Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

If you rely on Apple Maps to get around over other navigation apps, there's a lot you can do. Look Around lets you tour cities up close, restaurant reservations make dining less frustrating, and 3D view gives a new perspective of a neighborhood. While there are many more where that came from, iOS 14.5 just added six new features and changes you need to know about.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.

The HoloLens team is finally beginning to realize that to truly engage the mainstream, augmented reality needs to make its way out of the lab or factory floor and onto the streets.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

On Thursday, Snapchat opened up its walled garden of World Lenses to the masses of creators with the launch of Lens Studio.

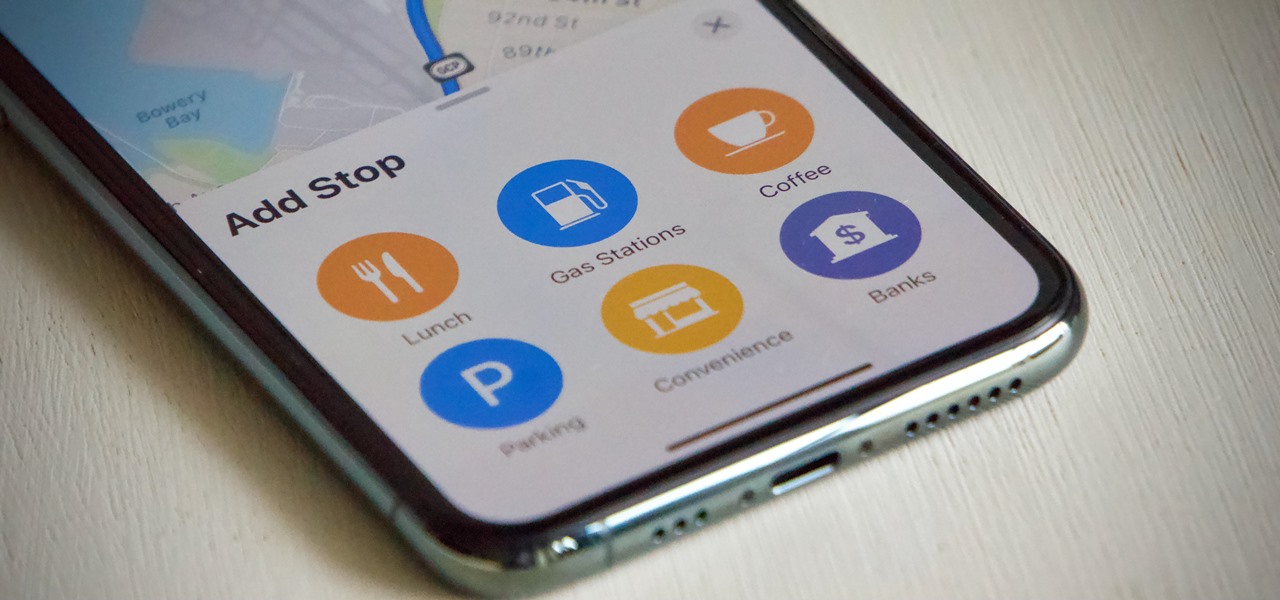
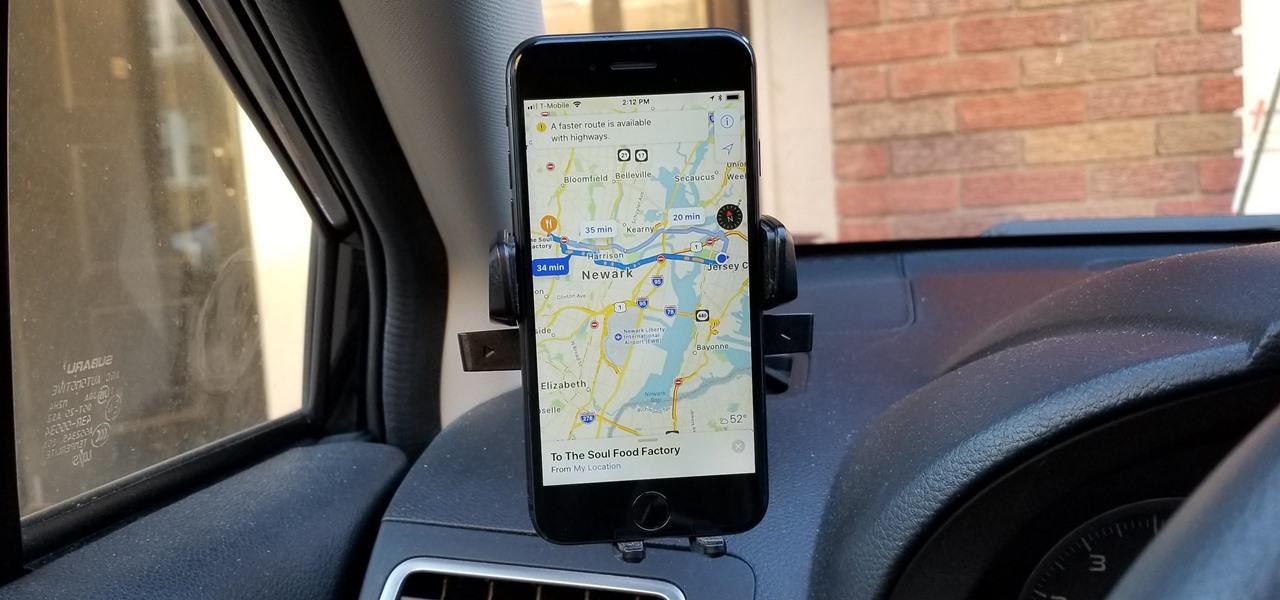
Highways are among the most efficient routes of driving from one place to another. Unfortunately, however, they're also the most used route taken by everyone else resulting in migraine-inducing congestion, especially during rush hour. Thankfully, Apple Maps has a feature that will direct you along lesser known routes that could be faster and/or safer.

