
How To: Tell if You Have a Cold or the Flu
Have the sniffles? Yes. Does your head hurt? Yes. Coughing? Yes. Could you have influenza? Yes. How do you know the difference? With these symptoms, you could also have a cold.


Have the sniffles? Yes. Does your head hurt? Yes. Coughing? Yes. Could you have influenza? Yes. How do you know the difference? With these symptoms, you could also have a cold.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Despite the availability of a vaccine against it, almost 50% of men aged 18-59 in the US are infected with the human papillomavirus (HPV). Why?

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.
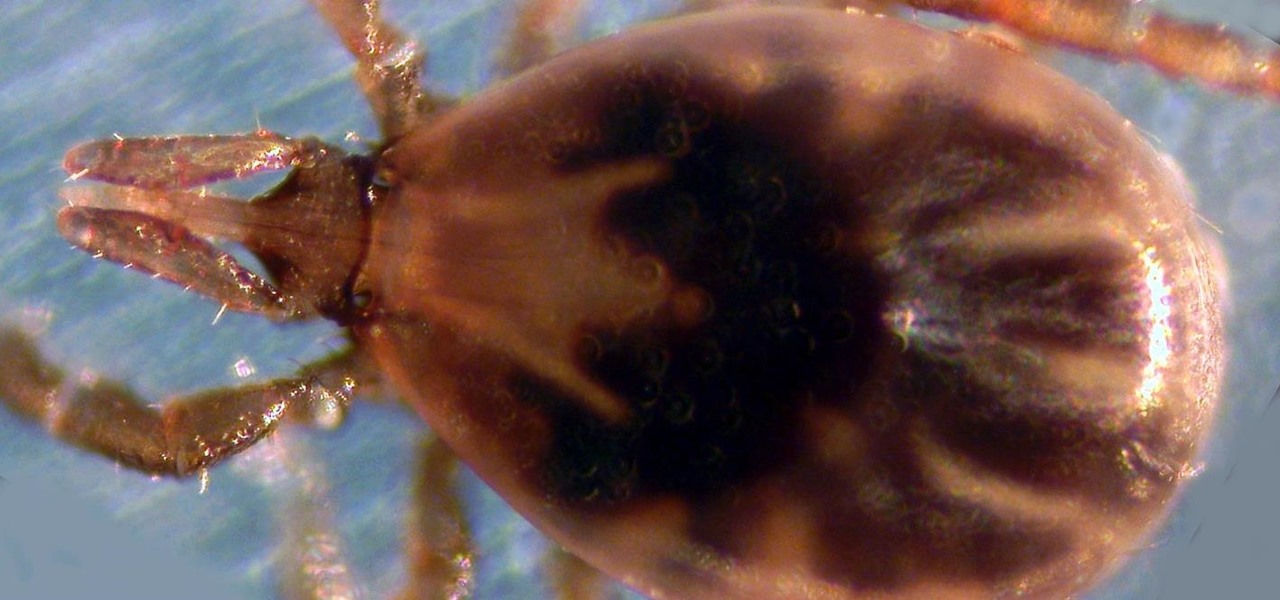
Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

It's become a routine for many of us to ring in the New Year with pledges to finally get our budgets and finances under control. Unfortunately, it's also quite difficult to to keep those promises. Some of us will just dive into our resolutions and wing it as we move forward, which usually ends in failure. But even for those of us who plan carefully, obstacles along the way can spell doom for New Year's resolutions.

With the height of the flu season ahead, there are some good reasons to keep a flu vaccination in mind.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

Pumpkin pie is a symbol of autumn, and it's the traditional dessert to whip up for your fam when Thanksgiving Day arrives. But year after year of the same old thing can be a total bore if you're not a strict traditionalist. So, we found 8 unique ways to make that pie a little less snooze-fest and a little more interesting.

To some people, Thanksgiving is merely quality time with family and friends that they can't get throughout the rest of the year. To others, it's that one time when it's okay to be a greedy hog and get hammered all weekend long.

With folks drawing lines in the sand before the upcoming election this November, it's important to know where you stand on some of the most important issues: the economy, foreign affairs, domestic affairs, and apples—caramel or candy apples, that is.

Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

Fondant looks pretty, but man, it sure does taste weird. Don't Miss:

I'll admit it: I ignore expiration dates. No matter if it's a sell-by date, "best if used before" date, or even a use-by date, I don't care. I just check for signs of food decay and keep on eating.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.

I remember the first time I used coconut oil; the whole kitchen was filled with a fragrant aroma that reminded me of the tropics. After learning it was a healthier alternative to traditional cooking oil—not to mention a great source of the good-for-you saturated fat—I was hooked.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Polenta can cause risotto-like anxiety for the most experienced cook. First of all, making polenta is time-consuming—it can often take upwards of 45 minutes (unless you use this shortcut). And in the midst of this long cooking time, you're constantly stirring to keep the polenta from becoming lumpy. Even after taking the utmost of care, the polenta can still turn out too loose, too firm, or too grainy.

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

There is a huge myth that most Americans believe, and it might be the marketing triumph of the 20th century. We pay an absurd markup (Zero Hedge says as much as 280,000% for "designer" water) on something we can get for free because most of us believe that bottled water is healthier than tap water. But is it? Here are 5 reasons why tap water is probably better than that bottled stuff you drink. 1. It's Not Cleaner (& Might Be Dirtier) Than Your Tap Water

Why did I write this when they're tons of scanning tools available.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Most mobile games have moved to an online-only format, meaning you need to be connected to the Internet in order to get any kind of multiplayer action going. This is great when you're at home on Wi-Fi, but when you're out and about, slow and inconsistent data speeds can cause serious lag. Or worse yet, you may be nearing your monthly data cap!

After you have registered to this site,sign in then to start missions. Basic Missions

The fridge is the heart of the kitchen; take it away, and the whole operation falls apart. Yet, despite this, the fridge is also one of the most overlooked appliances in any kitchen. Most people organize their drawers and shelves for maximum efficiency, while many others buy islands simply to make their culinary playground more space efficient. Heck, I know some people who have passed up on otherwise great apartments because the counter space simply wasn't large enough.

If you're feeling stressed, there are many home remedies you could use for relief. Meditation, yoga, acupressure, an ear massage, more sleep, shower soothers, playing video games… the list is endless. But a lot of these methods require a significant amount of time, so what do you do when you need immediate stress relief?

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.

Job interview success can be a difficult thing to measure. Is confidence a job-winning trait? Or were the interviewer's questions not answered as fully as they had hoped? Maybe you weren't sure how your big, happy smile went over with such a formal setting.

Cooking with animal blood is as old as civilization itself. I promise that your ancient ancestors, no matter where you're from, didn't have the luxury of throwing away any part of the animal, including the very lifeblood that used to run through it. Animal blood, along with everything but the skin, would invariably end up in the stew.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Lasagna, that layered, creamy baked pasta dish, is a lovely comfort food that's great for a crowd. But if you've ever made it, then you know you're usually left with some leftover lasagna noodles. (Although that's always better than the frustration of running out of the noodles while you're still making a traditional lasagna.) Still, what do you do when you're still left with a bowlful of the wide ribbons?

I'll admit it: I've spent many eight-hour workdays stuck at my desk, staring at my computer as my breaks slip past unnoticed. I frequently tell myself I'll take one in a few more minutes—but somehow, the entire day will pass and I won't have taken a single break.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.