This video tutorial shows you how to securely empty your trash in Mac OS X. 1. Click on the top Menu on your desktop. 2. From the drop down menu, choose "Secure Empty Trash". 3. You will be then be prompted with a messaging stating items will be permanently erased from your computer. If you wish to continue click the "Secure Empty Trash". 4. Depending on the amount of files, the process may take a few seconds to a few minutes.

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

There's no need to pay for a pricey electrician for a light switch problem— you can try to fix it yourself. This video from This Old House explains how three-way switches work and shows tips for finding and replacing faulty three-way switches in your home. First, you need to understand the difference between the hot and neutral wire, the ground wire, and the traveler.

This video is designed to help deaf people, or those with hearing impairments, learn how to do basic first aid. Specifically, this video deals with sever bleeding and how to stop it, and is taught in sign language.

In this video from Lowe's we learn how to use a gas smoker. This tip comes from Lowe's. You can cook with a smoker anytime of year. He is using a gas smoker. Keep this away from siding. The fire source heats the moist wood chips, which release the smoke that flavors the food. You need tongs and a meat thermometer for sure. Before you cook for the first time, season the smoker by smoking some wood chips without food in it. He is cooking a pork shoulder which he uses a dry rub, wraps in plastic...

Place 2 Tbsp. oil in a wok or large frying pan over medium to high heat. Add garlic, galangal (or ginger), shallots, and chili. Stir-fry until fragrant (about 1 minute). Stir-frying Tip: Add a little water to the wok/pan when it gets too dry instead of more oil.

These videos show you how to use baking strips to make a better cake. Use caution when using baking strips, and watch your oven carefully.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

Everyone gets cut every once in a while, but sometimes those cuts can be more serious than expected. It could turn into severe bleeding, and there's a certain way to deal with this type of bleeding in a victim. How would you treat someone who was bleeding severely?

iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Standard notifications on Android are pretty intuitive, but the little popup toast messages that appear at the bottom of the screen can be a bit elusive. They come and they go, and that's about it. You can't long-press them to change their settings or even tell which app displayed them in the first place.

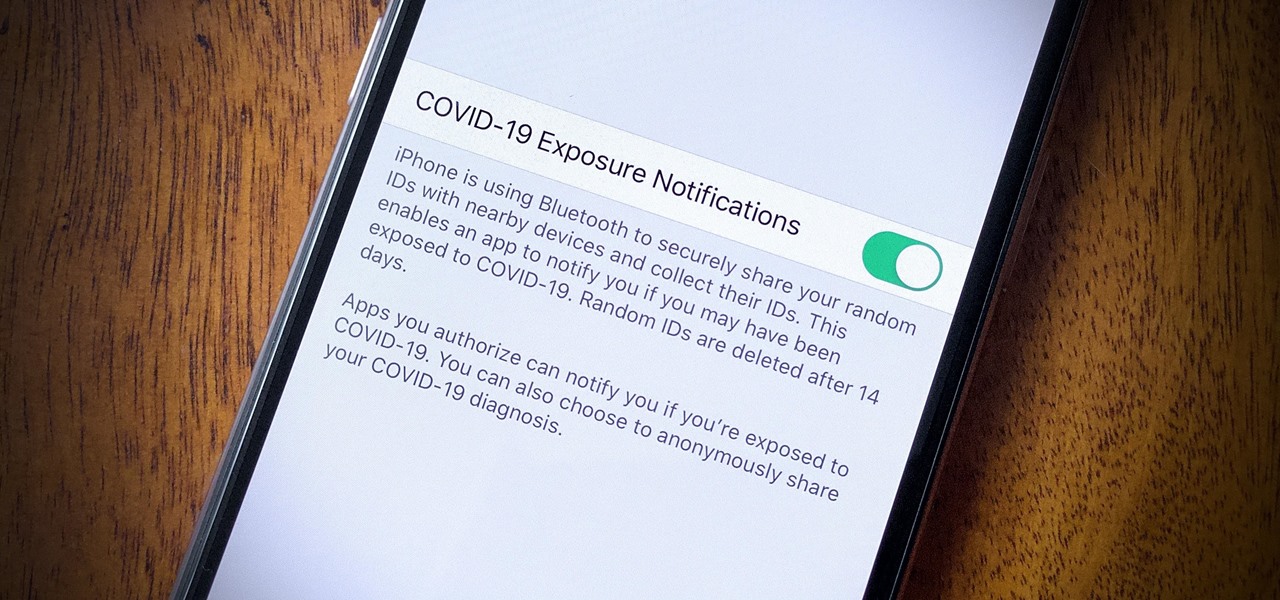
In iOS 13.5 and later, developers can create and release contact tracing apps for iPhone, which could help slow the spread of the novel coronavirus in the U.S. With these apps comes COVID-19 exposure notifications, which you may or may not want to receive. If you don't want to get these alerts, you can disable them.

When you're checking out photos and video on Instagram, its default bright white layout can literally be an eyesore, especially in dimly lit settings where the bleached UI feels blinding. Luckily, there's a really simple way to switch from the normal light mode to a dark mode look in the iPhone and Android app.

I already know what you're thinking: this guide is blasphemy. I am showing you how to turn a Galaxy Note 10 or 10+ into an iPhone 11 Pro Max. And while I'd usually agree with you, hear me out. How can you know you don't like something until you try it? So here is your way of trying out an iPhone using your Galaxy Note 10.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

In this video, Karlyn M. Campbell, an Information Technology student, goes through how to set up and secure a wireless network on a laptop. For a wireless network you will need your computer, a wireless router and its CD, and a USB wire. First the video goes through how to set up the router by using its installation CD. This video uses a Belkin router, and so shows the steps the Belkin installation CD takes the user through. The CD also lets the user decide which security settings he or she w...

Gather your hoop and supplies. Wrap the suede evenly around the entire ring. Wrap it either eight or sixteen times, depending upon your preference. Glue the ends to the hoop. Secure them with a clothespin until the glue dries. Make the web. Tie the nylon string to the suede. Make eight knots evenly dispersed around the ring. Keep the thread taunt between knots. Make a second row. Place each knot "between" the knots of the previous row. Continue in this manner until a small hole remains in the...

In this series of 4 podcasts, I will go over the major updates to Final Cut Pro version 6.0.2. In this specific episode, I cover the changes to the reconnect dialog box and also changes to how clips in the trash bin act.

Watch this video from This Old House to learn how to create a small deck. Steps:

Watch this video from This Old House to learn how to install a towel warmer. Steps:

Watch this video for instructions on making the Yukki Cross Artemis scythe from the anime / manga Vampire Knight.

By using sewing pattern Simplicity 4670, the author of this tutorial video takes you through the steps needed to produce a great shirt collar. First you should attach interfacing to one piece of the shirt collar. Here you will be using fusible interfacing and taking the facing to the shirt collar iron the interfacing to the wrong side of the fabric. Sew a guide line that is 5/8ths of an inch wide along the notched edge of the shirt collar's facing piece. At the dot markings of the collar clip...

When is a knot not a knot? When it's a grip. The knot outlined in this video isn't a knot per se but a way to wrap objects to increase their grip and also to store extra paracord. Specifically, this video demonstrates how to County Comm Micro Widgy Bar, which is a miniature pry bar. It’s made from hardened D9 steel and is around 3? in overall length.

Three hundred people die every year from carbon monoxide poisoning. Don't risk being a part of that statistic.

Shaun Alexander was an amazingly productive NFL running back. In this video, he takes some time to explain for young running backs how to hold the ball properly, protecting it from the defense and potential fumbles. Proper finger positioning and placing the body between opponents and the ball are both crucial elements.

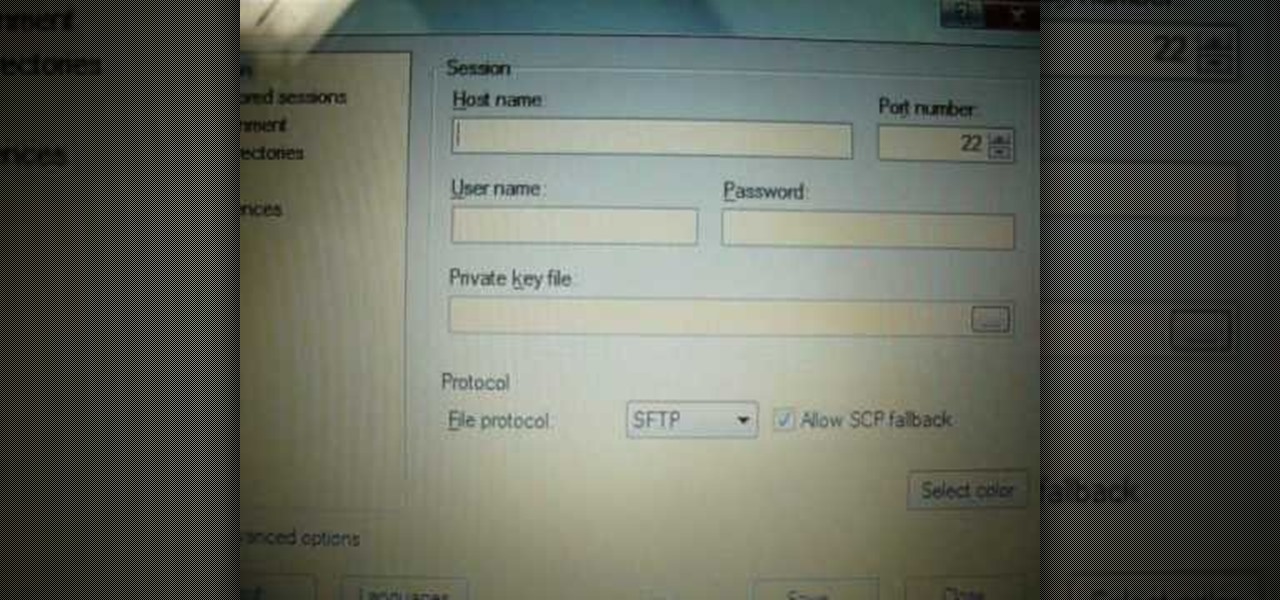
If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database securely via SSH tunneling. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a secure connection between a given MySQL database and the DreamCoder for MySQL, take a look!

