Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.
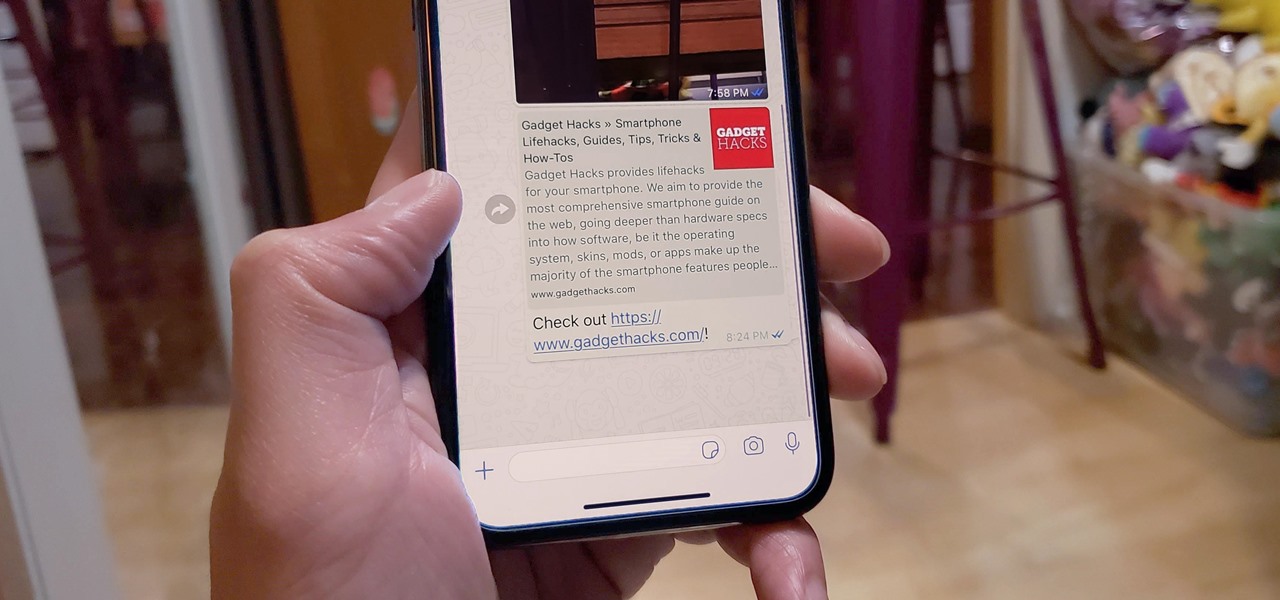
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

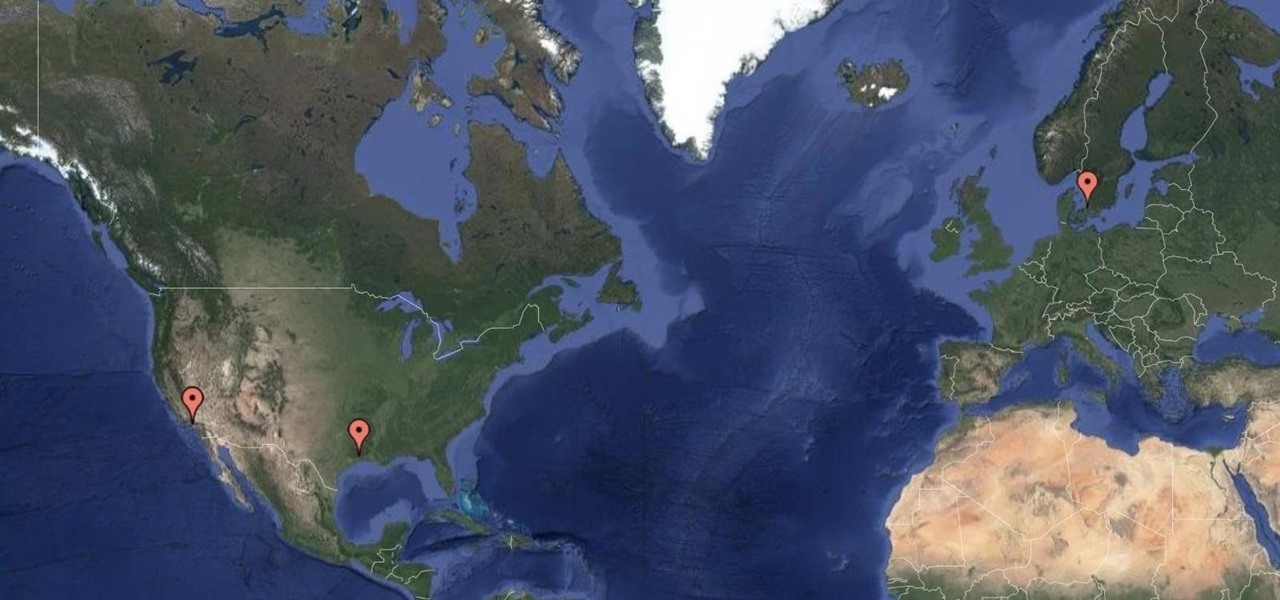
Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

