There are countless mods and apps for Android devices that give them an iOS-style look, but maybe it's about time we take some notes from Android, especially when it comes to the iOS 7 lock screen.

The sovereignty that's granted when we jailbreak our iOS 7 devices can only be described with one word—liberating. With this freedom comes countless themes and apps that let us manipulate our devices to really own them and turn them into something that is truly ours.

Here we go again, softModders, it's time for another awesome tweak for your iPod, iPhone, or iPod running iOS 7. Have you ever felt like changing your lock screen with a custom text instead of it saying "slide to unlock"? Why shouldn't we be able to edit this? We're not given much freedom as it stands with our Apple devices.
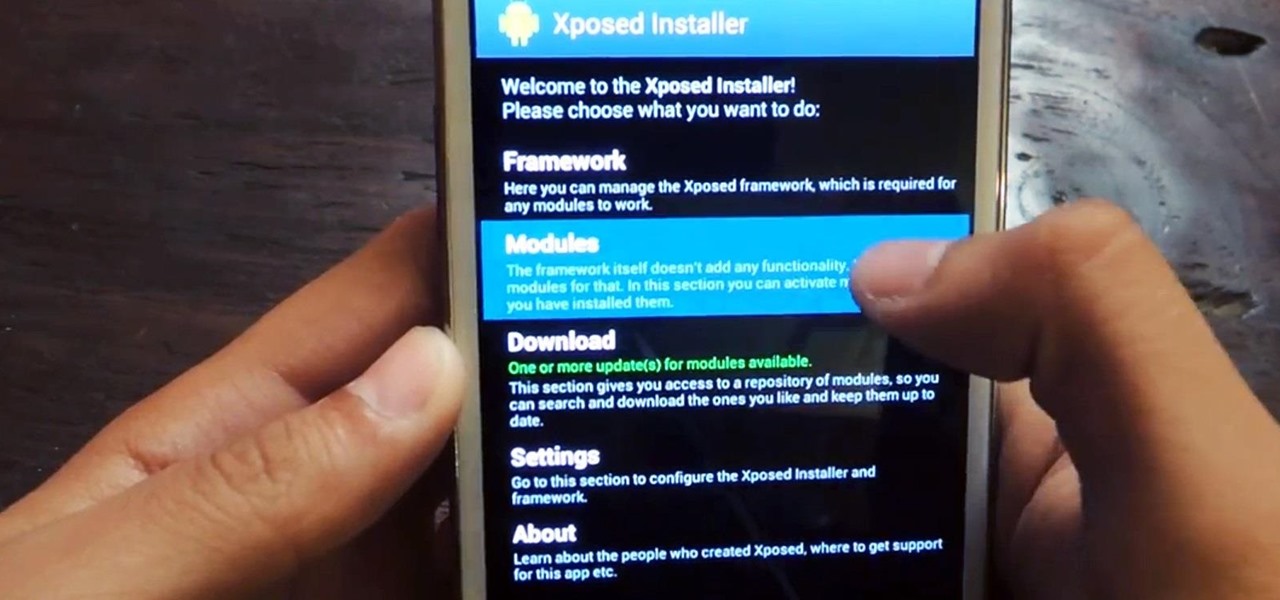
Android's deeply customizable platform has long been the attraction for those of us looking to make our smartphones more unique, but that doesn't mean that it's always easy. Flashing mods and installing custom ROMs can be difficult at times, as well as dangerous.

Whether you're trying to get an unconventional angle or just want to include yourself in the picture, there are plenty of times when a remote trigger can come in really handy. Of course, if you want to buy one, you have tons of options. But if you already have an Xbox 360 headset, all you have to do is plug it in. YouTube user Gurnarok accidentally found that by plugging his Xbox headset into his camera's remote port, the on/off toggle triggered the shutter release and flash.

