It seems nowadays the word "easy" has taken on an alternate meaning. When I see "easy," I expect a quick and painless process, but when it comes to flashing or installing a custom ROM, easy means anything but.
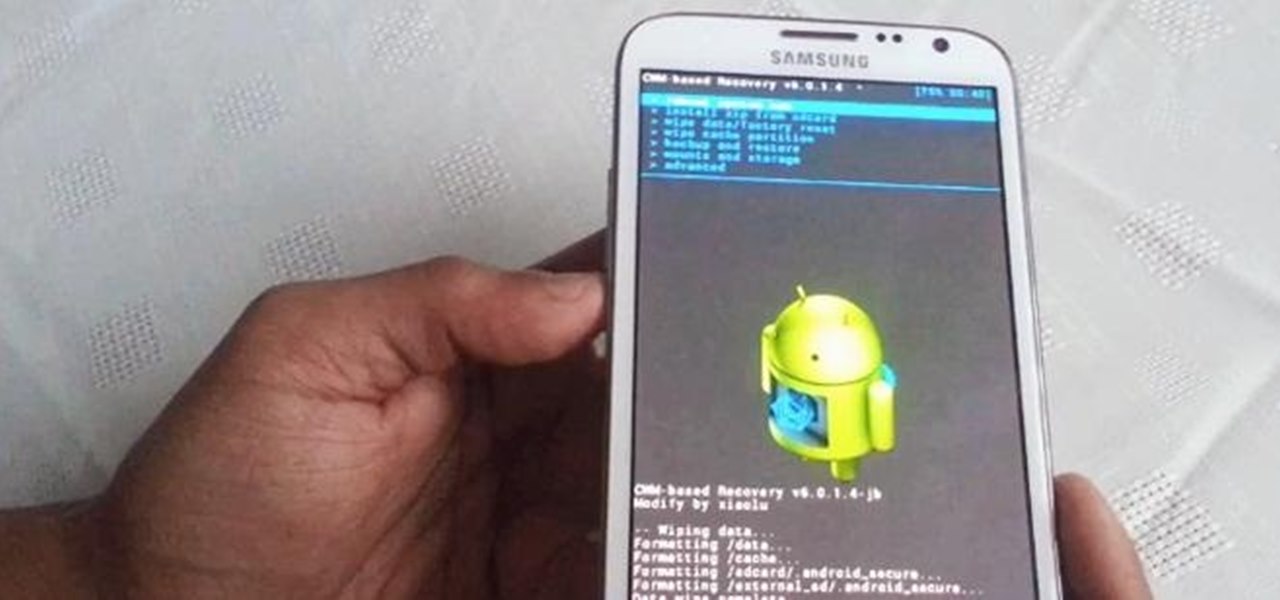
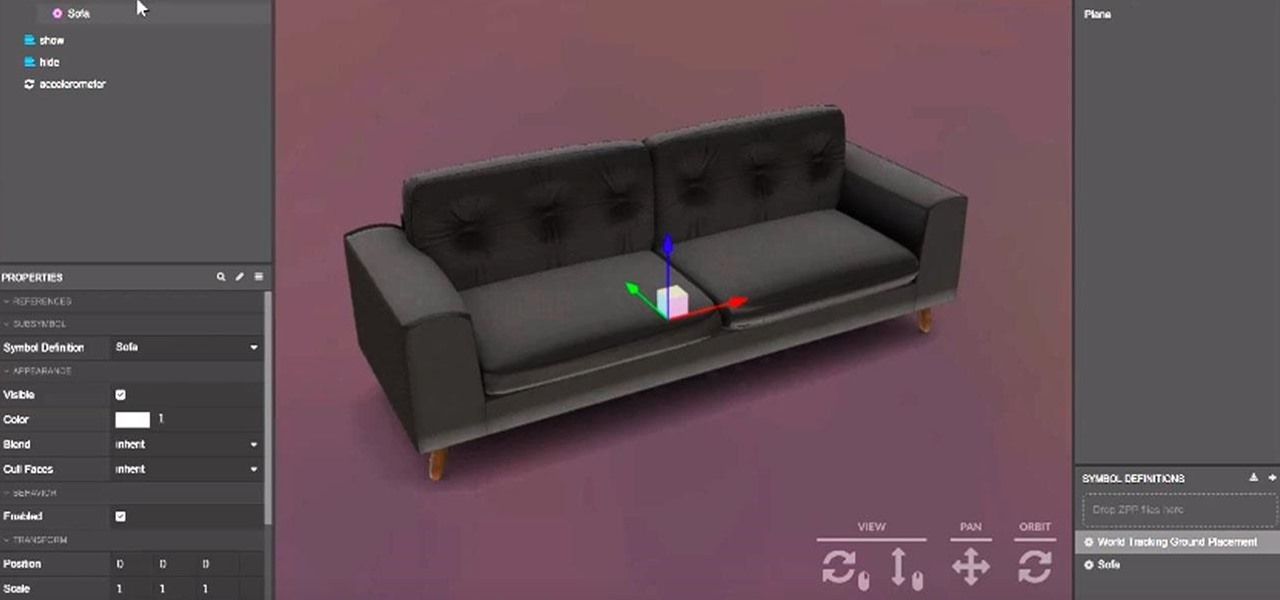
The new Samsung Galaxy Note II is a powerful and sleek device that begs for some customization, and there's no better way to customize your Android device than installing a custom ROM of your choice. One of your choices is the Omega ROM, which is just one of many that you can download and flash to your Galaxy Note 2. Before you begin, you'll need to root your Galaxy Note 2 and install Odin and CWM Recovery. You can get a toolkit of everything you need over at XDA Developers. Then follow the v...

