This video by repairs universe shows viewers how to replace the battery in the 2nd Generation iPod Touch. The tools you will need for this project include safe-open pry tools and a small phillips head screwdriver. To begin, remove the screen by releasing several clips that hold it to the frame using the safe-open pry tool. Run the tool between the case and the glass along all edges. Gently pull glass off and pry off the digitizer. Next, remove the small screw in the upper corner, lift up the ...
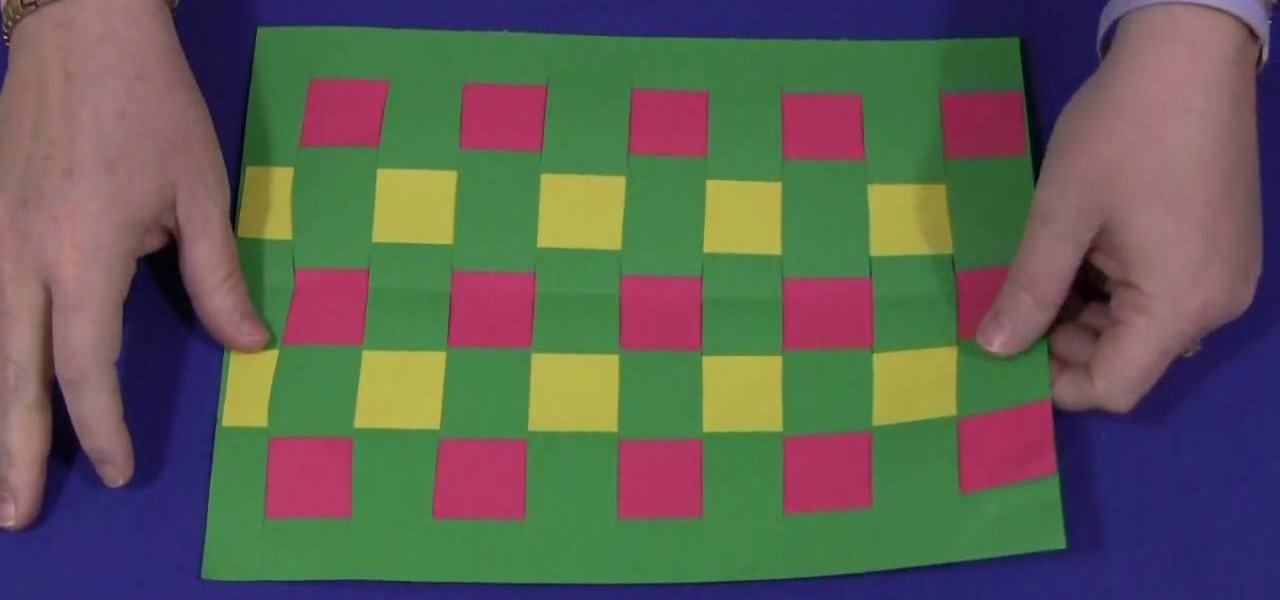
This is a project to keep your kids entertained. It is also a great way to practice hand eye coordination and motor skills. The materials that you are going to need are; construction paper and something to cut the paper with.Depending on the age of the child you can use 3 colors or more for older children and 2 colors for the younger children. Color choice is left up to what the child wants.To get started take a full size sheet of construction paper. Fold this paper in half length-wise. Take ...

The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new image" in the top tool bar. A new window will drop down, where you choose what you want to save the new image as. Give it a name, and choose the size you want it to be. Moving down, choose the encryption you want to use ...

Cute Girl Hairstyles shows you how to create a French braid hairstyle for your hairstyle. Firstly, divide the long hair into two parts with a zig-zag parting on the top of the head. Keep one half of the hair in a ponytail to keep it out of the way. Wet the hair down, and take a small section of the hair. Section that part into three and repeat. Cross the first piece with the second piece, and then cross the third piece over (braiding). Pick up hair and add it to the left lock and repeat. You ...

The Trilene knot is a multi-purpose knot that can be used in fishing to attach hooks, swivels and lures. This is a great knot because it resists slips and failures.