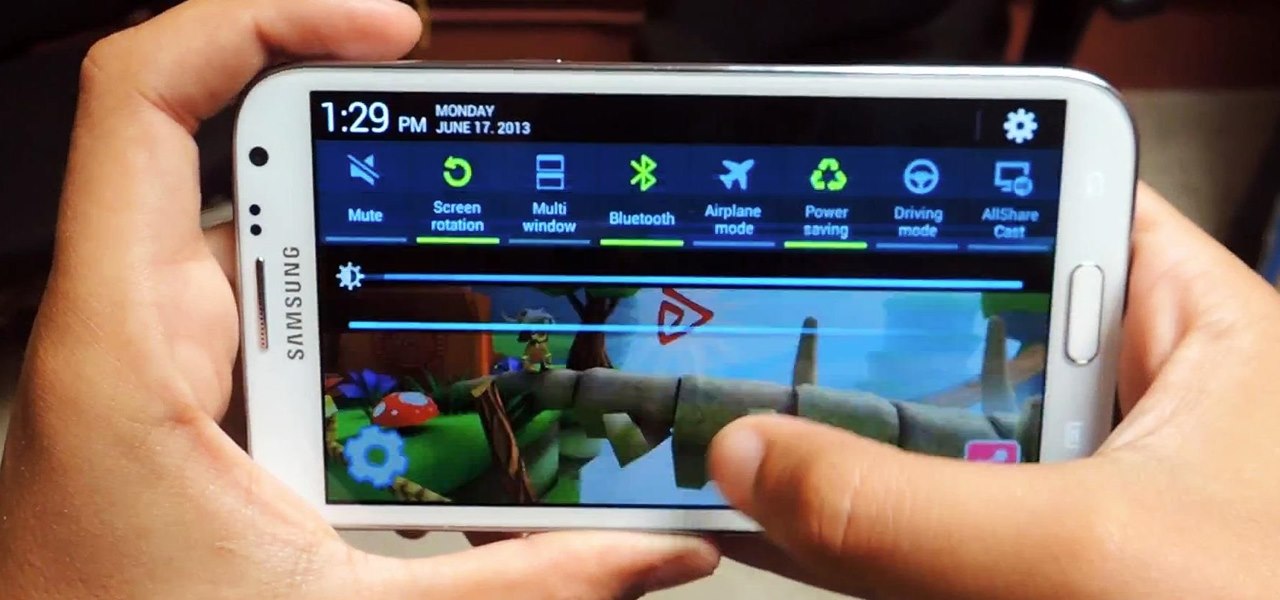
Personally, my favorite new feature in iOS 7 is the Control Center. With it, you can very quickly and efficiently access popular and much used settings, such as Wi-Fi, Bluetooth, brightness and more—all with one simple swipe.

The dryer’s idler pulley provides tension to the dryer’s drum belt so the belt won’t slip when the drum is turning. It can become faulty over time due to increased friction. If your dryer is making a squeaking or squealing nose then the idler is probably faulty. Replacing this pulley is a simple project. Repair your noisy dryer with this step-by-step tutorial!

Although the Samsung Galaxy Note 2 is a speedy device, one feature that feels a bit slow is swiping down from the Status bar to see the Notification tray when I'm using a full-screen app. When a full-screen app is open, I have to swipe down not once, but TWICE, on the upper portion of the screen in order to bring down the Notification tray.

I know I can't be the only person whose socks go missing in a shroud of mystery, but I'm determined to catch the sock-thieving gnomes in the act. While I have my suspicions, I can't quite prove it. Sure, I could drink a load of Red Bulls and never sleep, guarding my socks—but that's just crazy right? Luckily, I've found a way to set up my phone to catch the culprits.

When it comes to multitasking, the Samsung Galaxy Note 2 is the master of all smartphones, thanks to its huge screen size and many features. The phablet's display compliments its multi-window mode, which lets you run two apps simultaneously side by side Another cool feature is floating apps, which makes multitasking even better. So, with all of these cool features, what else could possibly be added to the Note 2's arsenal that it doesn't already have?

While the phenomena of viral videos and internet celebrities are relatively new, it seems like there's a new one every other day. Sometimes they're funny, other times they have a social mission, like Kony 2012, and sometimes they're just videos of cats jumping in boxes.

