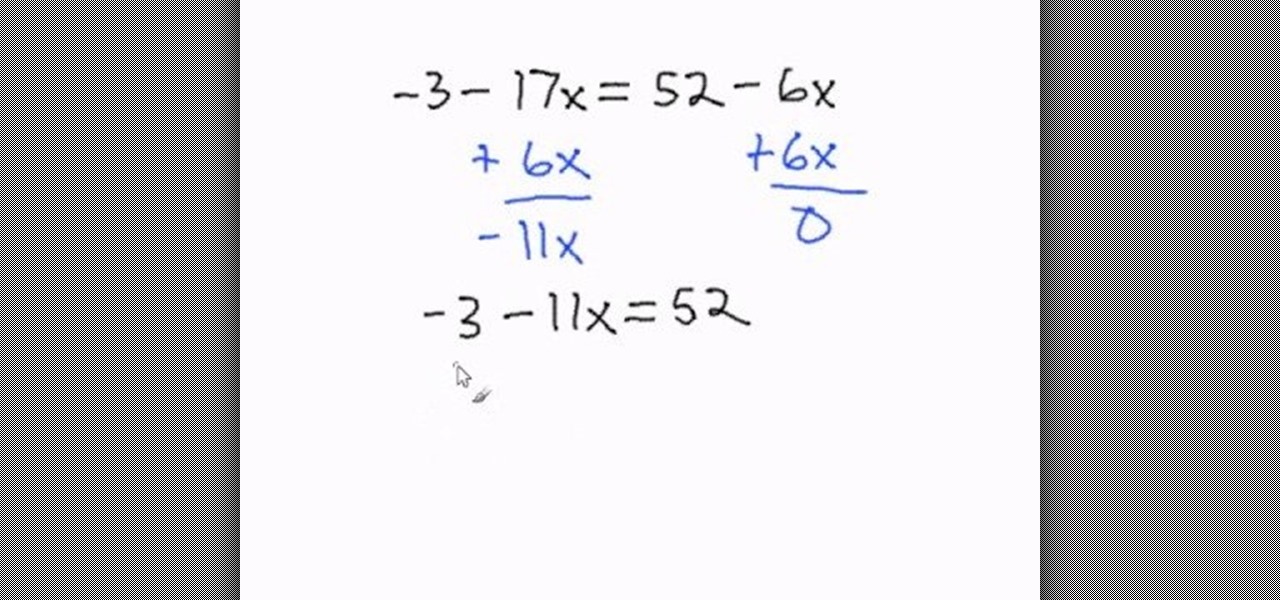
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

In Bhopal, India, a place nestled in between the royally pink city of Jaipur and the dry (i.e., alcohol forbidden) state of Gujarat, is a team of developers determined to make a fully driverless car suitable to the complexities of Indian traffic. An algorithm elaborate enough has yet to be made by any other company, but is the fundamental key to handling the intuitive habits of Indian drivers, the often intense and gridlocked traffic, and the country's vast expanse of jarring roads.

Welcome back, my nascent hackers!
Here is a video all about meeting other vehicles when you're having lessons with driving instructors in Nottingham and the surrounding area. It happens when you are passing parked cars and someone is coming the other way.

With a little bit of planning, you can avoid a lot of blood-pressure-raising traffic messes. You Will Need

This video aimed at electricians, is designed to help employers and employees what is required in the standard that is applied for the control of energy during maintenance and servicing of equipment and machinery. Employers are required by law to develop proper lockout safety procedures and provide proper protection materials and safety training. This video is highly important for any electrician, apprentice or journeyman, because it will help prevent injury… or even death.

Getting splinters is no fun, but making them can be if you've got the right tools and the proper technique.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

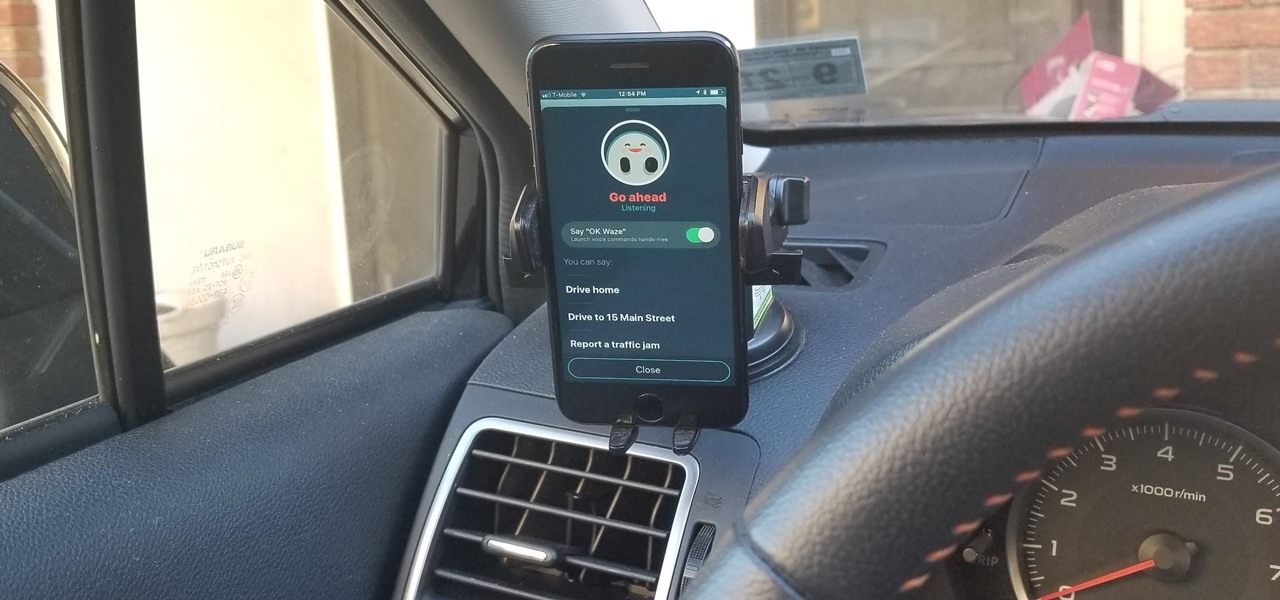
Before starting any drive where you're using Google Maps for directions, it's vital to make sure the app is functioning correctly, specifically, navigation prompts. After initiating turn-by-turn directions on your Android or iPhone, the last thing you want to worry about is Google Maps not audibly telling you where or when to turn, especially in an unfamiliar area.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