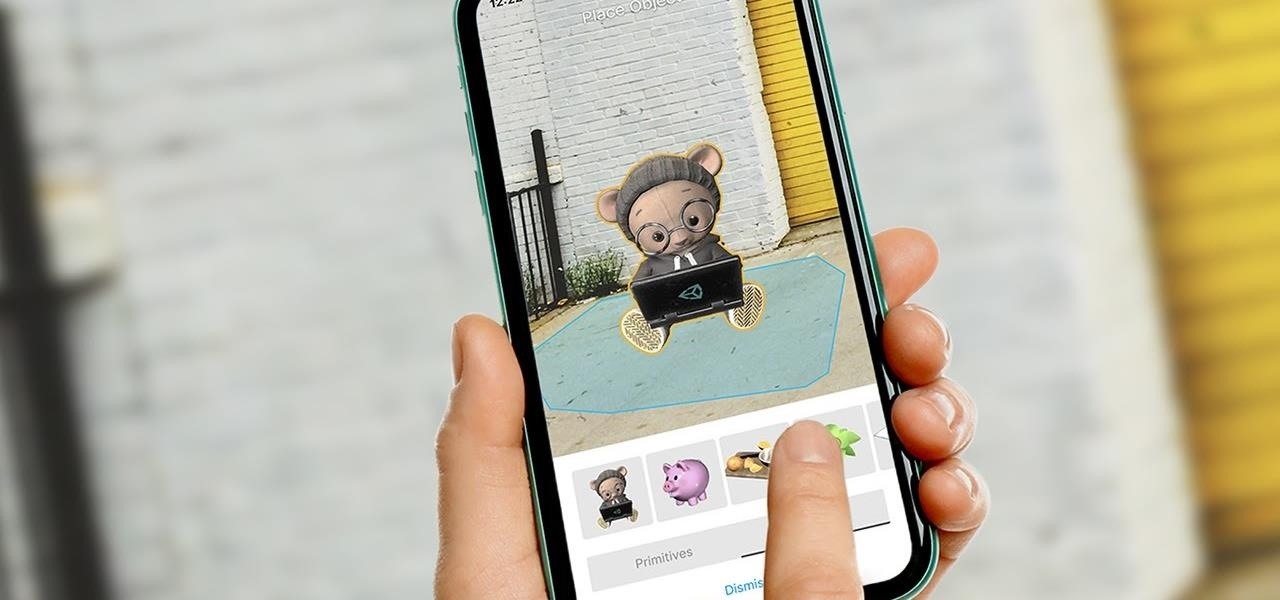
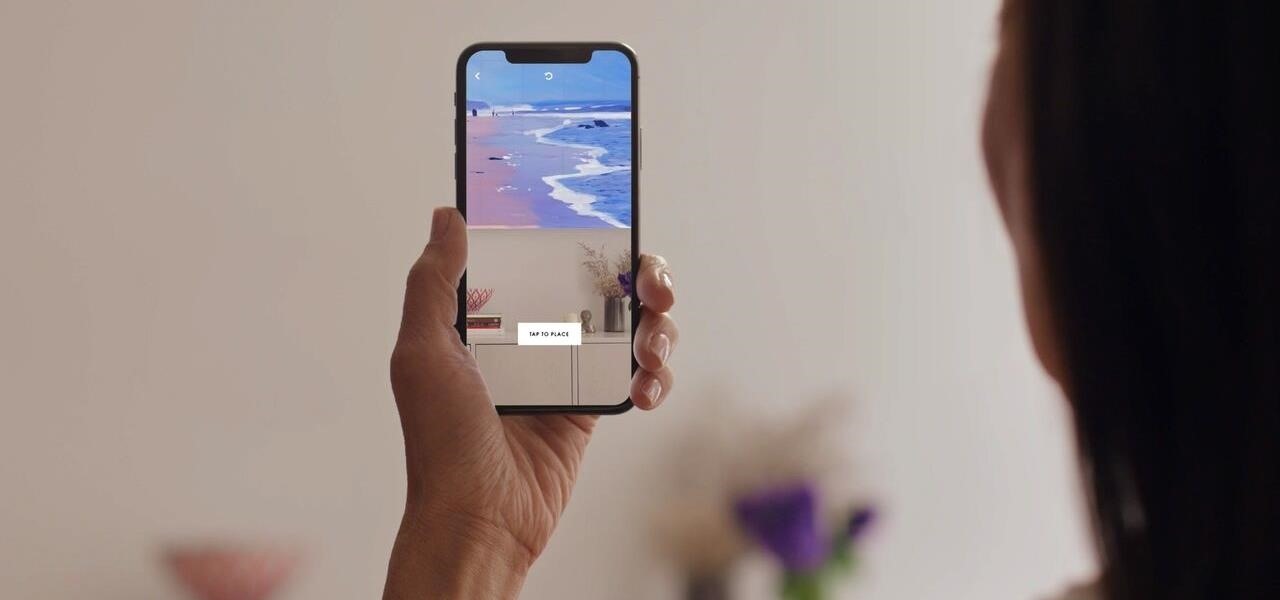
While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.
Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Unity often reminds us that the majority of AR apps and experiences are built with the Unity 3D engine, and now the Unity MARS service, which facilitates easy AR creation for seasoned coders and newcomers.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

