You're sitting in your favorite café enjoying a hot cup of joe, then you open up your laptop or turn on your tablet computer to get to work, but as always you get sidetracked and head straight for Facebook. Someone just tagged you in a photo, so you check it out, then you see it out of the corner of your eye—your Facebook picture digitally displayed on the wall in a nice, neat digital photo frame.

Firesheep caused quite a stir when it was released last October, giving both hackers and non-hackers instant access to people's account information when on a public Wi-Fi connection. When logged into an insecure website on the same network as someone with Firesheep, you're giving them access to the cookies that keep you logged in. This is called session hijacking, and grants them easy access to your accounts, like Facebook, Flickr and Twitter. Now, there's an even easier way to do this—a mobi...

Designer Andrew Clifford Capener has made an alternative to the classic Scrabble board that celebrates the expression of typeface. It isn't in production yet, but Capener's set would offer tiles in a variety of different fonts:

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

Would you rather live far up in the trees? Or deep underwater? A Nevada family of scuba divers have built the ultimate childhood getaway: the Needham family's "Bubble Room" is an underwater fort that sits at the bottom of a lake in the Sierras. The room is an air-filled pocket, made with vinyl and anchored down by an octagonal framework of metal pipe.

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

It's no secret that Jimmy Kimmel is a SCRABBLE man. He hosted and won the SCRABBLE 60th Anniversary Celebrity Doubles Tournament (SCRABBLE Under the Stars), and for the last couple of years, featured the National School SCRABBLE Champs on his late night show "Jimmy Kimmel Live!".

Fishtail braids can be a little tricky, but the look is worth the effort. Divide the hair into two sections. In order for the hairstyle to look neat from the

The seated hammer curl using resistance bands is used to target primarily the biceps, however because the wrist remains perpendicular to the ground rather than parallel, the forearm also gets a workout.

The seated row with resistance tubing is a great back exercise. The largest muscle in the back is scientifically known as the latissimus dorsi. You might see it referred to as the "lats" or "wings." The lats are used any time you pull something. For example, when you open a fridge or a car door, you are primarily using your lat muscles.

This exercise is a convenient alternative to the traditional barbell row. The main target is the upper back, or scientifically, the latissimus dorsi. The "lat" muscles function to pull things. So whenever you open a door, your lat muscles are allowing the movement to take place.

If you are ready to take your ab workouts to the next level, this exercise is for you! The plate crunch can be used as a progression to the traditional workout ball crunch. The range of motion is virtually the same. However, a bar plate is placed behind the head to increase difficulty.

The seated chest press can be done from any chair with a seat back. This exercise is great for shaping and strengthening the chest muscles. The chest is scientifically named the pectoralis. This muscle is used any time you push a chair up to the table, shut a car door, or push a shopping cart. There are two muscles that make up the pectoralis. They are the pectoralis major and minor. The pectoralis major is always the prime mover during chest exercises.

The use of heavy duty resistance bands (also referred to as "Powerlifting Bands") as a strength training aid has become increasingly popular over recent years. The bands are used for accommodating resistance; a technique that involves creating maximal tension throughout a full range of motion.

The seated leg extension is used to isolate the quadriceps muscles. The quadriceps muscles are located on the front of the thighs. As you might have guessed, there are four muscles that make up the quadriceps. Each muscle works in unison to extend the knee. In everyday life, the "quads" are used when you jump, walk, sit, kick, or stand.

If you are trying to work the hips and butt, this exercise is for you! The side kick mainly targets the gluteus muscles. Any movement away from the center of the body is known as "abduction."

The outer thigh lift is a great way to work the butt. Whenever leg abduction (movement away from the midline of the body) takes place, the gluteus muscles are involved. Instructions for the outer thigh lift are as follows:

The use of chains as a strength training aid has become increasingly popular over recent years. Chains are used for accommodating resistance; a technique that involves creating maximal tension throughout a full range of motion.

For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.

Android has a new security feature that every Android smartphone user needs to start using — even you. It won't change how you use your phone, but it will make life harder for nearby thieves.

