Update Feb. 2020: Google has removed the feature flag to move the address bar to the bottom of the screen. We've out to see if they have plans to bring it back, but received no comment. In the meantime, you can use the new Chrome Duet bottom bar instead.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

No one ever said you had to be a culturally-relevant pun for Halloween, you know—or a scantily-dressed version of the inmates from Orange is the New Black.

Google has a habit of starting on new projects for Android, then hiding them away if they didn't quite complete them in time for a major release. We saw this with multi-window mode last year (which is now an official Nougat feature), and this year, there was the hidden night mode setting that was easily activated.

This tutorial will show you how to customize a Monster High doll using a My Little Pony Equestria Girls Mini. Watch this video to see how it is done. When you are done painting your custom doll, add a thin layer of Mod podge to seal the paint.

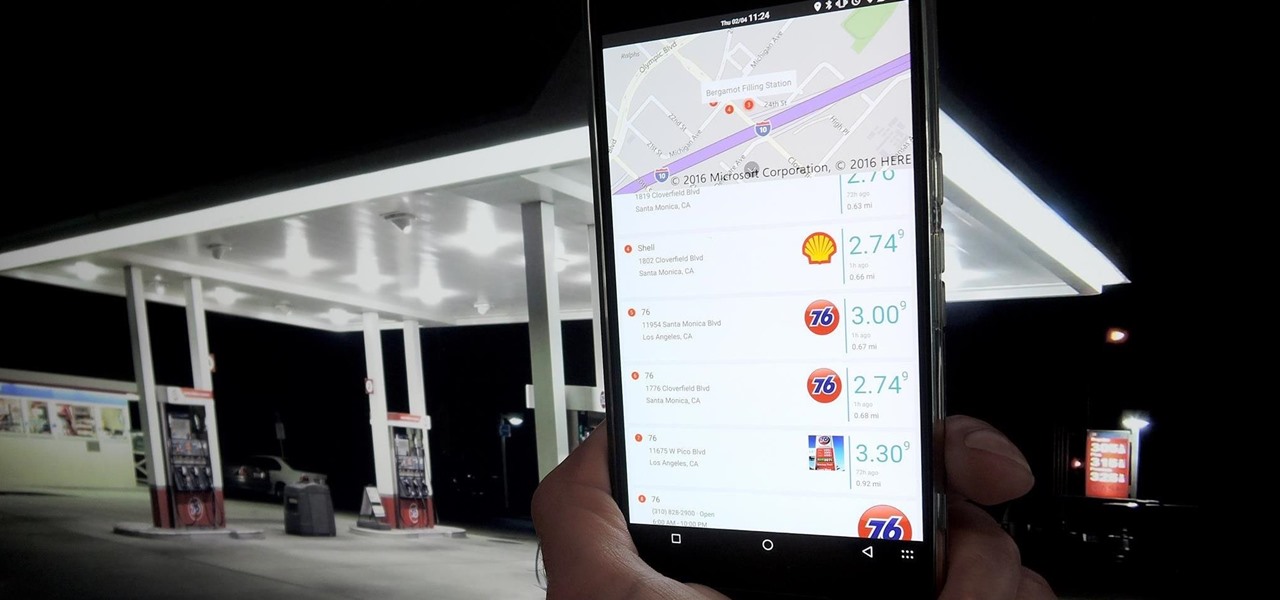
The Galaxy S7 edge comes with a feature called Edge Apps that lets you quickly launch your favorite apps by swiping in from the edge of your screen. It's a natural and intuitive gesture, and as a result, we've seen a recent influx of apps that look to emulate this feature.

