Interested in installing the µTorrent BitTorrent client to get started downloading torrent files? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over two minutes. For more information, including complete, step-by-step instructions, take a look.

A video on the basics of bittorrent technology and how to get started downloading a Bittrorrent client and torrent files.

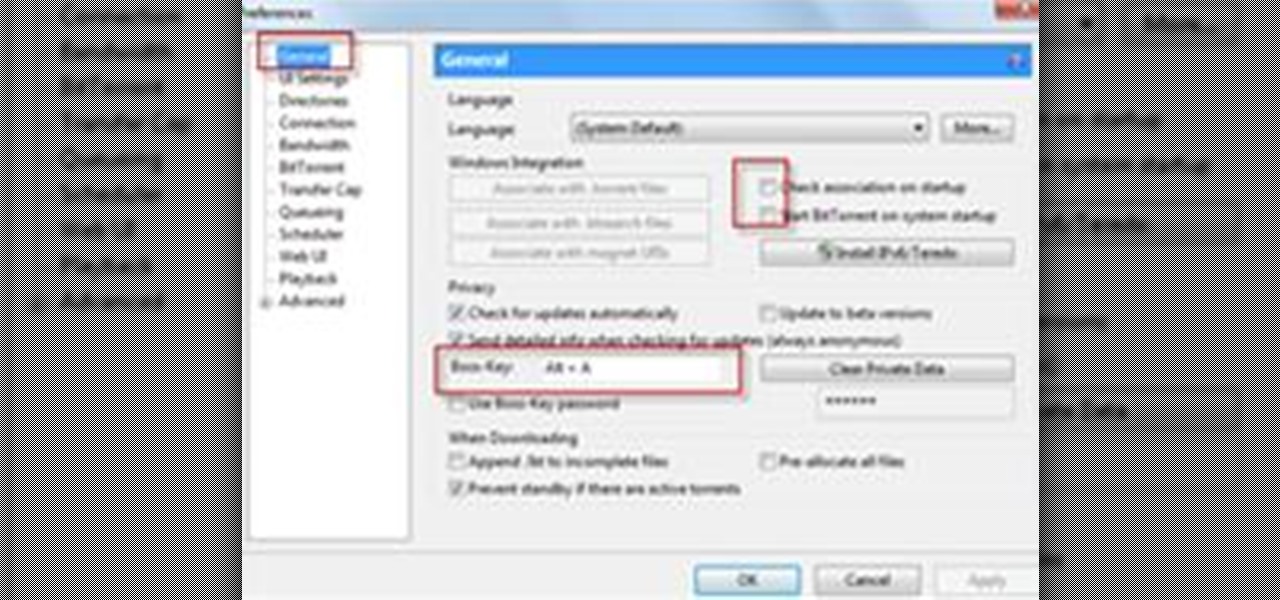
If you want to speed up your torrent transfers using uTorrent then the first thing you'll want to do is run the speed guide. This clip will show you how it's done. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about two and a half minutes. For more information, including detailed, step-by-step instructions, watch this video guide.

This video teaches the secrets of downloading and using uTorrent in your computer. First download the software from the link shown in the video and open it. Now to download any file search some popular torrent websites. Make sure you select a torrent file with more SEEDS but less LEECHERS and download it. Now open the downloaded torrent, select the required files if there are many and start downloading. After downloading stop the torrent and use the files.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

How to use uTorrent First of all we need to understand what uTorrent is. uTorrent is a file or a Micro-Torrent that helps you, the user, download stuff like documents, pictures, videos, or e-books. uTorrent is very, very, useful when you know how to do it. so hope fully this tutorial helps you learn to use uTorrent.

Completely Hide UTorrent and Bittorrent Software in Your PC While It Is Still Running!.

Apple released the iOS 8 Gold Master build to developers shortly after their WWDC event ended on Sept. 9th, which is jam-packed with tons of new features for iPad, iPhone, and iPod touch. The public version comes out on Sept. 17th, but if you can't wait to test out iOS 8, you can get it right now.

Use a torrent to download your favorite TV shows to your PC or Mac computer. You can also set up RSS feeds to get the newest episodes.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Part 1: What is Popcorn Time? Part 2: What is a torrent?

