Having an open-source platform like Android is great, allowing manufacturers and developers the ability to make their own skins and apps to truly customize the end-user experience. The only downside is that when an update comes to vanilla Android, many of us are left in the cold, unless you have a Google Play Edition HTC One.

Snapchat is great for sharing and receiving pictures that we don't want "living" for too long, but sometimes we'd like to hold onto those memories, whether the other party wants us to or not.

The status bar is an omnipresent force on our Samsung Galaxy S3s; always there to give us that vital information about battery life, date and time, Wi-Fi access, and much more. But there's just something about that default black bar that's so...boring.
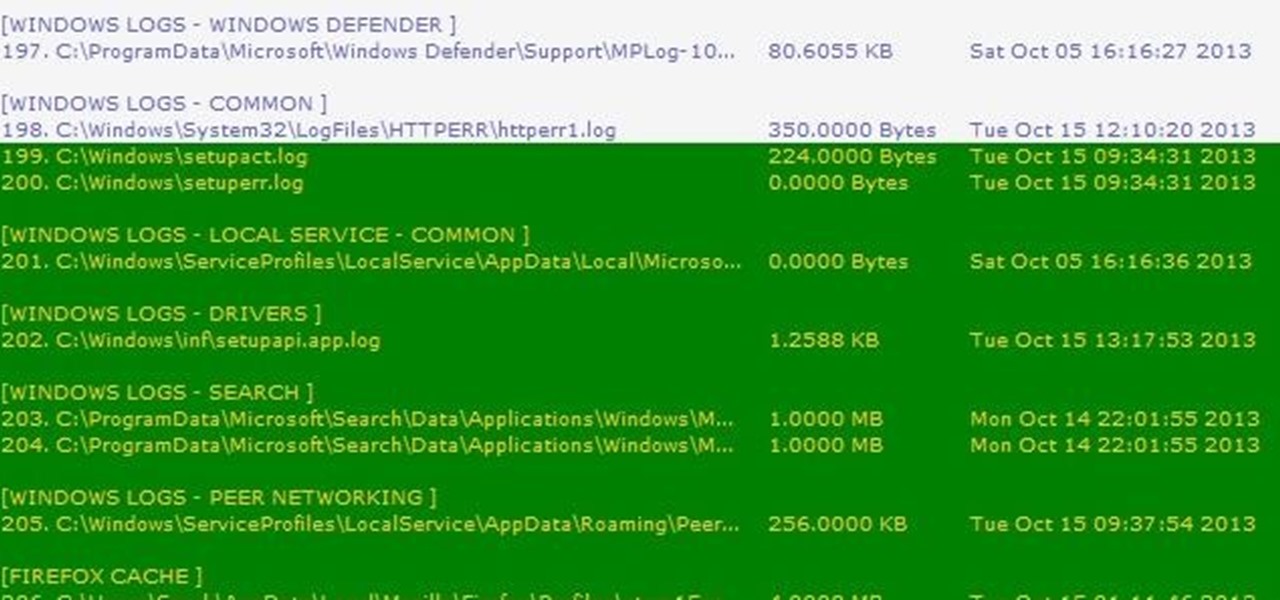
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

A lot of you are enjoying a nice winter snowfall right now. Some of you aren't enjoying the snow at all, especially if your car's stuck in it or you have to grab the snow shovel, yet again. But perhaps you'll change your distaste for snow when you try out some tasty homemade snow cream!

Portrait drawings are difficult for most artists, but one thing's for sure— drawing nerds is as easy as they come. Nerds are easier to draw because you can stray from the formality of portraits, putting your own spin on it, over-compensating the details, exaggerating the dorky features. It's a drawing class in its own, and Merrill shows you how to draw his version of the NERD!

Keeping your supplies of caps and ammunition high in Fallout 3 is one of the game's biggest challenges. No more! This video will teach you how to use a glitch in the game's shopkeeping interface to attain unlimited caps, ammunition, and free item repairs. You should have no trouble beating this epic game after following these instructions.

