
Hacking macOS: How to Create an Undetectable Payload
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.


Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

While the Twitch app for iOS came out way back in 2011, livestreaming iPhone games was a rarity until Apple recently updated its ReplayKit in iOS 11. However, Twitch hasn't jumped on the bandwagon yet, but that doesn't mean you can't livestream your iPhone games to Twitch right now.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

I've been an Android user almost as long as the operating system has existed, so when I received my first iPhone in April, I felt like I was in a foreign land. Sure, it runs most of the apps I'm used to, and the phone itself feels about the same in my hand as any similarly-sized device, but everything else is just different.
Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Macaroni and cheese is one of those dishes that automatically make me feel all is right with the world. I even like the boxed kind in a pinch. However, real macaroni and cheese is pretty easy to make and is worlds better than the boxed kind. It's also pretty easy to make really, really good macaroni and cheese once you know some essential pointers.
Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

Tea has been around for thousands of years, and as a result, tons of customs and ceremonies have sprung up around its consumption. Some cultures take their tea plain, while others put things in it. Sometimes there are special tea-holding vessels, other times not. Maybe there will even be special foods meant to be eaten with tea. However, in America, our appreciation of tea has waned. For many, iced tea is their biggest source of tea consumption, and it's imbibed with no ceremony whatsoever in...

As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those looking to just while away the time.

While I am a writer with a degree in Creative Writing, I haven't published any Steampunk fiction. However, as a panelist and track director, I've been on panels with many well-known Steampunk writers and have gleaned insight from the things they've said. I've compiled some of those things into this post, which will hopefully be helpful to all of the writers out there!

Apple just pushed out iOS 14 to everyone on Sept. 16, but you may not want to jump right into updating your iPhone. If you have Automatic Updates turned on, you may want to turn it off real quick before it tries to download and install iOS 14 before you're ready.

It's almost impossible to use Apple News at night without having to mess with the white point and zoom filters. That might sound a bit dramatic, but it's really not when you consider that iOS 13 has a perfectly good Dark Mode that should work for News. So why are we stuck reading most news stories in Light Mode? We're not, but you have to put a little work into it going dark in News.
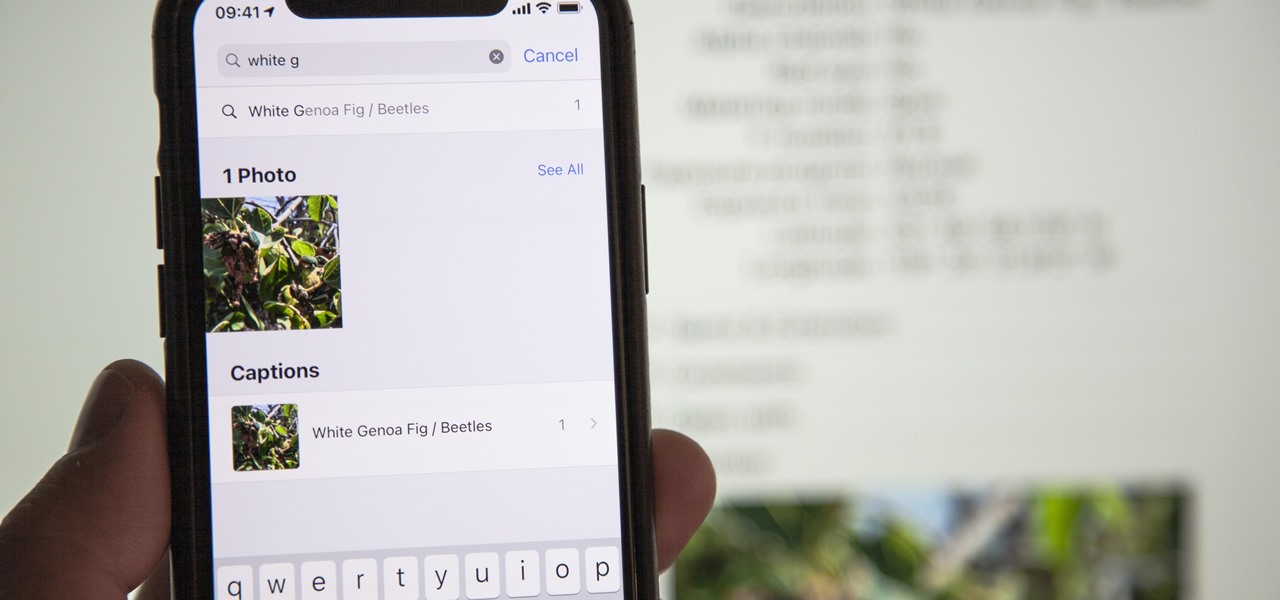
If you've been an iPhone user for quite some time, you probably have quite a bit of photos and videos in iCloud or on your device. Unless you know the date, location, or event, it can be pretty hard to find a specific memory. Even with intelligent search suggestions, AI-created categories, and multi-keyword filters, you still may not be able to find what you want. The new iOS 14 update changes that.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