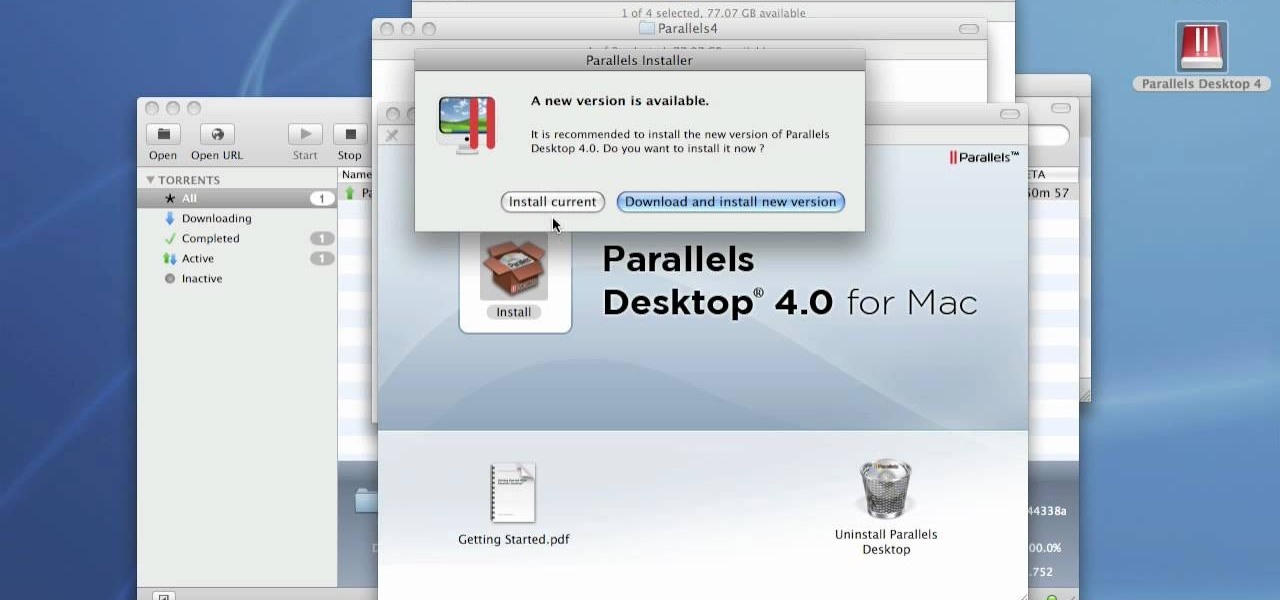
How to Install Parallels 4.0 on your Mac

Increase speed, here and now! Yes, you will go super fast with tons of seeds, so quit whining. Torrents with ten to twenty people are another story. Tons of people complain that their torrent downloads go slow because they're scared of prosecution, which means they limit the upload rate for fear of the RIA.

This video tutorial from knif3r2 shows how to install and run Mac OS Leopard on PC using Virtual Machine.

The video shows us how to use audacity to record audio. Firstly you need to have the software audacity installed in your system and for that Google and search for 'audacity' and after that you get a link to save and install the software. Once the installation is done, open audacity and on the drop down menu the default is set to microphone, change that to stereo mix and copy my settings. Once this is done we will be recording the audio. Go to a site like youtube and press the record button in...

Do you want to play Brink, but don't feel like paying for it? This video will show you how to download Brink and crack it, so you can play for free. You'll need to download Alcohol 120% and a torrent in order to make this work.

See how BitComet can handle more than just torrent downloads. Watch this software tutorial video to learn how to drag, drop, and download with the program BitComet. This how-to video is geared toward beginning BitComet users.

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

I loved the original Star Wars trilogy when I was a kid, but loathe all of the current DVD, Blu-ray, and streaming versions available today. Ever since 1997, every version of A New Hope, The Empire Strikes Back, and Return of the Jedi has had horrendous CGI effects added in that George Lucas deemed necessary to bring his "ideal" version to life.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

This step-by-step tutorial will show you how to install Mac OS on Windows 7 on Virtual Box. Video: .

These days, there are Android apps for every budget—forgive me if that sounds like a car commercial, but that's just the way things are in the age of the smartphone and tablet. You've got apps that require monthly subscriptions, paid apps that will run you a $30 one-time installation fee, and even games that start at 99 cents, but quickly skyrocket in price with in-app purchases.

Hi there, nullbytes :) I've recently seen many questions regarding VMs with Kali, and personally I prefer using a Live Boot USB to get Kali without removing my system (and for many reasons).

