Apple's iOS 11 release promises many improvements and fresh ideas. One of those new ideas is an image codec called HEIF (similar to HEVC for videos), designed to reduce the space photos take up on your iPhone. But it's so new that it's already causing issues with compatibility.

While the Mail app didn't get as much love from Apple in the iOS 11 update as Maps, Photos, Safari, Siri, Camera, Messages, Notes, and the App Store did, there are still a few new features you need to know about when emailing on your iPhone.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

From all the demos we've seen, we know for sure that the marketing world is going to change drastically thanks to Apple's ARKit.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.
There are many different ways and many different apps that allow you to censor a racy photo and then share it to Instagram or Facebook. If you're in a time crunch and don't have the time or the patience to deal with something like Photoshop, then Snapseed is a great and easy app that will blur out your raunchy images in a quickie.

Sports gaming company ePlay Digital, Inc. is looking to capitalize on the fall launch of iOS 11 and ARKit with an augmented reality fantasy sports app.

Map apps, while incredibly helpful in our technology-centric world, can often be a source of frustration. No maps app is perfect, and things can get confusing fairly quickly when trying to navigate GPS mapping. iOS developer Andrew Hart has experimented with a new way of mobile mapping using Apple's ARKit that could make finding your way so much easier.

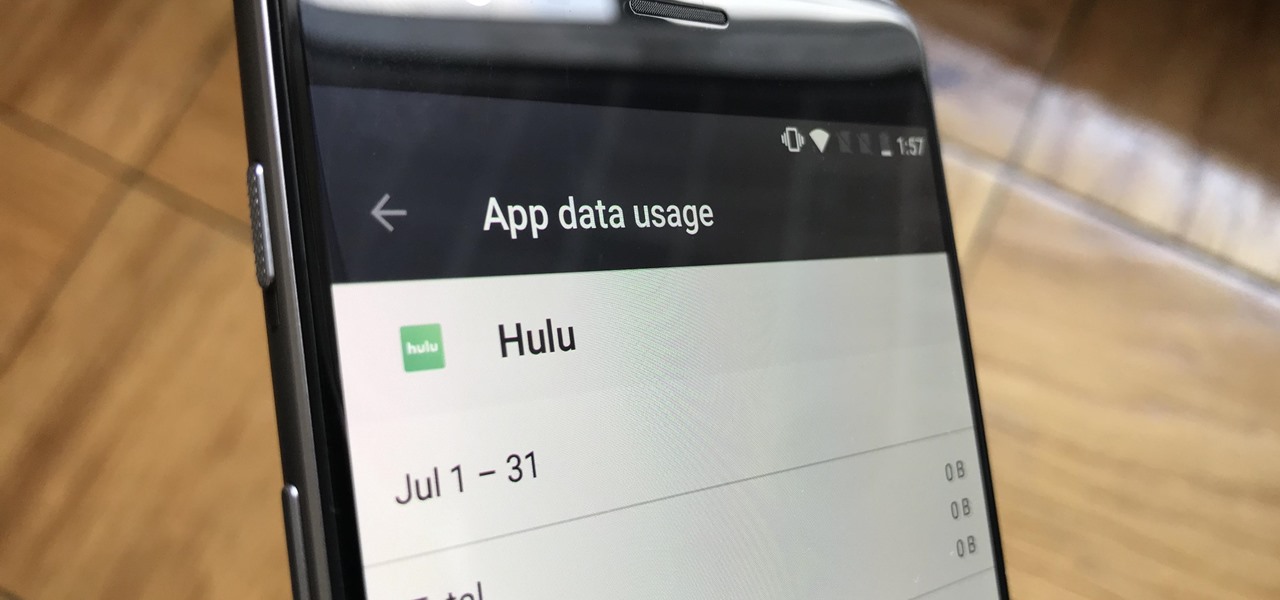
It seems almost every carrier now has an unlimited data plan, and free Wi-Fi is now available in more places than ever before. If you want to be connected, it has never been easier — but that still doesn't mean that everyone can stream as much as they please.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

Bitmojis are not only a good way to personalize your Snapchat account, but also a really fun Snap addition to play around with. A bitmoji is basically like your little avatar, letting you design your mini-self whichever way that you desire.

