Several Tanzanian girls demonstrate how to tie a kanga (an African sarong). The first method is to wrap the kanga around the waist and tuck the end in at the waist to secure. The second method is to wrap the kanga into a cylinder to use it as a base for carrying a parcel on the head. Another way to wear the kanga is to wrap it around the neck like a shawl or wrapped under an armpit and tied over the shoulder for a fancier look. To wear the kanga as a scarf, fold it into quarters the long way,...

To create an apostolic or pentecostal hairstyle, start with a poof in the front of the hair. It can be ratted behind for stability. Use two bobby pins to secure the back corner of the poof. Squirt the hair with hairspray before moving on. Then create a low ponytail in the back of the hair, pulling the top up and out slightly while forming the ponytail so it creates another poof in the back of the head. Spray the ponytail with hairspray then smooth out the hair on the top of the ponytail. Wrap...

This video illustrate us how to make a light bulb oil lamp. Here are the following steps; Step 1: Take all the things required that is bulb, socks,adhesive tape,scissors,kerosene, rim with a hole in the center.
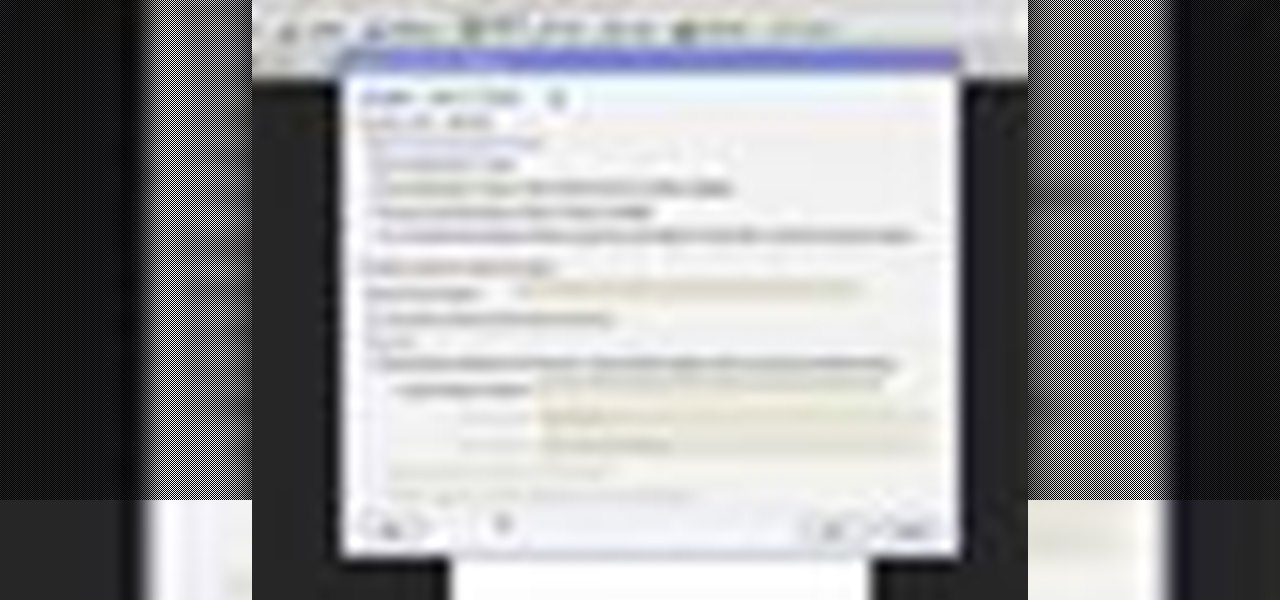
In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...
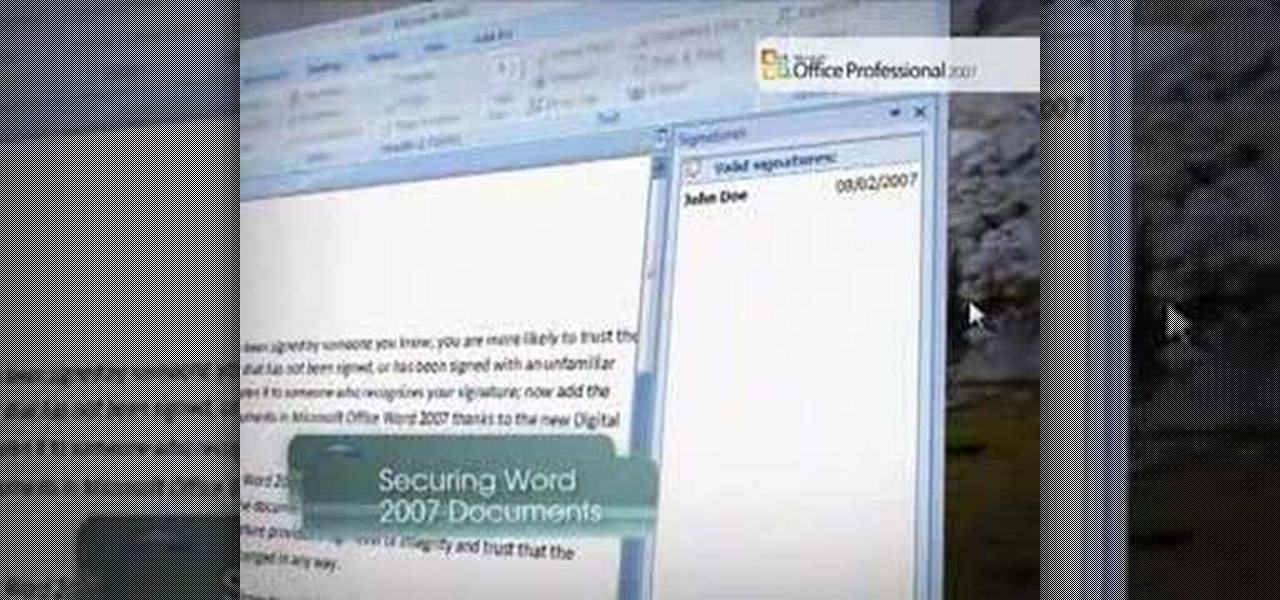
Securing Microsoft Office Word 2007 documents with Digital Signatures - When you receive a document that has been signed by someone you know, you are more likely to trust the contents than those of a document that has not been signed, or has been signed with an unfamiliar signature. Signing a document validates it to someone who recognizes your signature, now add the same degree of integrity to your documents in Microsoft Office Word 2007 thanks to the new Digital Signatures feature. For more...

