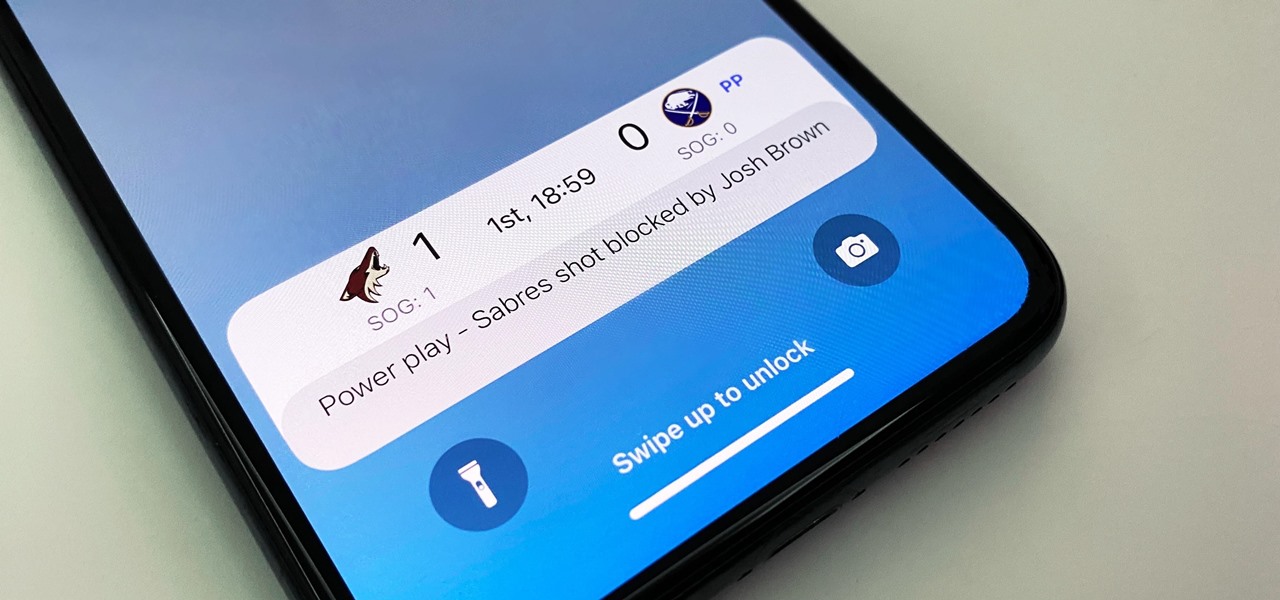
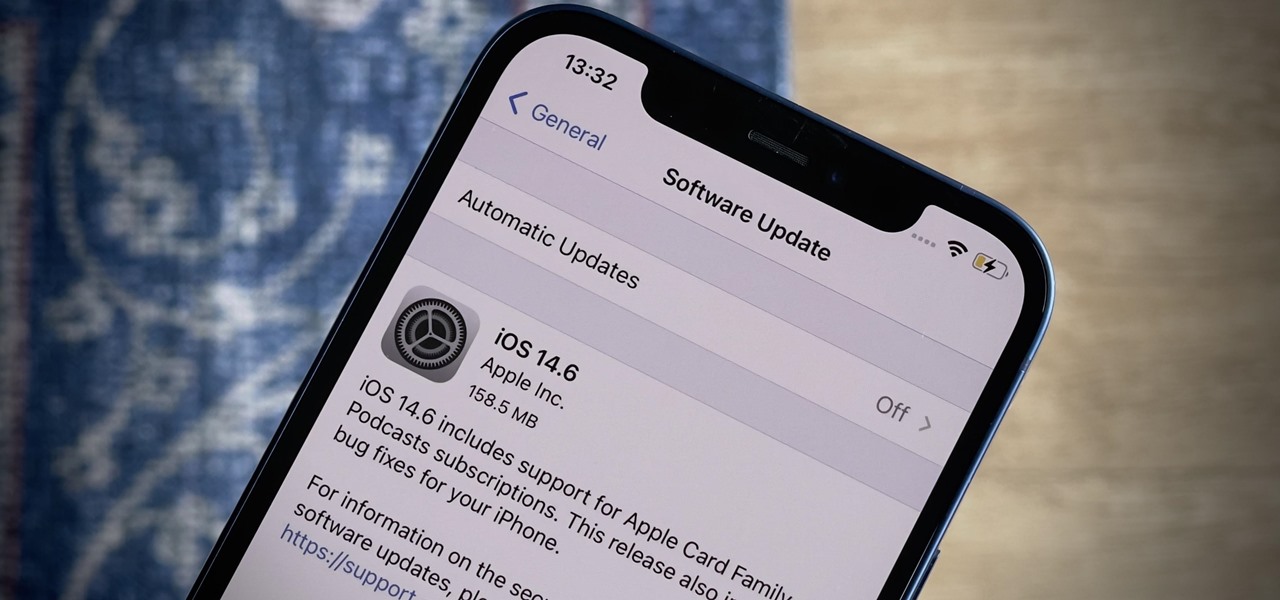
Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Traveling abroad can be a hassle. Between the flight, hotels, food, and the languages barriers, it can be a lot to manage. There's one tool you have that can help with all of this — your smartphone. Fortunately, nowadays, you don't have to change your carrier to continue using your phone.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

