Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Last week, we told you about one of the first pairs of augmented reality smartglasses to get Amazon Alexa functionality, and now we're finally getting a look at how it works.

While Apple launched ARKit to enable developers to build augmented into mobile apps, Mozilla, the company behind the Firefox browser, is taking advantage of the platform to advocate for browser-based AR experiences.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

Trendy restaurants are fun, but waiting in line isn't. Too often, we arrive at a location to find a queue between us and our dinner. If only we could know when wait times were down so we could go out at the optimal time.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

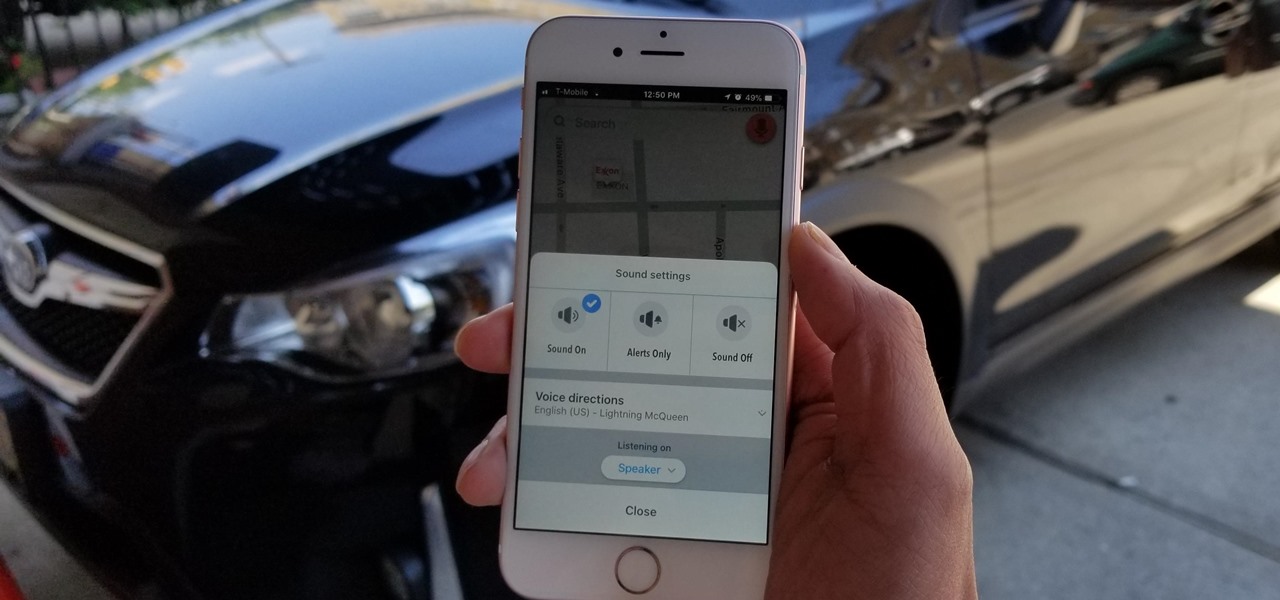
If you've been looking for an alternative to Google Maps, look no further than Waze. In addition to benefits like crowd-sourced traffic data, police trap locations, and road work avoidance, the app even lets you personalize the voices used for navigation and directions.