This half-hour episode of Hak5 covers several topics: Using a DSLR camera to create HD footage, building your own Google TV, unlocking & copying locked files with Lock Hunter, using PicPick for screen capture, using WinDirStat for analyzing & cleaning your hard drive, setting up a secure FTP server with Ubuntu Server, and secretly copying data from USB drives with USB Dumper.

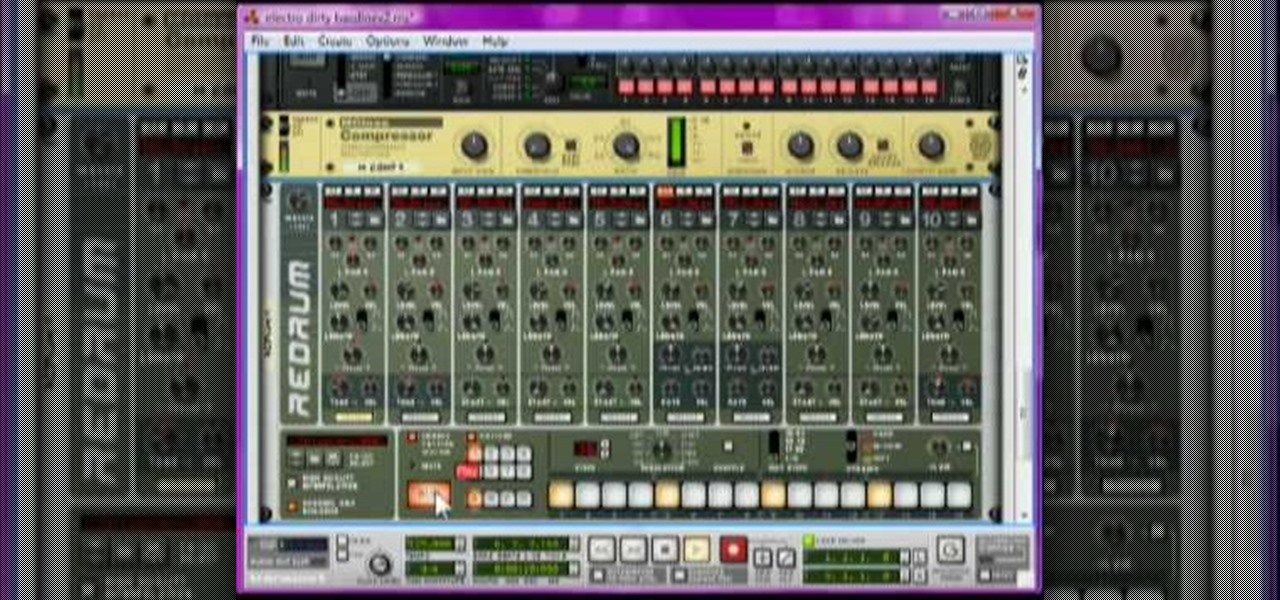
Justice might not have produced any new material in a while, but their place in electronic music history is already secured due to their filthy electro-house beats that have become ubiquitous in the years since they first broke out. Watch this video to learn how to make a dirty electro bass synth line like theirs in Reason 4.

The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

While there isn't as much personal data residing on your Apple Watch as there is on your iPhone, it's still a good idea to set a passcode for it and lock it up when you're not using it. If you don't, while it's charging or otherwise off your wrist, others may be able to sneak a peek at your activity, messages, emails, and other personal details. Plus, you won't be able to use Apple Pay without one.

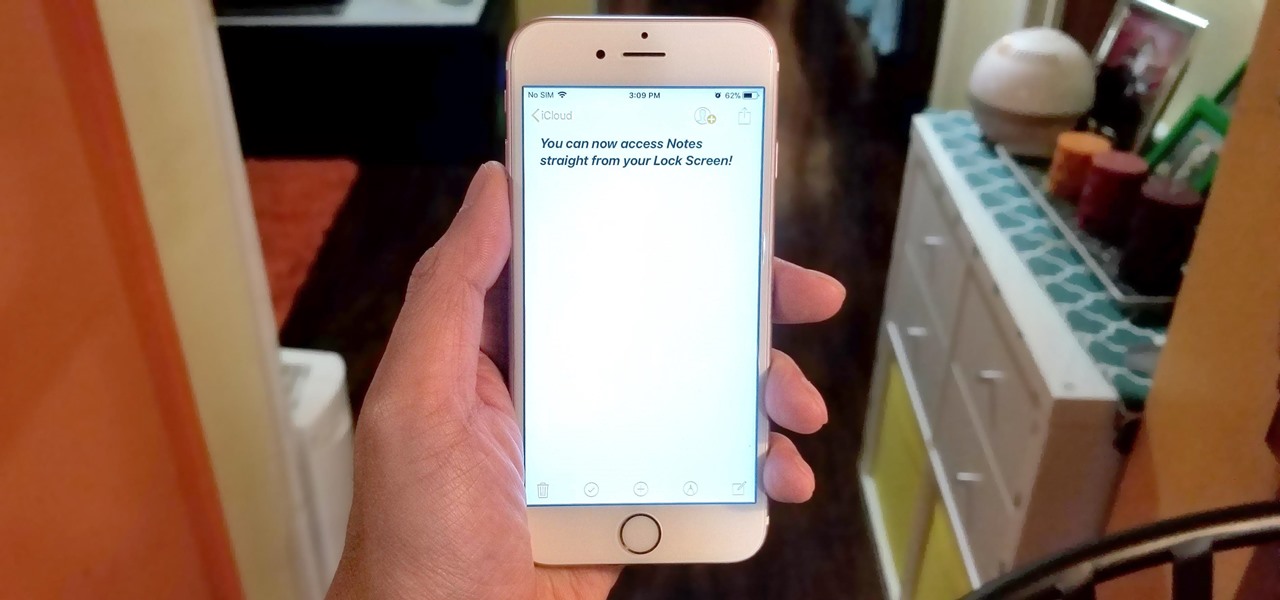
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

Among the many changes in Android 7.0 Nougat, a less talked-about feature may very well be one of the most interesting. As part of a new system-wide API, apps can now create their own Quick Settings tiles, and it doesn't require any complicated workarounds like it has in versions past.