When it comes to differentiating from the competition, brands are continuing to leverage augmented reality to give consumers to the point that there are few "firsts" left to achieve in the marketplace. While L'Oreal jumps on the augmented reality bandwagon for cosmetics, Acura finds a new way to make augmented reality a spectacle in the automotive industry.

Ah, the sand between your feet, the sun on your skin, and the debt you're accumulating. However strong my sense of wanderlust may be, I still can't justify dropping thousands of dollars on a vacation. Fortunately, a new site — Wander — promises to help you book vacations that match your budget.

This Fourth of July, stock up on hot dogs, ice cream, and smartphones. Yep, this Independence Day is a surprisingly good time to get your hands on the iPhone SE. If you're interested, head to your nearest Best Buy to check out this major deal. (Or wait for the iPhone 8 to come out ...whenever that will be.)

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

At Facebook's first Communities Summit, admins from top Facebook groups assembled to discuss tools to better manage and optimize their members. Here, Facebook CEO Mark Zuckerberg announced that these changes fuel the company's shifting focus from connecting the world to uniting it.

With iOS 11, Apple's very own Notes app will now come standard with a number of new features that aim to make it significantly more user-friendly and help it compete against more popular notepads like OneNote and Evernote.

It looks like all the unregulated fun and games we were having promoting products on Instagram is about to get, well ... regulated. According to a new report by Mediakix, 93% of celebrities on Instagram are not in compliance with the Federal Trade Commission when it comes to posting paid content.

Full disclosure: I really like Apple's stock ringtones on the iPhone. After all, there are over 50 to choose from if you include the classic ones. With all that choice, why would you ever need more? Personally, I get bored easily, and I'd like my music to play when people call. Apple doesn't let us pick a song from our music libraries, but there is still a way to use our favorite tunes as tones.

Who said sports need parity to be fun? For the third year in a row, the Cleveland Cavaliers are facing off against the Golden State Warriors on the NBA's biggest stage, and basketball fans everywhere couldn't be more excited.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

It really is a pain getting an Apple device fixed ... What's a gal to do when there's jelly stuck in your Macbook Pro fan and no Apple Store in sight? (Yes, this actually happened to me. Stop laughing.)

Deep down inside, Kindle Fires are actually Android tablets — the only trouble is, Amazon has layered so much of a skin on top of it all that you can't normally use Android's main app store, the Google Play Store. The Amazon Appstore, which comes bundled with Kindle Fire devices, only has about 600,000 apps, so it would be great if you could access Google Play's library, which boasts 2.8 million.

Asobo Studios, one of the first companies to partner with Microsoft on HoloLens development, is applying their expertise towards building applications for various business verticals through their internal HoloForge Interactive team.

Monday has been a big update day for Apple. Alongside the release of iOS 10.3, iWork has been updated across both iOS and macOS. The biggest change is the ability to unlock password-protected files with Touch ID, either on iPhone and iPad, or on the new MacBook Pro with Touch Bar.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.

The newest version of Snapseed features three awesome new tools for you photo-editing enthusiasts. The 2.17 update for the editing app was rolled out on Tuesday, March 21, and its new additions are something to behold.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

Apple lets you save webpages as PDF files in iOS 10, but the only obvious way to do this is by using iBooks. The thing is, most people would probably rather save their PDFs to a service like Google Drive or Dropbox to make sharing a bit easier. Plus, iBooks isn't officially available for Windows or Android, so there are some cross-platform problems there, too.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

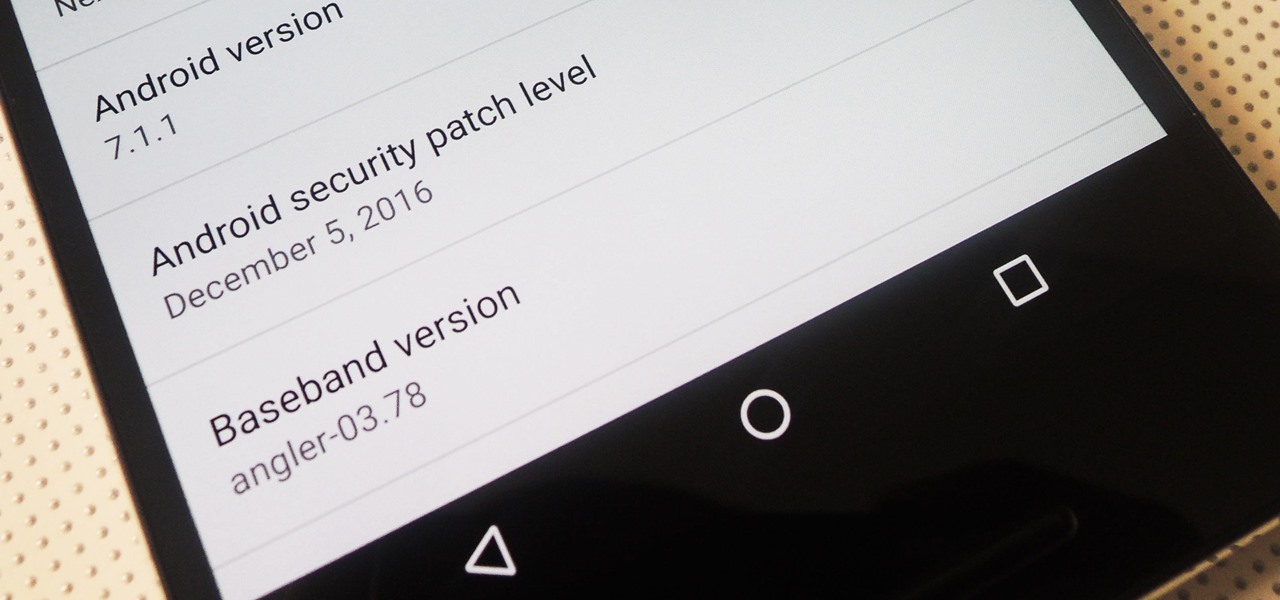
Android 7.1.1 stock images for the Nexus 6P were released last week on December 5, 2016. However, Verizon users seem to have been excluded from the update. Google's factory image page states "All carriers except Verizon" next to version number NMF26F. This doesn't seem fair, especially since Verizon Nexus 5X users received the latest Android Nougat update.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

Regardless of what they call them—be it Pixel or Nexus—Google's line of smartphones have a cool feature called "Ambient Display" that wakes your screen in a low-power black and white state when you receive a notification. This feature was added back when Google owned Motorola, as Moto's phones had a similar lock screen effect called "Active Display."

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

Apple caught a lot of flak for removing the headphone jack in their iPhone 7 models, but they definitely got the last laugh when preorders with a delivery date of September 16 sold out within minutes. Headphone jack or not, the iPhone 7 and 7 Plus are still highly desirable products, and consumers have confirmed this by voting with their wallets.

Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displays—there's really only one thing that separates the Note7 from the Galaxy S7 Edge: The S Pen.

Among the many changes in Android 7.0 Nougat, a less talked-about feature may very well be one of the most interesting. As part of a new system-wide API, apps can now create their own Quick Settings tiles, and it doesn't require any complicated workarounds like it has in versions past.

The iPhone 6s models introduced Live Photos in iOS 9, a cool new camera feature that takes a GIF-esque moving image every time you snap a pic, but the cool factor pretty much stopped right there. You couldn't take them on older iOS devices, share them with non-iOS users, or even edit them.

With each update, Apple Music continues to become a bigger part of iOS. It's gotten to the point where you have to fend off multiple requests to subscribe to the streaming music service before you can listen to your own songs on an iPad or iPhone, but as it stands in iOS 10, maintaining your own MP3 library is still possible. Just barely.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.