With the raw, visceral feeling of zooming around on the open road, it's easy to get carried away when you're out for a ride on your chopper, super bike, or scooter. This increases your chances of getting lost, plus routes can differ slightly for motorcyclists and cagers, unbeknownst to most drivers. Luckily, Waze has rolled out a feature that caters specifically to bikers.

Until self-driving cars become mainstream, augmented reality might be the next big technology to hit your dashboard.

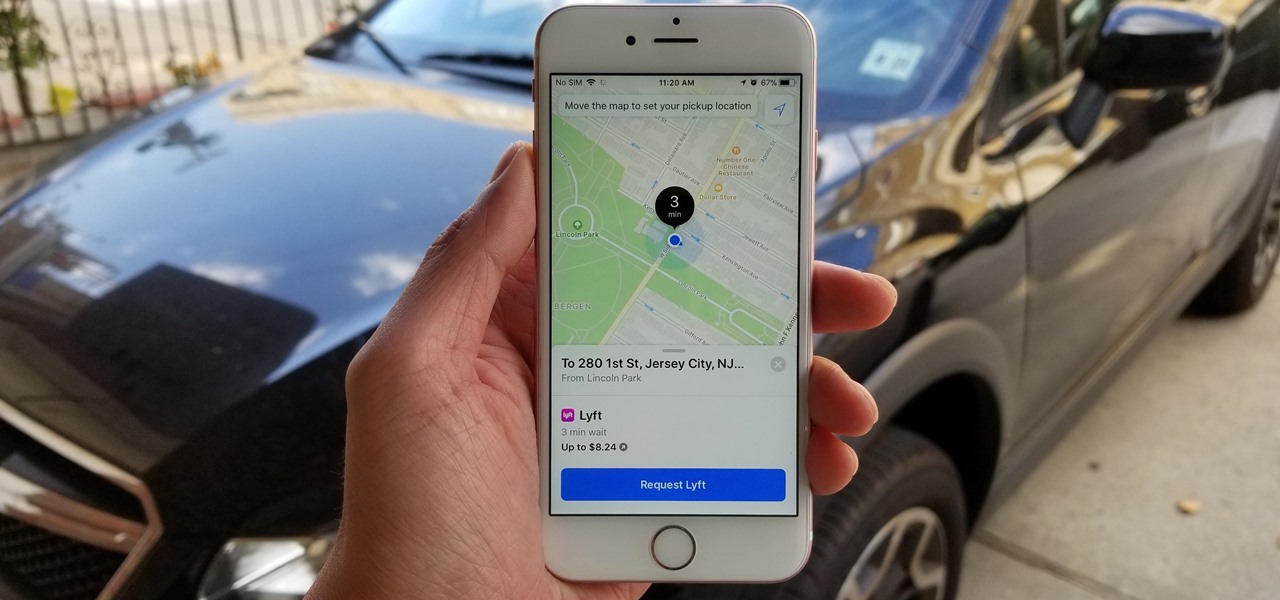
There's no denying the impact ride sharing apps like Uber and Lyft have made on our lives. With fares that undercut traditional yellow cabs, combined with the fact that your ride is just a tap away, these services have become the primary mode of transportation for many folks in urban areas. Thanks to iOS 11, booking an Uber or Lyft has just become a lot more convenient.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

France's Groupe PSA (formerly known as PSA Peugeot Citroën) — one of the world's top-10 carmakers — aggressively seeks to take a lead in the rollout of the industry 's first driverless cars, as it becomes the first mainstream carmaker to announce it will launch a Level 3 self-drive vehicle launch by 2020.

The new Leaf with Nissan's ProPilot driverless feature could launch as soon as this year, following a teaser image and video the Japanese carmaker released of its flagship EV yesterday.

Instagram Stories is one of the most flexible ways to share creative and original content with your followers. It allows you to alter text, markup images, and add cool graphics and stickers, along with other fun ways of expressing yourself.