If you've recently jailbroken your iPhone 5, there's a likely chance that you're overwhelmed by the huge numbers of themes, add-ons and tweaks littered throughout the Cydia directory.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

A common problem on bumper covers is that the tabs that attach the bumper to the car get broken. This is critical, as this is what secures and aligns the bumper cover. Many times, a broken tab is all that is wrong with the bumper cover. With the cost of these plastic parts $200 to $700, the replacement cost can break the bank.

The biggest problem with having a lot of gaming systems lying around the house is the clutter. Each device has several cables and adapters that need to be plugged in somewhere and it could leave your gaming area look something like this... Not a pretty sight, huh?

Not sold on Apple's iPhone claims of battery performance? I will show you some simple tweaks and tips to reduce that rapid battery drain and extend the use of your iphone between charges -free.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

Here is how you can build a frame for your MEGA SOLAR SCORCHER in under an hour, and for less than $8!! This is effectively a 4 foot magnifying lens that concentrates insane amounts of heat from the sun. What would you do with all this free solar power? My design for this custom "Scorcher Frame" is easy to use, and incredibly cheap to make, as you can see in this step-by-step video.

Spices are a necessary ingredient in any kitchen. It doesn't matter how good of chef you are—without proper spices, your food will always fall flat.

In this tutorial, we learn how to make a ribbon bow with the help of toothpicks. Start with a full twist on your ribbon, then place it behind the toothpick and hold it in place with another toothpick. Next, make another loop and then do a front loop with a half of a twist. Now, secure those in place with toothpicks and do three side loops with half twists. Secure them with toothpicks, then continue with larger loops made with half twists. When finished, hold the ribbon in the middle with your...

You see it in the movies all the time. A character on the phone doesn't like what the other person is saying or telling them to do, or they just don't want to talk to them anymore, so they fake bad reception and cut the call off. In real life, it's pretty easy to tell when someone is doing it, and there are better ways to end a call abruptly so that it looks like you didn't hang up on them.

Dark mode helps battery life and low-light viewing, and it also just looks better. That's why apps like Facebook Messenger, Twitter, and Chrome have adopted dark themes, and it's why both iOS and Android have added a system-wide dark mode. But what about WhatsApp?

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

Today's pollution, hectic lifestyle, inadequate sleep and no time for pampering can leave your skin lackluster resulting in drying skin and making dry skin drier ultimately causing the early appearance of wrinkles and aging. A good fruit facial helps relax your skin from deep inside and the proper messaging gives it a rosy glow by increasing blood circulation imparting your face with a luminous glow. These are even better because they are natural and chemical free unlike the artificial facial...

There comes a time in relationships when two people decide to move in together, and when this happens, you learn two things:

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

Last summer, Universal Pictures released the sequel to the popular 2010 animated film Despicable Me, bringing back everyone's favorite characters—the Minions. They're adorable, yellow, and they speak a gibberish "Banana Language." What's not to love? If you're planning on dressing yourself (or your kids) as Minions for Halloween this year, you'll be in good company. There are tons of costumes out there you can buy or make, and here are five of the best DIY options for you.

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

Originally made as portable convenience locks, padlocks are known for their cheap, simplistic and relatively secure design. Their construction is made up of a body, shackle and locking mechanism, with the shackle typically assuming a "U" shape to be easily linked to things like fences and chains.

Scrabble Bingo of the Day: CABRESTA [n/pl.] A cabresta (also cabestro or cabresto) is simply a lasso, a rope formed with a running noose that's used on ranches and Western plains for catching horse and cattle. Cabresta comes from the Spanish word halter, which refers to the headgear used for leading or tying up livestock and other animals. But halter also used to mean to hang someone by roped noose, which could be how it became popular as a term for a noosed lasso.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the target for many online predators, many of who are fully-grown adults aged 60 or 70. Here is the link to an article I found about it: Wizard101 Internet Predators