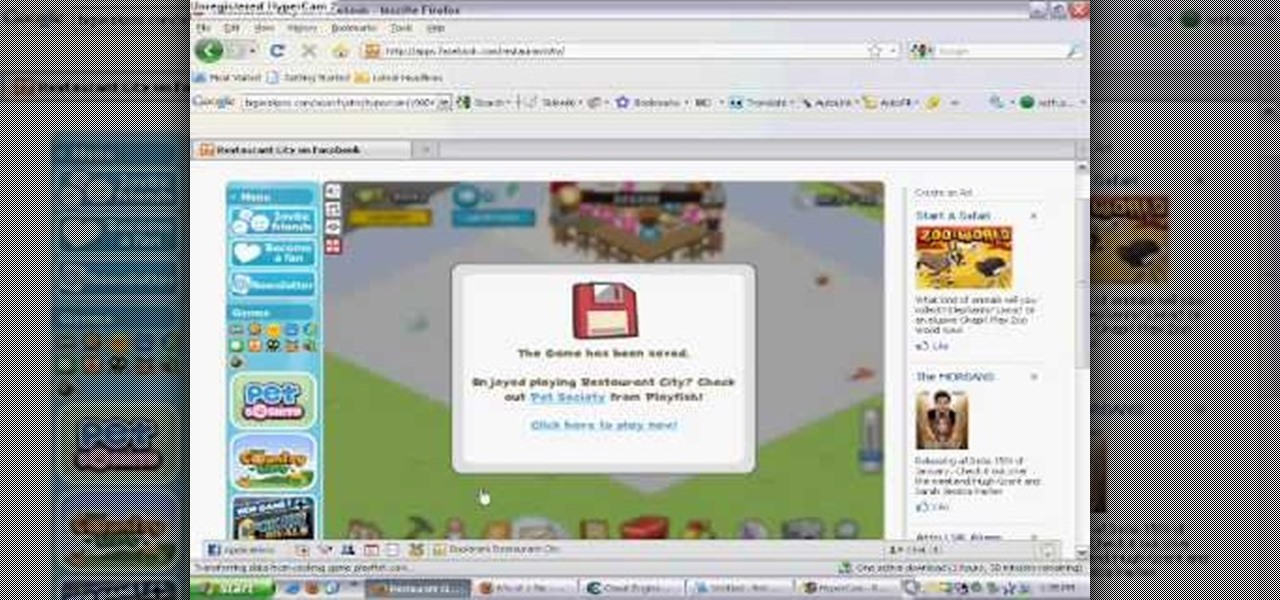
This is one of the easiest Restaurant City hacks out there… the rubbish hack. All you need is Cheat Engine and very little time. Very easy to complete.

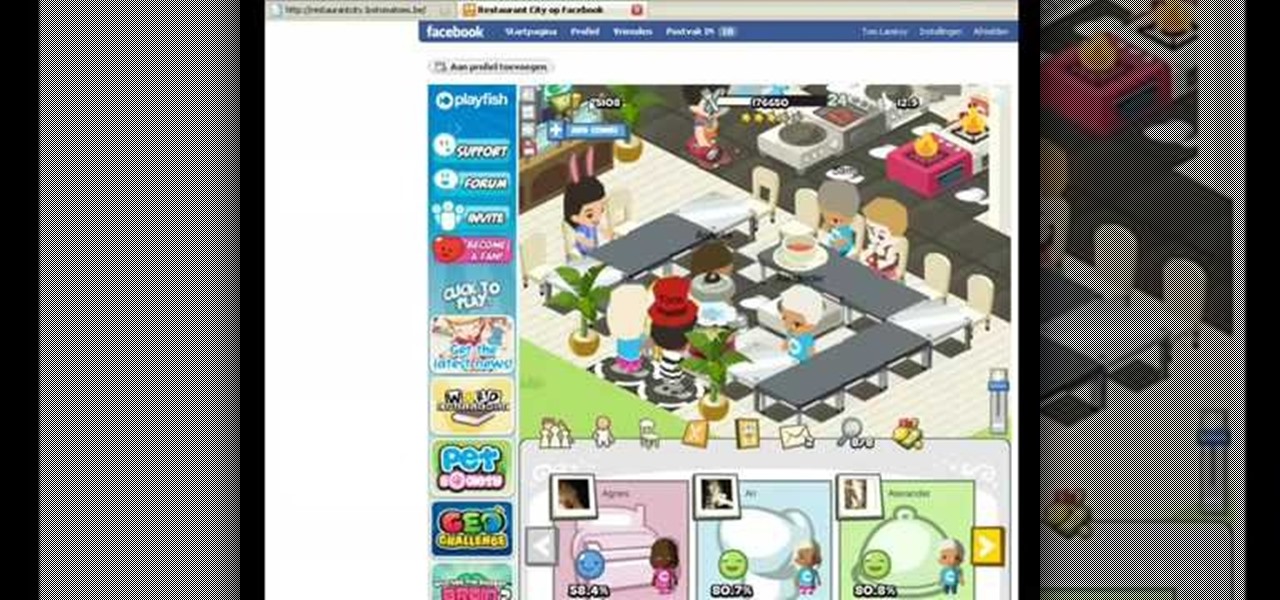
Need a little more cash on Restaurant City? That's easy. Hack money to get your desired amount. Just get Cheat Engine.

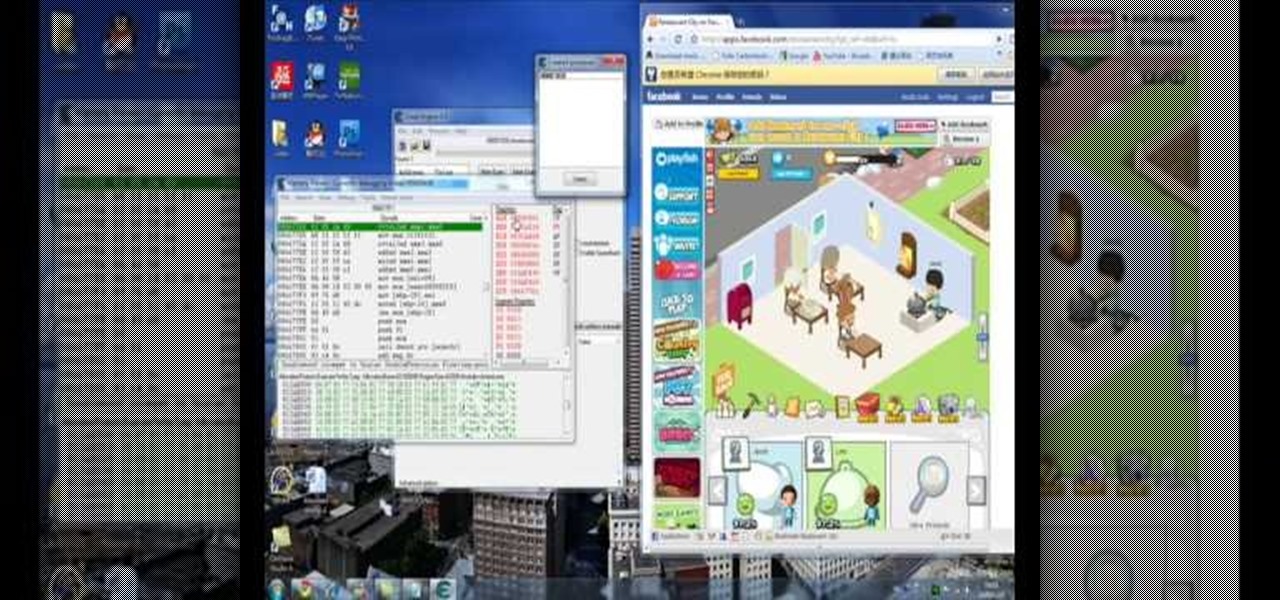
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

No need to run home from work to change for an evening on the town. With some simple switches, you can be on your way. Follow this Howcast guide to learn how to change your look from day to evening in just five minutes.

If you're a LARP maniac, or just a fan of LSD-themed (Latter-day Saint) games and activities, then this tutorial is perfect for you. Watch this video to learn how to make a foam-padded sword that is easy and inexpensive. This level one boffer sword will take care of your LARPing opponents in no time. If you're a fan of live action role-playing, then this boffer sword is just the beginning. The first video shows you step-by-step how to make this foam sword for awesome LARPing. The second is ju...

