When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

In recent weeks, Unity has made a few great leaps forward for HoloLens development. These new features will increase iteration speed inside Unity and quickly increase the output of applications in the mixed reality space. Of these new features, let's take some time to talk about Holographic Emulation and why this will do so much for the development community.

Today at the Unite '16 conference in Los Angeles, Unity's Timoni West and Amir Ebrahimi showed off its new virtual reality authoring and world editor, EditorVR, using the HTC Vive. Coming in December to Unity is a version of its editor that works inside a VR headset, which will change the way developers interact with the worlds they build—even if they aren't building for VR.

Pitting cherries is really annoying. There's no neat way to do it with a knife and, though they make a tool that does it, not everyone has space in their kitchen for a gadget that does so little. But fresh cherries are so delicious when they're in season... it's almost worth the extra hassle and/or space usage.

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:
How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

One thing the whole Internet can agree with is that cats are cute and (sometimes) cuddly. But what those endless cat videos you find yourself watching for hours on YouTube don't tell you is that cats stink. While cats aren't the source of the smell, owning a cat means a stinky litter box.

At first glance, the Big Green Egg looks like it was created by Dr. Seuss or some other whimsy-driven being, like Zooey Deschanel. And while this earthenware cooker may look cute, it produces serious results that can rival the best barbecue or grill. In fact, it's got quite a large cult following. Entrepreneur and former Navy serviceman Ed Fisher fell in love with the taste of food cooked in kamodos (traditional domed, covered earthenware vessels in Japan) and began to import them for sale in...

I'm not a big fan of single-use tools, especially ones that don't get used particularly often. And I'm especially not a big fan of seldom used single-use tools that take up a large amount of space.

Meet the Wonderbag. The "first non-electric slow cooker" uses an insulated bag made of poly-cotton fabric, polyester, and repurposed foam chips. You bring your one-pot meal to the desired cooking temperature, usually via the stovetop. Then you turn off the heat, pop the pot into the Wonderbag, and it will continue to cook thanks to the retained heat in the bag.

Bringing lunch to work or school is a win-win situation. You save money, you eat better, and you create less waste. But while the virtues of brown-bagging it are undeniable, it also gets kind of boring after a while. How many times can you shove a container of salad or noodles into an insulated sack before you say screw it and buy a $12 burrito for lunch instead?

With all due respect to the fine folks at DrinkTanks, it's a little surprising that no one came up with their idea sooner. After all, last I checked, beer was pretty darned popular.

Most of us enjoy taking photos with our iPhones and sharing them with friends and family, but it's adding that extra touch or funny caption that turns an ordinary picture into something unforgettable or downright hilarious. With Inkboard, you can use your imagination to draw and scribble over any photo you take or have in your iPhone's camera roll.

A good, sharp knife is a cook's best friend, which is why there's so much passionate debate about what kind you should get. Most enthusiastic home cooks opt for a stainless steel knife, but it turns out there's a different option that the pros favor, and that's carbon steel.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

The newer Graph Search in Facebook can help you find friends in specific cities, photos of a particular subject, restaurants that your friends liked, and a whole lot more. One thing it can't help you with just yet is searching public posts on Facebook, which you could do in the previous search version. Actually, some users do have the option to search public posts with Graph Search, but it's very limited and doesn't include me. If you're like me and don't have access yet, there is a workaroun...

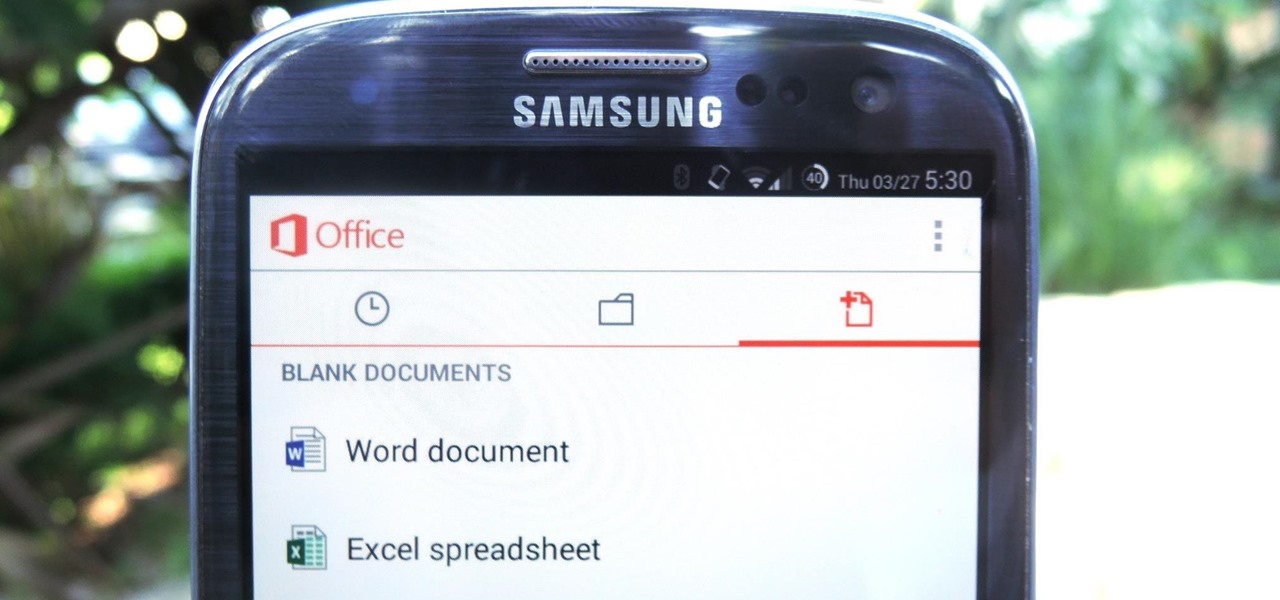
In a flurry of moves today, Microsoft has not only released their suite of Office apps for the iPad, but they also updated their Android and iOS Office Mobile apps to allow for creating and editing documents without requiring an Office 365 account (so long as it's for "home" use). Microsoft Office Mobile for Android & iOS

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

One of the most frustrating things about full touchscreen phones, especially for those coming from one with a physical keyboard, is typing and editing text. Whether it's a quick text message, or Swyping out a full e-mail, it sucks realizing you've messed up a few words and have to go back and fix them.

Oversleeping isn't just an epidemic that affects millions of hungover college students every year, we all want that extra minute or two of sleep. Unfortunately, oversleeping and showing up late to work or class isn't something we can generally afford to do.

Whether it's because you want to make a quick tutorial video or want to show off your gameplay skills, recording the screen your Nexus 7 tablet isn't an easy feat. At least, until now. Hidden inside Android 4.4 KitKat is a built-in screen capturing feature, but it takes a little effort to dig it out.

No offense to T-Mobile, but if you head over to their support page for the Samsung Galaxy Gear, you get the information below on how to take a screenshot of your smartwatch. Oh, thank you for that.

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

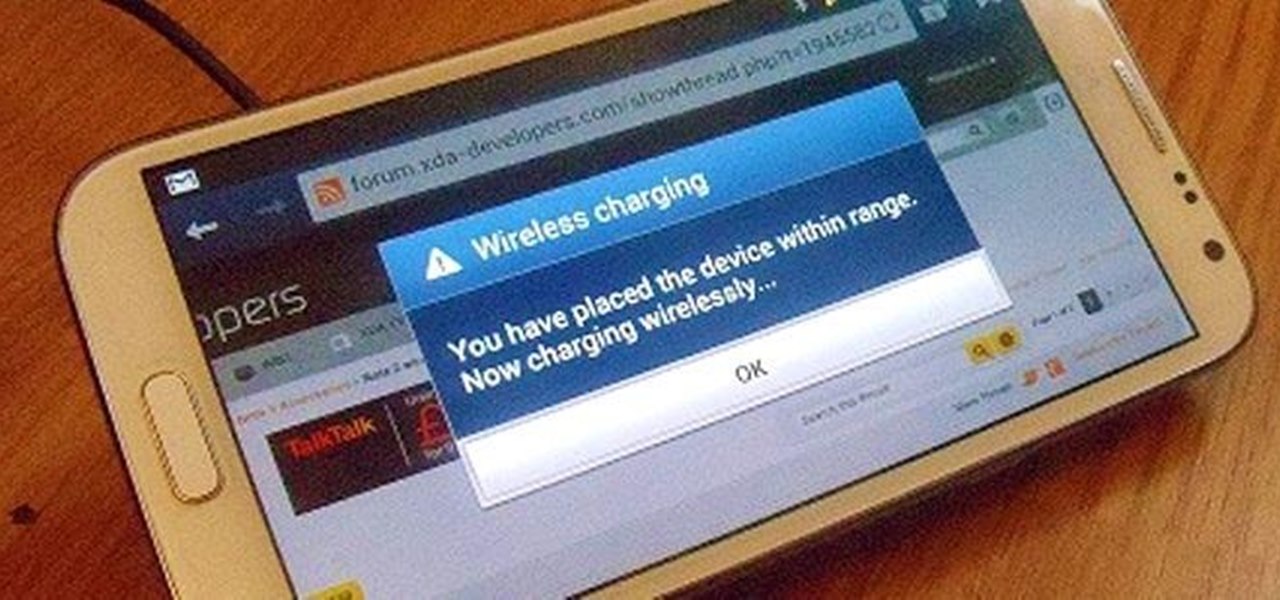
Inductive charging is already a reality on popular smartphones like the Samsung Galaxy S III and Google Nexus 4, and Apple has recently published a patent that would make inductive chargers a reality for the iPhone. There are also several phones that have the capability for wireless charging, such as the Samsung Galaxy Note II.

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

Before you whip out your iPhone and call your neighborhood plumber for a job that's sure to cost you a pretty penny, check out this video to learn how to do some impressive plumbing yourself. Using a few tools you probably already have lying around your house, you'll learn how to install a shower base in your shower unit and then connect it with the drain - effectively, you'll be setting up a plumbing system.

Looking to do a little Friendster account hacking? Well, this video will show you how to hack into anyone's Friendster account after getting their password. Friendster was Facebook before Facebook was around, and beleive it or not, people still use it! You'll need a little tool to do the work, which you can find here. After that, follow the steps and get into any Friendster account. Remember, hacking is illegal, so be responsible out there.

Give your home an autumnal sparkle! This tutorial shows you how to glitterize pumpkins as a home decorating tool. This uses the very small pumpkins, but the techniques can be applied to larger pumpkins if you wish. Paint the stems gold for some added glitz!

In this video we learn how to increase & decrease the size of web page content. First, click and hold down the control key and move the mouse wheel up and down. After you do this, you will start to see your web page content get larger and smaller right before your eyes. You can also use the plus and minus keys on the keyboard to get the same effect. Keep in mind you will need to do this for each of the different pages as you access them. For a more permanent fix, you will need to go to the to...

In this tutorial, we learn how to jump over a car with film effects & tricks. First, you will take a long shot of someone pretending like they are jumping over a car, make sure they add in excitement. After this, you will take a long shot of a car driving over in the same area. Now, load your clips and add in the image of the person jumping with the image of the car. After this, use the magic tool to add them both in the same scene, then you will have a great film effect that makes it look li...

In this tutorial, we learn how to tile a shower floor and curb in your own bathroom. To start, you will need to apply the foundation of your tile with a smoothing tool from corner to corner of each of the corners. After the mortar is lied, grab your tile and press it down firmly onto the mortar. Use your hands to press down on all the corners of the tile, then place another one next to it and continue until you reach the end of the shower. Use a straight edge to cut tiles where the are too lo...

In this tutorial, we learn how to repair cracks and holes in drywall with Lowe's. Drywall can be damaged in a number of ways, but can be fixed easily. If you have a medium size hole in the wall, first place caulking on it and then smooth it out. If you have a larger area, you will need to use a sanding strip around it to smooth out the area and all around it. Use drywall compound to fill in the area that is empty. Then, smooth over it with a flat tool then paint over it with the same color pa...

In this tutorial, we learn how to install laminate flooring in your home. First, you want to inspect all your flooring. Clean your floor and then remove baseboards around the room. Lay down your underlayment before you begin, then lay down your flooring where you would like it. As you snap the pieces into place, you can use a hammer and positioning tool to ensure they are tight together. After you do this, you may have to saw some pieces to make sure they all fit together. When finished, you ...

In this tutorial, we learn how to grout tile in your custom tiled shower. First, you need to score away anything in between the seams of the tile. Now, grab a bag of sanded grout mixture and grout enhancer. Next, wash the surface of the tile with a damp sponge to take off any impurities. Then, mix half the bag with half the enhancer and stir until combined. Use a tool to rub the mixture onto the walls and leave it on for 15-20 minutes. Now, go over the area with the mixture and go over it wit...