Netflix has become the subject of heavy buzz this week, and not due to the latest season of Daredevil (which gets two thumbs up, btw). The online video entertainment provider is drawing fire over its admission that it has been throttling video streams for its AT&T and Verizon customers for years.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

The following are 10 simple yet effective pranks you can set up around the house, school or the office on April Fools' Day. You'll won't need any special tools or materials to pull these off.
By default, the Play Store app on Android is set to automatically update your apps in the background. This definitely makes it easy to ensure that you're always running the latest versions, but it does come with some downsides.

Google dropped its opposition to T-Mobile's Binge On service due to some favorable policy changes at the magenta carrier. From now on, YouTube and Google Play Movies will happily work with the feature. Binge On rolled out late last year, allowing many customers to receive unlimited video streaming at 480p. That's not a great offer if you care about video quality, but it's nice if you want to save money.

In this video I'm going to teach you 5 pranks you can get away with at school or at home On April 1st.

Video: . The following are 5 Simple household pranks you can pull off on friends and family this upcoming April Fools' Day! All the material needed you already have at home so lets get started! Check out the video tutorial for further instruction.

While there are tools online that let you turn photos into interesting emoji art, and mobile apps that let you create emoji mosaics, none do it better than an iPhone app by second verse, which makes it a super easy, highly customizable process.

This year's Nexus devices are already two of the best bang-for-your-buck smartphones on the market, but with a new sale price from several retailers across the net, they might just be an unbeatable deal.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

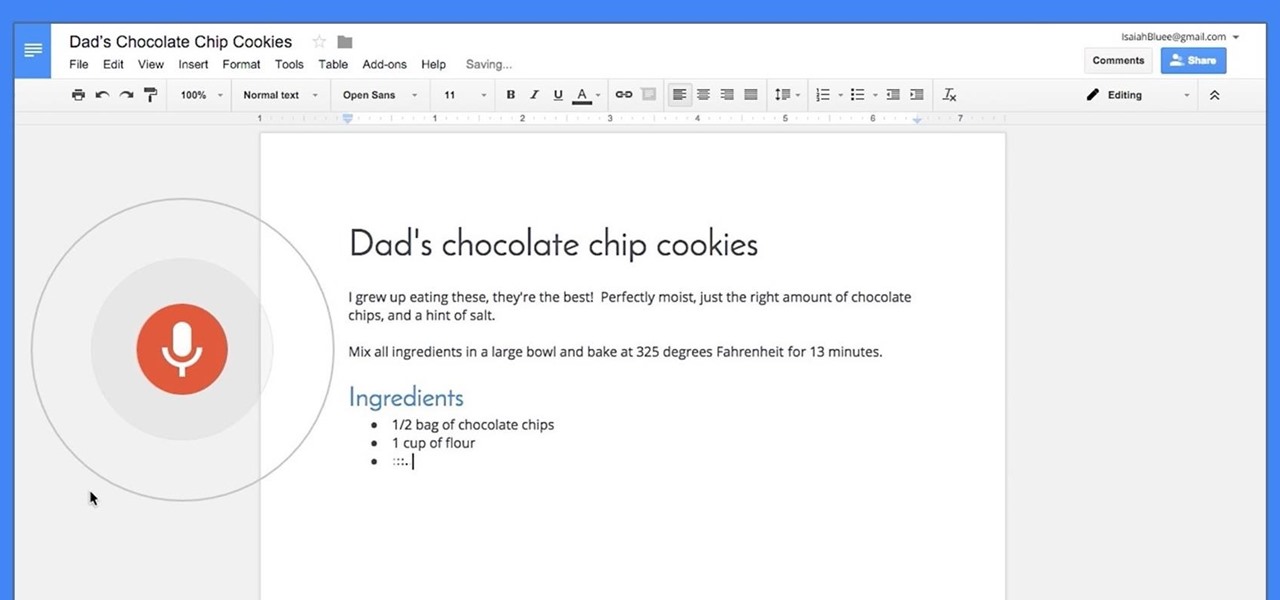
Google launched voice typing for Google Docs last Fall, and followed that up about six months later with voice commands that let you format and edit text as well. You can do things like select text, apply format settings like alignment and headings, and add and edit tables—all with your voice.

For years, users have been clamoring for a "dark mode" theme in Android, but it has always seemed like Google is so committed to the white motif from their web services that such an option would never become a reality. But in a stunning turn of events, Google is finally embracing the idea with a night theme that will work in any app, and I'll cover all of the specifics below.

After months of speculation and sifting through rumors, Samsung finally unveiled its Galaxy S7 and S7 edge flagships, and they're pretty much what we had been anticipating. But just because there weren't any major surprises doesn't mean that it's not still exciting. Let's have a look.

