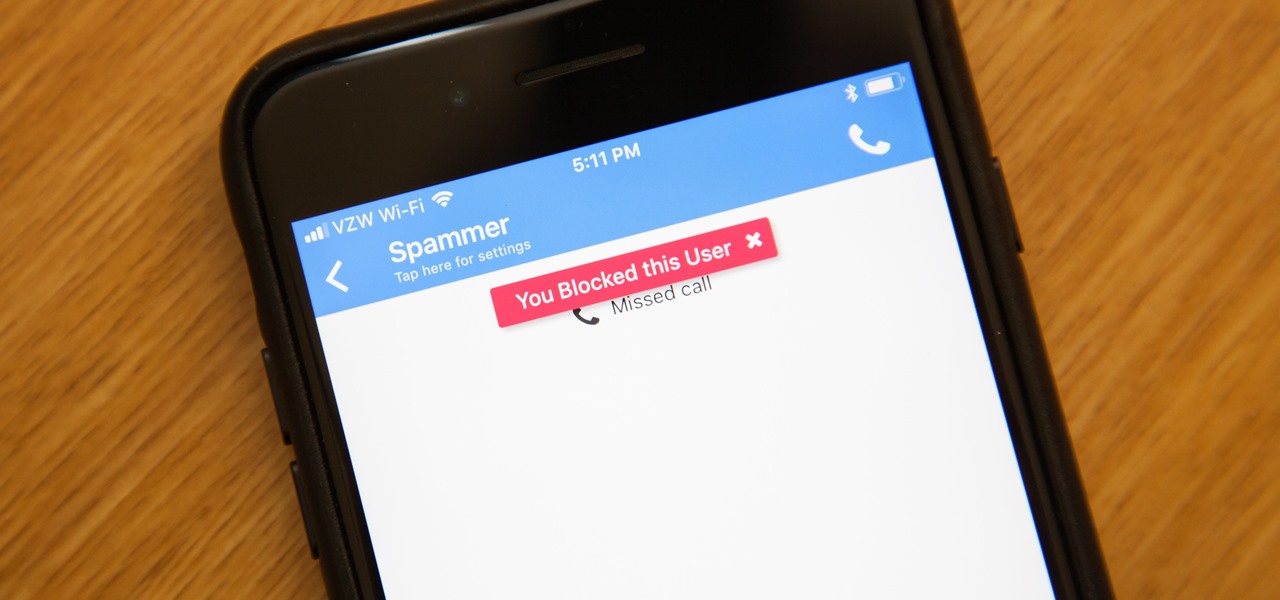
One important part of jewelery making involves properly crimping beads. This jewelry how-to video demonstrates the proper way to crimp beads on a wire. With the crimp bead on the wire place the bead in the first notch of the crimping pliers. Gently squeeze the tube until it is flat and secures the wire.
Take a look at this instructional video and learn how to install the Twilight hack for you Wii. The twilight hack is an exploit that reads a elf file off the root of your secure digital (SD) card. To start up this hack, you'll need to load the Zelda: Twilight Princess game before you can run any unofficial software.

In this how-to, Gary Rosenzweig of MacMost.com takes a look at best practices for making and storing passwords. You should have a different password for every account, for example, use secure passwords and store them in using a security utility. Learn how to store your passwords securely with this tutorial.

Ladies, here's a tip on which shoe size to buy your dance shoes in. A snug pair of shoes is more secure, and will make Latin dancing easier. Watch this video dance tutorial and learn how to pick the right size of shoe for Latin dance.

This instructional violin playing video shows one method of reducing the shaking of the violin when practicing vibrato. Just wrap the scroll with a piece of towel, and then place it against the wall to secure the position. Then practice the vibrato on the violin. This video is great for beginning violinists.

Tired of slipping and tripping on that pesky area rug? You can make any rug in your house non slip with just a tube of silicone adhesive. Watch this how to video and find out how to secure the rugs in your house.

RC Car Action Magazine Editor Kevin Hetmanski shows you how to put thread lock on your wheel nuts. Thread lock will keep the nut from loosening. Watch this video tutorial and learn how to secure nuts with thread lock on a remote control car.