There is so much information in the world that trying to make sense of it all can be daunting. That's where data analytics comes in. By learning how to inspect and model data, you can take large data sets and transform them into highly valuable information that can take any business further.

After introducing and launching Reality Composer alongside iOS 13 and ARKit 3 last year, Apple is making it easier for developers to create apps with it.

Hollywood loves sequels so much that studios and their marketing teams are not too proud to release a sequel of an augmented reality promotion.

As Android device partners ship new products, Google has been diligent in its efforts to ensure that users can enjoy ARCore apps once they boot up their new toys.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Less than a week after ARKit 1.5 became available to the public through the iOS 11.3 update, the App Store has its first app with AR features (Artsy) to leverage Apple's AR toolkit update.

Space might be the final frontier, but NASA is making a detour into augmented reality first. The Spacecraft AR app, developed by NASA's Jet Propulsion Laboratory (JPL) in collaboration with Google, debuted exclusively for Android this week (an iOS version is also in the works).

Continuing with its new paradigm of using augmented reality to cover the news, The New York Times has published a feature story that takes a peek into the late David Bowie's eclectic wardrobe of on-stage outfits.

Location services provider Mapbox is giving developers a means for building location-based AR apps and multi-user experiences with its new Mapbox AR toolkit.

A very low-key update to the ARCore developer's site has expanded the universe of officially-supported devices for Google's augmented reality toolkit to include the Samsung Galaxy S7, S8+, and Note 8 handsets.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

The Microsoft HoloLens mixes the digital world with the physical one, allowing you to coexist with holograms of your choosing. But those worlds won't fully blend until we can experience it all together and create for each other. Vuforia could make that possible in the near future.

If you're familiar with games like Half-Life 2, Left 4 Dead, Portal, and Team Fortress 2, then you've probably seen some of the cool animated movies that Valve has made for them using their Source Filmmaker moviemaking software. It's a tool built to make animated films inside their Source game engine. It's even been licensed to make the upcoming animated film Deep.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

While "Baby Yoda" from The Mandalorian threatens to overshadow it, Star Wars: The Rise of Skywalker arrives in theaters next week, which means it's time for Disney and Lucasfilm to ramp up its promotional strategy.