YouTube announced last October some of the original programming it was producing for its YouTube Red subscription service, and the first four originals went live on Wednesday, February 10th.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Samsung makes some wonderful phones, but one thing I've noticed is that battery life can start to degrade over time, causing the phone to die a lot faster than it used to. If you've been experiencing this issue, and have asked yourself, "Why does my Galaxy S5 die so fast?" there are a few likely causes—and we've got you covered with troubleshooting tips and simple fixes below.

The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

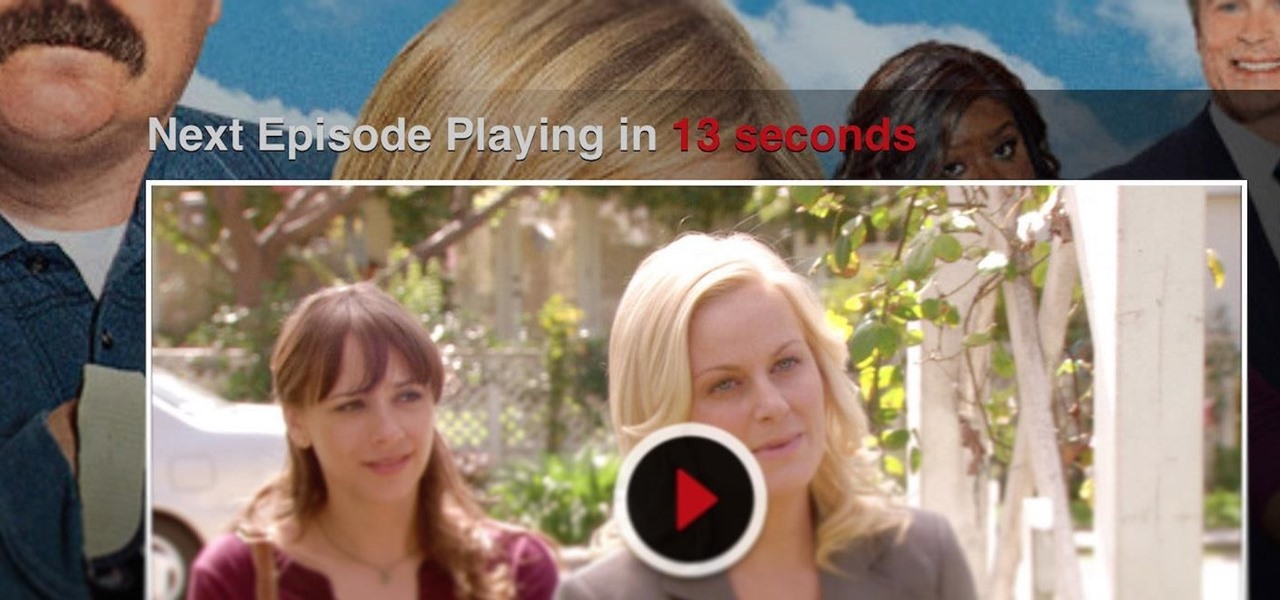
Cord cutters are changing everything about TV—the more of us that sever ties with cable, the more changes we start to see. In fact, viewing habits have already changed so drastically that waiting a week to see the next episode in a series is no longer acceptable, as binge watching has completely eclipsed this old-fashioned format.

Hello there Nullbyters, Last tutorial we discussed navigating and setting some options.

Hello there Nullbytes, In my previous tutorial found here,

My least favorite aspect of the winter season is how my fingers always turn into stiff, numb digits, unfeeling and seemingly incapable of making even the slightest movement. Yes, that might sound overdramatic, but if you hate wearing gloves like I do, you probably know exactly what I mean.

Most wood furniture is long-lasting, durable, and resistant to great wear and tear over the years. However, set a single sweaty, wet cup or bottle on the surface of your favorite wood dining table, or your prominently placed wooden coffee table, and you'll end up with a round water ring stain that is difficult to get rid of.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

The Creative Lab at Samsung, also known as their C Lab, is trying to make wearable fitness devices more inconspicuous with its wearable smart belt, the WELT, but that might not be all.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

If you've been visiting websites of ill repute, or if you've been Christmas shopping and don't want to spoil the surprise, it would be a disastrous situation if anyone were to come across your browsing history. Visited sites, cookies, and cache can paint a very clear picture of your recent internet activity, and depending on the situation, you may only have a few seconds to delete your history before someone else barges in.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

What's up guys! It's time to discuss strings in more detail. Review
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

Starting a few months back, you might have noticed that some text messages you received from certain friends or family members had blank or missing characters. This was because Apple included all of the new Unicode 8.0 emojis in an update to their iPhones, but Android devices didn't have some of these just yet, so they weren't capable of displaying them.

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

It's nearly impossible to keep a stovetop clean when cooking, at least, in my experience. No matter what I do, liquid and solid food bits fall to the surface and around the burners every single time, creating a hard-to-clean mess.
Basically, this article is a true life experience writing from the introspective mind of the writer and do share more knowledge on how to deal with introvert lifestyle.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"