RC Car Action Magazine Editor Paul Onorato shows you how to anchor an antenna tube to keep it from falling out. A piece of fuel tubing will solidly affix the antenna to the chassis of the remote control car. Watch this video tutorial and learn how to secure an antenna tube to the body of a remote control vehicle.

Watch this video jewelry making tutorial and learn how to flatten a crimp tube while making jewelry. Crimp beads when clamped, other beads from sliding around past a marked section,as well as secure closures on earrings, necklaces, or any other kind of jewelry.

This tutorial video will show how to do the typical soft knot used in silk ribbon embroidery, or the preferred method of the quilter's knot. Most ribbon embroiderers do not use a knot and just pierce tails or come back with another needle and thread and secure the tails that way.

This how to video is a tutorial on how to introduce a new color into a crochet project. Changing to a different color yarn is very simple with this instructional video. All you have finish your last row with a slip stitch, pull it through and secure it. Follow by adding you new yarn color with a simple slip knot.

What you need to do is press a certain button when your computer boots (it should say something like press this key to enter setup). Press the specified key and inside the bios find the option that allows you to set a password. Once you create a password then you have to set it so the computer requires the password on boot. Please rate and comment this video.

This "double sheet bend knot" is the same as the sheet bend, except that is has an extra turn to make it extra secure. Use this knot instead of the sheet bend if you have springy or slippery lines.

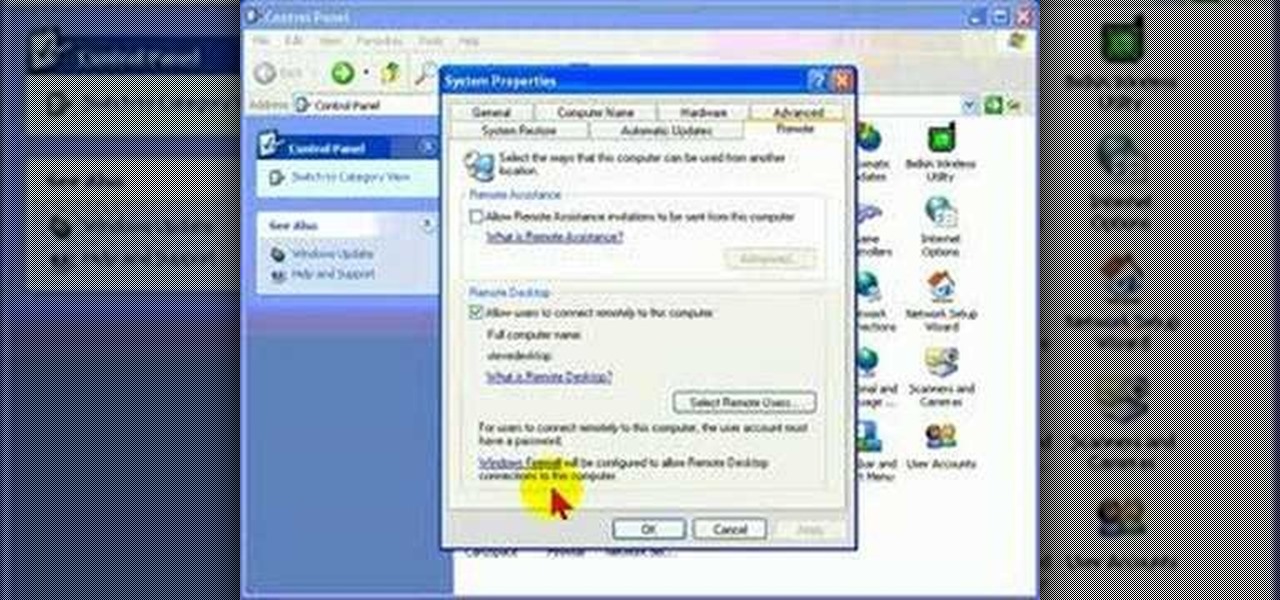
Remote Desktop is a feature of Microsoft Windows, that allows you to access your PC from anywhere in the world, and use it as if you were sat right in front of it.