Since its debut, retro thriller Stranger Things and its characters have become ingrained in our popular culture — especially the telekinetic Eleven. For cosplayers, it didn't take long before they grabbed their boxes of frozen Eggo waffles, blonde wigs (or bald caps), and pink smocked dresses to transform into El herself.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

Whether scheduling meetings, events, tasks, or even keeping tabs on the weather, a good digital calendar can help you stay on top of your game in ways that a normal calendar could never do. Indeed, there are many calendars to choose from, but Google Calendar is one of the best due to Google's excellent cloud service, feature-rich web-client, and their easy-to-use Android and iOS applications.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

While iOS offers a plentiful mix of excellent and exclusive features, what you see is what you get. Apple doesn't leave much room for customizability, meaning most people's iPhones look relatively the same. You can make yours stand out, however, by giving your apps unique and personal icons.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

In the latest software updates for iPhone and iPad, there's an even easier way to view all your saved Wi-Fi networks and credentials and share them with family, friends, and others who need access.

Apple has revolutionized how we write with the introduction of its new Writing Tools, powered by Apple Intelligence. In beta on iPhone, iPad, and Mac, these tools allow you to select text and use intelligent features to summarize, proofread, or rewrite it until the tone and wording are just right. In a future beta, Writing Tools can even write original content for you.

Apple last month released iOS 17.2, its biggest iPhone software update since iOS 17.0, with 60 new features. Now, as of Jan. 22, we have iOS 17.3. Overall, it's not the behemoth software update that iOS 17.2 was, but it has a few exciting new things you'll definitely want to know about.

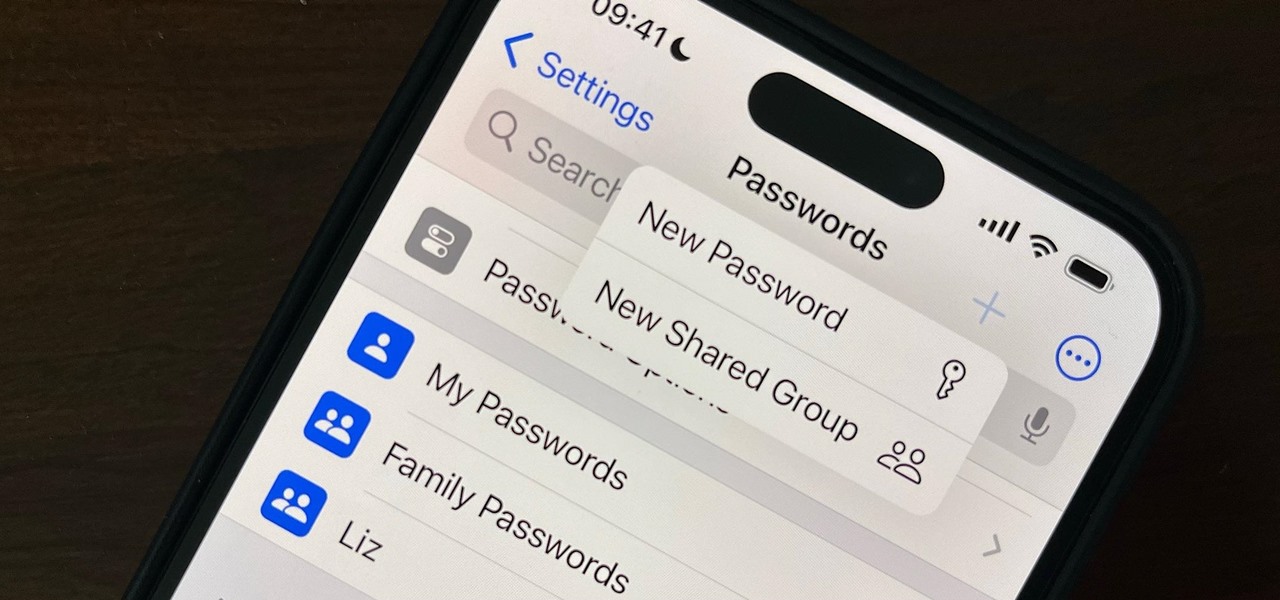
Previously, you'd have to use a third-party password manager on your iPhone, iPad, or Mac to securely share passwords with other people or groups outside of AirDrop range. And while apps like 1Password, Bitwarden, and Dashlane let you store passkeys, only 1Password has added support for passkey sharing so far. Now, Apple itself makes sharing passwords and passkeys much, much simpler.

With iOS 17, Apple News integrates more deeply with Apple Podcasts and Apple Stocks and has become a bit more fun thanks to new crossword puzzles. But that's not all that appears in the updated News app.

