
How To: Edit lighting in Photoshop
Learn some basics on editing lighting and other aspects of photos in Photoshop.


Learn some basics on editing lighting and other aspects of photos in Photoshop.

You don't have to be pyschic to know what that check engine light is trying to tell you. See how to use a handy device called the CarChip to read the engine's computer and save a trip to the mechanic.

Learn a trick to bend a lit cigarette while smoking it without breaking it in half.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

Smartphone videos get better and better each year. Seven or eight years ago, who would have thought iPhone and Android phones could support 4K video recording. Some phones can even shoot slow-motion at 960 fps. But no matter the resolution or frame rate, a phone's rolling shutter can make quick movements in front of the camera appear wobbly, distorted, or with artifacts.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

If you've been getting that "Please update from the iOS 12 beta" alert continuously in iOS 12 public beta 9, Apple just issued a fix for it Friday, Aug. 31, with iOS 12 public beta 10 — just in time for Labor Day weekend. This marks the second update this week as dev beta 11 and public beta 9 were released on Monday. It's also just one day after Apple announced its Sept. 12 event.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

Gatorade: its popular red flavor can stain the whitest fabric, and its sweet taste is oddly refreshing after breaking a sweat. If you've ever participated in a sport, you probably spent halftime at games and practice breaks chugging the stuff. Though it made its name as a sports drink, Gatorade is also a well-known hangover helper—but its beneficial and interesting uses don't end there. The brightly colored drink can do so much more than just hydrate you.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.
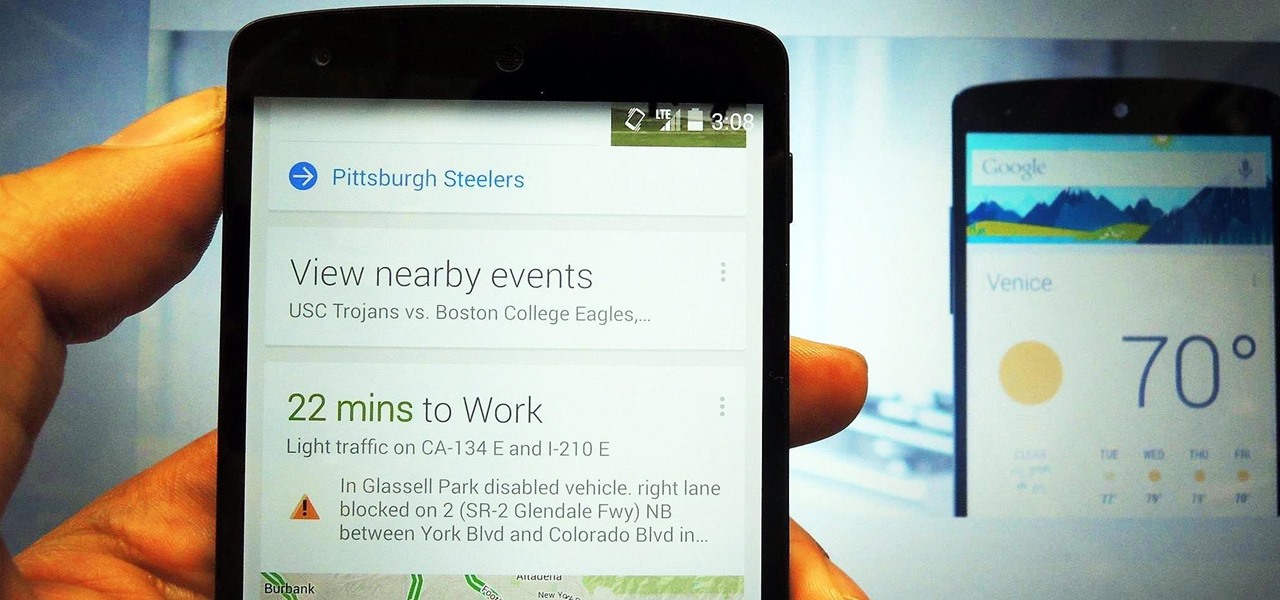
The launch of Android 4.1 Jelly Bean was also the launch of Google Now, a service that was supposed to one-up Siri, the resident personal assistant for iOS devices. Google Now offered enticing features, but its launch went unnoticed by a great many Android users.

