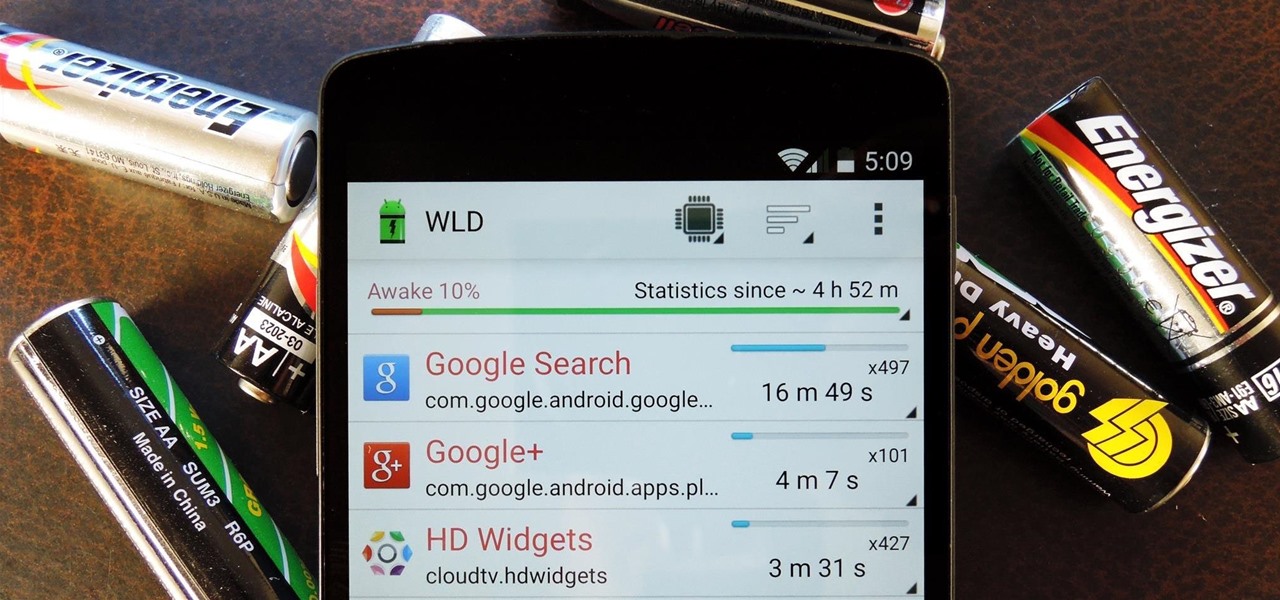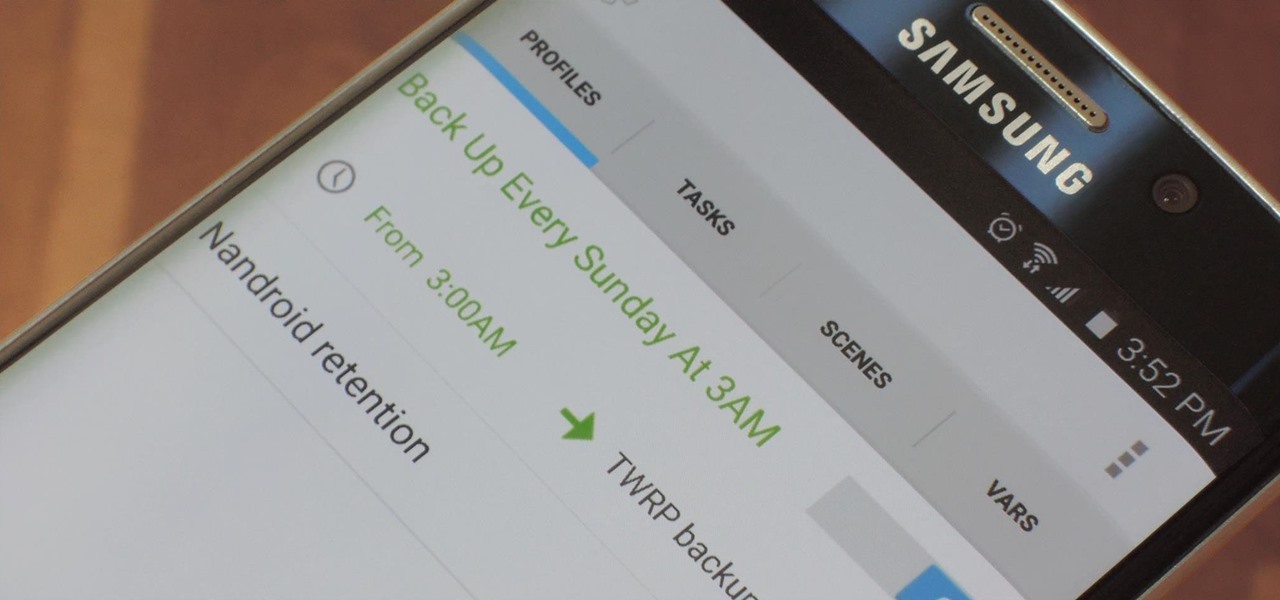
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

