Parenting Coach, Nancy Stone provides a few tips and techniques for easing your toddler through the transition from diapers to being toilet trained. First off, Stone suggests allowing your toddler to help pick out their potty seat. Secondly, keep in mind that boys and girls are different - tossing a few Cheerios into the potty and letting your boy aim for them makes it kind of a game, which Stone says is important. Thirdly, ask your toddler quite frequently, point blank "Do you have to go pot...

Next time you don't want to make your bed, dry the dishes or clean the house there's no need to feel guilty. You may be doing yourself a favor. There are legitimate scientific reasons why some chores aren't always the best health choice.

Getting an outdoor itch to start something new? How about the ever-so-fun game of shuffleboard? Begun more than 500 years ago as a game for European royalty, shuffleboard is becoming more popular with Americans who see it as a less expensive alternative to golf.

Looking to make a nutritious change in your life? By choosing the right foods in the right amounts, you can reap rewards that will benefit you in all aspects of your life. In this tutorial, learn how to eat healthy and make positive changes in what you consume.

Shave precious seconds off your running time and you just might win your next 5K. You Will Need

Whether your plane made a crash landing or your ship got lost on a three-hour tour, now you're stranded on a remote island. Here's how to get help.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a free XMPP/Jabber server in ten minutes.

Learn how to practice proper etiquette on a BlackBerry, smartphone or PDA. Make sure your love for your BlackBerry or other PDA device isn't making you obnoxious.

Constipation affects almost everyone at some time. Follow these tips to help prevent it. This how to video lends helpful advice on preventing constipation (and possibly resulting hemmeroids).

Learn how to sink a pool ball into a pocket. What do pool sharks know that you don’t about sinking a ball? Lots.

Thinking of selling your car on the internet? Make sure you don’t get taken for a ride. You Will Need

When it comes to household versatility, baking soda is king. Here are just some of the many cleaning uses for baking soda. Cleaning tips:

The heart needs exercise just like any other muscle. Live longer and healthier by pumping it up! You Will Need

New to electric guitar? You needn't sound that way. This nine-part video guitar lesson series is aimed at those who have never played electric guitar before and would like to try it for the first time. By the end of this series, you'll be playing the main riffs from Deep Purple's "Smoke on the Water," "Satisfaction" by the Rolling Stones, Roy Orbison's "Pretty Woman," and "Stairway to Heaven" by Led Zeppelin. To get started playing any, or all, above the above riffs on your own guitar, take a...

Learn how to use a heavy boxing bag to do speed alternate gut punches. Presented by Real Jock Gay Fitness Health & Life.

New to the sport of archery? Maybe you're trying to hunt that perfect buck? Whatever the case may be, sport or hunting, this eight-part video tutorial series will help improve your beginner skills, to start you on your way to becoming a great archer.

Keep a high traffic floor evergreen using replaceable carpet tiles. All you need is a straight edge, measuring tape and a utility knife. Watch this how to video and grab your equipment to give your living room an entirely different feel.

Safety is of primary concern when driving a vehicle or riding a bicycle. Watch this video tutorial on how cyclists and motorists can safely share the road when the former wants to make a right turn and the latter is cycling straight.

Peerguardian2: Block the RIAA and Malicious IPs +Mac/Win. Doesn't block http traffic though, and it's not very accurate and won't make a difference.

Someday, maybe not today, maybe not tomorrow, but someday, you'll find yourself on the road in your car, maybe on the highway, and you'll hear something.

You can learn how to drive traffic to your website using links. The most important thing is to get people to your website. You can not spend hours and hours writing emails to people who steal your articles.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

The long-awaited Dark Mode may have grabbed all the spotlight with iOS 13, but Apple has made subtle changes across the whole platform to make your iPhone even more user-friendly. A small option aimed at people who are sensitive to motion is one such example — a feature that can also be a godsend for the rest of us.