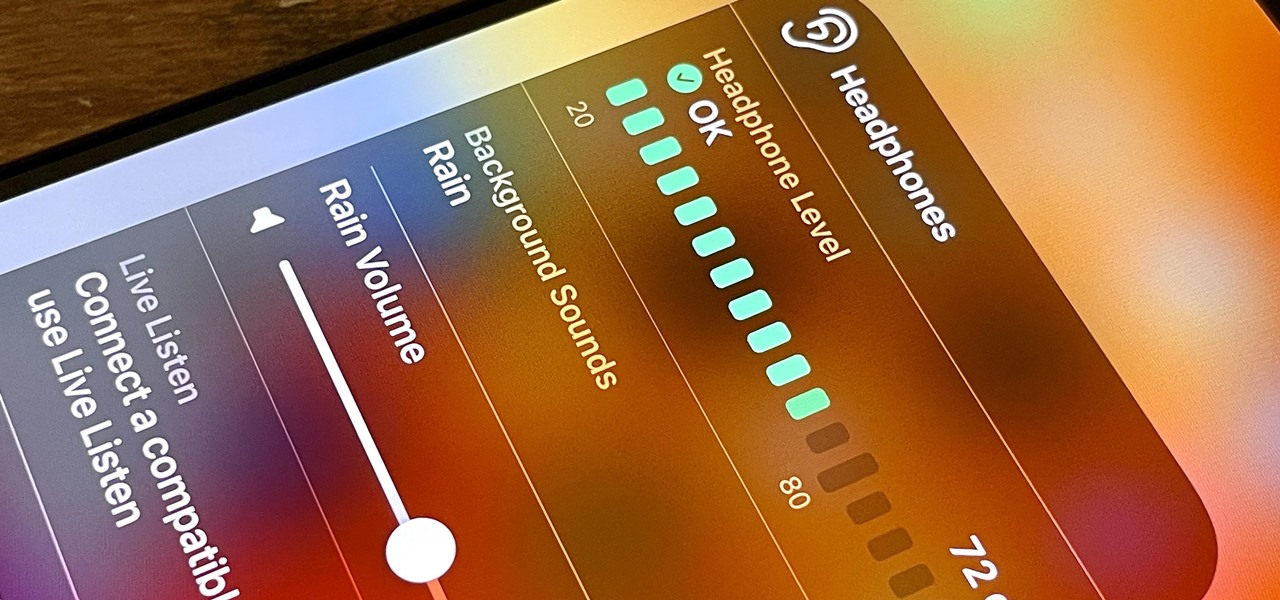
If you get distracted or stressed out easily, your iPhone might be able to help you focus or calm you down. It can even help you fall asleep with white noise, and you don't have to install a third-party app or buy an audio track to turn your iPhone into a personal sound machine.

Samsung has a cool security feature built into One UI that has an interesting side effect, one that lets you have two separate copies of any Android app on your Galaxy phone. And that's not the only integrated Samsung tool for cloning apps.

While Apple's reputation for privacy and security is nearly unmatched, it'll never be perfect when Hey Siri is always listening. Aside from iOS devices, Hey Siri always listens for questions and commands on the HomePod and HomePod mini smart speakers. If you rarely use Hey Siri on those speakers, it's worth disabling the feature for some extra privacy.

The Pixel 5 is a bit of a departure from previous Pixels. Gone are the Pixel 4's Soli-based Motion Sense gestures, the Pixel 3's dual front-facing speakers, and the glass back panel of previous generations. But perhaps the most notable omission for long-time Pixel users is the lack of a squeeze gesture to trigger the Google Assistant.

Apple has an excellent reputation for its privacy and security policies. That said, it isn't a perfect reputation. Take Siri, for example. The helpful iOS assistant isn't just communicating with you — Apple saves and listens to a history of your Siri interactions. If you don't want Apple storing your Siri history forever, there's something you can do about it.

Using your iPhone for a smart home remote just keeps getting better and better. Apple has consistently improved its HomeKit platform since the Home app came out, adding new features, tweaks, and refinements to the system with each update. And iOS 14 continues this trend with a few changes to help make your home even smarter and easier to use.

Android phones finally have a true AirDrop alternative called "Nearby Share." The new feature was added through an update to the Google Play Services app that comes pre-installed on all Android devices in the US, so you don't even have to wait on a firmware upgrade — it's just there.

The rush to secure face masks and hand sanitizers in March left many Americans concerned for their safety. With an expected second wave this fall, consider stocking up on PPE now.

Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

If your smartphone is running Android 10, iOS 13, or a newer version of each, you have access to a system-wide dark theme. And that dark theme works well with Google Calendar, but it's not the only way to go dark. If you have an older operating system, it's still possible to darken Calendar's theme on your phone.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Whether you're new to Android or you just haven't kept up on the app scene lately, we hand-picked over one hundred essential apps that are all designed to improve your experience. From custom launchers and icon packs to weather apps and file explorers, there's something for everyone in this list.

The race to the driverless finish line just got more challenging as Apple seems to have joined the pack. Friday, the global superpower secured a permit from the California Department of Motor Vehicles that allows them to test autonomous cars in the state.

Encryption is on everyone's mind these days, from the FBI's battles in court with Apple to WhatsApp's recent announcement of end-to-end encryption for their one billion users. Now you can add Signal, whistleblower Edward Snowden's favorite messaging app, back to that whirlwind discussion. Created by Open Whisper Systems, Signal is an encrypted messenger app that allows you to send text, images, video, and audio messages without the fear of prying eyes. They already have an Android and iOS app...

Although pasta is a remarkably simple dish, I find it to be one of the most aesthetically appealing foods. The noodles—especially thicker iterations, like linguine and fettuccine—are graceful and luxurious. Add in some sauce coating the noodles, and a sprinkle of Parmesan or a drizzle of olive oil, and pasta single-handedly reminds us of a basic tenet of cooking: sometimes keeping it simple is the perfect way to go.

