Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.
Google's hard at work beefing up their new Google+ social network, and while they continue to improve new features like Circles and Hangouts, they haven't lost track of their other online features already widely in use. If you're already a part of the Google+ project (currently closed to invites right now), you've probably noticed the changes in Picasa Web, but Gmail has been getting some great updates as well—and you don't have to be in the Google+ network to use them.

Check out this Do It Yourself (DIY) RV maintenance and repair video to learn how about RV battery maintenance. Know how to do it to keep your batteries running strong in your recreational vehicle with this RV tutorial video.

Sometimes you will want to add fringe to your knitted scarves. Follow the steps below for an easy way to make fringe.

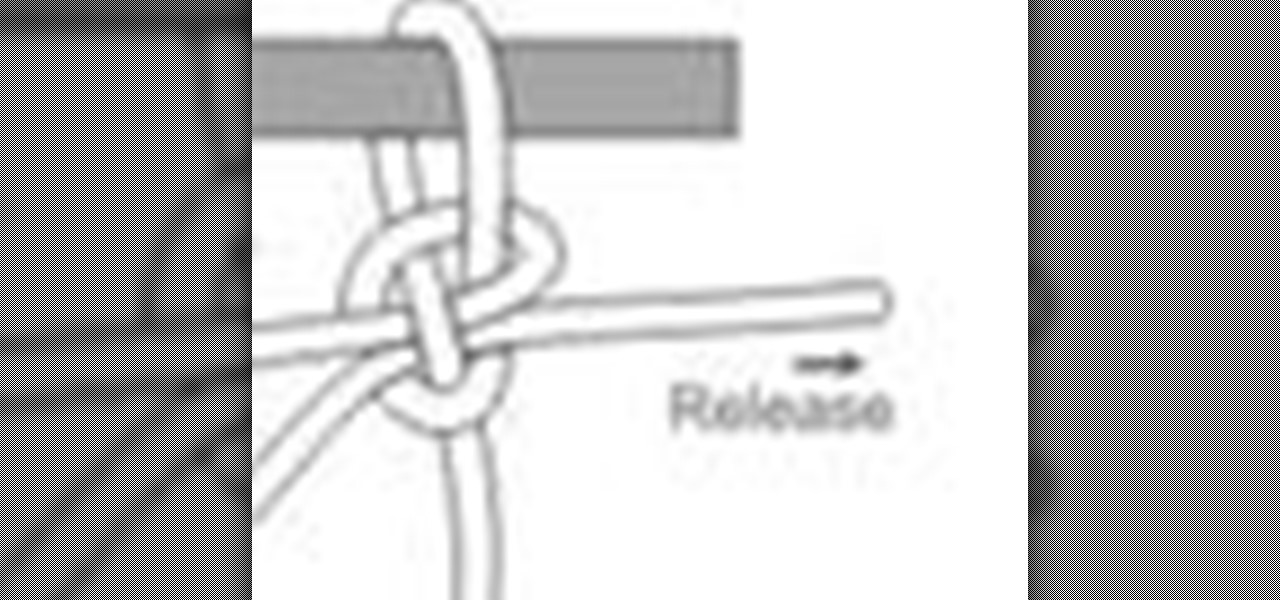
The Palomar knot is a powerful fishing knot, used to secure fishing line to a fishing lure, snap or swivel. It's great for all kinds of light fishing lines, especially braid, which won't pull out of this knot. It's retains almost the full amount of original strength of the line. Wade Bourne of MyOutdoorTV will show you just how to tie the Palomar knot.

New to eBay? Don't worry, setting up an account and buying and selling doesn't take that much effort at all. Everyone who has an Internet connection has at one point come across eBay, to find the perfect gift for their loved ones, to find the cheapest deals on plasma televisions and computers, or to get rid of their dusty, old record album collection in their web store.

You just bought a new Chrysler Jeep Wrangler from Mopar, but you don't know how to use its soft top, what do you do? Watch a video tutorial, that's what.

You just bought a new Chrysler Jeep Wrangler Unlimited from Mopar, but you don't know how to use its soft top, what do you do? Watch a video tutorial, that's what.

Ever wonder how to tie the rapala fishing knot? Wonder no more. Watch this instrucional knot tying video and find out. The rapala knot is a popular method to tie a lure (such as a rapala!) to a line such that it can move freely and unimpeded by the knot. Essentially the same as the non slip mono loop, the knot has one more step in it's making. Whether this makes it more secure is still up to debate. It does make it slightly more difficult to tighten down neatly, but with practice it can be do...

The mooring hitch knot for boating is a more secure knot than the better known (and easier to tie) slippery hitch boating knot. The mooring hitch knot holds fast while under tension yet can be released quickly with a tug on the free end. Despite it's name, this is a temporary boating knot and not to be trusted to moor a boat or anything else of value! Hope this knot tying instructional video helps you perfect your mooring hitch boating knot. Enjoy! Tie the mooring hitch knot for boating.

Watch this instructional video to learn how to perfect your rolling hitch knot for boating. The rolling hitch knot is a secure and easy to tie method of fastening a rope to a post. The rolling hitch knot holds firmly in the direction of the standing line. Not for use by climbers though, just boaters! Pass this helpful knot tying tip along to your friends. Tie the rolling hitch knot for boating.

Watch out for this popular knot - the square knot for boating. It is including here as much as to warn you of its pitfalls as to show the proper way to tie it! The square knot is an easy to tie knot that is good for securing non-critical items. It should not be trusted to join two ropes together or to hold down something that absolutely has to stay put. This knot will capsize or jam under load and will also untie itself under movement. This knot tying instructional animation will help you hon...