Locking up your iPhone with a passcode prevents mischievous friends from looking at your pics and emails, and makes it harder for thieves to access your data before you get around to wiping it. For even more security, there's the password option, which gives you more than just 4 lonely digits.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

Julia, AKA Hairbeauty4you, gives detailed instructions on how to do a quick half up-do with a twist in under 10 minutes. She notes that this style is best for medium to long length hair. Julia starts with straight hair, then sections off the top part and clips temporarily. She then separates another section on either side of the top part- from the ear to the clipped section- and pulls it back into a high pony tail and repeats identically on the other side, securing each with clear rubber band...

In this tutorial, we learn how to toggle between the two graphics cards built into certain models of Apple's MacBook Pro laptop computer. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

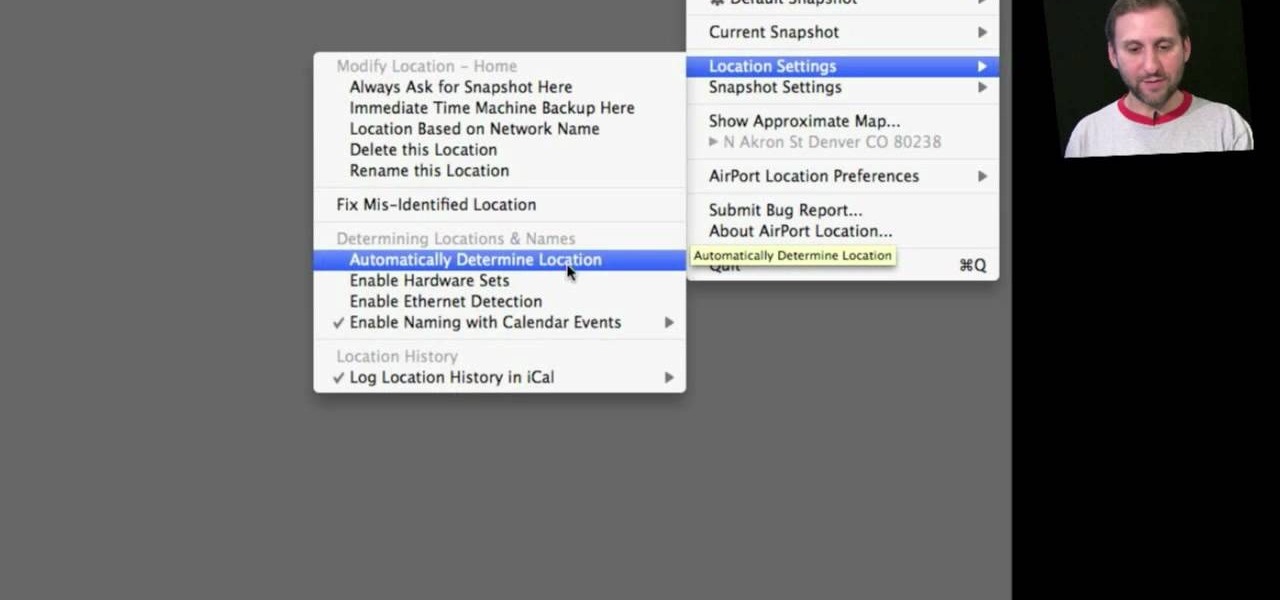
In this clip, you'll learn how to record and toggle between different preference settings on an Apple computer running Mac OS X. With Airport Location Utility, it's easy! So easy, in fact, that this home-computing how-to from the folks at MacMost can present a complete overview of the process in just over three minutes. For more information, including step-by-step instructions, take a look.

