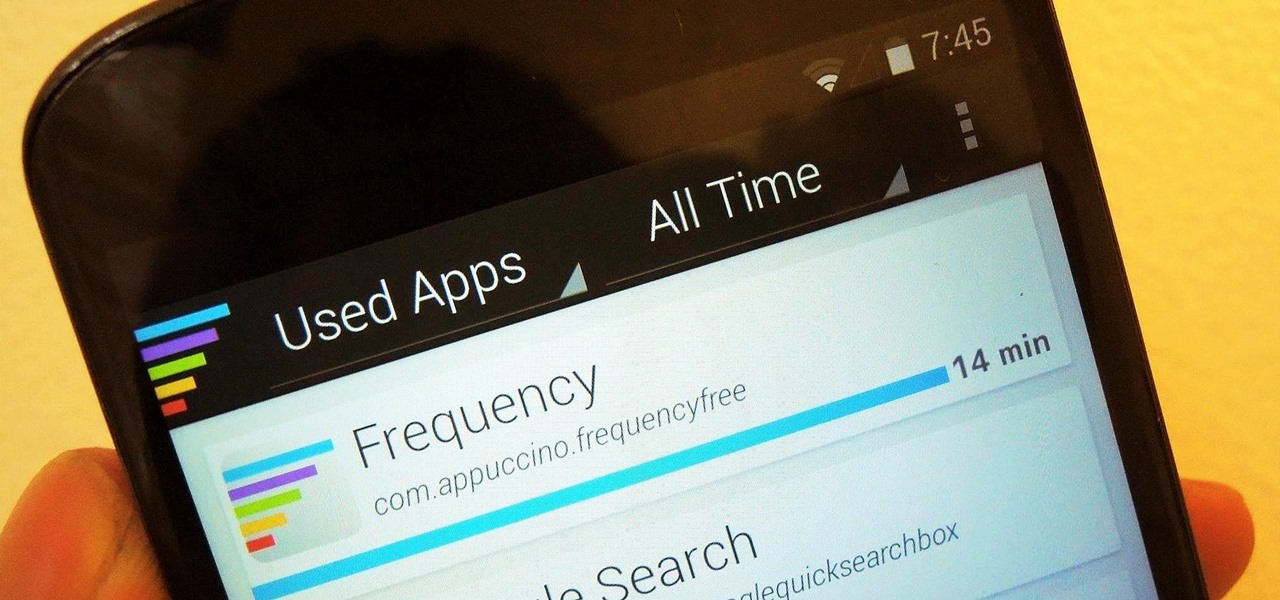
How To: Monitor Your Kid's App Usage on Android
As a parent, navigating smartphone usage with your children can be a perilous journey as you hand them that new device they've always wanted, or even your older hand-me-down phone or tablet.


As a parent, navigating smartphone usage with your children can be a perilous journey as you hand them that new device they've always wanted, or even your older hand-me-down phone or tablet.

Every morning I walk out the door with my headphones plugged in and music blaring. While it's not be the most difficult thing in the world, unlocking my phone and starting my music manually every time feels like a hassle. Pressing play on my headphone's remote will auto-start music in the HTC Music app, but I prefer Google Play Music instead.

Erudite. Barbiturate. Cacophony. Denouement. Okay, that last word is technically French, but words like these make the average person sweat, and it turns out that the key to learning how to pronounce them once and for all just might be getting them wrong.

Team Win Recovery Project (TWRP) is a custom recovery for Android devices and the one used by most softModders, mainly because it has touch-based actions, as compared to the more time-consuming button-based approach that ClockworkMod (CWM) uses.