While autonomous vehicles are almost assuredly the future of personal transportation, we are likely many years from seeing self-driving cars become as ubiquitous as manually-driven ones, as the auto industry has a myriad of government regulations and other constraints to contend with. Until then, augmented reality is looking like the next big thing in automotive technology.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

Live Activities is Apple's hottest new feature for iPhone, but it's not always straightforward. Sometimes you'll trigger one without realizing it, but it may seem frustratingly impossible to start one when you really want it.

It can be very frustrating: You open your Messages app, send an iMessage, and then see that dreaded red exclamation point or horrible green SMS bubble. At this point, you may be curious whether it's just your iPhone or whether iMessage is broken for everyone, but how do you find out?

Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription support for shows in Podcasts.

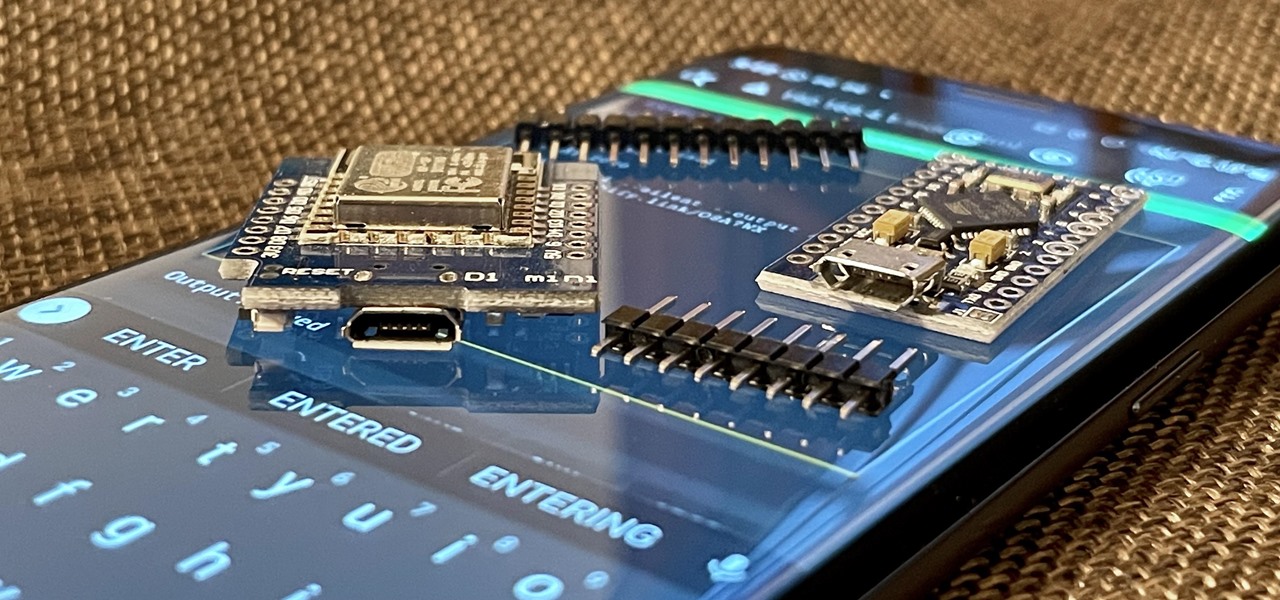
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