Puzzles include multiple pieces each with a designated pattern so that when a user regroups the pieces, a picture or a particular image is presented, which provides practice to the coordination of the user's concept to space and structural relationship between pieces. However, no matter how large the quantity of the pieces is, puzzles only provide user's spatial concept in two dimensions. To enhance spatial concept and increase entertainment to the user, building blocks are promoted so that u...

Under the rocket's red glare and the bombs bursting in air, the Statue of Liberty is swaying in celebration this Fourth of July thanks to Snapchat.

On Friday, at IFA 2018 in Berlin, Samsung invited attendees into the residence of Family Guy's Griffin family to learn all about its "smart home" products via augmented reality.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

With the official launch of Magic Leap One expected by the end of summer (translation: days from now), Magic Leap's hype machine just took a big hit with the sudden loss of a key marketing executive.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Flying under the radar during Magic Leap's big week at the Game Developers Conference, the company settled a potentially ugly lawsuit with a former employee.

This year will be an interesting one for iPhones. With speculation that the expensive iPhone X is underperforming, rumors have circulated that Apple will release three "bezel-less" devices, one of which will cost less by omitting the OLED panel for a traditional, yet large, 6.1" LCD. Now, thanks to the source of this rumor, we have an idea how much that lower-tier iPhone will cost.

Enterprise augmented reality developer Atheer is bringing its AR solution for enterprise businesses to the HoloLens by way of a joint venture with fellow AR developer Design Interactive.

Using the CES tech conference in Las Vegas as the launch pad, Dell has announced that it's partnering with Meta Company to offer its augmented reality headsets to business customers.

Now that it has buried the legal hatchet with Meta Company, augmented reality startup Dreamworld has announced plans to open up pre-orders for its Dream Glass AR headset.

Apple has billed ARKit as a means to turn millions of iPhones and iPads into augmented reality devices. The refrain is similar for Kaon Interactive, a developer of product catalog apps for businesses.

Companies are already clamoring to figure out strategies for integrating augmented reality into their advertising platforms. AR is going to become a huge asset to marketers, and Apple's ARKit is only going to help that along. Mixed reality producer Bilawal Singh Sidhu has given us a sneak peek of what the world of advertising could be with the ARKit.

Baidu signed a cooperation agreement on June 7, the first day of the CES Asia conference, with multiple companies in the autonomous vehicles industry. The companies listed in the press release include Desay SV, United Automotive Electronics, and Hangsheng Electronics, as well as possibly additional auto manufacturers. Baidu plans to "jointly develop" upcoming intelligent driving production plans.

Any parent with a rambunctious child who may have at one point racked up a hefty bill on their Kindle or Android device can now breathe a sigh of relief. One, Jack Black has had it happen to him too, and two, Amazon will be refunding up to $70 million of in-app purchases made by children after downloading apps from the Amazon AppStore.

Uber resumed its pilot program for driverless cars after one of its autonomous vehicles crashed in Tempe, Arizona last weekend.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