If there's one thing that gets used far too frequently in the modern kitchen, it's the trash can. Home cooks everywhere waste enormous amounts of food by throwing it away before it's actually ready to be tossed.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

In general, smartphones and cars don't mix—but this is mainly because you have to take your eyes off the road to poke around on your handheld gadget. In reality, the only difference between your smartphone and your car's FHWA-approved infotainment system is that the latter is mounted in a fixed position and has an oversized interface that makes it easy to use without looking away from the road.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.
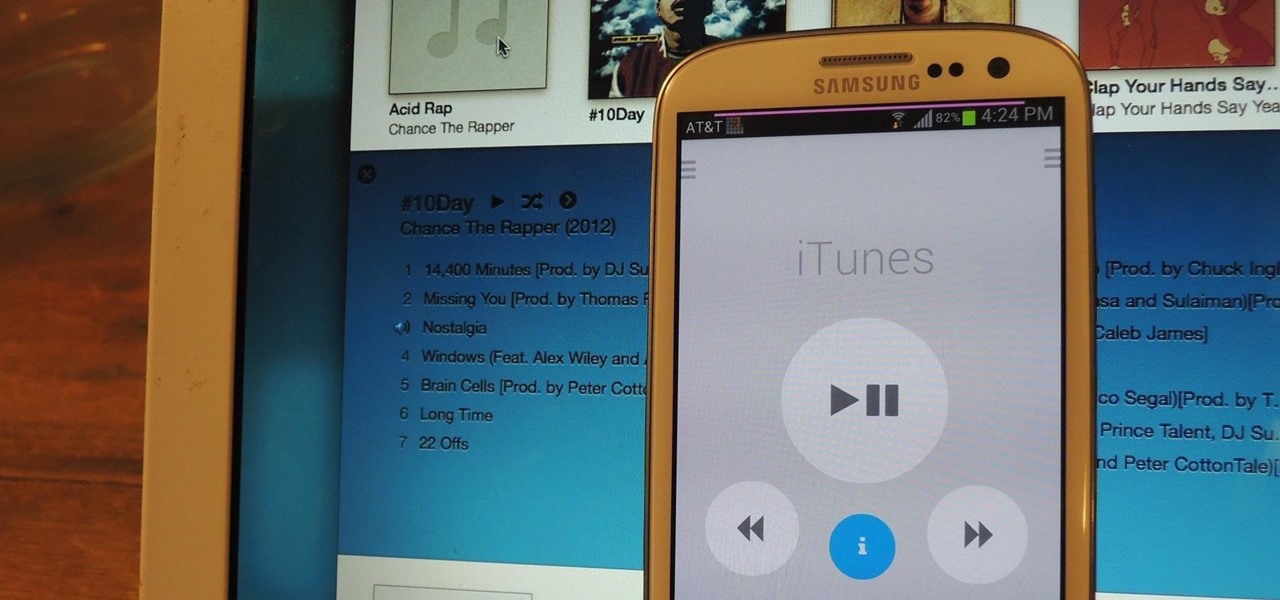
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Having websites coded for mobile browsing is great for small screens, but if you have a Plus model iPhone or even the iPhone X, desktop versions of websites might show you more of what you want. Plus, there's the case of poorly designed mobile websites, where the desktop view is clearly the better option with more functionality and features. Luckily, asking for desktop sites in Safari is simple.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

Since the new Mac OS X 10.11 El Capitan is brand new, I recommend installing it on a separate partition on your hard drive. This will keep your current Yosemite system safe from harm, and will let you easily switch back to it should El Capitan become unusable for any reason.

Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our absolute favorites.

Samsung has a long-standing reputation for packing their devices with lots of added functionality, and the Galaxy S6 Edge is no exception. It comes with a nifty feature called "Information stream," which allows you to get quick, at-a-glance information by swiping the edge of your screen back and forth while the display is off.

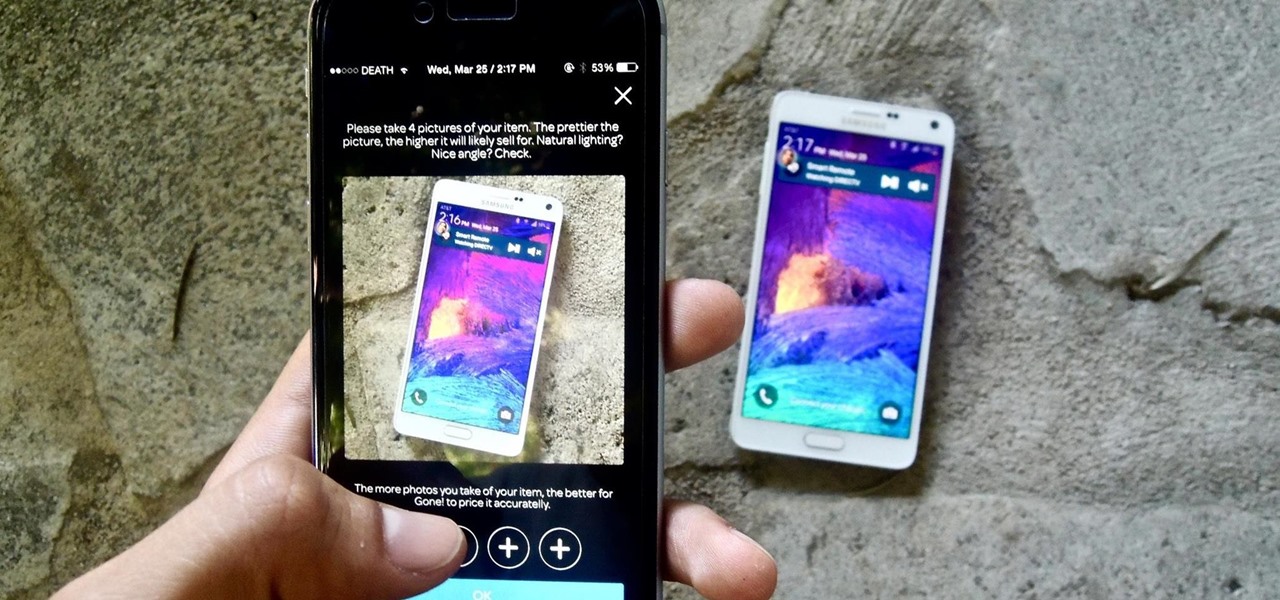
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedback. Craigslist is a little bit easier, but usually requires you driving somewhere to meet the buyer in a public place (if you want to play it safe).