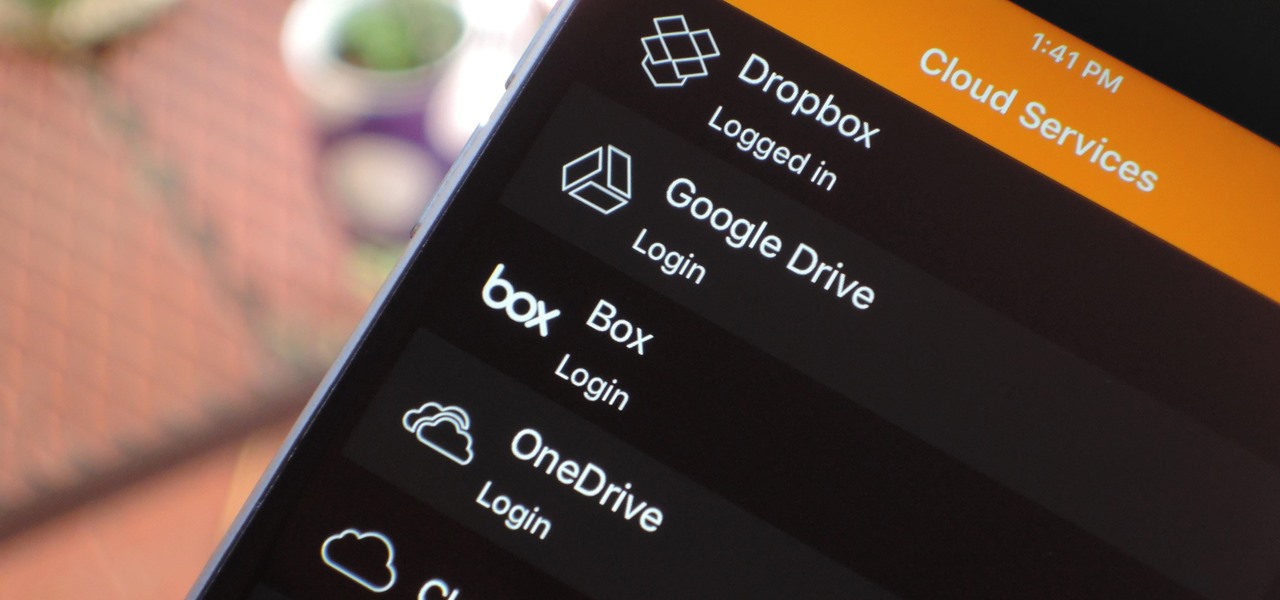
If you have movies and videos stored on Box, Google Drive, Dropbox, or OneDrive, you should definitely be using the VLC app for iPhone. After setting a few things up, VLC will let you stream videos directly from any of these services with a proper video player UI, complete with gesture controls.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading.

Waymo has done a lot of things over the course of their driverless journey, but their solution to little birdies pooping all over a self-driving car's LiDAR system is definitely our favorite.

You would think most people would agree that you shouldn't use your smartphone while driving. Apparently, most people would be liars, according to recent data from the National Safety Council (NSC) and Zendrive.

While not quite a true self-driving car, Mercedes is gearing to release a vehicle with a plethora of assistive-driving features, some that might have you excited about what autonomous vehicles can do in the future.

At Adobe Summit 2017 this week, Adobe announced they are looking to occupy a new space in the market by combining their analytic capabilities with augmented reality. Teaming up with Microsoft, the company has combined Adobe Sensei software with the HoloLens, reports GeekWire. Together, the tech and software create a new tool for retailers to track their consumers' habits.

Both the US and UK seem to be leaning toward requiring level 3 autonomous cars to train their "eyes" not just on the outside world, but even on the driver itself.

Earlier today, Alphabet announced that the Self-Driving Car Project has officially graduated from their innovation factory (X) and will now operate as an independent company called Waymo.

HoloMaps, an application by Seattle-based Taqtile, is available for free on the Windows Store. Taqtile, whose Vice President of Product Management was Microsoft's former Director of Business Development, is one of the few partners currently in the Microsoft HoloLens Agency Readiness Program. This interactive 3D map they have created, powered by Bing, offers more than just a top-down view of the world on the HoloLens.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