The original Kit Kat was a mutton pie served at a political club in London during the 18th century, which is quite different than the chocolatey version we're familiar with today. Kit Kat bars have been around since 1911, are produced in 13 countries, and have been sold in over 200 flavors in Japan.
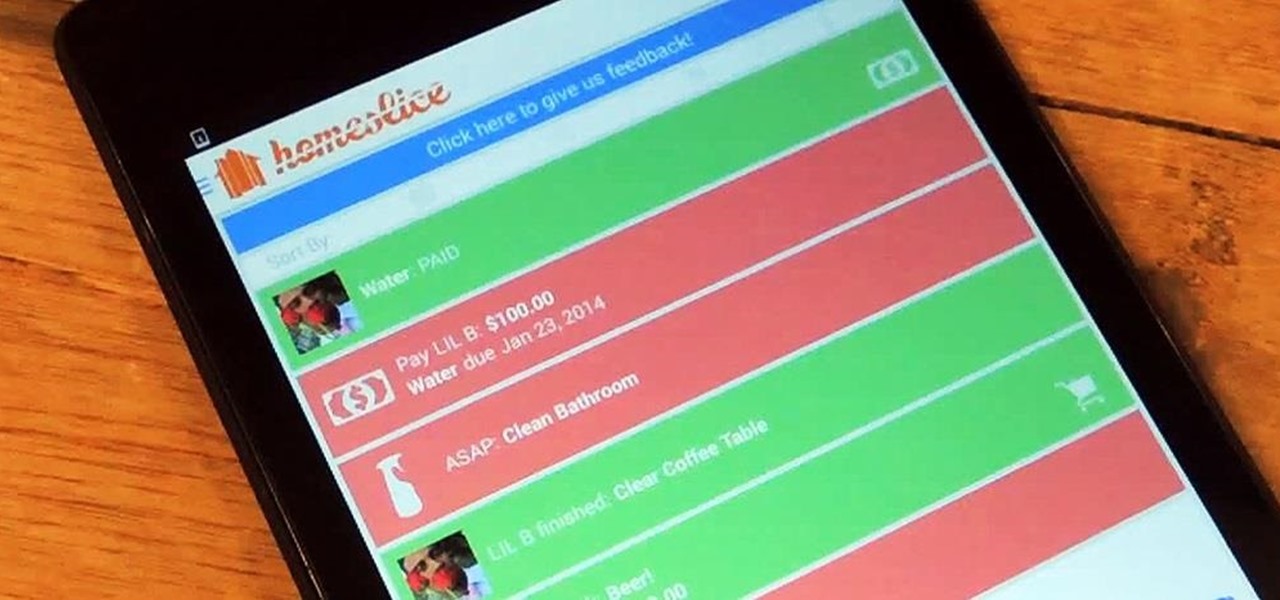
We've all heard our fair share of roommate horror stories, or have some of our own, because we never truly know who someone is until we've lived with them. Cohabitation issues generally revolve around things like bills, chores, cleaning, and groceries. Approaching a roommate, especially an adult one, to remind them to do their chores can be an anxiety-ridden and daunting task. After all, we're roommates, not parents!

The transition from an iPhone to a Samsung Galaxy Note 2 or other Android device can be a tough one. A vastly different operating system and the ability to customize anything and everything might be too much for some people. Taking in all that new, while having to let go of the old, can be as daunting as climbing Mount Everest.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

There are a ton of options available to Android users when it come to messaging, but the problem is that with all of these options, where is the go-to app? The one used by most people? The one that can offer a more unified approach?

So, you've finally converted from an iPhone to a Samsung Galaxy S3 smartphone. Great. Only now you're overwhelmed with the unfamiliar look and feel of the Android operating system.
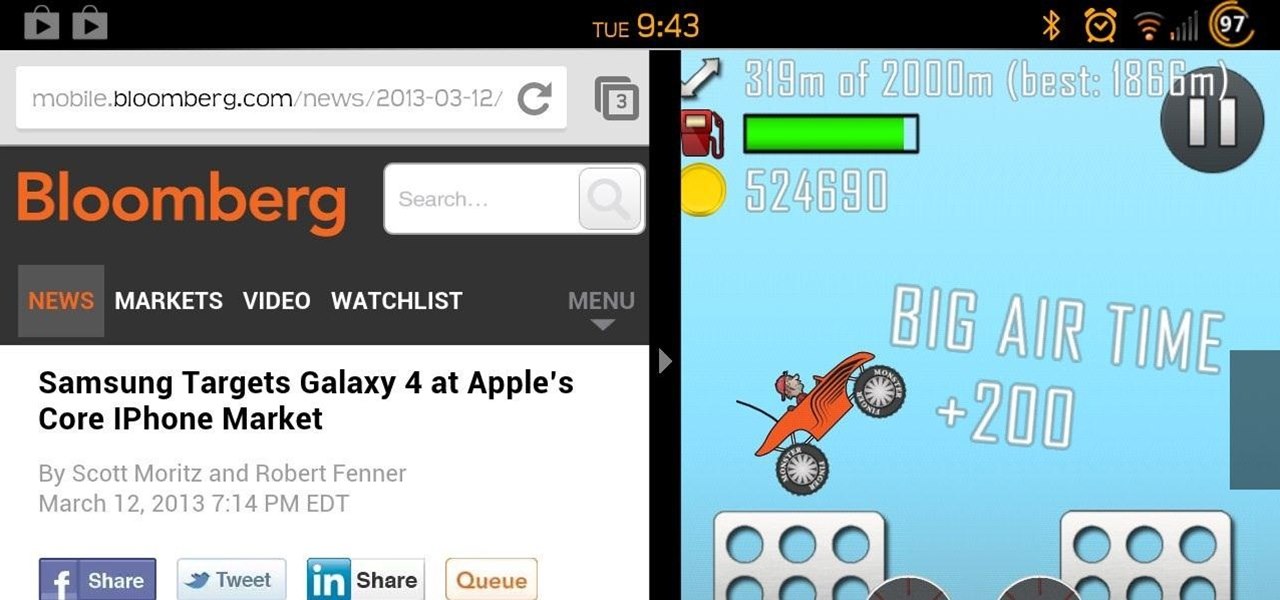
While many of the U.S. carriers have updated their Samsung Galaxy S3 devices to Android 4.1.2 already, one major absence from the upgrade is Samsung's Premium Suite. One of the coolest features from the Premium Suite is Multi-View, a function that lets you truly multitask by running two apps at the very same time—right next to each other. As you can see above in the left image, I have both Pandora and Spotify running. Why? Because why not?!? On the right, I have YouTube on top and Maps on the...

The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

This post has been brought to you by the letter S. With the Christmas season fast approaching, it's time to ask one of the most important questions of our lifetime:

As the holidays approach, so does that wonderful Autumn day where loads of people happily camp out in freezing weather in front of their favorite stores to save a few bucks on their favorite electronics. And yes, that day is near... Black Friday brings the biggest markdowns of the year, and that includes slashed prices on many of our favorite touchscreen devices, including the Kindle Fire HD, Samsung Galaxy Tab 2, and Nexus 7. Want to get your hands on an Android tablet for cheap? Below are a...

The pumpkin is everyone's favorite cucurbit come Halloween time, and while there are only a few types of Halloween-friendly pumpkins out there, there is definitely no shortage of what you can do with them.

Psy's K-Pop hit, Gangnam Style has taken YouTube, and now the world by storm. Love or hate the song, there is just no way you'll watch the music video only once.

Chopsticks are very easily reusable, yet they always get thrown away. You use them when you get Chinese takeout, then toss them out without even a backwards glance.

The guitar is a double-edged sword. I've played all my life, and though I love the act of guitar playing, there are quite a few people I could live with never hearing play again—ever.

The introduction of smartphones has been what some may see as a step backwards in technology regarding batteries. The first cell phone that I had would last 3-4 days on a single charge; however, the lack of functions minimized the use that is saw.
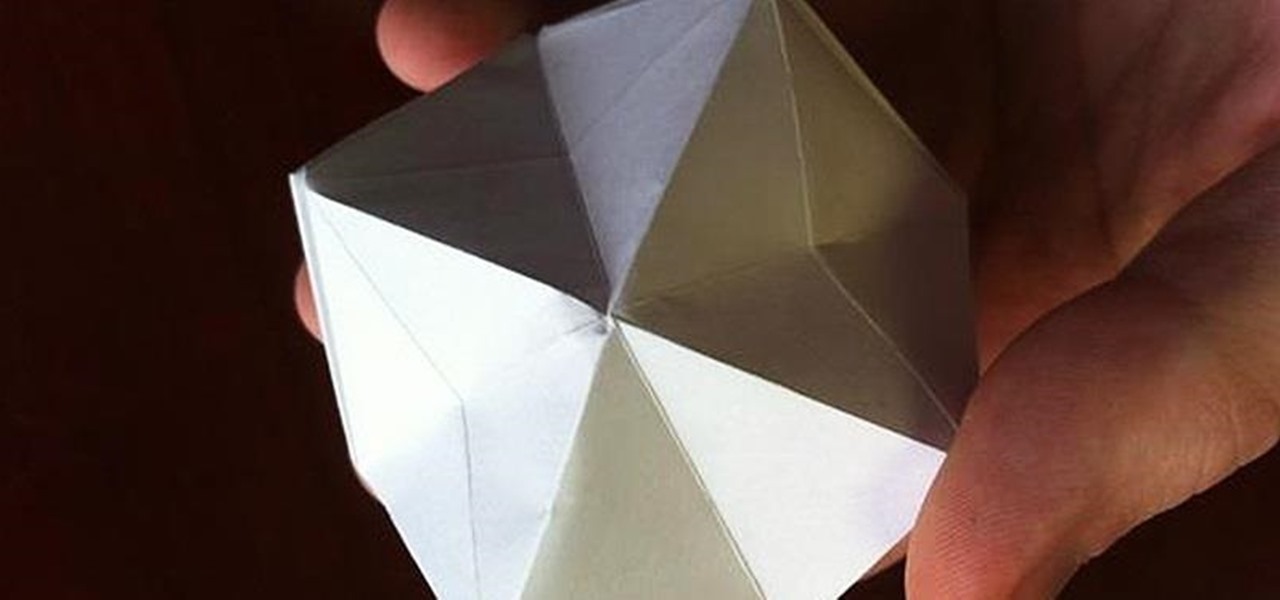
One of the most popular and basic origami geometric shapes is the "water bomb," which is a simple inflated cube. With a few extra folds and only a minor shift in approach, a more complex geometric shape can be achieved.

Deer can wreck havoc on your plants and yard. No need to go to war with the deer, when with a few tricks of the trade, deer can be discouraged from feeding on your yard. The neighbor‘s yard, on the other hand, might seem that much more appealing.

For awhile now, Google has offered the ability to translate text through smartphone cameras via Google Translate and Google Lens, with Apple bringing similar technology to iPhones via Live Text.

Angry Birds, one of the first franchises to find success in mobile gaming, continues to shoot its shot at new life in augmented reality gaming.
As Apple, Google, Snap, and Facebook wrestle for positioning to lure developers and creators to build augmented reality experiences for their respective tools, Facebook is looking at a learning approach for its Spark AR platform.

The new Chromecast represents an evolution of Google's smart TV dongle as well as the Android TV platform. In addition to a remote control and the ability to install apps, Chromecast with Google TV hosts the debut of Google's innovative Google TV interface, which will eventually make its way to Android TV.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

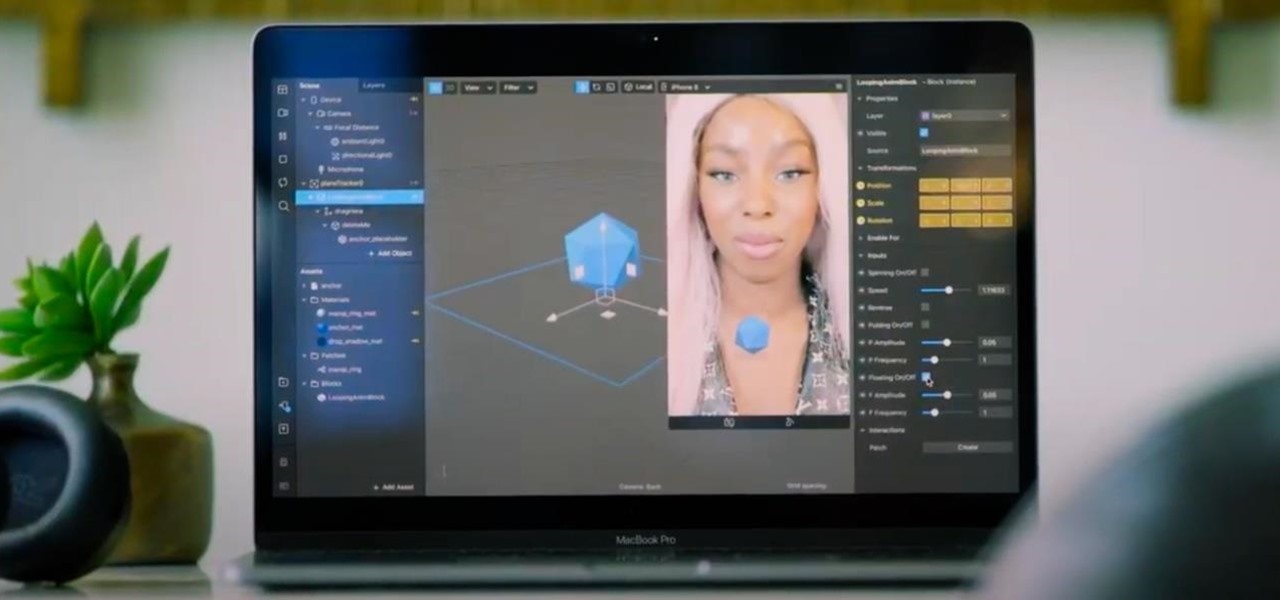
In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.
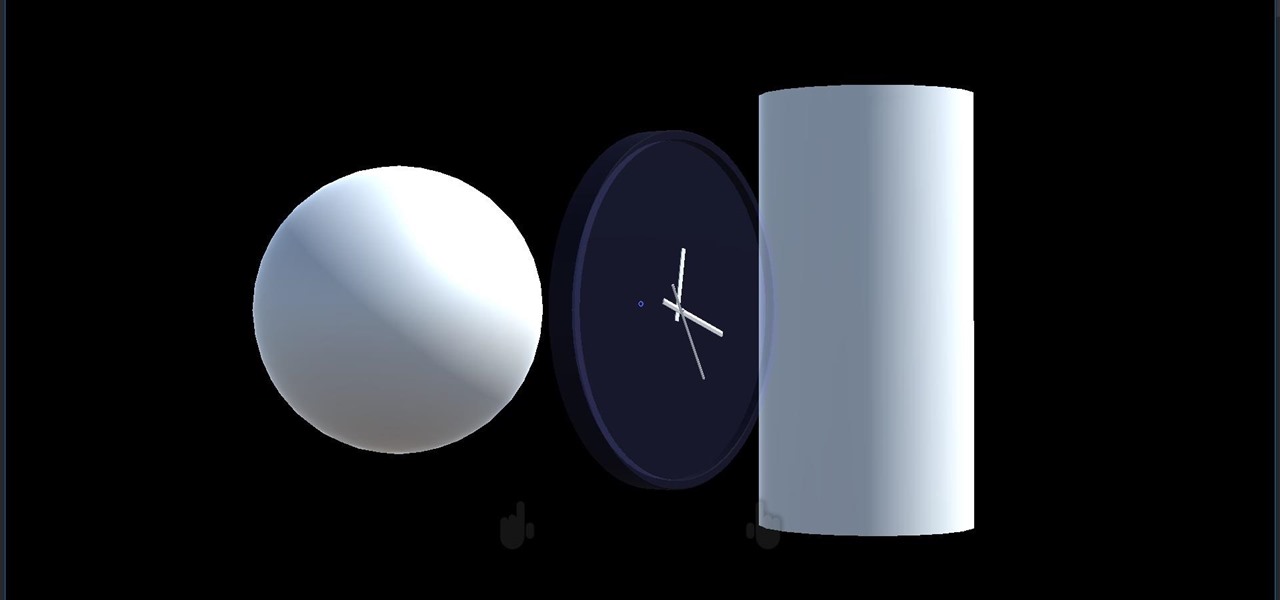
We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.
In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.