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

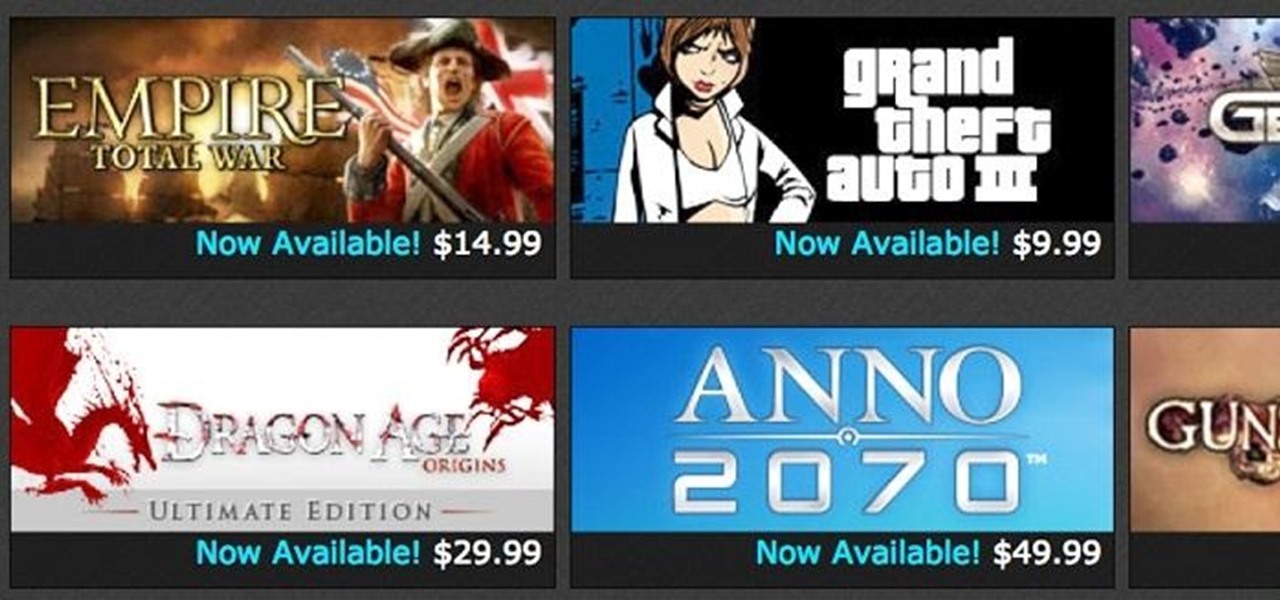
As an avid Steam user, I'm faced daily with high prices for all of the games I want to download and play. It's gotten to the point where I don't even bother going on Steam altogether because I might end up spending a bunch of money I don't have.

'Tis the season to be jolly, and what's more jolly then unleashing a torrent of bullet fire on the opposing team using a LMG emblazoned with a Santa Claus emblem?

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Popcorn Time is an app that streams movies directly from torrents on to your computer, and it's seen its fair share of publicity, being lauded as a free Netflix alternative and chastised as an illegal file-sharing network.

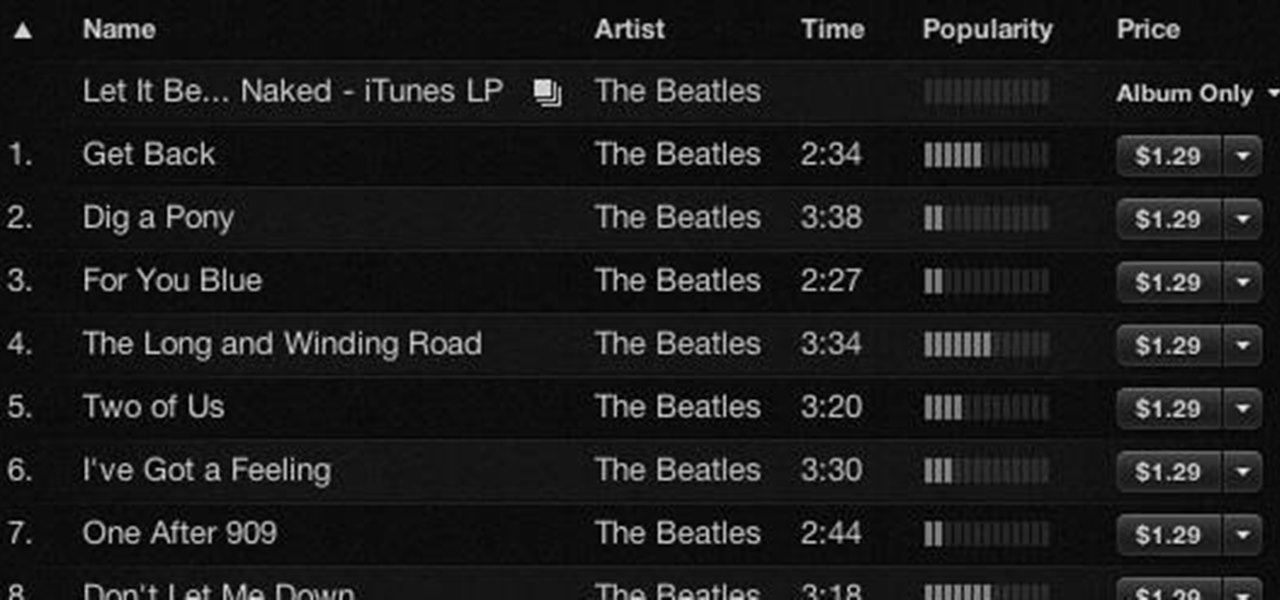
If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

Apple announced earlier this week that the official release date for iOS 6 will be September 19, but why wait when you can get it now? The Gold Master developer version was made available on Wednesday, and it's the same file as the final version that's going to be released to users on the 19th. Anyone can download it, so if you want to avoid being part of the frenzy on Wednesday when everyone else is trying to get it too, it may not be a bad idea to get a head start. A quick note: If you inst...

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

Improving your experience online is getting easier every year. Browsing can be safe, easy, and boundary-less with the right VPN, and gaming online is working better than ever to connect and compete with other players.