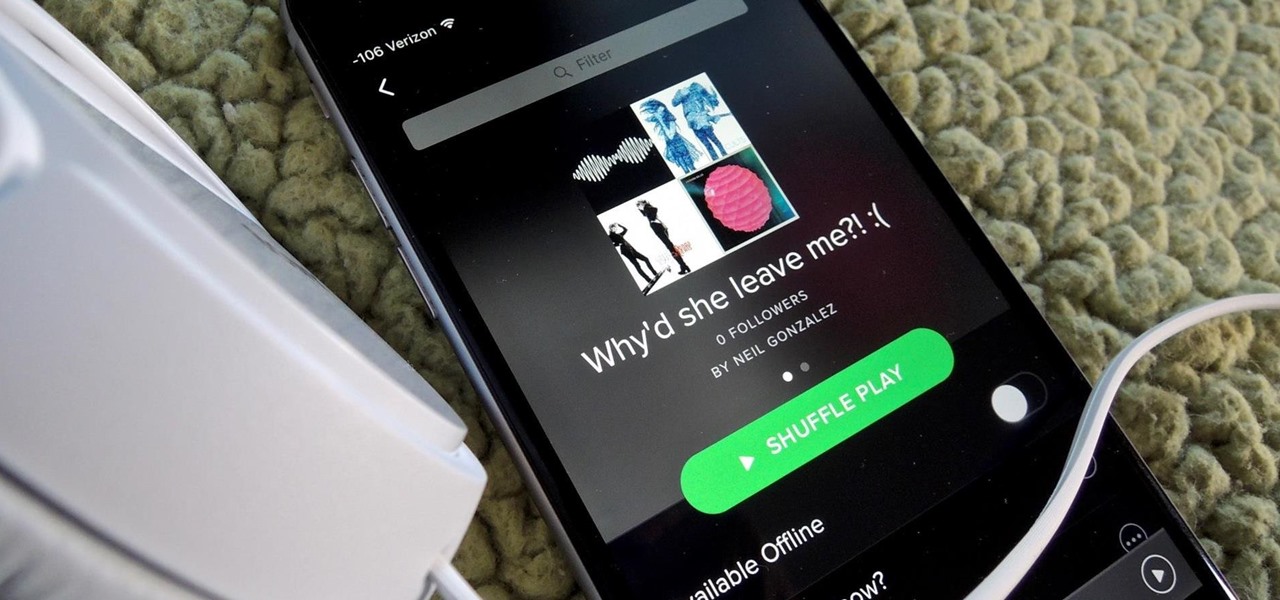
Playlists are more than just a list of songs that you enjoy listening to while in traffic or hosting a party—they're stories that illustrate who you are or your frame of mind at a certain point in your life.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

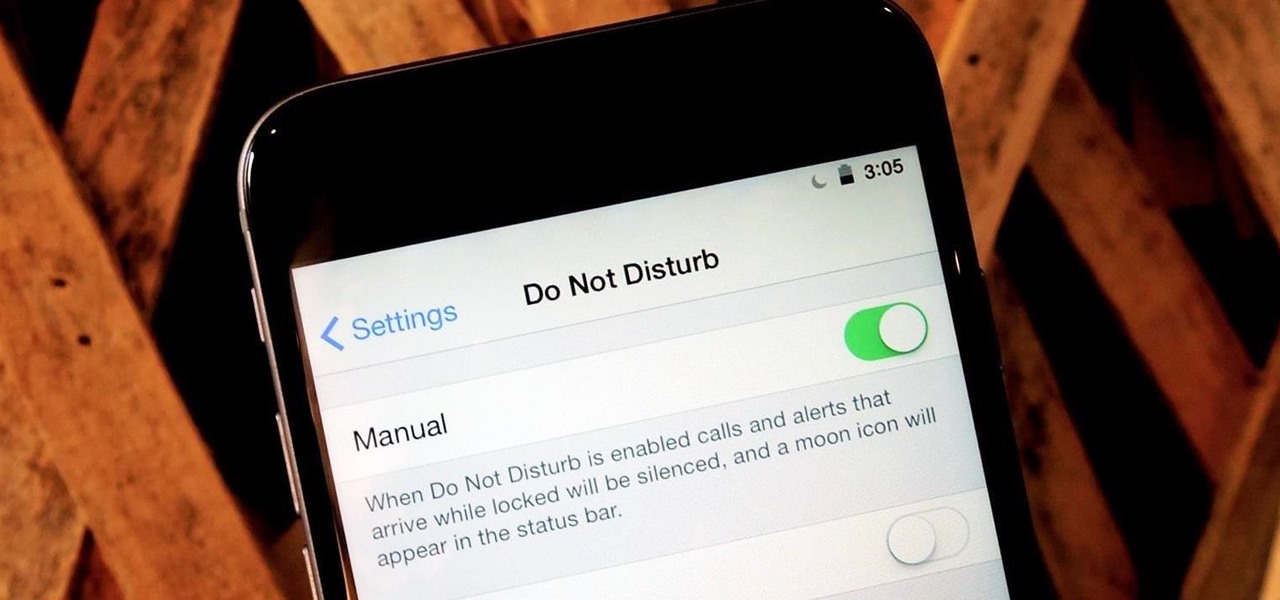
At certain times of the day, like when I finally get home after sitting through aggravating traffic, the last thing I need is the sound of my phone irritating me any further. So, I toggle on the "Do Not Disturb" feature (introduced in iOS 6) on my iPhone and get to enjoy a little peace of mind.