Remember that feeling when you first took your smartphone out of the box, powered it on, then proceeded to futz around with it for the rest of the day non-stop? If you've owned your device for more than a year, chances are, that scenario is a distant memory by this point.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Microsoft is working hard to make Bing a good alternative to Google for more than just looking up images of the "human anatomy" that Google and a lot of other search engines filter out of their results.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

A series on how to build a Mack F series cabover conversion model truck at 1/25 scale. Part 1

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

My father never cooked a meat without some kind of marinade. He always used a slew of ingredients: salt, pepper, Season-All, Cajun seasoning, vinegar, olive oil, liquid smoke, Worcestershire, hot sauce, onions, lemons... I'm pretty sure this isn't a complete list, but I've honestly forgotten the rest! It always tasted amazing, but the long list of ingredients was definitely a detriment whenever replicating the marinade.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

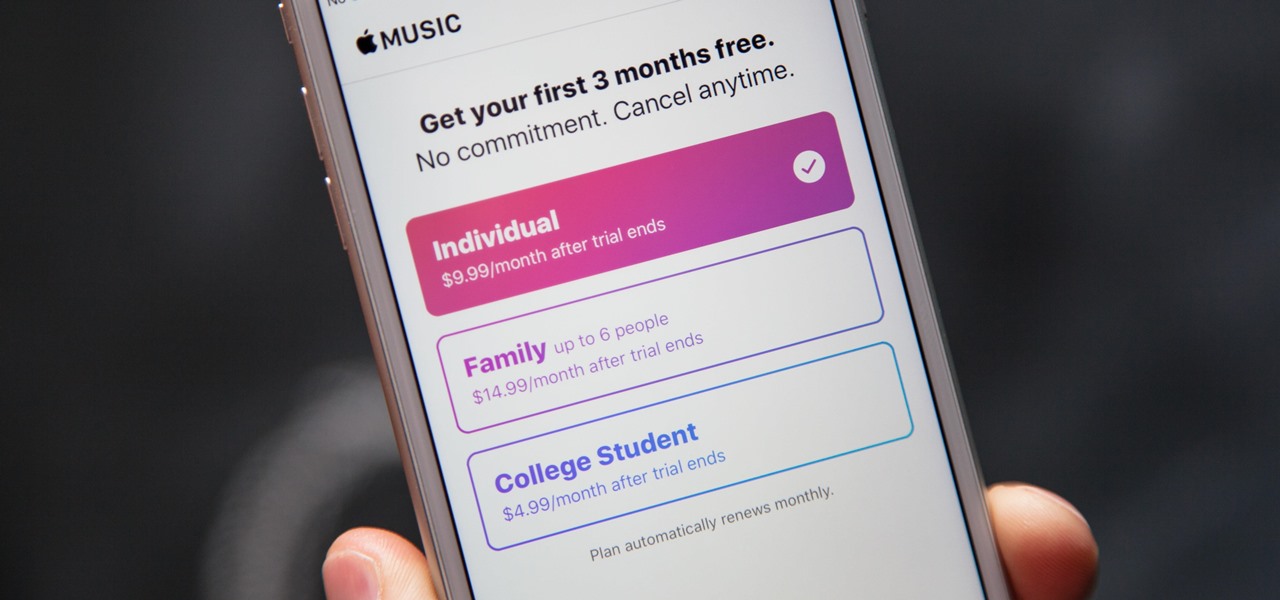
Apple's streaming music service, Apple Music, offers a three-month free trial that hopes to get you addicted enough to pay for a monthly subscription. You may even see a one-month trial if you're a former subscriber. While it's not very obvious, there is a way to cancel either free trial from auto-renewing. That way, you don't have to deal with Apple support to try and get your money back because you forgot.

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

Hi there, nullbytes! I've been recently using NullByte as my only source of learning (almost) and it has proven to be really good to me.

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

Was it your New Year's resolution to quit smoking this year? Whether you are a first-time quitter or a chronic relapser, this is the year to kick this unhealthy habit for good.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

The autocorrect feature in Apple's default iOS keyboard is anything but perfect. Sometimes it can't autocorrect things on your iPhone to want you want, while other times there's a software bug that just flat out gets it wrong. These autocorrect issues can get even worse thanks to Apple's predictive text feature, QuickType, and the inability to edit your custom dictionary.