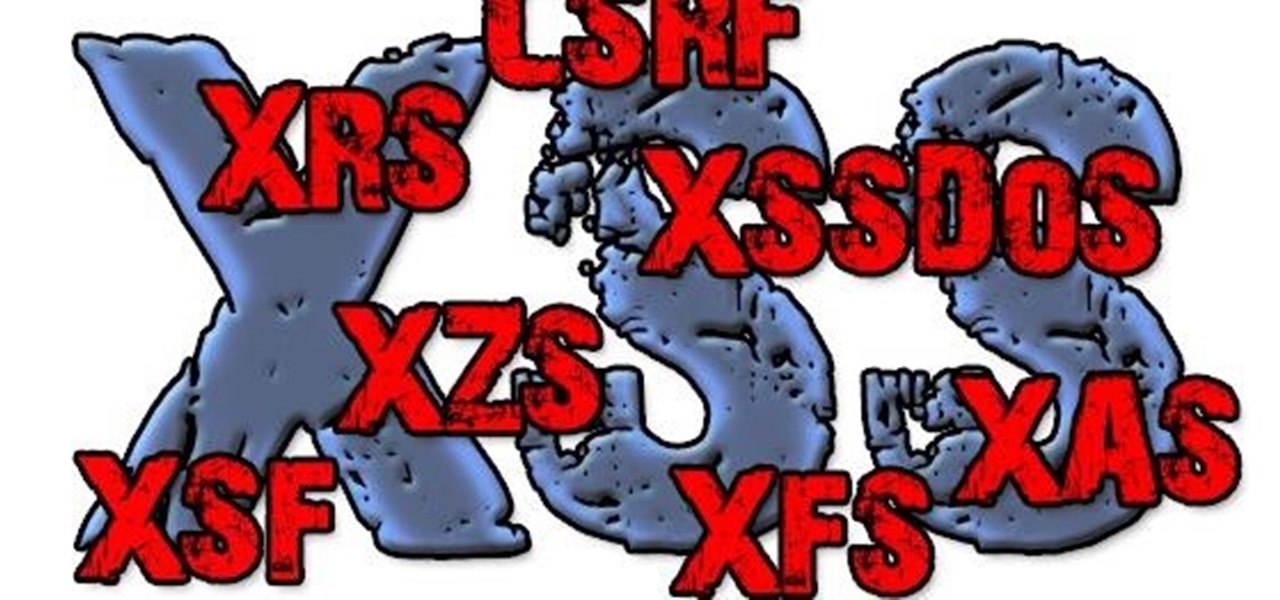
BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...

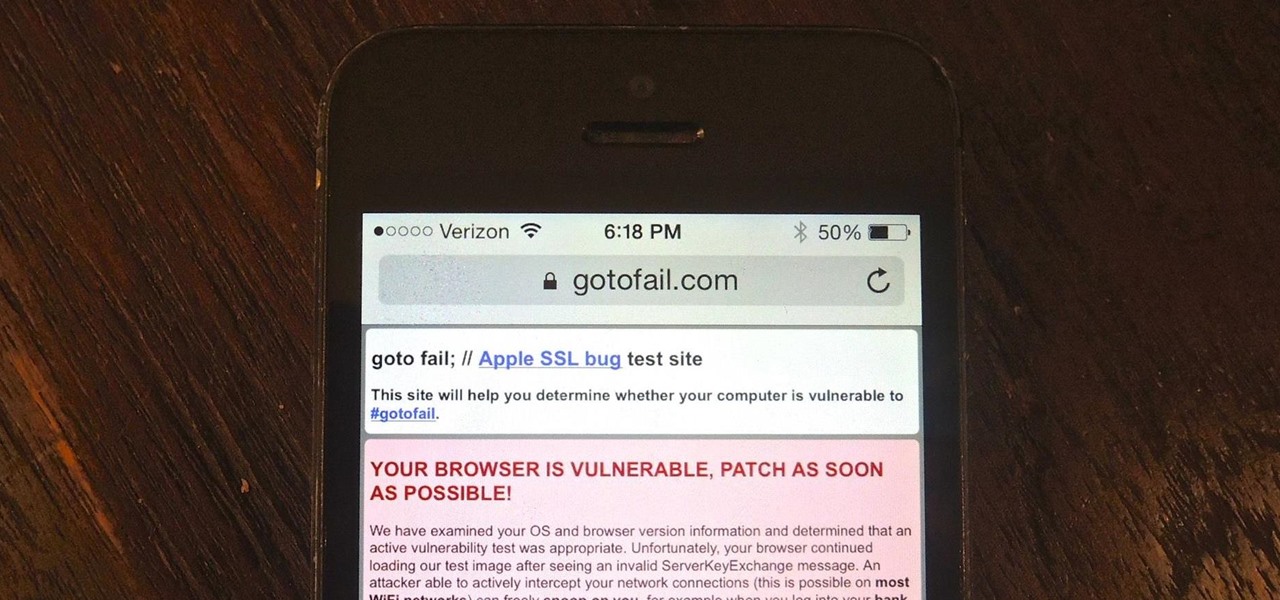
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.