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

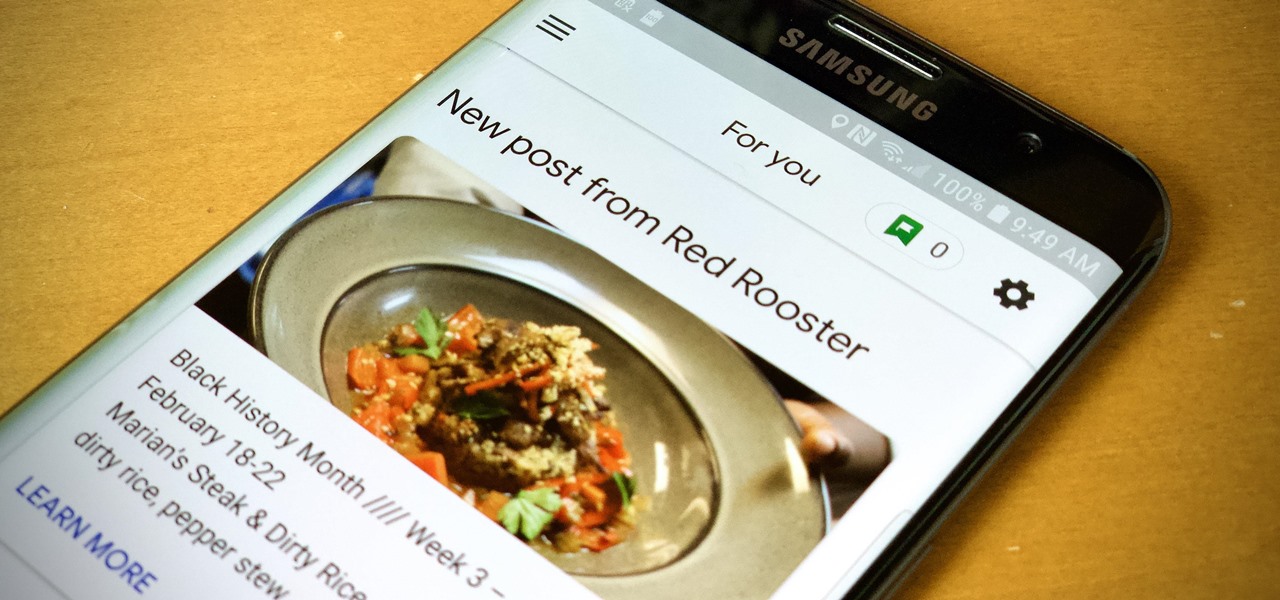
When you need to know how to get somewhere, Google Maps is the app to beat, but the king of navigation doesn't want to stop there. Google aims to make its navigation app for more than just directions, as made clear by its recent feature that lets you follow businesses in the app. Combining timely news and events posted by local businesses with real-time transit seems like the perfect match.