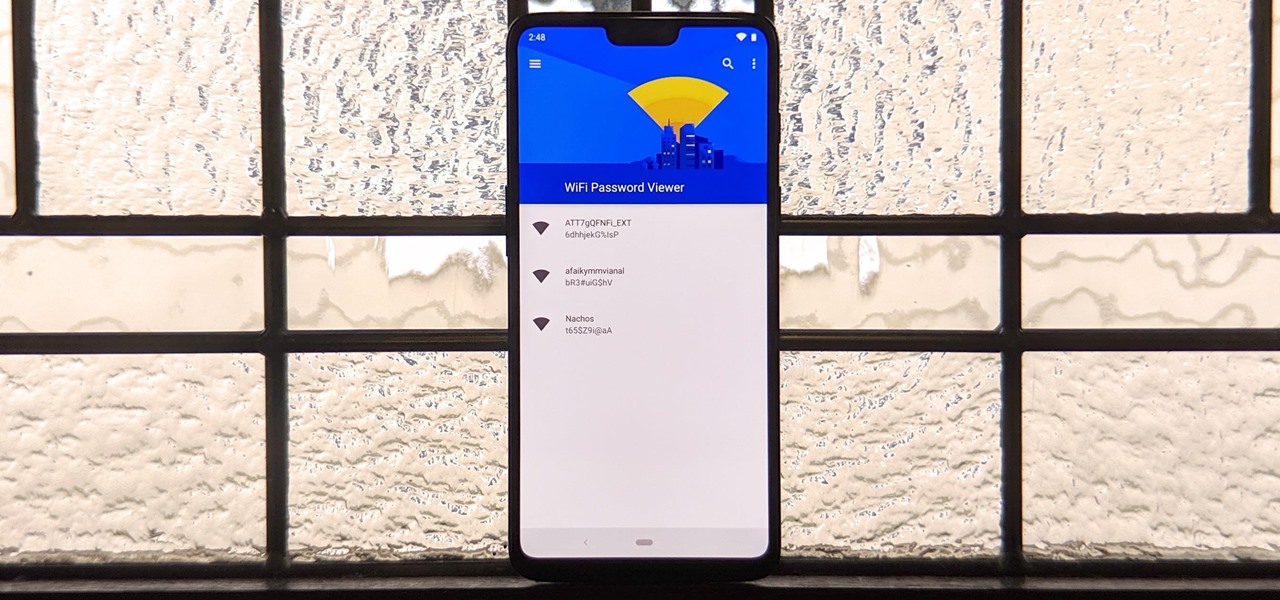
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

just experimented to wear those eyeglass which are partially concave and convex no editigns and mixings in this

In this Red Giant tutorial, Aharon Rabinowitz shows you how to create a realistic traffic pattern backdrop - great for a scene in which the camera overlooks a low lying, but developed area - perhaps looking down from a high hill onto a residential neighborhood.

This is a video for children to learn about the traffic light for pedestrians use. It is an interaction game where the children can push the proper light to answer questions pertaining to the traffic light. Teach children about traffic lights.

No better way to celebrate summer coming to an end than ice cold party favors. The Jewels of New York offer up two mouthwatering booze popsicle recipes, gratis, for your enjoyment:

These are a series of clips to show you how to deal with the different situations when turning right at traffic lights. In the U.S. or countries that drive on the right, these principles will apply to left hand turns. Deal with right turns at traffic lights - UK.

Austrian composer Peter Ablinger has created a "speaking" piano. Ablinger digitized a child's voice reciting the Proclamation of the European Environmental Criminal Court to "play" on the piano via MIDI sequencer. Apparently, the computer is connected to the piano, which analyzes the human speech, and then converts it to key-tapping.

In this video tutorial, we learn how to create a realistic traffic pattern backdrop within After Effects through use of the PlaneSpace and Text Anarchy plugins. Whether you're new to Adobe's popular motion graphics and compositing software or a seasoned video professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch...

Search engine optimization (SEO) is now one of the most important topics for website owners to understand. Anyone that depends on their website to bring them business needs to know the ins and outs of SEO in order to maximize their website’s potential. And if you want your website to have a high Google rank then SEO is essential.

Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor.

Gun shots, dog mauling, compound fractures, partially severed limbs... Sometimes direct pressure isn't enough to cut the blood loss. This U.S. Army field instructional is a fascinating and thorough medic's walkthrough. Learn exactly how to apply a lifesaving tourniquet to an injured limb. No first aid poster can compete with the unmistakable deadpan of a military issue instructional. Only the American Army could deliver such eyewitness first aid advice. Bookmark this. If you're ever stuck bet...

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

This little guy landed on the window of my truck while I was stuck in traffic.
Well another great way to burn up our taxpayer money. From Cold Warriors to targeting trafficking: US military shifts focus in Europe - World News.

This video is a series of short clips that show how to merge onto a freeway. These clips show how to assess the speed of the traffic already on the freeway (or highway) and join the flow of traffic safely. Made in the UK, if you're in a country that drives on the right, just think right instead of left and the principles will still apply. Merge onto a freeway or highway.

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

Video: Add LED lights to avoid speed detection while driving.

Google AdSense is a beautiful thing. They pay you for posting content online, whether it be through a third-party website like WonderHowTo or on your own website. WonderHowTo seems to be a good place to start from if you plan to make money with AdSense, but it's not the only place that you can submit content to and receive all of the revenue generated by the AdSense ad units. You may want to get a wider audience and more traffic, and for that you must look beyond the horizon of just one site.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers: