
How To: Play backline positions in a game of rugby
Playing backline in rugby is an important position on the field. Learn how to play rugby, including rules and skills, in this video rugby lesson.


Playing backline in rugby is an important position on the field. Learn how to play rugby, including rules and skills, in this video rugby lesson.
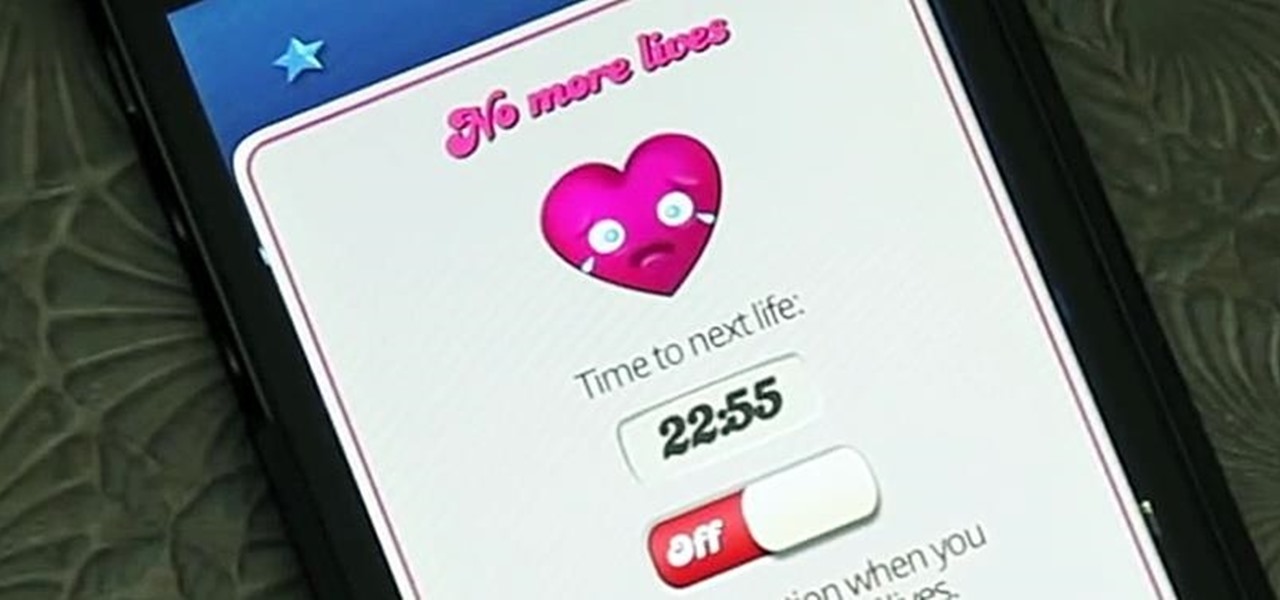
I hate waiting to play, and I hate bugging my Facebook friends even more. But that's what Candy Crush Saga makes you do if you want to get new lives and levels faster.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.
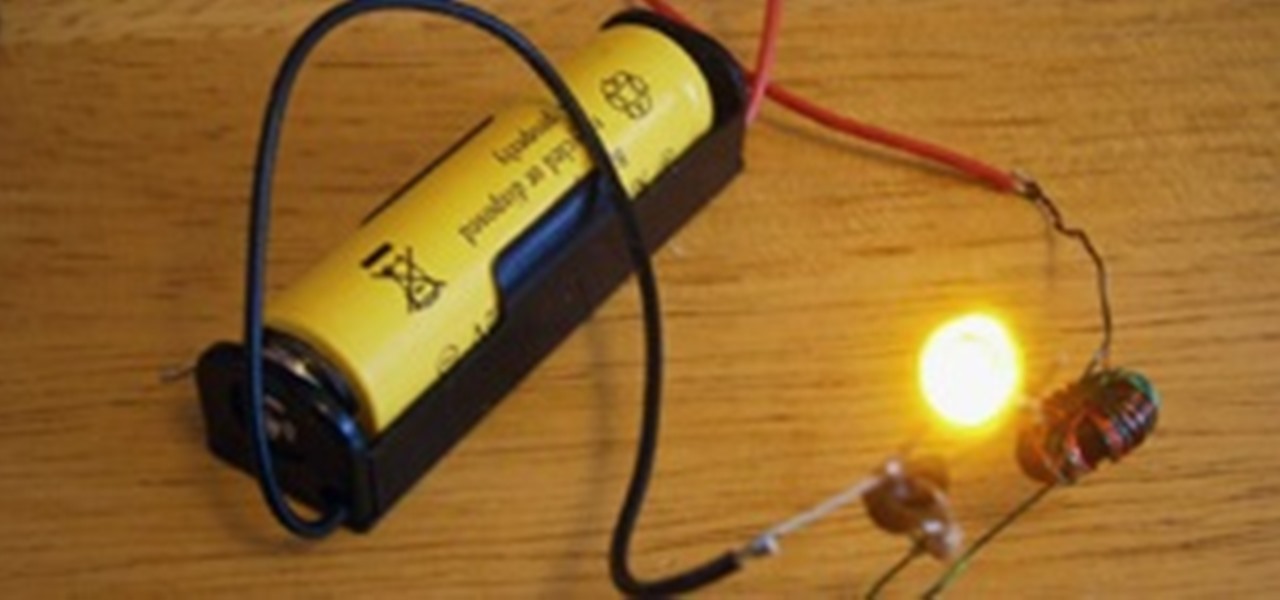
Just about every household gadget we own runs on 1.5 volt batteries of one size or another. Wouldn't it be great if you could reuse all of those dead AA, AAA, and D batteries after they've passed on? It turns out you can make a simple circuit called a "Joule Thief" to reanimate the undead flesh of your deceased batteries and create a zombie battery.