Veronica Belmont from Tekzilla shares a tip for finding lost podcasts without unsubscribing and resubscribing to the feed. To do this by a simple keyboard combo fist close the disclosure triangle so that the individual episodes are hidden, then hold down the 'Option key' in Mac or 'Shift' in Windows and toggle the disclosure triangle as shown. The iTunes feed will refresh and all the past episodes will reappear. Combine this with the "Get All" button to find lost podcasts.

All you need is a basic digital camera and GIMP photo editing software to create your own version of the Pan's Labyrinth creatures. The Keyboard Shortcuts used, in case you can't hear it properly:

Tie a clove hitch knot again, again, and again.

In this video, we learn how to do wrapped pigtails on your American Girl doll. First, separate the hair from side to side. Then, take a small section from the front of the hair and put it aside. After this, you will need to comb the hair back into a ponytail and secure with a rubber band. Secure the other side into a ponytail as well, but put all the hair back into it. After this, you will take the front from the other side and wrap it around the ponytail. Clip it into place and then you will...

In this video, we learn how to tie a Palomar knot to secure a fishing line. This knot is pretty easy to tie, it won't take long. First, you will take the fishing line and make it into a loop. After this, insert it through the eye on the hook. Next, bring it back over and then tie an overhand knot, leaving it a little loose when you tie it. You should be able to see the working end hanging down. Now, take the loop and put it over the hook. Now when you tighten it up, you will have the complete...

In this video, we learn how to do the triple nifty knots hairstyle on your AG doll. First, comb the doll's hair back and then take the hair from the crown of the head. Put this into a ponytail and then secure with a rubber band. After this, section the tail off into two parts and twist them individually. Then, bring these around each other and create a bun at the top of the doll's head. Secure this with a rubber band. Do this with two other sections of the hair on the left and the right. When...

In this tutorial we learn how to fix an RV awning that will not retract. If you find yourself in the situation where the awning on your RV just won't retract, then this is the video for you! To secure the awning you will first need to go to the roof of the RV. When you get on top, you will need to look at the awning and see if something is stuck and causing it to stick. Manually secure the awning when you go to the roof so that it will stay in place for when you need it. If this doesn't help,...

In this tutorial, we learn how to install a cold air intake for a 96-04 Mustang. First, you will need to lift up the hood and locate/disconnect all wiring harnesses. Then remove the bolt around the air filter housing and set aside. Separate the intake and the housing, then pull out the air filter housing. Reinstall rubber grommets that may have come out, then disconnect all hoses from the engine. Put the intake and the pieces together, then you will start to place it back into the car the way...

In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

In this video, we learn how to make a box. First, fold the piece of paper into a triangle, then another triangle. Now, unfold the paper and fold all the sides into each other, making a square. After this, fold in the sides once more, making sharp creases on the edges. Now, open up the paper and do this again on the other sides, opening up again when finished. Now, fold the sides of the paper and turn it upside down. Follow the creases that you just made to fold the box up into a secure box. M...