Patti, the Garden Girl, host of the national PBS show Farmers Almanac TV shows how to brighten up your home and keep it secure with climbing roses.

The half blood knot with a tuck is similar to the improved clinch knot. The half blood knot with a tuck is a multi purpose fishing knot. The half blood knot with a tuck provides one good method of securing fishing line to hooks, lures, or swivels.

The improved clinch knot (overhand knot variation) is as the other clinch knots a multi purpose fishing knot. The improved clinch knot provides one good method of securing fishing line to hooks, lures, or swivels.

Protecting a new or young tree by staking it enables it to grow the strong root system it needs to secure itself in the ground. We will showyou how to stake a tree.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Windows 8, the latest version of Microsoft's flagship software has introduced the new Metro UI screen as a replacement to the classic Start menu. If you want to get rid of the Metro UI, or you want to get the Start menu back, follow the directions detailed in this video

In this video tutorial, viewers learn 4 different hacks that will make typing easier in Windows. Begin by clicking on the Start button and select Control Panel. Then click on Ease of Access Center and select "Make keyboard easier to use". Now users are able to configure the keyboard options for easier use such as: turning on/off the mouse keys, sticky keys, toggle keys and filter keys. All the features have more specific settings for self-adjusting to the user's liking. This video will benefi...

The EOS 7D has an accurate level display, which you can activate on either the read LCD monitor or in the viewfinder. See how to work the electronic display on the Canon digital SLR camera. This is great for getting a steady shot wherever you need it.

Looking to get into the weird world of circuit bending? In this four part video tutorial geared towards beginners, learn in thirty minutes how to circuit bend. Tools you will need include a soddering iron with innerchangeable tips (thin pencil preferred), thin sodder, hook-up wire, a wire cutter, a wire stripper, a drill with drill bits, plyers (needle nose included), and screw drivers of various small sizes. Other useful tools include cresent wrenches for toggle switches, jewelers files, & a...

There are tons of quick pop up tents available nowadays, but the classic A-Frame tent still remains one of the most popular. A-Frames are those classic tents with the spikes in the ground that hold it up. They take a little more effort to erect but they are perfect for backpacking or short camping trips.

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

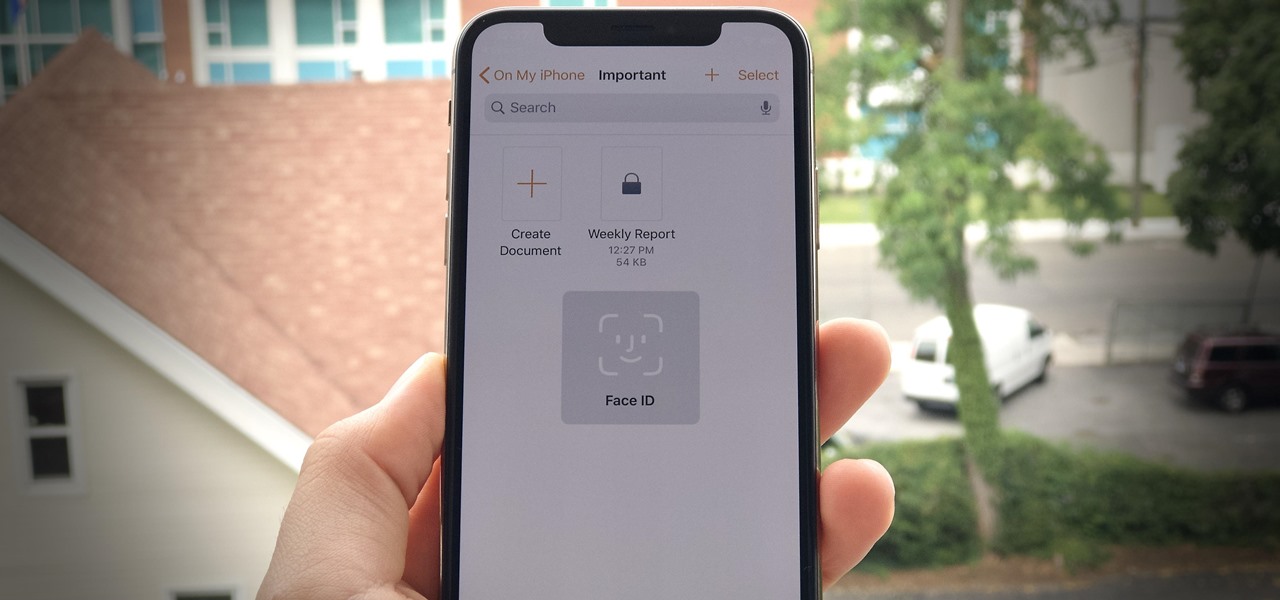
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