While the iPhone came before the first Android smartphone, every new iOS version seems to include a wealth of features already existing on Android, and iOS 17 is no exception.

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

You may use Safari on your iPhone or iPad to open links and browse the web, but there's so much more it can do for you. On updated software, you can implement third-party Safari extensions in your browser that go above and beyond content blocking, sharing, and performing basic actions.

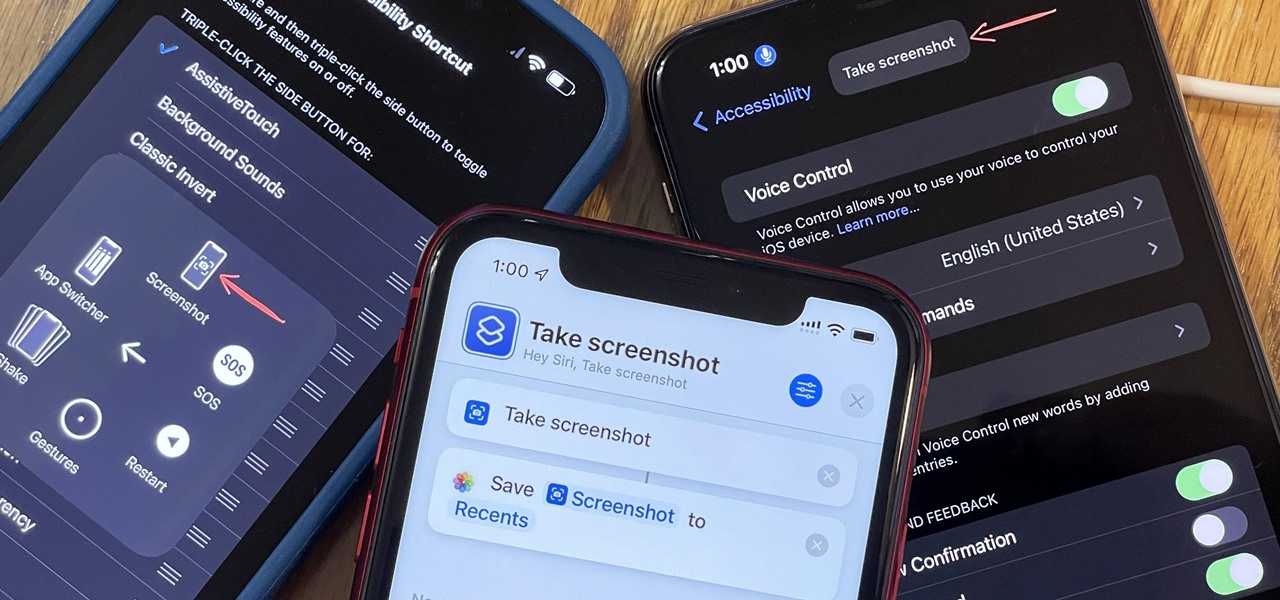
Using an iPhone isn't difficult, but it can be if you're using it for the first time, especially if you switched from an Android phone. That's primarily because of the massive difference in the user interface between the two operating systems. And when it comes to taking screenshots, you have more options than just using the hardware buttons.

Amazon really wants to make itself at home in your home. Like, everywhere in your home, from your doorstep to your kitchen, your kids' rooms, and everywhere in between.

Over the past week, practically every major tech company working on augmented reality has held their quarterly earnings calls with investors, and each addressed or at least mentioned the role of AR during their prepared remarks. However, Facebook's earnings call had some of the spicier commentary on the technology.

Brands are increasingly adopting augmented reality to promote their products and services, and they have multiple paths for bringing AR experience to their audiences.

In these times of social distancing, video calling is becoming the technological substitute for face-to-face connections. For those who carry an iPhone, the art of video calling defaults to FaceTime, the native app on iOS that is exclusive to Apple devices. But what do you do if you or the other party is on Android?

The makers of arguably the two most important mobile AR apps, Niantic and Snap, both had good news this week, with the former preparing to replicate its success with Pokémon GO for another franchise and the latter notching another popular augmented reality Lens for Snapchat.

On June 7, Apple will reveal to developers what's in store for its upcoming operating systems, but anyone can watch the livestream to see all the new features coming this fall to iOS 15, iPadOS 15, macOS 12, tvOS 15, and watchOS 8.

Google and Snap held their annual conferences this week, and both companies managed to upstage their new AR software features with fantastic new AR hardware.

The tech world was taken by surprise this week with the unexpected unveiling of Snap's augmented reality Spectacles smartglasses.

Sure, Microsoft has mostly marketed its HoloLens headsets towards enterprises and developers, but we learned this week that, like every other tech giant, the company is working on a consumer-grade AR wearable. Speaking of consumer smartglasses, Apple made another strategic investment this week that has implications for Apple's AR future.