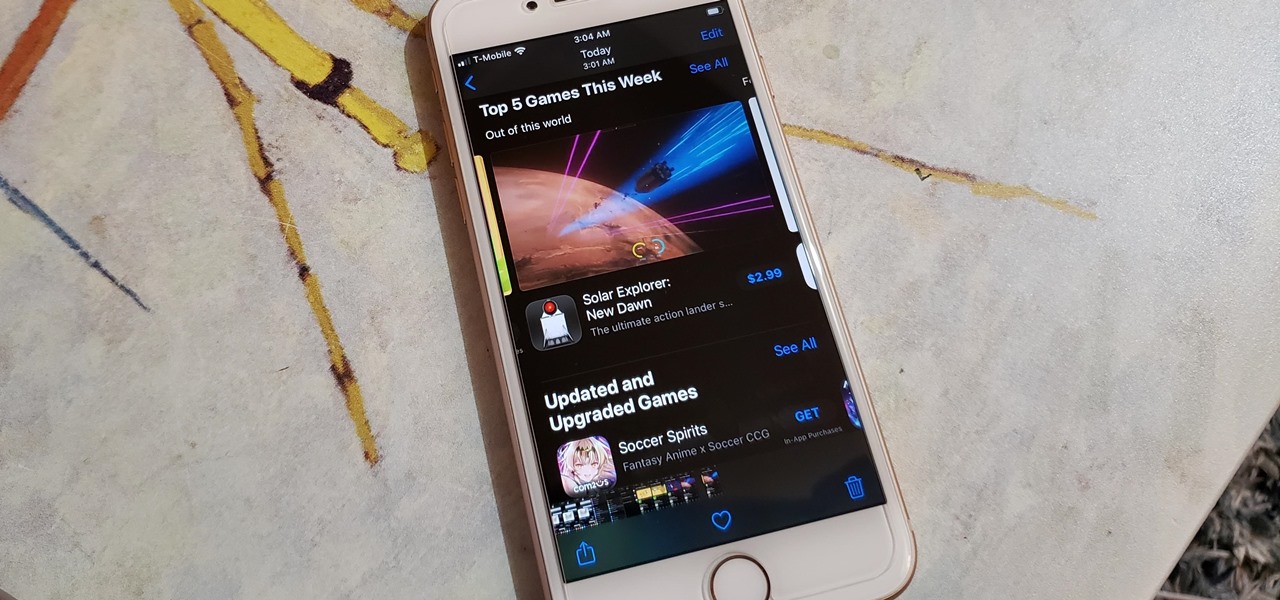
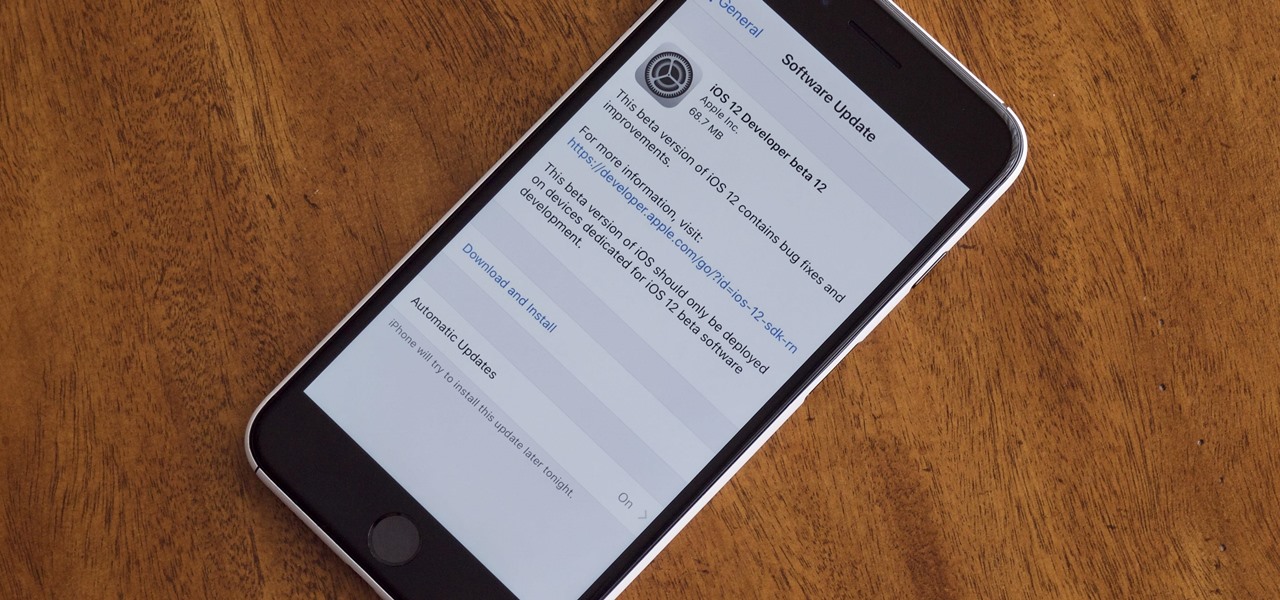
Right before the Labor Day weekend, Apple issued iOS 12 developer beta 12, which comes four days after dev beta 11 and public beta 9, and just one day after announcing the Sept. 12 event. This update primarily fixes a bug where you would be continuously prompted to install a new iOS update even when none existed.

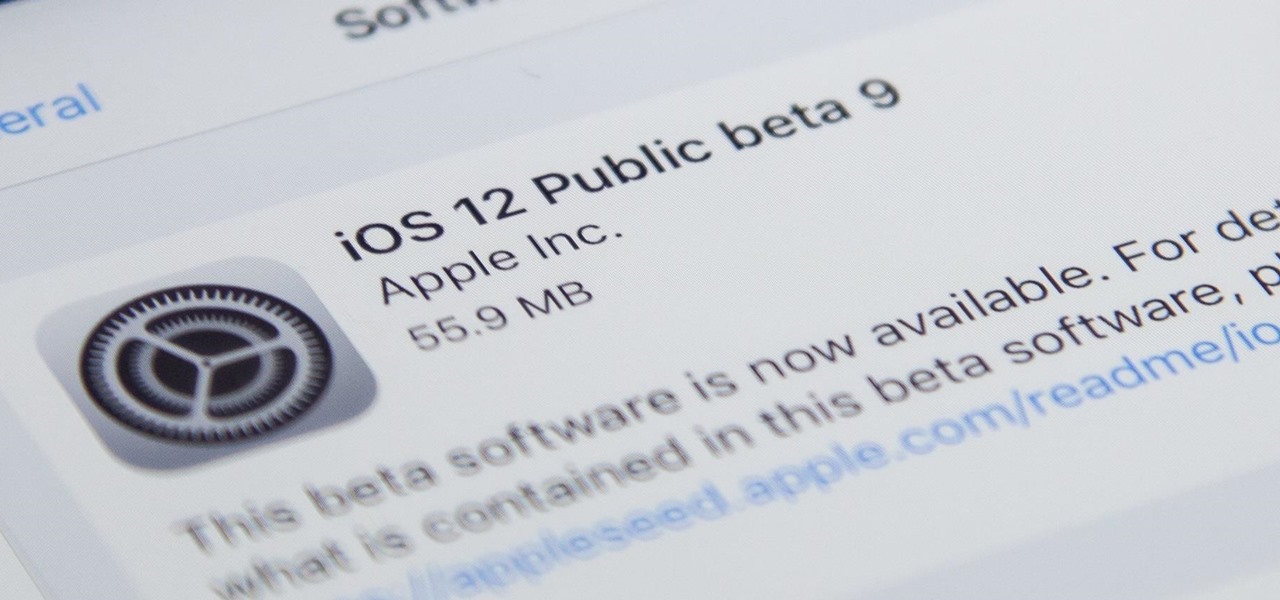
Apple released iOS 12 beta 9 to public beta testers on Monday, Aug. 27. The update comes at the same time as the release of dev beta 11. This is surprising, as Apple typically releases developer betas at least a few hours before the public version. Then again, everything Apple is doing with its iOS 12 beta as of late is surprising.