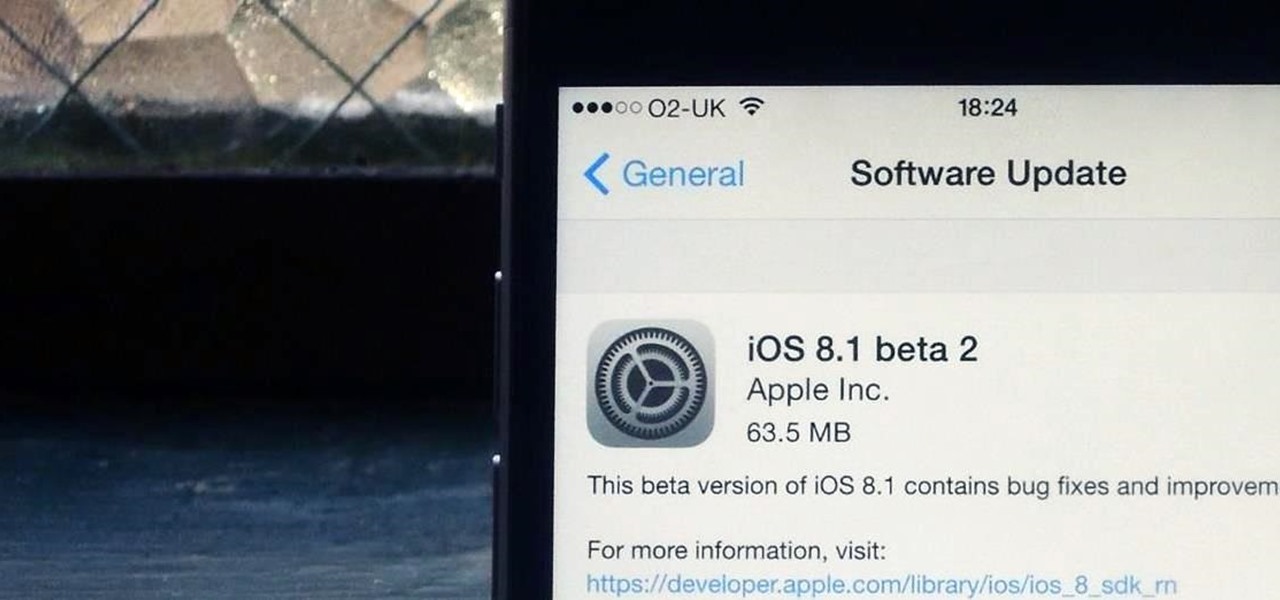
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

While texting and driving may get you a ticket, there are still a ton of uses for your phone in your car, music and navigation just to name a couple. Every Android device comes with access to GPS and traffic updates, but none of those apps really have your back in real-time.

Google Now is a quick and intuitive way to tailor your device to work for you and, unlike other personal assistants, provide you with up-to-date information based on search habits, emails, and the general all-knowingness of Google.

On a recent trip to Palm Springs, I found myself navigating with Google Maps and virtually exploring my destiniation using its built-in Street View feature. The thing is, using Street View can make keeping track of your exact location difficult as you zoom in, out, and about. It's a little discombobulating.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Most of the time, if you're actually using your computer, it won't just go to sleep on you. But when you're reading a long article or watching a video and don't move the mouse or use the keyboard for a while, the screen automatically dims or goes into sleep mode.

Google Now is an extremely intelligent personal assistant that automatically updates and prepares the most pertinent information for you on your Android device. Traffic updates, alternatives routes, weather conditions, and other important data is constantly being monitored and updated for you.

Last week, Instagram stopped supporting media Cards on Twitter, meaning that in order to view a full photo shared in a tweet, you have to click through to Instagram rather than seeing it on your Twitter feed. Otherwise, the photo will appear to be cropped.

Having the ability to stream music or video from practically any internet-capable device is a thing of wonder—especially at the airport. I don't know how many times Netflix has saved me from watching something like CNN for 5 hours straight at the gate during long layovers. But streaming video sites like Netflix only work in North American and few other regions. So, if you're a U.S. subscriber currently in Australia or France or any other international location, Au Revoir to your streaming cap...

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.