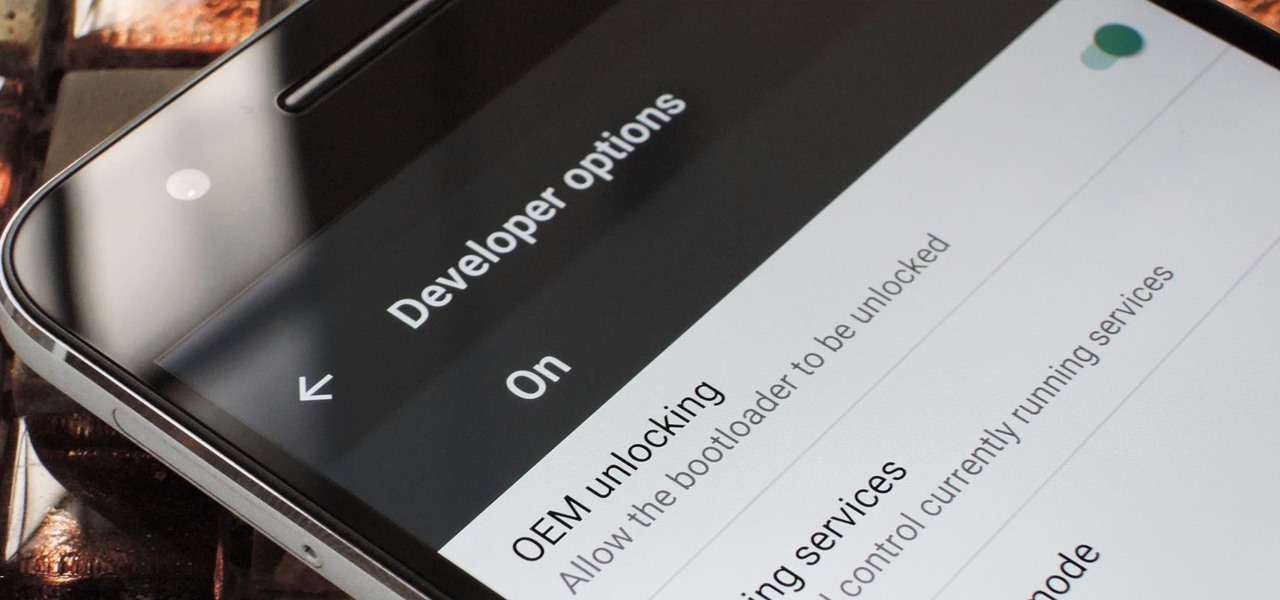
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

There's a lot of personal information residing on your phone, possibly even more than on your computer, so it's only a matter of time before someone tries to access it.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

If you've spent countless hours scrolling through Instagram feeds full of selfies, then I'm sure you know that some are, well ... better than others. There are so many different things you can do to start taking better selfies to post on social media. One really easy way is to start shooting in VSCO.

No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

Do you live in a dangerous neighborhood? Even if your area isn't known to be dangerous, it could still be a target of home burglaries. Don't let the thieves have the upper hand. Make sure the only thing they're stealing is grass. To properly secure your home from external threats, you must find weaknesses potential and potential entry points and fix them.

You love your bike and it was stolen. Although, this is not a good scenario, you still may be able to retrieve it. Sketch the serial number or means of identification into the bike and then when it is stolen you can really get the word out to all the places that it might turn up.

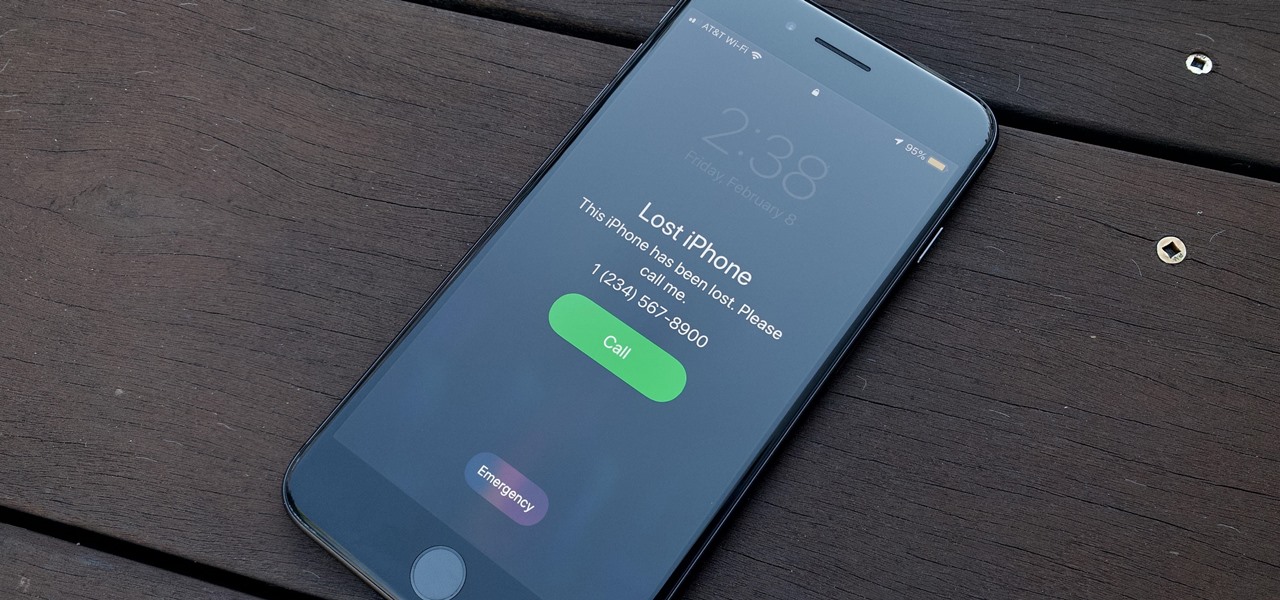
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.