If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity.

Sometimes, stock just doesn't cut it. When you're sick of the limitations in Sense on your HTC One, a new ROM can be a ray of sunshine. By installing a custom ROM, you can add or unlock new features in Sense, or you can get a pure Android experience instead. It's all up to you.

Nintendo fans rejoice! Not only can you play classic NES games on your iPad or iPhone without jailbreaking, you can play Game Boy Advance and Game Boy Color games. And that's not it. Now, thanks to @angelXwind, we can add Nintendo DS to our list of non-jailbreak emulators for iOS 7.

The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further.

Me doing 21 wide grip pull ups to get the day started.

Xposed, by XDA developer rovo89, is a framework for your Samsung Galaxy S4 (or other Android device) that lets you add tweaks and customizations to your ROM (either stock or custom) without any real hassle.

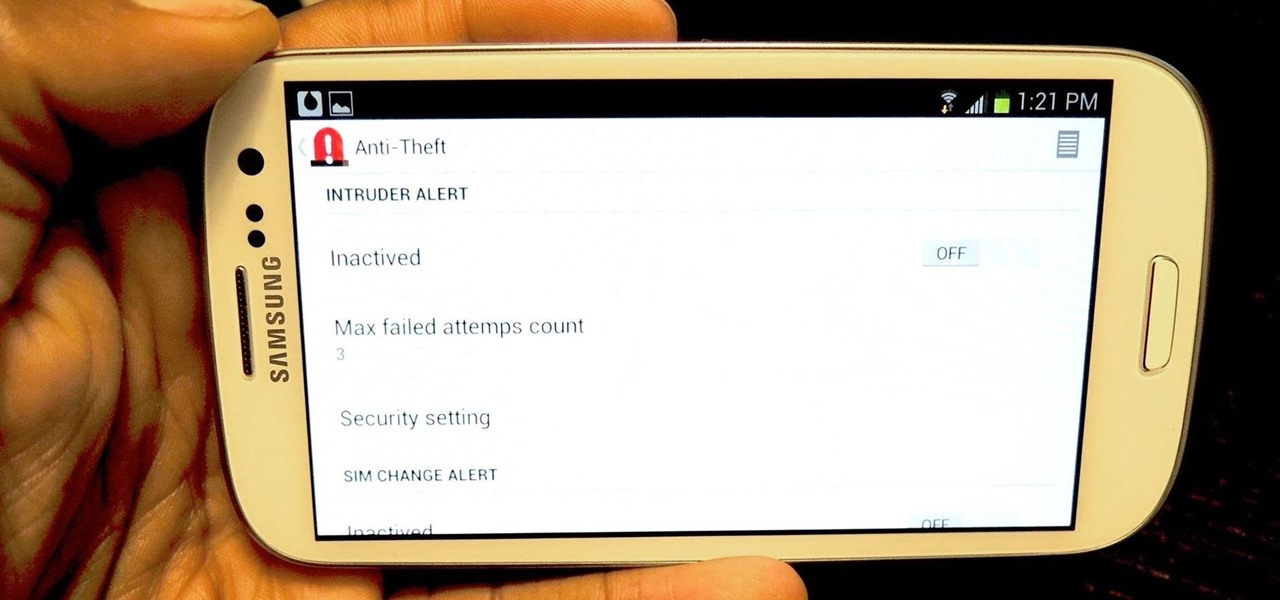
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

One thing that gets overlooked on Facebook is the amount of videos you can watch, and I'm not just talking about videos uploaded directly by Facebook users—I mean everything ever shared—YouTube, Vine, Instagram, Vimeo, etc.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

There are a lot of do's and don'ts when it comes to block sanding the primer surfacer on your car. In fact, this can make the difference of creating a show quality paint job and a less that average paint job.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.