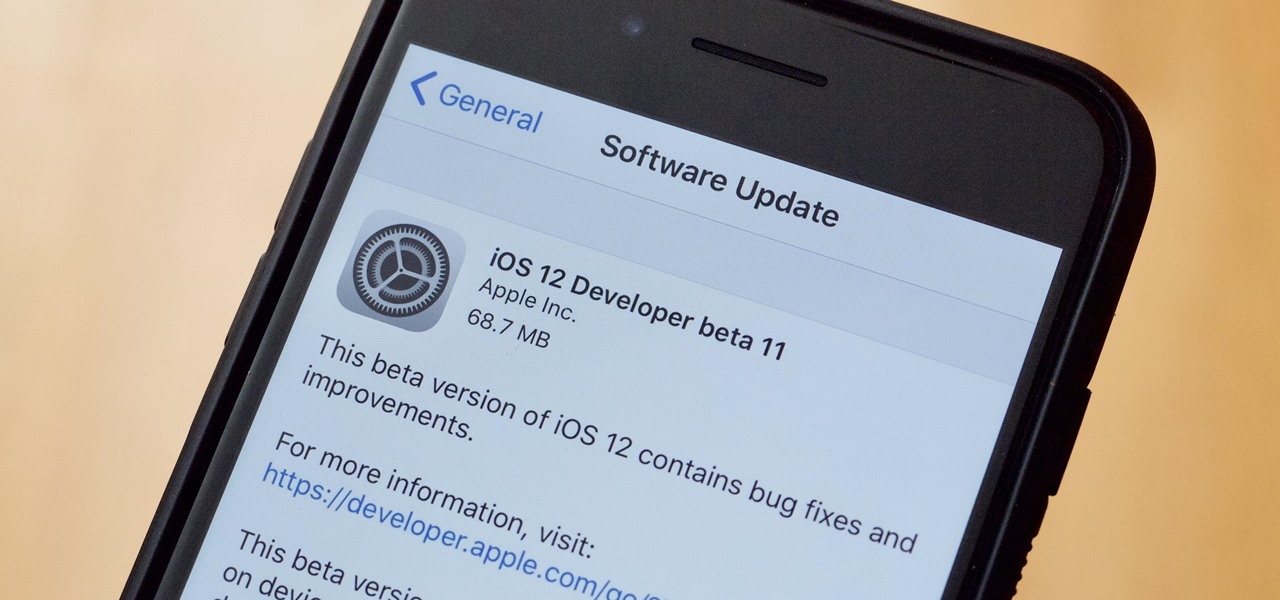
Apple released the eleventh developer beta for iOS 12 to registered software testers on Monday, Aug. 27, only four days after the company unexpectedly released both dev beta 10 and public beta 8. Apple has ramped up its beta release schedule as of late, offering minor updates twice a week in the lead-up to iOS 12's official debut in a few weeks.

Apple released the tenth iOS 12 developer beta unexpectedly Thursday afternoon, Aug. 23. The update comes only three days after the release of iOS 12 developer beta 9, a surprising move for Apple, even with the irregular releases the company has made in recent weeks.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.

On Monday, toy maker Merge virtually blasted its way into CES 2018 with a new tech-meets-toys innovation in the form of an augmented reality gun controller for use with smartphone-powered first-person shooter apps.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

A few months ago, we gave you a small peek at a new entrant in the race to deliver augmented reality smartglasses to the masses, and now the device is finally ready for the public. ThirdEye Gen is now accepting preorders for its X1 Smart Glasses, which will also provide users with an AR-centric app store.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.