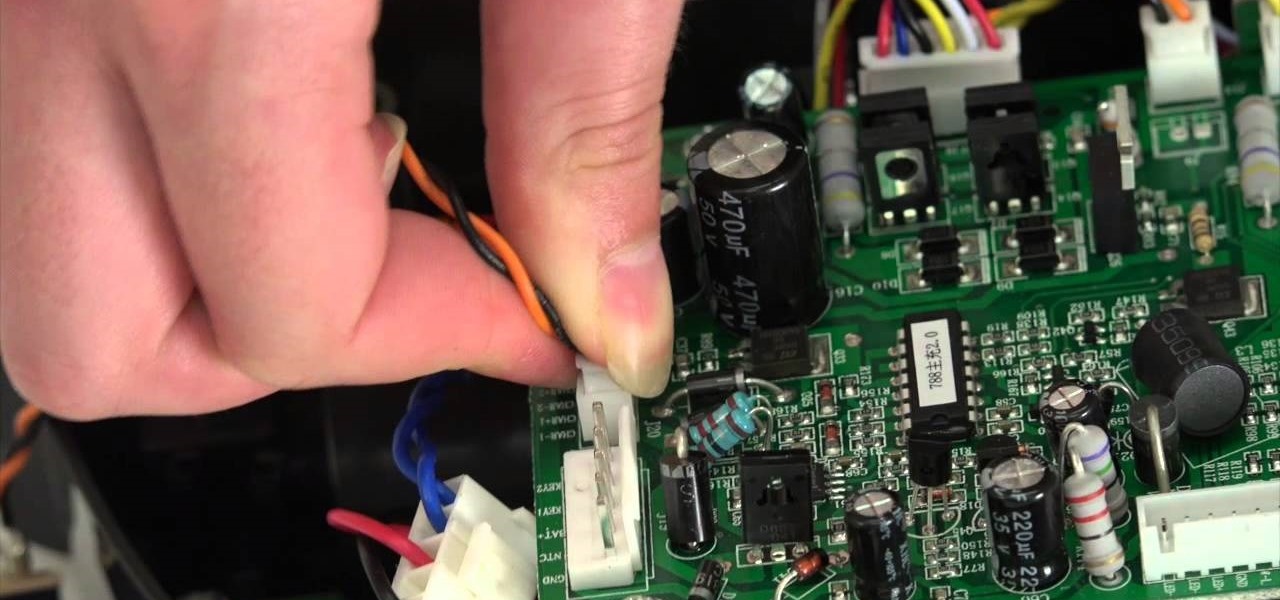
This video describes how to solder a wire. The first thing you have to remember is that the wires should be cleaned, shiny, and bright. Then trim about 1/2-inch of the insulation of the wires and then make a secure mechanical connection. Next, put some soldering pencil clean and shiny 60/40 rosin core solder. Do not use 50/50 core solder. Start by making sure that the soldering iron is tint. Put the soldering iron underneath the joint. Heat tends to rise and then touch the solder to the joint...

Clean out the empty bottle that you are going to use. You can use a white dish-washing soap bottle or a cleaning agent bottle. Just make sure it is empty and clean. Use the pen to draw a wide rectangle that measures 3 inches long by 1/4 inch wide onto the bottle. The teeth you are making are going to stretch from either side of your canine teeth above and over your two front teeth. This will help them be more secure. Draw this onto a part of the bottle where it is curved. Draw two vampire tee...

See how to make a very tall, simple, yet elegant centerpiece for weddings and other events. You first need a tube and a base that it will fit into. Placing the tube in the base, use a hot glue gun to secure the tube into the base. You can then fill up the balloons with air using an air pump and tie pairs of balloons together. Twisting together four balloons, place the cluster of balloons around the base of the tube. Repeat with an additional 8 balloons and place this cluster at the top of the...

This video shows you how to remove and replace a sink basket. It's real quick and very efficient if you have a new sink and an old basket. Here are the steps on doing this.