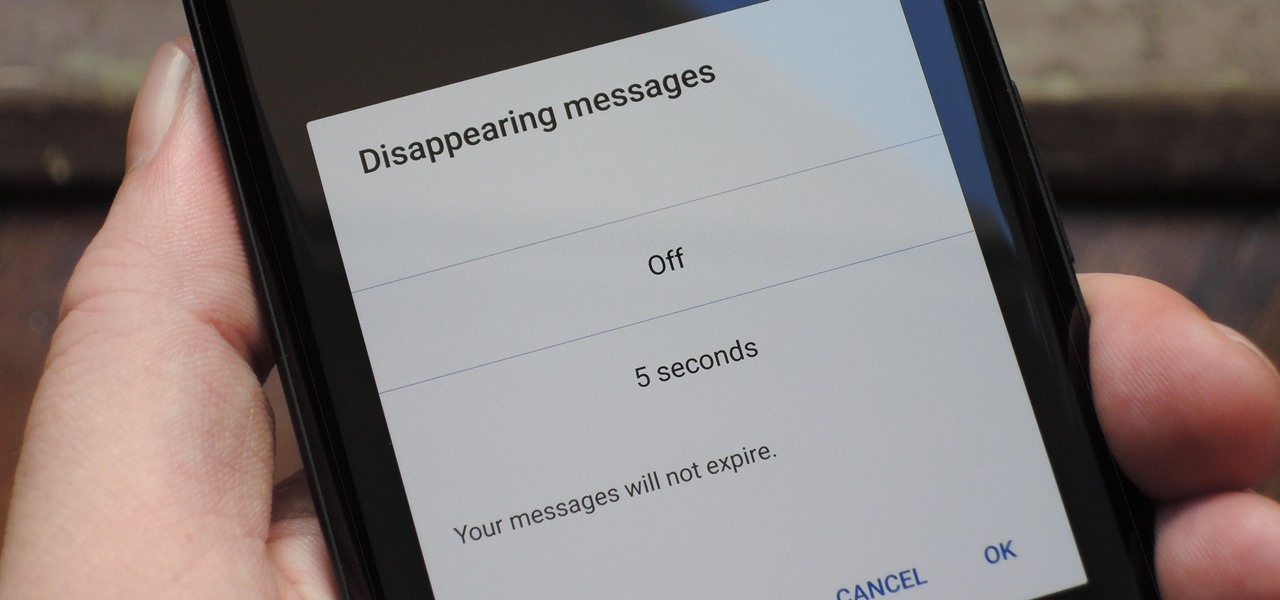
With Signal's class-leading end-to-end encryption, you can be sure your messages will remain secure as they travel to the recipient. However, once the message arrives, its privacy is completely dependent on the receiver, who could share it anywhere if they wanted. To patch this vulnerability, Signal added disappearing messaging.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

While it's a more secure platform for messages and calls, Signal's job isn't to prevent unknown users from contacting you, so you run into the same issues you would with a regular phone number. People you know that you don't want to talk to may try to strike up a conversation and you'll still get spam messages. Luckily, it's easy to block these suckers.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

Take a look at this new and contemporary Prom Bun Hair Style which is super cool and exclusive to adorn. Its over the top style has a unique and sophisticated appearance which appends a ritzy accent to your urbane persona. Try out this style following this simple tutorial. Step 1: Comb Your Hair to Make Them Smooth and Tangle Free. Once Done Gather All Your Hair in a

Mermaid Braid Hair Style Tutorial For Beginners!!!!
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.