The figure eight follow through boating knot is one of the strongest knots. (also can be used for paddling). It is generally rated at 70% - 75% of rope strength. Due to it's strength and the fact that it is easy to visually inspect, it is commonly used by climbers as their "tie-in knot" - the knot that connects the climber to the rope. It forms a secure non-slip loop at the end of a rope. For even greater security, finish the tag end with a backup knot such as one side of the double fisherman...

Watch this boating instructional video to learn how to tie the double fisherman's knot. The double fisherman's knot securely ties two ropes together or can be used to tie the ends of rope or cord together to form the loops. Another use for this knot is to make another baoting knot more secure by tying this knot with the tag end of the rope behind another boating knot, a practice common to mountain climbers. In that case, you are effectively tying one half of the double fisherman's boating kno...

Watch this instructional video on tying boat knots, specifically the clove hitch boating knot. This is a simple all purpose hitch. Easy to tie and untie, it holds firmly but is not totally secure. Make a turn around a post with the free end running underneath the standing part. Take a second turn around in the same direction and feed the free end through the eye of the second turn. Pull the clove hitch knot tight. Voila! Now you know how to tie the boating knot known as the clove hitch knot. ...

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

In Obstetrics and Gynecology (OB/GYN), doctors deal specifically with the female reproductive organs, which means a lot of visual inspection of the vaginal area. Whether you're a doctor, surgeon, nurse, or nursing assistant, knowing how to properly drape a patient is detrimental to the patient feeling protected and secure with the hospital staff, along with having some privacy. This video will cover different types of draping techniques.

Ringtones and text tones can be annoying, so my iPhone is almost always set to vibrate on silent mode. Unfortunately, that causes me to miss phone calls and text messages when the device isn't in my hands or pockets. While I hate missing alerts, I'm still reluctant to switch to ring mode — and that's where another iOS and iPadOS feature helps out.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Over the past few days, we've learned a lot about Samsung's upcoming Galaxy S9 and S9+ smartphones. In addition to a full list of hardware specs, we have complete renders direct from renowned leaker Evan Blass. Of course, Samsung always has a few surprises up their sleeve, and today, we have some new information about the facial unlock method arriving on the S8.

As the Samsung world anxiously awaits an official Android Oreo update, some Galaxy Note 8 users are waking up to find their devices have jumped the line. Are you one of them?

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

The new iOS 11 was just released by Apple, and you can install it right now. Overall, it's got some great features, but how does it fare battery-wise on your iPhone? And how can you increase daily battery life for more juice and less charging every day?

The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest browsers on the market.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

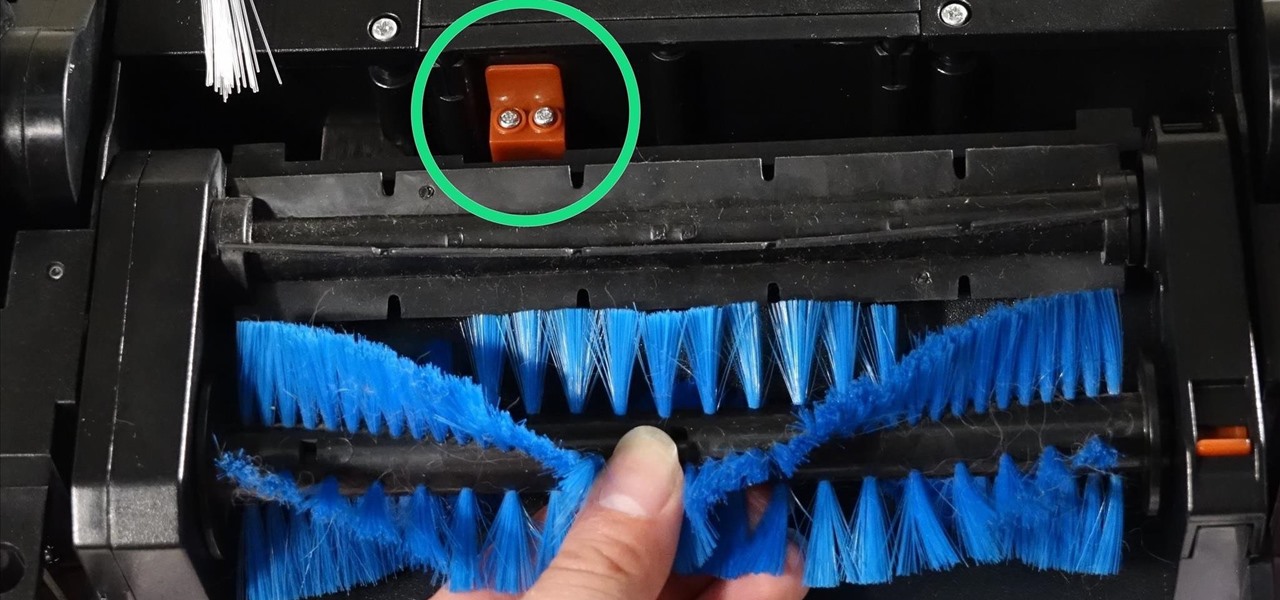
One of the quickest repairs for bObi is replacing the main brush motor. To do this, you'll need a Phillips head screwdriver and a replacement main brush motor.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

With the new year just around the corner, it's a time we all reminisce about the year that was. In the midst of families fighting over white elephant presents and the financial stress that comes with holiday gifting, you may also be dealing with the stress of hosting parties and get-togethers as well as the decorating that goes with it.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.