Virgin Wireless, perhaps best known for Sir Richard Branson and all of his antics, is an affordable cellular option here in the US. Virgin customers can enjoy — if that's the right word for it — Sprint's cellular service, at a discounted rate, however, there are usually some compromises for that. Now, there will be yet another compromise for Virgin customers who don't like iPhones — Virgin will now only carry Apple's phone on their network.

Uber drivers do a lot for us. They sit through traffic, make conversation, put on our favorite tunes, drive us however far we need to go, and they work long hours. Some even have to deal with people who may have had too much to drink, which we all know can be obnoxious. So yeah, we'd say that it's about time for Uber to include a tipping feature in their app.

Instagram can be pretty exact when it comes to where you are located. That's why, sometimes, it's best never to geotag your precise location, but a broader area where you are less likely to get, well, um ... stalked?

A Norwegian shipping company says it will launch an unmanned container ship within four years, as the shipping industry begins to apply driverless technology to commercial sea transportation.

In this article, I am most likely going to humiliate myself by showing you all the horrible hashtagging I am wont to do. When it comes to hashtags, well, everybody knows if you desire any chance at all of getting noticed on Instagram, you got to hashtag.

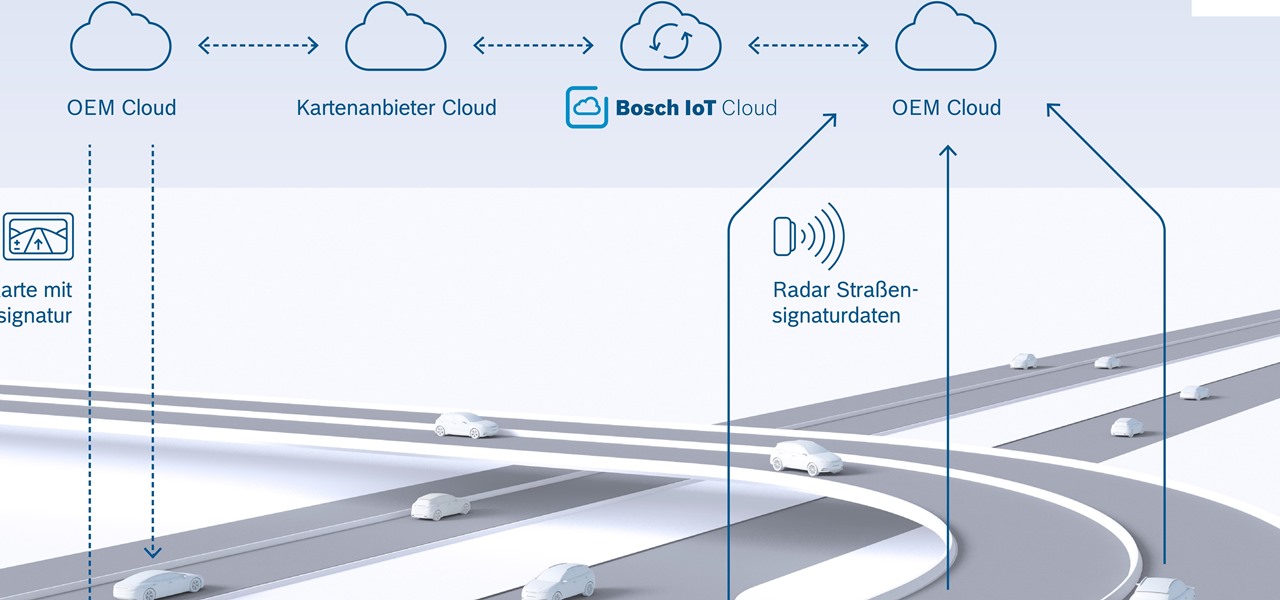
New "radar road signature" technology from Bosch will be used to create maps for high-accuracy self driving. The new map is the first to use radar signals for a localization layer.

New York City may not be the friendliest city, but with the apps Via and Curb now letting users ride-share in the city's yellow taxis, New Yorkers can expect to snuggle up close in the back of a cab next to complete strangers. That's right, get ready to feel the love.

It seems like everyone wants to be flying without wings these days, and some big players in the autonomous car industry want a piece of that airborne action. Google co-founder Larry Page just invested in flying car startup Kitty Hawk, while Uber is adamant that its own-brand of flying vehicles will be zooming around the US come 2020.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

It seems nowadays there's no limit to what type of companies are looking to invest in augmented reality. Given both the positive outlook on the future of AR, and its reported benefits for efficiency in employees, this makes sense. Safran, an international corporation with three main sectors—aerospace, defense, and security—is one such company taking the plunge into incorporating AR in their business.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

The desktop browser market has some stiff competition going on, but Opera has always been able to maintain its market share by offering innovative features such as a data saver option. With over 350 million users, it's safe to say folks are appreciative of the efforts being made by the web browser's development team.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.