Drivers the world over are painfully aware of the inherent danger of taking their eyes off the road even for a second. In fact, according to the National Safety Council, 27% of all car crashes result from distracted driving due to attempted cell phone use. Fortunately, Waze comes with a feature that can help keep you from being a part of this grim statistic.

Forget Waymo, Uber, Tesla, and other other heavily mediatized driverless contenders — German premium carmaker Audi AG has become the first OEM to introduce a Level 3 car sold in retail channels.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Texas has become the 18th state to pass a bill into law regarding autonomous vehicles, the third this month to do so.

So, according to Sprout Social, mentioning an Instagram handle in the caption of your posts increases audience engagement by up to 56 percent. If true, that's pretty impressive.

While Live Photos has been a fun addition to iOS ever since the iPhone 6S and 6S Plus, there hasn't been much practical use for Apple's moving images so far. That was, until iOS 11 added advanced features such as long exposure effects that make a DSLR less and less impressive these days.

After Uber noticed that if you walked to a more convenient pickup spot — instead of your exact location — that it would save you time and money, they decided to make a change to their system.

Disney is gearing up fully autonomous vehicles that will shuttle you and your family from the parking lot to the amusement park, stress-free. Well, as stress-free as you can get while introducing grandma to the concept of a car with no driver. No, grandma, Satan is not "steering this contraption." At least, we don't think he is ...

There's nothing worse than driving up to your destination only to discover that there isn't a parking spot in sight — but thankfully, Google Maps will soon have you covered.

For all of its drama, Uber's driverless program has states like Arizona excited for the future of self-driving vehicles. But it's not Arizona alone that supports the driverless craze; the Illinois House of Representatives will hear a bill that would allow driverless cars on the road with or without human operators.

Oh, Waze—you know, that Google-owned traffic navigation app that tempts drivers into stopping at local food joints like Dunkin' Donuts and Taco Bell? Well, now you can even order a large iced coffee through the app before you even arrive at a fast food hotspot.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

Yes, you read that right—you can now get Google Maps back on your iPhone again. It may not be officially replacing Apple's notorious Maps app, but it sure is a sight for sore eyes.

One of the greatest consoles ever to exist in the world of gaming is the PlayStation 3, which even lets you do a million different things unrelated to games. But no matter how big of PS3 fan you are, you have to admit that the internal browser is not the greatest. Far from it. While you can access most websites from the PS3, a lot of those site's functions are limited, including Facebook. After reaching over one billion users earlier this month, Facebook is undoubtedly one of the most popular...

We can't overstate the importance of stretching in yoga. Yes, you may think that yoga itself is just a bunch of stretches flowing one right into the other, which is true, but there are certain yoga poses aimed strategically at increasing your flexibility so you can do other yoga poses better.

Plastic water bottle caps are more than just a massive strain on the environment. They can also be used to perform this cool party trick! All you do is hold the cap in your fist and then pound said fist from the bottom with your other hand. If you do it right, the cap should launch high into the air with a nice little pop. This is sure to impress the guests at your next party or puncture the cornea of one of your enemies, depending on what you aim the cap at.

In this tutorial, learn all about how to make the most of your iPhone camera when on the street. Sometimes on vacations or trips, it is difficult (and dangerous depending where you are) to carry around a big, heavy camera all day. Did you know that you can take great photos with a pocket-sized iPhone? In this clip, Lisa will show you where to aim and how to set up your shots with an iPhone to get the best pictures possible. The best part about mobile picture taking? You can upload your images...

This video shows you how to make a fake "virus" that shuts down the computer of your victim when they open it. This video also shows you how to email or AIM this prank virus to a friend.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

This video is aimed at beginner level viewers and shows one of the basic techniques involved while solving linear equations having one variable.