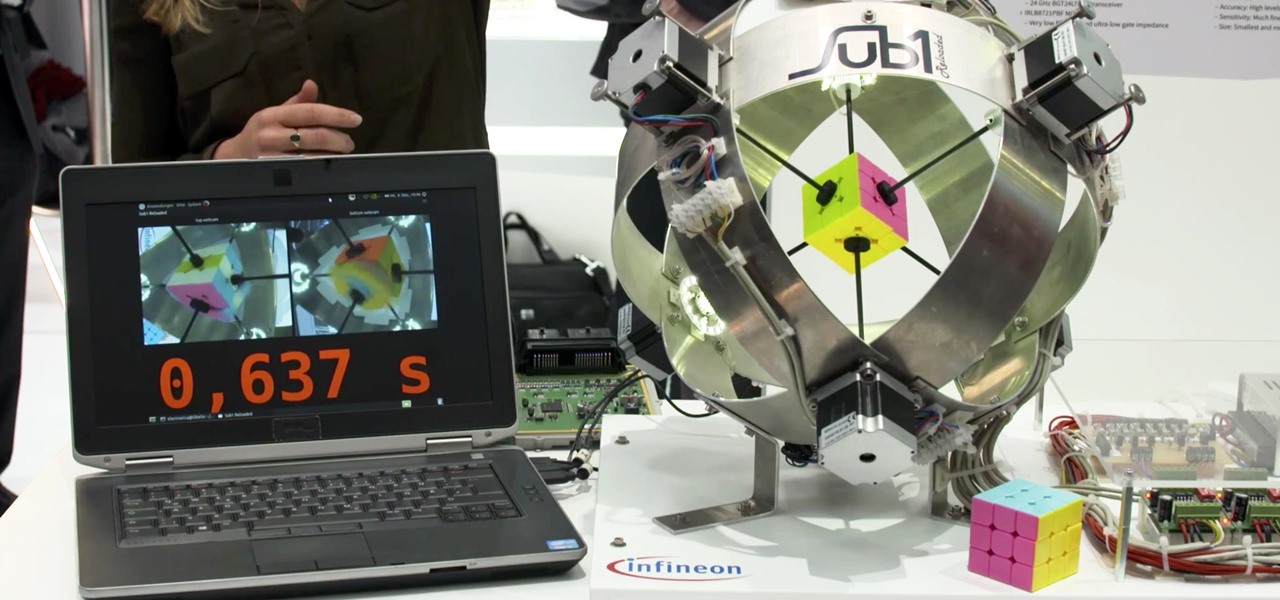
In December of last year, Australian Feliks Zemdegs broke the human world record for solving a Rubik's Cube with a time of 4.737 seconds. Well, this robot did it way, way faster by solving one in under 1 second. Don't tell me a robot takeover isn't real possibility.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

Apple's new iPhone 6 and iPhone 6 Plus go on sale Sept. 19th, but pre-orders begin on Sept. 12th. If you're ready to trade in your iPhone 5 for one of these bigger and more iOS 8-friendly devices, you're probably going to pre-order.

Over the weekend—just days before Apple's big event—an actual iPhone 6 leaked on Chinese site cnBeta. Again, nothing here that we already didn't know about—Sapphire screen, round(er) corners, larger display, and new button stylings. Below are images of the new iPhone 6 next to the current iPhone 5S. We can clearly see the protruding camera module as well as sections on the top and bottom of the back where the antennas will be housed. A second source was able to put together some videos, as yo...

The release of the Nexus 5 marked the debut of the Google Now Launcher. Even with an integrated Google Now page on your home screen, the most talked-about feature was actually the always-listening functionality.

It looks like Snapchat, it feels like Snapchat, but after using it for a few minutes, you realize there is a huge difference between Facebook's new Slingshot app and the Snapchat we've all grown so accustomed to.

E3, or the Electronic Entertainment Expo, is the 20th annual trade show for video games and gaming tech. The event takes place on Tuesday, June 10th at the Los Angeles Convention Center, and you can watch a live stream of the event on Twitch.

Most of us have traded our desktop systems for laptops, tablets, and mobile devices, meaning there's a lot of outdated hardware sitting in attics. Want to give your old computer a new purpose? Matthew Chappee turned his iMac G4 into an HDTV using the guide by Dremel Junkie. One thing to note before you take on this project yourself is that if you want to use it to watch cable, you'll need a converter box to get around the MPAA's HDCP restriction. But, a converter box is considerably less expe...

Sea otters are the largest members of the weasel family. When people started hunting sea otters for their fur, their population fell from roughly 225,000 to about 1,500, until the International Fur Seal Treaty took effect in 1911. Since the international ban on otter hunting, the population has rebounded back to roughly 107,000.

If you bought the new iPhone 5, you've probably been less than thrilled with the lack of cases and accessories that you can use it with. Docks are no exception—users were disappointed to learn that Apple has no plans to even make one for the newest addition to the Apple family.

Teach your preschooler to improve their sight, touch, hearing, and smell with Montessori activities. Learn how to use Montessori materials to teach preschool in this free video series.