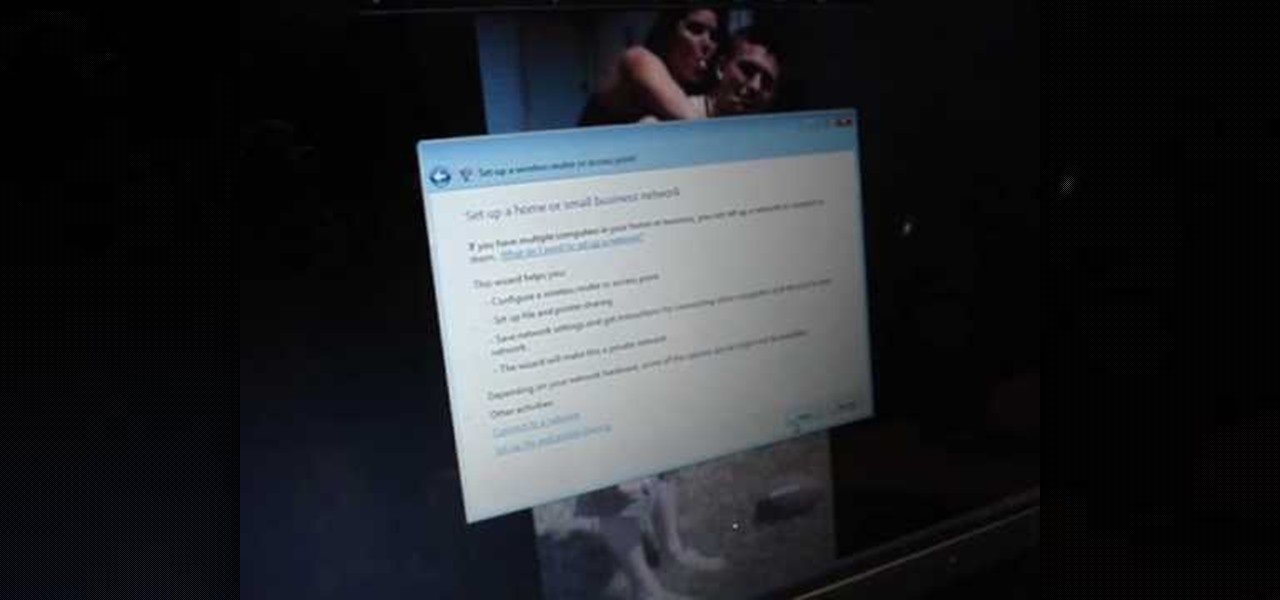
In this tutorial, we learn how to set up and secure a wireless router. First, take your cable and plug it into your modem from your computer. After this, plug in an Ethernet cable into your modem to a wireless router. Now, plug the wireless router and modem into the wall. Now, look for the icon on your computer that says you have connected a new device to it. Go through the set up wizard to make a new wireless network, once it doesn't find one, connect a USB to the computer. Now, click on the...

In this tutorial, we learn how to replace the spark plugs on a 2008 Kawasaki Ninja 250. First look underneath your bike to find out exactly where the spark plugs are at. Next, use wrenches and ratchets to loosen the parts around the spark plugs, then remove the spark plugs completely. After you have pulled them out, replace them with the new one and secure them into place. When finished, replace all the casing around the plugs and make sure you secure them tightly. Add on all bolts when you a...

In this tutorial, we learn how to make a floating illusion style necklace. You will need: beading wire, crimping pliers, wire cutters, beads (your choice), crimp beads, crimp covers (3mm), and a clasp (barrel clasp). First, cut your beading wire to the length you want your necklace, add 3-4 extra inches. Next, space your beads out on a beading board evenly, 1 1/2" apart. Now string a crimp bead onto your wire and take the end of the wire and string it through the crimp bead on the opposite si...

In this video, we learn how to properly pack glass for moving. Make sure you have a table or work area that has a furniture pad on it. Now, place packing paper onto the bottom of a box carton for glasses and china. Glass should be on the top of the box while plates should be placed at the bottom. Put the glasses into a rolled piece of paper until secured, then place upside down into the box. When finished, add crushed paper to the top of the first layer to avoid any glass from breaking. Make ...

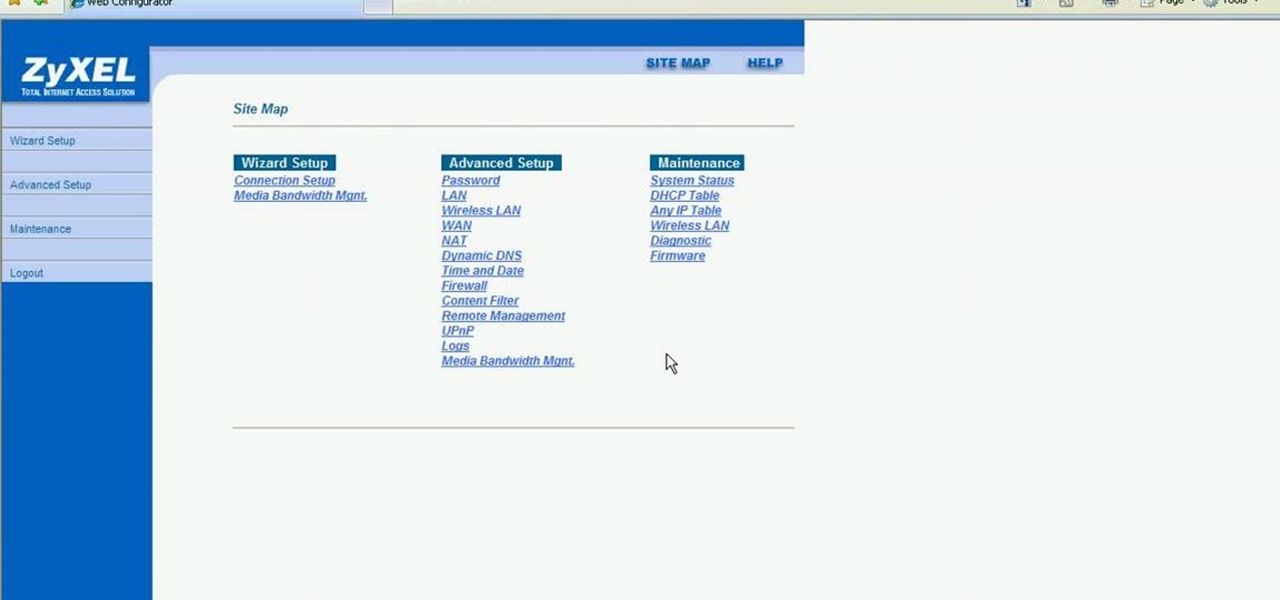
This video shows how to secure a wirelees internet connection on your Zyxel P-660hw-t1. For this, first click on Start button and open Internet Explorer(or any other browser). On the address bar of the browser, type in the IP address of your router. On the next page, enter your password and on the next page, either change the password or ignore. On the next webpage, under Advance setup, click on Wireless LAN. On the next page, click on 8021xWPA. Select authentication required and then click a...

Abigail Goss demonstrates a traditional Apostolic hairstyle, the vertical roll with pin curls. She starts by creating a poof, back combing the roots from the crown to the forehead. Then she creates a section of hair above the ears. She rolls this hair several times in one direction and then puts all of the hair into a ponytail at the base of the neck. At this point the style looks like a french twist with a ponytail at the bottom. She then coats the hair with gel. To make the curls, she takes...

This video illustrate us how to make a piano bracelet on a loom. Here are the following steps: Step 1: First of all secure the piano tabs to the loom and criss cross the string on the tabs.

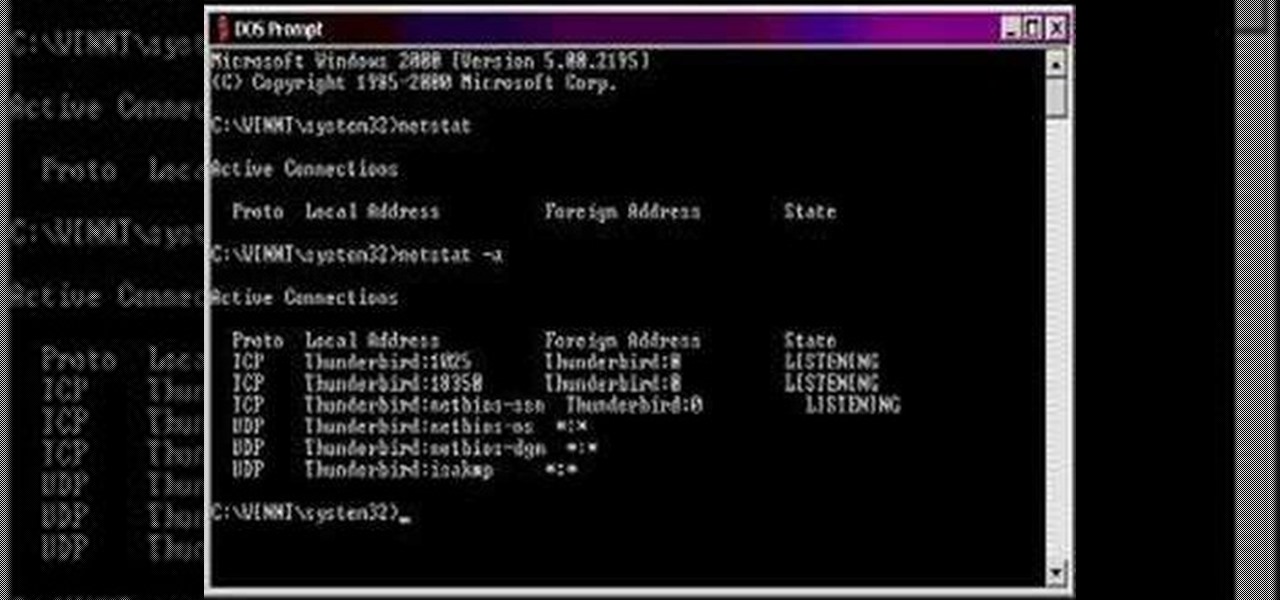
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