If you're lucky enough to have a large, winding staircase, there's no reason not to dress it to the nines for this holiday season. Make sure that your party guests' jaws drop to the floor once you open the door by decorating your staircase with this gorgeous golden splendor themed garland.

In this video, we learn how to make fudge from scratch. First, add 3 3/4 c sugar to a saucepan with 4 oz unsweetened and chopped chocolate, 1.5 c heavy cream, and 1 tsp salt. After this, add in 3 tbsp light corn syrup and stir it all together until it's all combined. Now, put the pan over medium heat and stir gently until it comes to a boil. Once boiling, put the lid on and cook for two minutes. Then, rub the candy thermometer with butter and stick it into the pan. Make sure it doesn't touch ...

During the fall, warm and comforting colors like brown, red, and sienna abound. Embrace the natural richness and beauty of fall by incorporating these colors into your next makeup look.

Despite what their name may imply, chess bars have nothing to do with chess and everything to do with delicious foodie goodness. These chess bars are made from a blend of cream cheese, butter (of course), and yellow cake mix and the result is a crunchy but light dessert.

What's better than either pound cake or French toast? The love child of these two delicious bready treats. Check out this tutorial to see how to whip up a French toast pound cake that's light, delicious, and perfect for serving up on chilly fall mornings.

California is struck by earthquakes everyday, but the biggest ones, on average, appear every 150 years, just south of the San Gabriel Mountains. The last super-destructive earthquake in California was over 300 years ago, which could mean a long overdue Californian earthquake is on the horizon.

If you've ever gone on a diet then you know that "dessert" usually leaves your vocabulary quickly. But sometimes you gotta live a little and satisfy that sweet tooth! After all, not doing so may just cause you to pig out and totally fail on your diet.

Trix are for kids, but Fruit Loops are for everyone? Don't you ever think you're too old to nom on the pure sugar heaven that is Fruit Loops! While we are totally for grabbing handfuls out of the box and stuffing it in your face, there are other ways you can make use of this colorful "tropical" treat.

In this tutorial, we learn how to make Indian chaat: Batata vada. To make the vadas, you will need: 2 lbs peeled and mashed potatoes, 1/2 tbsp ginger, 1/2 tbsp green chili paste, 1 tsp roasted cumin powder, 1 tsp sugar, salt, `.5 tbsp lemon juice, and 10 sprigs cilantro. To make the batter you will nee: 1 c chickpea flour, 2 tbsp rice flour, 1/8 tsp asafetida, salt, 1/4 tsp baking soda, red chili powder to taste, 1 tbsp oil, and 1/2 c + 2 tbsp water. For the seasoning you will need: 1 tbsp oi...

It seems that cupcakes are the designer foodstuff of choice these days. They're really not all that different from cakes (they're made from the same dough, after all), but their miniature size makes them individually portioned for convenience and also a great base for adorable decor.

What is it about Parisian women that makes them so effortlessly chic and timelessly beautiful? Whether we're talking about Charlotte Gainsbourg, AKA Jane Birkin's daughter, or an older lady like Juliette Binoche, Parisian women really take it easy when it comes to applying makeup, emphasizing skincare instead. And they look gorgeous doing it.

Sweet and sour sauce makes everything taste better. You can add this tangy dip to fish, chicken, meat and even tofu for an Asian flair. In this tutorial, Betty will show you how to use simple household spices to whip up your own easy batch. Enjoy!

In this clip, learn how to make Betty's most elegant dessert - strawberries romanoff! This tasty twist on summer fruit is a great, simple dish to serve your guests when dinner is done. You will lick the bowl when you finish these sweet babies - they are so good!

Need to eliminate those pesky leg hairs but want to bypass the credit card bill? Then read below for a homemade sugar wax recipe and watch the video to learn how to rip off your hair!