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

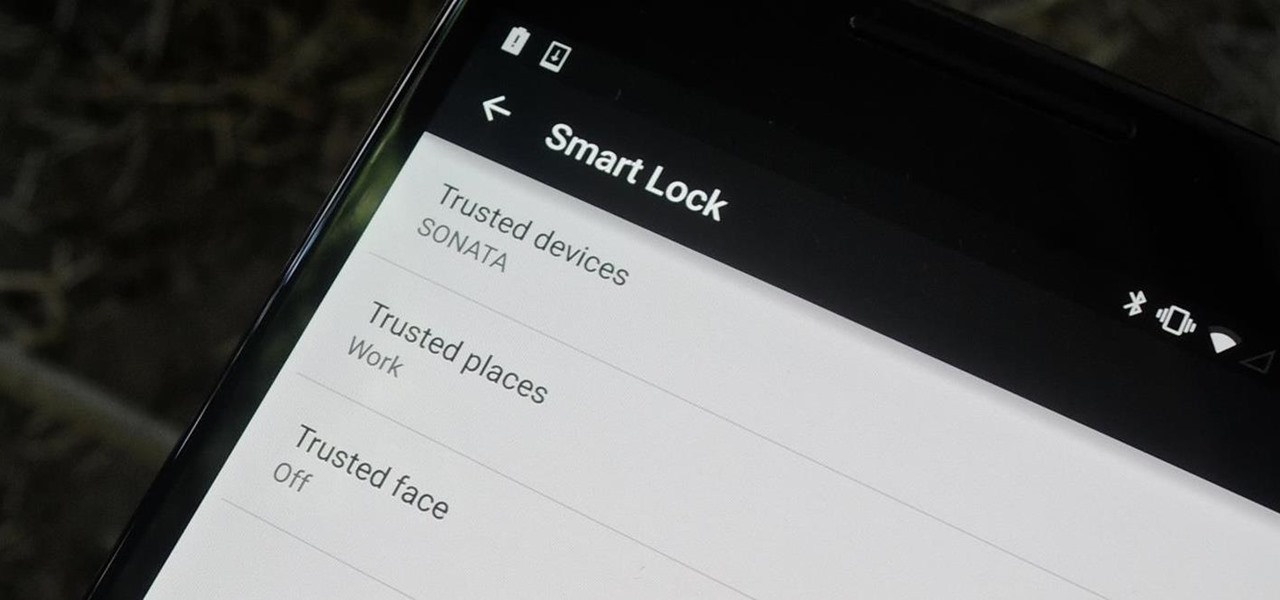
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Linux may not be the most popular consumer operating system out there, but what it lacks in consumer app variety, it definitely makes up for in flexibility and security. And if you've ever tinkered with a Linux distro, you know how easy they are to install—most of the time, I skip standard installation and boot directly from a CD.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

iPad, iPhone, and iPod touch owners: it's that time again. iOS 8 has been released to the public, and those who have been eager to update since Apple's WWDC announcement won't have to wait any longer. Since iOS 8 promises to pack a bunch of new, really great features, it's time to present your options for getting on the latest and greatest for your Apple device.

All Android web browsers are not created equal. Some, like Chrome, have slick interfaces and quick rendering, but are not very robust. Others, like Firefox, boast tons of functionality and support add-ons, but are lacking in the interface department and could use a boost in performance.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

It's common knowledge that certain foods foster brain development, health, and memory. Fish almost always makes the list, as do any foods that are loaded with antioxidants like blueberries, nuts, whole grains, green tea, and dark chocolate. Spices like turmeric are being studied for their ability to prevent Alzheimer's, among other things.

If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particular app.

While some mobile sites have built-in text-resizing tools, many do not. A lot of those that don't won't even let you pinch-to-zoom. That makes it difficult for people with low vision to read small fonts on their iPhones. In some cases, like with photo captions, even those with perfect eyesight suffer.

With just a swipe and tap of a finger, we can access enormous libraries of information on our smartphones like never before. Whether we want more info about gluten sensitivity or just want to brush up on 18th century philosophers, there's an article somewhere in the vast ocean of the internet that can lend us a hand.

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

It's nice to have a drink on an airplane, whether you're taking a flight somewhere fun or for work. However, what's not so nice is the high prices and relatively bad quality of the liquor that's available.

If hearing the names of classic PC games like Commander Keen, Fallout, Master of Orion, and Wolfenstein 3D send you into a fit of nostalgia, then DosBox Turbo is the perfect app for your Android device.

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typical brick, but also in the form of watches and cell phones.

Windows 8's interface was met with criticism when it was released, mainly directed at the tiled Start screen, a departure from Windows versions of old. Many felt that this new home screen style was better suited for mobile devices like Microsoft's Surface tablets and Windows Phones.

I'm a pretty nice person, so when someone asks me to take a group picture of their friends or family, I can't easily say "no," even if I have somewhere else to be. Even worse—sometimes I'm the one asking, fully knowing just how annoying it can be. Maybe you've been told "no" before, and have had to settle for being left out of the picture, which kind of sucks.

One of the most frustrating things about full touchscreen phones, especially for those coming from one with a physical keyboard, is typing and editing text. Whether it's a quick text message, or Swyping out a full e-mail, it sucks realizing you've messed up a few words and have to go back and fix them.