If you need some help rigging a soft plastic fishing bait, this quick video can help. Use tandem rigging to get it done. The tandem rigging is liked when short strikes become an issue. As baits get increasingly longer, the second hook becomes increasingly important. Particularly recommend is tandem rigging on longer baits, such as 14” and 18” models.

Wireless headphones are convenient, comfortable, and more common than ever before. With the massive proliferation of wireless earbuds, it's hard to identify which ones are good and which ones just want to look like they're worth the price. Avanca T1 Bluetooth Wireless Earbuds are high-quality wireless earbuds with excellent functionality and a low price of $29.95 now that they're 50% off.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.
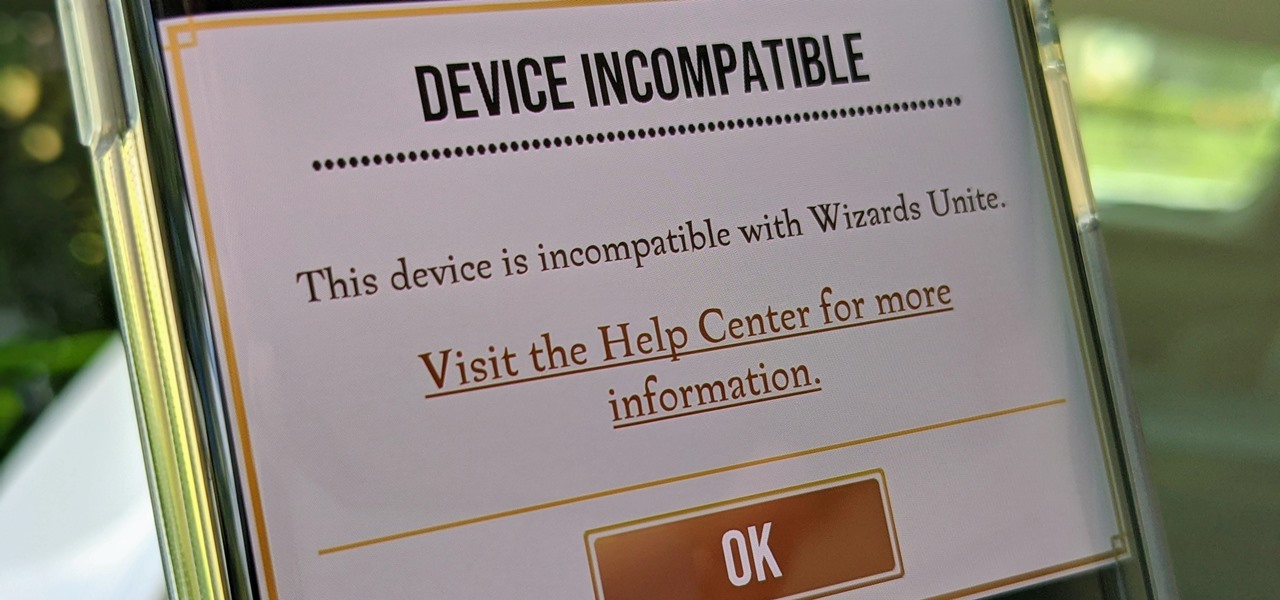
Harry Potter: Wizards Unite has gained quite the fan base since its launch, but not without a few bumps along the way. Niantic, the game's developer, has a long-running history with trying to block all root users on Android. The methods will vary for each game, but this time around with Wizards Unite, they appear to have a new detection feature at play from the recent 2.9.0 update. Let's find out what's going on.