Learn how to make a sword out of cardboard with this video. Materials:

This video tutorial shows you how to install a glass vessel sink or countertop. First you need to make sure that the glass vessel sink or countertop has all of the pieces needed and that none of the pieces are scratched or broken. You then need to place the mouthing ring on the countertop where the sink is going to go. Make sure that the rubber side is facing down. Then carefully set the sink on the mouthing ring. You must then take off the tail piece of the pop up drain. Take off the ridge a...

Digidesign has transitioned all of their plug-in software copy protection from floppy drive based key disks to copy protection authorizations that reside on the iLok technology provide by PACE. The following is some information about iLok technology.

This instructional pet video shows a good way to introduce your pet rats to water. However, it's important to understand that some pet rats will just not like water. Your success will vary depending on your individual critter(s). Watch this tutorial video to learn the best methods of approach.

Whether you're using your phone's map to navigate or entrusting your passenger with the responsibilities of the mobile DJ, your phone needs a secure place in your car. And if it could charge while it's there, that's great too. The Naztech Smart Grip Wireless Charging Car Mount is exactly what you're looking for if you need a place to keep your phone secure, charging, and able to be used when it's safe to do so. Right now, this adjustable phone mount is on sale for $39.99, an 11% discount.

Google dropped several of the Pixel 4's more gimmicky features in favor of perfecting the basics on the Pixel 5. While you probably won't miss Motion Sense or the Assistant squeeze gesture, you'll definitely like the extra battery they packed into the space those features once occupied. Almost 50% more battery, actually.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Though more well known for their OLED displays and advanced cameras, Galaxy phones like the S8, Note 10 & 10+ and S10 series are a force to be reckoned with when it comes to audio. In fact, flagships from the S9 on up feature AKG-tuned stereo speakers, along with a slew of software enhancements that make listening to music a truly pleasurable experience.

As much funding as Magic Leap has secured, another round of funding will still catch headlines. However, the latest funding solidifies the company's strategy for succeeding in the consumer segment of AR.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

Well this law was passed... Our privacy is slowly being pulled away from us. But I'm certainly not going to let it stop me. We'll just have to take more secure measures. If You Use Tor Browser, The FBI Just Labeled You a Criminal.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

In an effort to prevent drones from being hacked, DARPA has been developing an "unhackable system," and seems to think they're almost there. The development team "proved" mathematically that their kernel was unhackable, and they hope to use it for more than just drones (power grids, cars, phones, pacemakers, etc.).

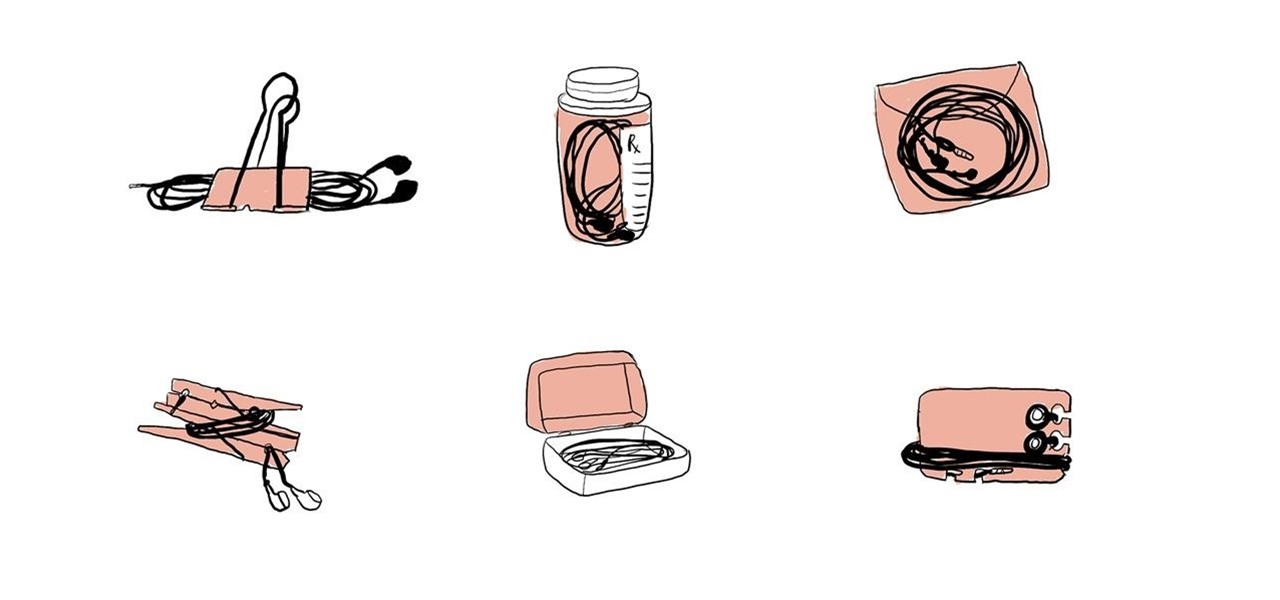
If you always carry earbuds with you in your purse or backpack, you can use simple household objects to prevent the cords from tangling up into knots.