Dark mode themes for mobile apps are all the rage these days, but YouTube is taking that a bit literally with its latest augmented reality experience.

NASA is going going to Saturn's moon Titan, and the space organization is using augmented reality help them do it.

Augmented reality has taken the advertising industry by storm, but the technology has a steep learning curve. Luckily for advertisers, Unity is here to flatten the curve a bit.

After one of Britain's "Brothers Bling" bought Blippar out of bankruptcy, the mobile augmented reality company is getting back to business with the addition of web-based AR capabilities to its platform.

If you've been putting off upgrading your iPhone or iPad, you might want to start shopping for a current-generation device to take advantage of the latest capabilities in ARKit 3.

Augmented reality platform maker Zappar and its marker-based augmented reality technology have been around well before Apple and Google brought markerless AR to mobile apps.

As one of the leading 3D engines for augmented reality development, a new release of Unity is a significant event that carries the potential to facilitate huge leaps forward in AR content creation.

Over the past year, two trends have emerged among augmented reality development software: make it easier to create AR content, and give AR apps better environmental understanding with just a smartphone camera.

Lebron James, or King James to his royal subjects, is extending the reach of his kingdom beyond basketball and into the realm of augmented reality.

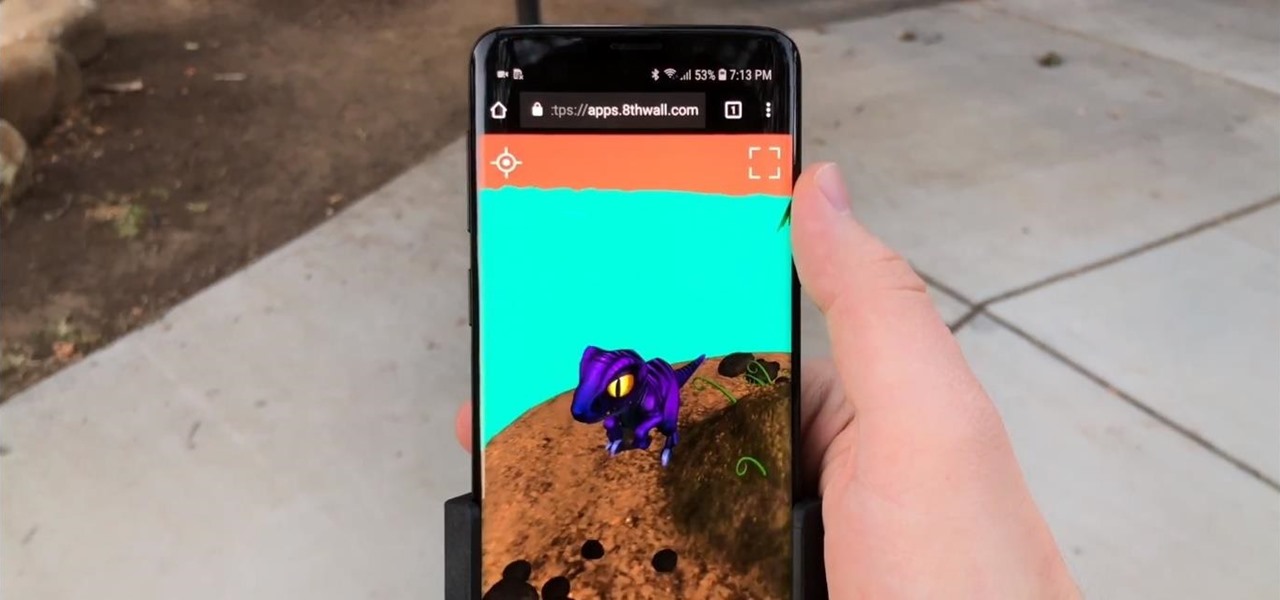
In the past few years, augmented reality software maker 8th Wall has worked to build its platform into a cross-platform augmented reality toolkit for mobile apps, as well as web-based AR experiences.

French cosmetics giant L'Oréal isn't wasting any time putting its new subsidiary, ModiFace, to work. On Thursday, the company launched a new tool that enables a photo-realistic augmented reality simulation of nail polish shades and textures to be accurately displayed on a user's fingers in real time.

Electronic Arts is inviting players of The Sims Freeplay and their friends to visit the homes of their Sims in augmented reality with a new AR mode that supports multiplayer and persistent content using ARKit 2.0.