Babies have no way of communication other than crying. = Touch is one of a baby's most highly developed senses at birth. Holding, caressing and cuddling your infant is crucial to helping her feel safe and secure. There are a number of tips demonstrated in this instructional video to help calm a crying baby. Watch this video child care tutorial and learn how to comfort a baby.

This video demonstrates how to install or replace a dead bolt in your door. Having a dead bolt lock gives you a added sense of security, because it is more secure than just the lock on the door handle.

The improved clinch knot… why is it improved? Well, the improved version of this popular fisherman's knot includes an extra tuck under the final turn. If you want to learn how to tie the improved clinch knot, just watch this video with Wade Bourne of MyOutdoorTV.

This Butterfly knot will accommodate a load in any direction, and is used mostly in outdoor and boating situations, but also could be used as a paddling knot. It's used for securing a loop or many loops in the middle of a rope. Great for mountain climbing and canoeing.

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to check car fluids properly.

Treat your guests to some wand-erful Witch's brew this Halloween. They'll be screaming for more! Follow along in this cooking how-to video to learn how to make Witch's Brew punch decorated with creepy spider ice cubes.

Learn how to tie the trucker's hitch knot. The trucker's hitch knot is one of those boating knots that once you learn it, you wonder how you ever got along without it! Use this knot to cinch down a load on you car top, boat, horseback, you name it. This combination of knots allows the line to be pulled tight as a guitar string. Tie off one end of rope. Lay rope over load to be tied down. Tie a slippery half hitch knot in the middle of the line to form a small loop. With the free end make a tu...

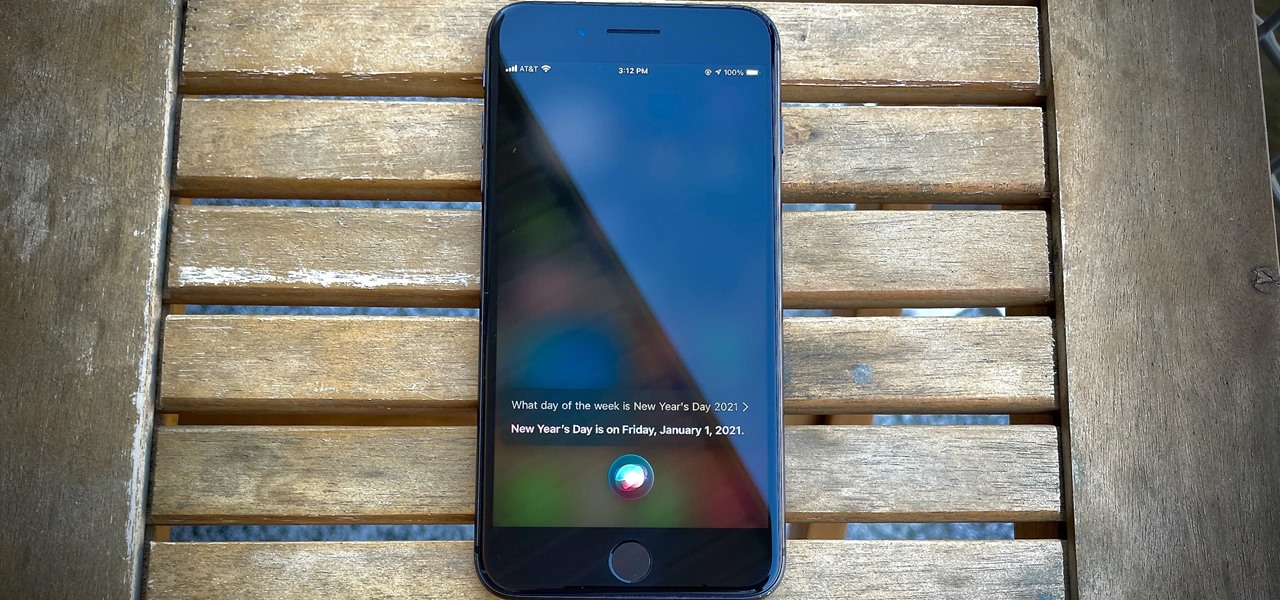
Full-page interfaces are so iOS 13. With Apple's iOS 14, alerts such incoming phone and FaceTime calls now appear as small banners instead. The same goes for Siri. Instead of using your iPhone's full display, Siri now exists in an unobtrusive overlay. But if you miss the focus that full-screen Siri used to bring, you're in luck because the feature still exists — it's just hidden.