I'm a new parent and I just moved into a new home. The first thing I wanted to do was ensure my toddler's safety in his new digs. That meant buying a bunch of baby-proofing products from Amazon, realizing most were junk, then buying some more until I found solutions for all my needs.
TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

A relatively unknown musician from the early-'70s that's gained popularity stateside over the last ten years just got the remastered treatment with two new reissues available on CD and 180-gram vinyl. And they're available right now.

After playing Mario Kart Tour for a little while, you'll notice it's a bit different from previous games in the series. The biggest change is how they've deferred to new players by automating many of the controls. But what if you want the traditional experience? We've got you covered.

It happens to all of us. You're ahead of the pack, clearly in first place, when someone launches the Spiny Shell (aka, the blue shell). It catches up and circles you before crashing into your kart, and there's seemingly nothing you can do about it. But what if I told you there are two ways to avoid this fate in Mario Kart Tour?

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

Describing how and why the HoloLens 2 is so much better than the original is helpful, but seeing it is even better.

Four months have passed since Mojo Vision emerged from stealth, and we are no closer to seeing exactly what its "invisible computing" technology looks like.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

The story of Meta and its Meta 2 augmented reality headset isn't over, there's a new development that could impact its ultimate fate.
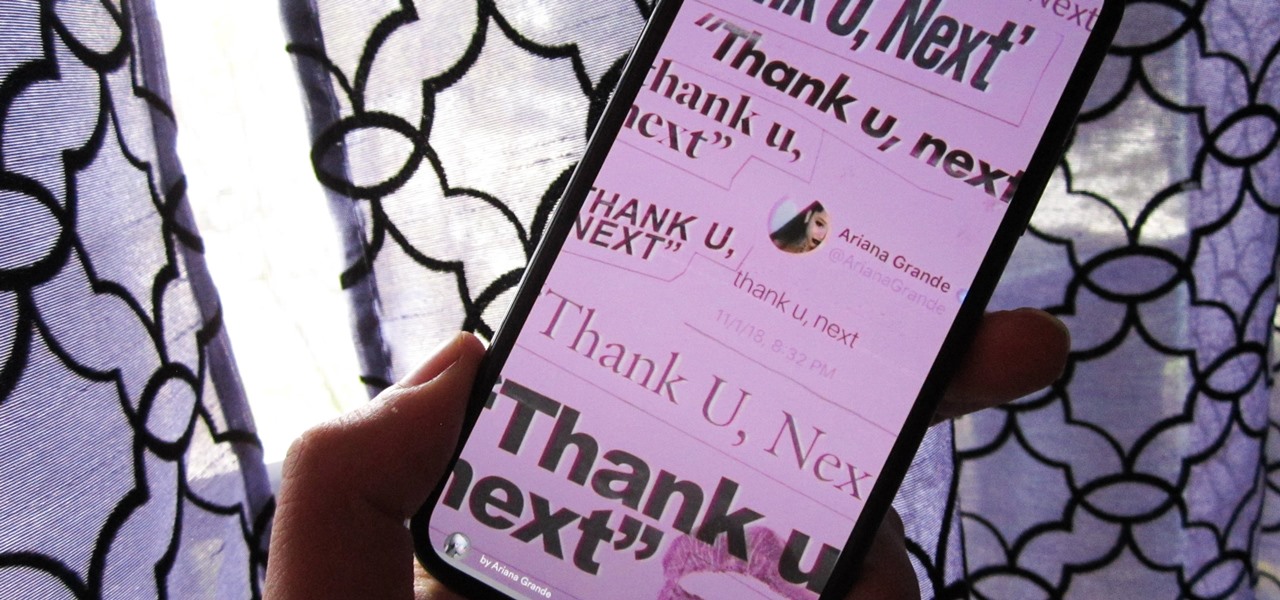
Back in 2018, Spotify began testing a new mobile feature that has grown very tiresome: three to eight-second looping videos that take over the entire screen. Known as Canvases, they effectively hide the cover art and lyrics of the current song — and they're still very much around to annoy and distract the hell out of you. Thankfully, Spotify has also included a way to get rid of these things.
The ability for apps and devices to determine the precise location of physical and virtual objects in space is a key component of augmented reality experiences, and the latest advancements in Bluetooth technology may have a hand in facilitating such location services in the near future.

Although next week will mark the late David Bowie's 72nd birthday, his fans and admirers are the ones receiving a gift in the form of an augmented reality app that explores the artist's career

While Leap Motion has given makers a DIY solution for building their own augmented reality headset with Project North Star, a self-described "AR wonk" has taken the blueprints one step further by creating an untethered version.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

Thanks to leaks that let us try out the latest Android Pie beta on the Galaxy S9, we already have a good idea of what the update has in store for Samsung's flagships moving forward. As we've come to expect, Android 9.0 brings a slew of notable updates, such as the addition of a system-wide dark theme and an all-new TouchWiz replacement called "One UI."

So far, consumer augmented reality headsets haven't found mainstream success. That's primarily because no manufacturer has managed to hit the sweet spot between slim form factor, performance, and affordability.
Do price tags on mobile games give you pause? We get it. With so many freemium games out there, it's tough to justify spending three or four dollars on a game for your iPhone or Android device. That's why you wait for moments like this one, as both "Reigns" and "Reigns: Her Majesty" are aggressively on sale.
The Pixel 3 XL versus Galaxy Note 9. Stock Android versus Samsung Experience. When I began this comparison, I thought the Pixel 3 XL would be unfairly outmatched. But after looking at the specs side-by-side, you'll see a different picture. This year, Google delivered a worthy alternative to Samsung's best offering.

Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.
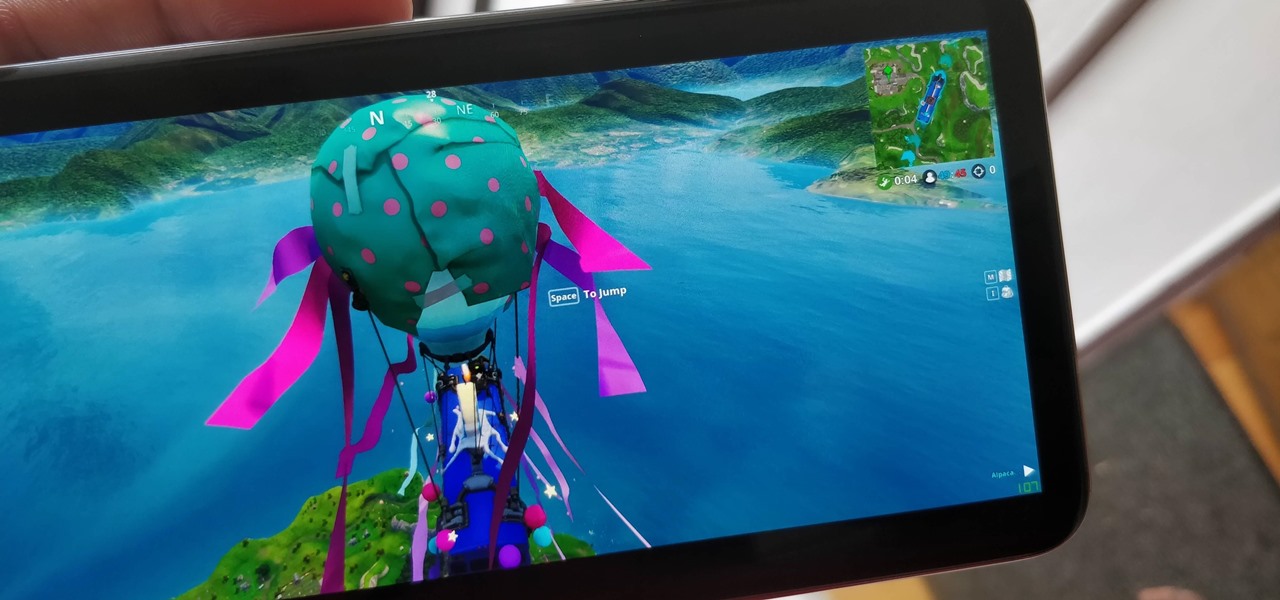
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.
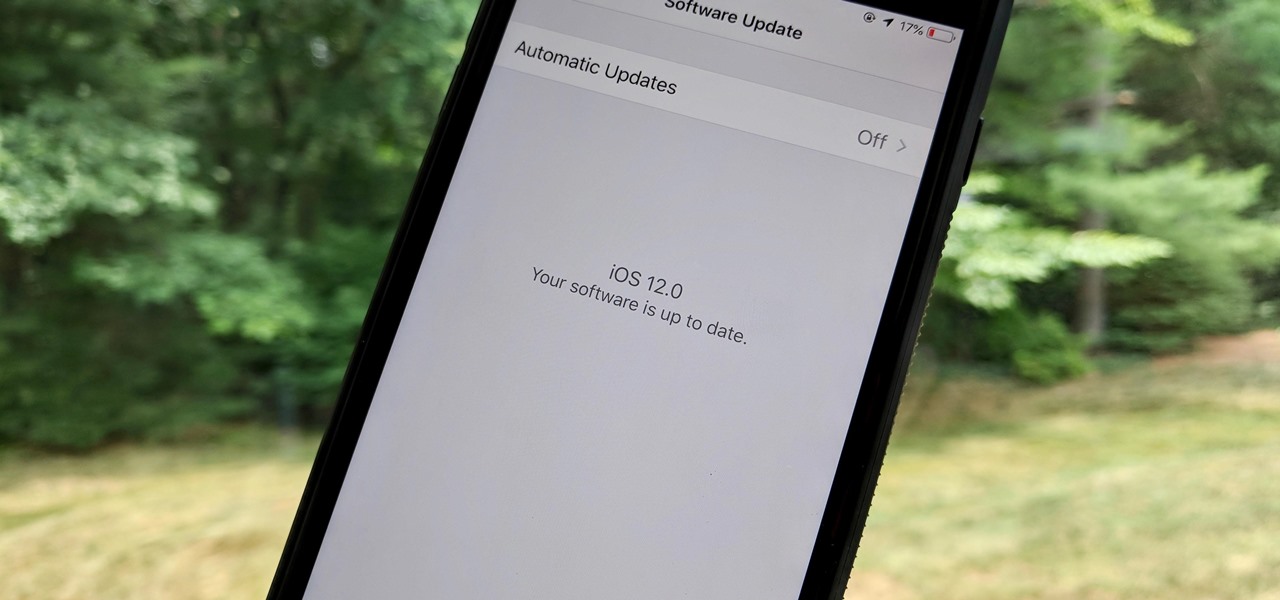
As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

In 2018, notches are the hot trend with smartphones. Essential was first to release a phone with a notch in mid-2017, but Apple kicked off the fad in earnest with the iPhone X. Unfortunately, unlike the iPhone X, every Android phone with a notch has a noticeable bottom chin. Let's take a deep dive to find out why.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

If you're not looking closely, it's easy to mistake last year's Galaxy S8 for the brand new Galaxy S9. Design, build materials, screen size, software — it's all virtually identical, save for a few exceptions. But those minor differences can add up.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

On Tuesday, NBA Commissioner Adam Silver joined Magic Leap CEO Rony Abovitz on stage to unveil a partnership between the two companies.