The guide will walk you through a power switch replacement on a bObsweep Standard or Pethair. It includes:

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

Lorrie Faith Cranor: What’s wrong with your pa$$w0rd? | Talk Video | TED.com.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

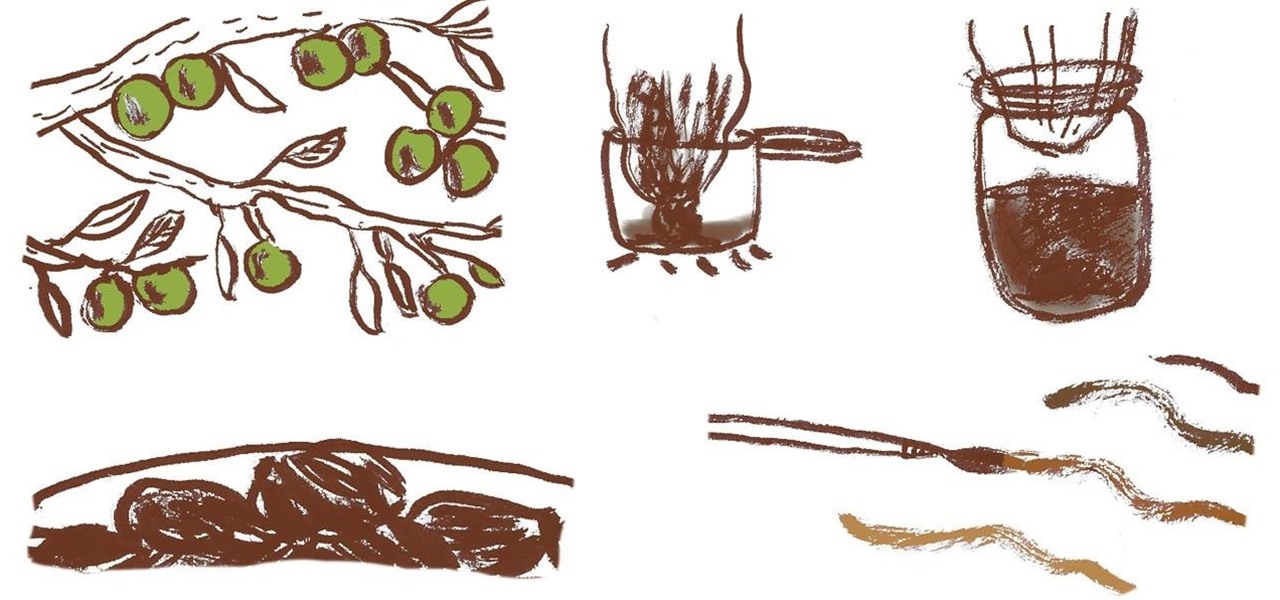
Using black walnuts, boiling water and a lot of time, you can make your own beautiful shades of deep dark brown to black ink for your next drawing, calligraphy, or wood craft project.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.