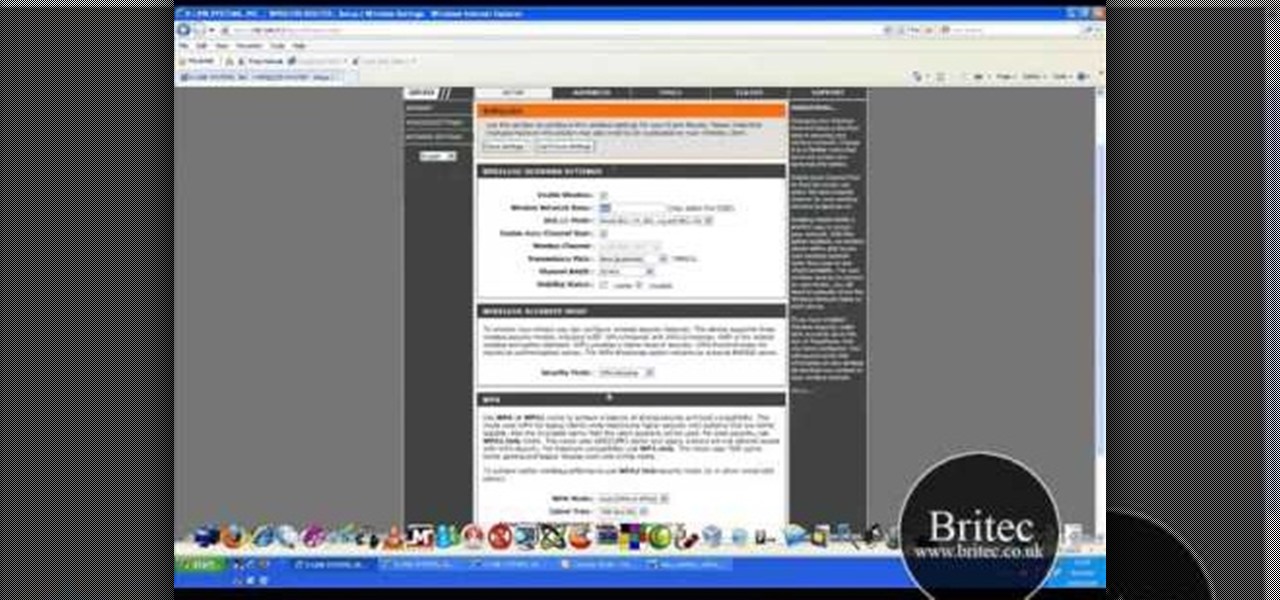
Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

How to build a high tunnel to protect your plants

This is a video using Swarovski Crystals to make jewelry. This video shows how to make one with a gold bow. You need a pendant with 2 hoops (in this case it is a gold bow), a pendant holder, a crystal, a bill, and pliers. You take the bill and hook the crystal on it. Then you hook the bow on it and secure it using the pliers. You take the pendant holder onto the top of the bow pendant, and press it down to secure it, and you’re finished. You can also make rings, earrings, necklaces, and many ...

This video shows the viewer how to secure crimp beads using both crimping pliers and chain-nose pliers for the purpose of jewelry making. The video uses two millimeter crimp beads, beading wire, and both sets of pliers to demonstrate the technique. To crimp using the crimping pliers, the viewer will utilize both notches of the pliers to crimp the bead onto the wire. In order to crimp using the chain-nose pliers, one must simply flatten the bead onto the wire. Crimping is a good method to secu...