The holidays are stressful. Between traveling, family, and dinner, Thanksgiving weekend can feel like weeks. Many families have traditions that make the days long, but some of us would rather curl up somewhere and watch our favorite shows. But all is not lost — our phones do so much for us now that they can help make the long stressful weekend much more bearable.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Apple Maps keeps getting better and better for all the hikers in the world. The latest update gives you access to thousands of detailed trail maps within U.S. national parks and topographic views, but it also lets you create your own walking and hiking routes.

Thousands of emoji are available on iPhone, iPad, and Mac, and you can use these in many of the apps you have installed on your Apple devices. But there's one emoji you'll likely never see on any of Apple's official emoji keyboards, and its absence may surprise you at first, considering it's embedded in virtually every Apple product. That emoji is, of course, the Apple logo icon.

Your iPhone's Mail app has a lot of fantastic productivity features, such as unsending emails, follow-up reminders, opening drafts from almost any view, the snooze option, bulk-selecting messages, and the formatting toolbar, but one of the most helpful ones might just be the one you're not using.

Music goes well with almost every Instagram story, but adding a particular song or soundtrack isn't the most obvious task if you've never tried before or haven't done so in a long time.
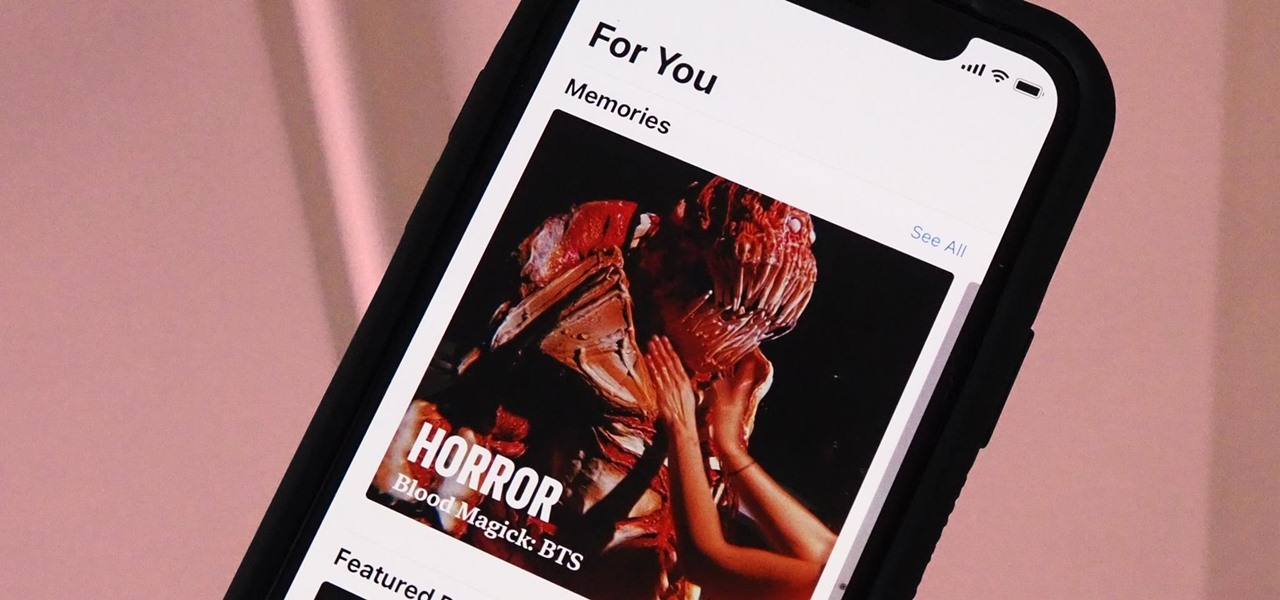
The Memories feature in Photos is meant to help you rediscover old or forgotten experiences by creating a short slideshow of photos and videos based on locations, dates, and events. It's a fun feature to relive exciting times, but it isn't always perfect because it's generated automatically. It might include incorrect content, but in iOS 14, you can now create your own Memory Movies.
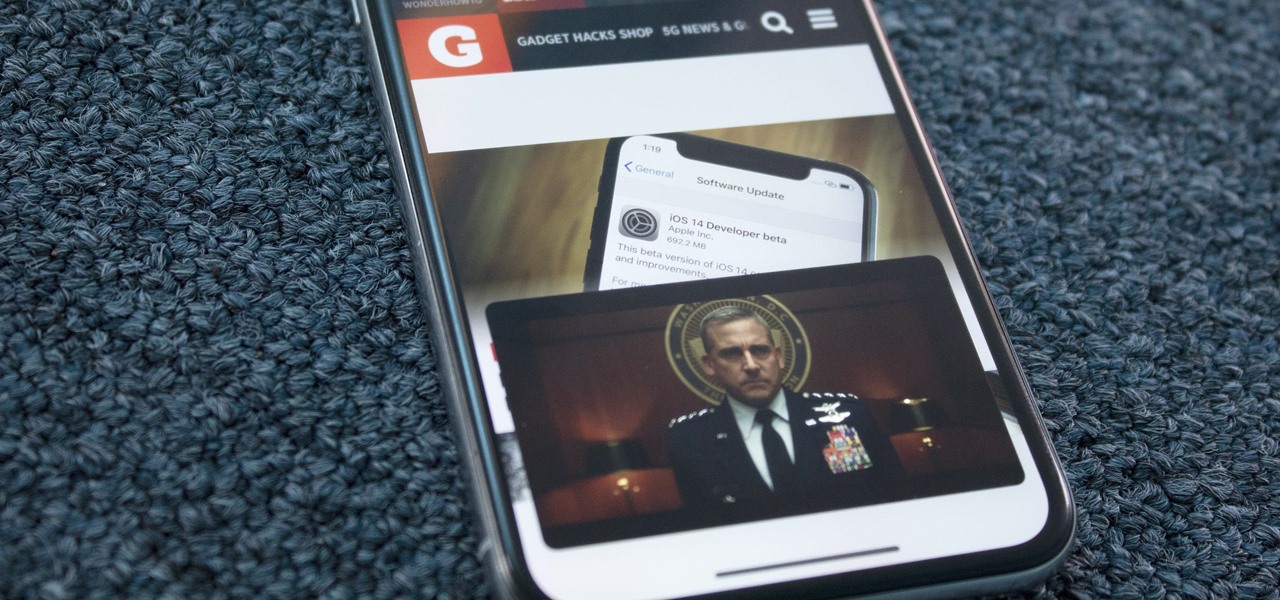
Have you ever watched a video on your iPhone but wanted to look at something else real quick? Before iOS 14, you had to choose between pausing the video or waiting until it's over — not exactly ideal for a device that's supposed to help you multitask. But with iOS 14 or later, we can use picture-in-picture mode to watch and perform other on-screen tasks at the same time.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds.