Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.
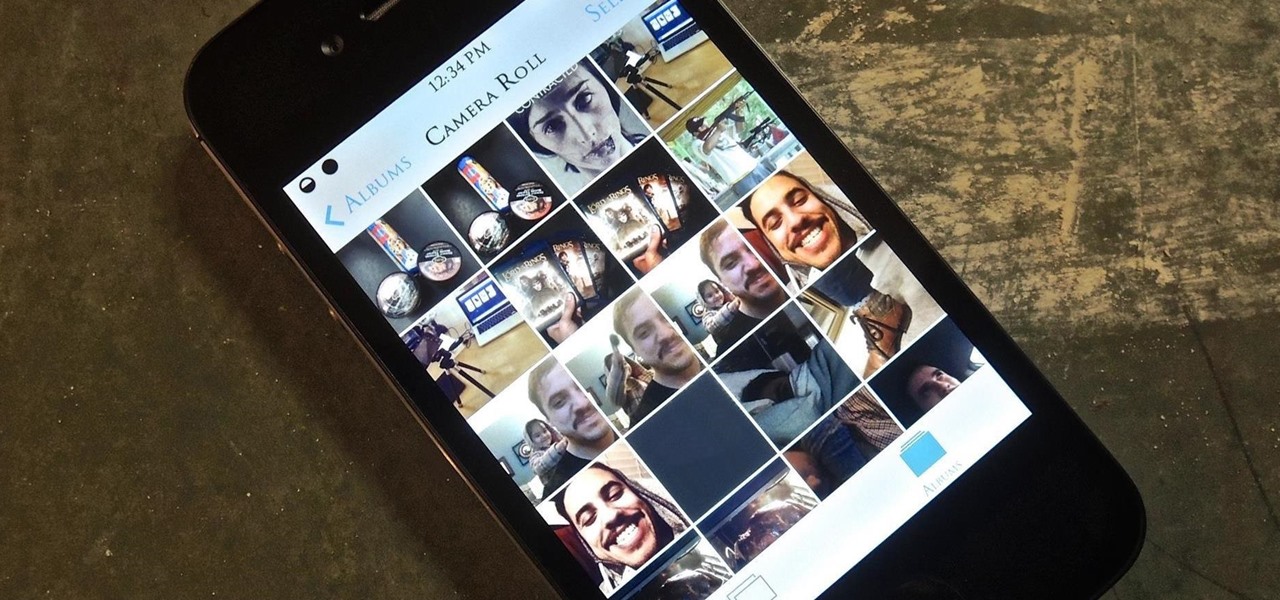
I have over 400 photos on my iPhone, and I don't even know where half of them came from. Scrolling through all of those pictures is a pain in the ass, but it's not nearly as bad as trying to actually find an old image. Organization is not my strong suit, so I'm definitely not the type to create new albums to sort through my 400+ photos.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

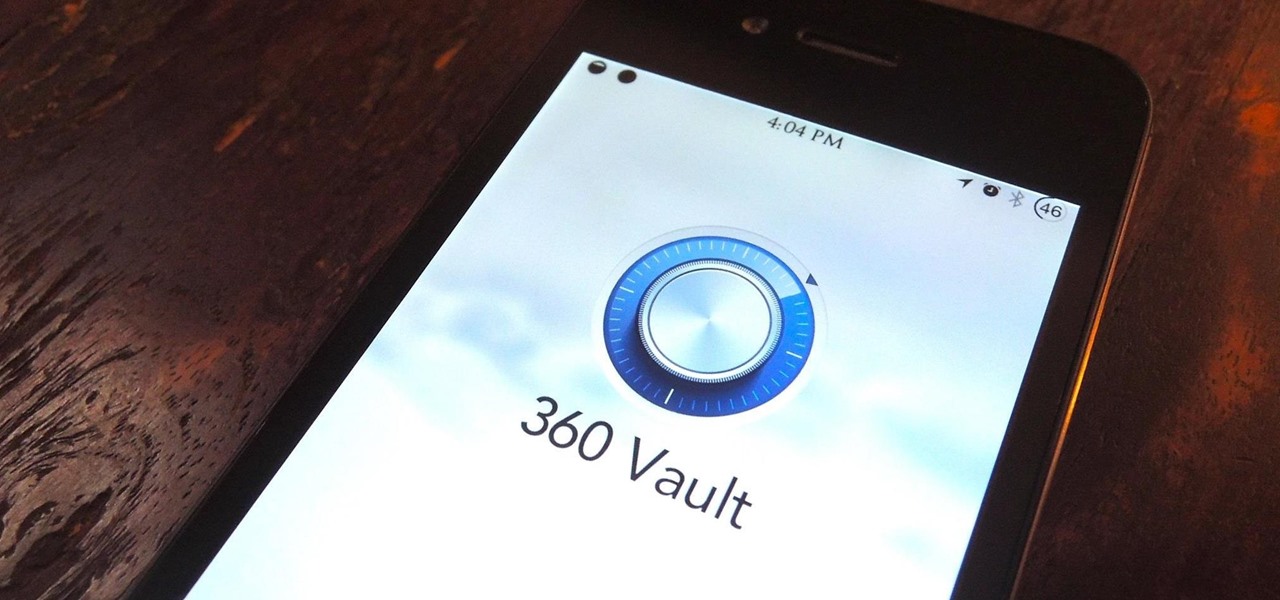
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

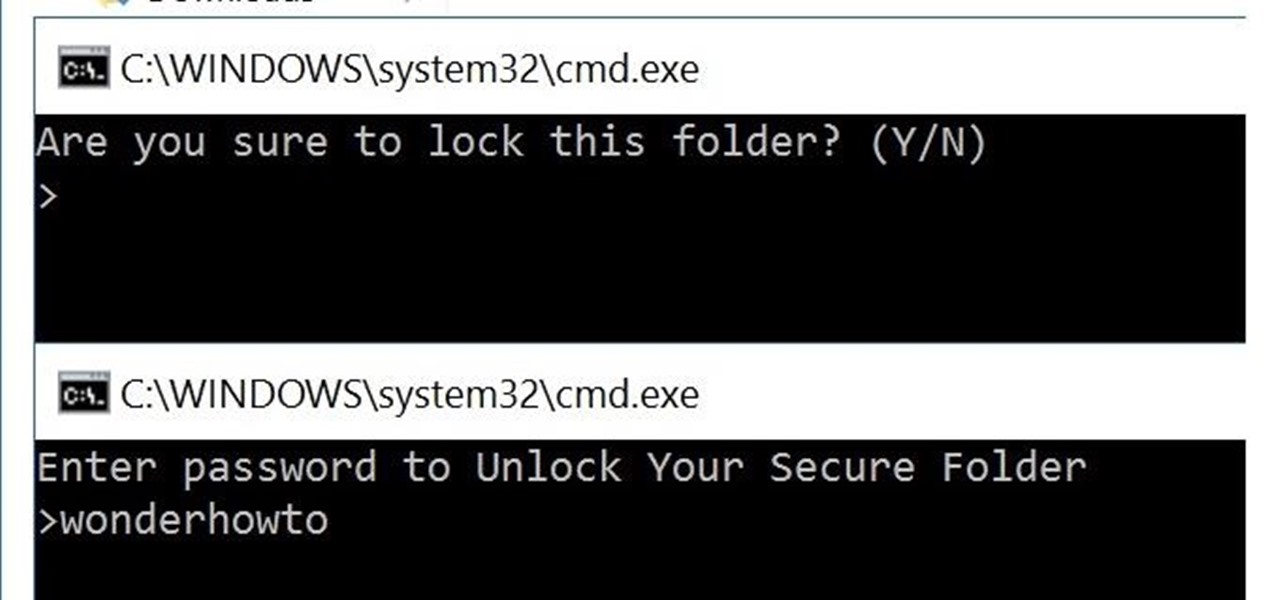
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

We will show you with easy step by step instruction how to create a beautiful edible apple swan. This swan is easy to create and can be done in under 5m. Makes for a great centre piece during a special dinner.

There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

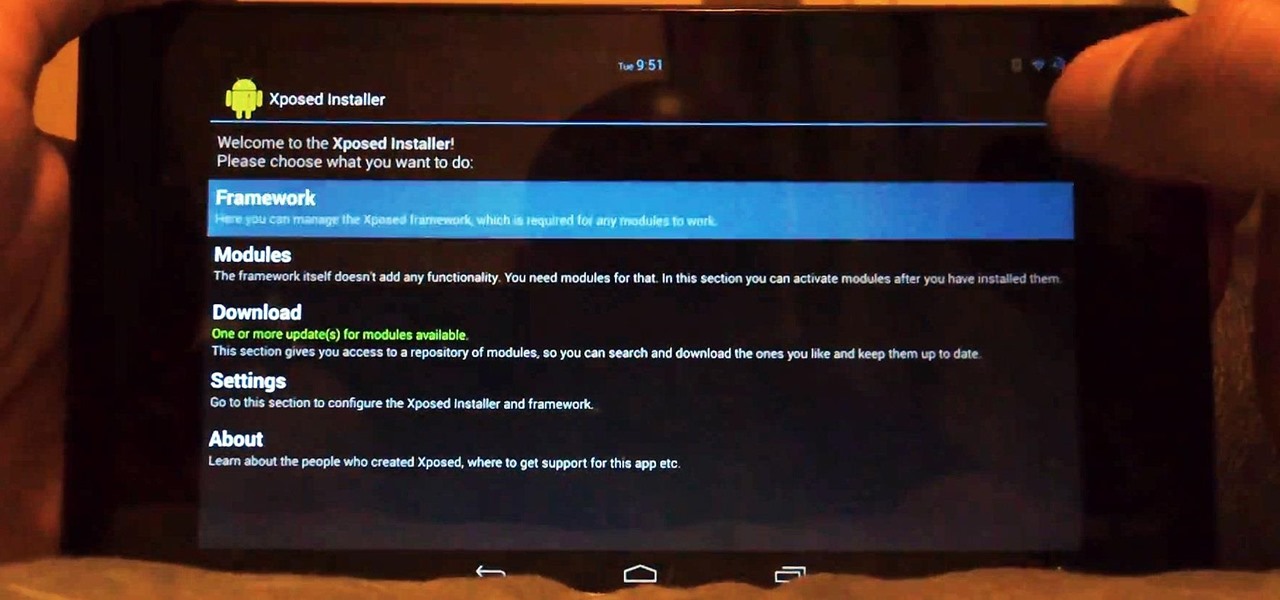
Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

The high limit thermostat can be found in gas and electric dryers and serves as a safety feature that helps to prevent the dryer from becoming too hot when it’s running. The thermostat is designed to shut off power to the dryer’s heater when the dryer vent is blocked or clogged. The high limit thermostat on your dryer is something that does need to be replaced from time to time. Fortunately, it is a job that you can do on your own with basic tools.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

You jump in your car and notice that is feels like it is slipping out of gear or shifting in and out of neutral. What could the problem be? One problem may be that the transmission fluid and filter need to be changed.

Wall framing. How to frame a wall. Whether you're re-sheeting an old wall or building a new timber frame wall, before you install the plasterboard or drywall, take the opportunity to have a really good think about what services or insulation qualities you might want to have in that space. There are issues to consider like electrical, plumbing, noggins for wall fixtures and insulation.

When the time comes to move home, the logistics of moving your belongings can easily become tiresome, tricky and even disastrous. However, with a little careful planning and foresight, the act of packing can be a simple process. The key to getting the most from your move is in efficiency, planning and care. Here, we take a look at the best ways to pack in order to ensure a safe and simple move.

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

At the recent DefCon conference in Las Vegas, researchers opened many of the top commercially available gun safes with simple tools like a straw or a paper clip, and in one case, just by shaking it a bit. The investigation began after the researchers, Toby Bluzmanis, Marc Tobias and Matt Fiddler, learned that certain Stack-On safes, issued to some law enforcement officials to secure their firearms at home, could be opened simply by jiggling the doorknob.

Have you ever wondered what sort of microscopic critters are floating around in your water? Well, you can find out with just a few bucks worth of materials and a laser pointer. Really. That's all it takes to build your very own homemade laser projection microscope, aka a water drop projector.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

Tethering your Android phone basically turns it into a mobile hotspot, allowing you to funnel a 3G or 4G internet connection from your phone into your PC or laptop via USB. As you might expect, phone carriers brought the hammer down in an effort to stop users from getting around the fees they charge to normally allow you to do this.

Jake von Slatt of The Steampunk Workshop kept breaking the rear glass panel on his iPhone. So, he ended up making his own gorgeous replacement out of brass to replace the standard Apple logo ones who kept getting. The only problem was that it made his signal strength super weak, so he figured out how to transfer the etching onto a glass back. Here's the basic rundown of how he accomplished this feat...

Did you know you can help protect yourself when traveling with a gun? No, not like that; and not in any way that's going to land you in prison. Simply by packing a gun, you can ensure that not only will your luggage be safer, but that the airline will make certain that it reaches its destination. Photo by Alamy

Paper towels are really cool. I like having them around for quickly cleaning up messes and what not. However, I do not have a stand or something similar for my paper towels, so it can sometimes get a bit taxing to pick up the roll and unravel it every time I need a towel.

Steaming food has a lot of advantages over other cooking methods. The gentle heat of steam allows for meats, such as chicken wings, to become more moist after cooking.
An amazing amount of news this week; new proposals and new agreements have sprung up. But so has our "need" to spread our presence. The military warns of another war, while 26 congressmen decry the use of drone strikes. Read on:

Willow Smith has what it takes to be a star, just like her parents, Will and Jada Smith, and her brother, Jaden Smith. But this Smith, at the tender age of 9, is quickly becoming a pop superstar and preteen trendsetter, thanks to her music video "Whip My Hair".

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a mouse.

Health, safety and security are three main issues which determine if your cruise is a successful vacation.
From Infowars: “Of course, at this stage Mr. Paul is little more than a distraction to Mr. Romney, and the two candidates are said to be quite fond of each other. Until now, Mr. Santorum had also been pinning some of his hopes on Texas, which, with its 155 delegates, has the most delegates of any contest to date,” writes Gerry Mullany.

Watch out Macs. Flashback is back. Variations of the trojan have reportedly infected 600,000 Mac computers around the globe, with about 57 percent in the U.S. and another 20 percent in Canada.

In this article, I'll show you how you can make your very own bullet/shell bottle opener. All you need is a .50 caliber deactivated round and some workshop tools!

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

In photography, using filters over lenses is a common practice and provides a great way to set the mood or to create an artistic image. The only problem is that they can be quite costly and there currently aren't many available for cell phones specifially. Fortunately, there is a simple solution to this, and all you need are everyday objects that can be found around the house. If you're a purist and don't want to rely on filters provided by camera apps, this is a great way to experiment with ...

The holidays are here and all of us here at Phone Snap hope you're spending them under a nice warm roof with some yummy food and great company! For this week's Phone Snap challenge, we want you to utilize your cell phone to capture some holiday spirit. Whether it be the gifts under the tree, stockings hanging over the fireplace, Christmas lights outside, or everybody gathered together wearing their favorite holiday sweaters—we'd love for you to share with us!

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

I've previously mentioned how saving browser passwords is a bad idea, but I never went into much detail as to why. Passwords that are saved in your browser can be carved out and stolen very easily. In fact, even passwords you save for instant messaging and Wi-Fi are vulnerable. Windows is very inefficient with the way it stores passwords—it doesn't store them in key-vaults, nor does it encrypt them. You're left with passwords residing in memory and filespace that's unencrypted.

Now we're getting to the kids who actually know what's going on. You're more likely to get enthusiasm and dare I say focus from grade school and middle school kids. Here's the lowdown: