Killstreaks: Advantages and Disadvantages 3 Kills – Spy Plane: Advantages: This lets you see enemies on the radar in the upper left hand part of your screen. Though it is one of the lowest killstreaks, it is very beneficial and gives you a huge advantage. Disadvantages: It can be shot down and it will not detect enemies who use the ghost perk.
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

Search engine optimization (SEO) is now one of the most important topics for website owners to understand. Anyone that depends on their website to bring them business needs to know the ins and outs of SEO in order to maximize their website’s potential. And if you want your website to have a high Google rank then SEO is essential.

Google AdSense is a beautiful thing. They pay you for posting content online, whether it be through a third-party website like WonderHowTo or on your own website. WonderHowTo seems to be a good place to start from if you plan to make money with AdSense, but it's not the only place that you can submit content to and receive all of the revenue generated by the AdSense ad units. You may want to get a wider audience and more traffic, and for that you must look beyond the horizon of just one site.

China is a hot mess of traffic and is stereotyped for spawning some of the craziest drivers in the world. The traffic jams are known to be so bad, drivers have been gridlocked for 9 straight days.

This video is a series of short clips that show how to merge onto a freeway. These clips show how to assess the speed of the traffic already on the freeway (or highway) and join the flow of traffic safely. Made in the UK, if you're in a country that drives on the right, just think right instead of left and the principles will still apply. Merge onto a freeway or highway.

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

Ok, this prank is an idea I have for part of a comedy film I am writing a treatment for, and it is dedicated to pranks and pranksters!This idea is based on women always, ALWAYS, going nuts over their butts and how big they are! Women are always so self-conscious about their weight and their butts, and always putting guys on the spot asking how they look in clothes and if something makes their butts look big, so this is dedicated to all those women out there!We would need a guy, maybe a cast o...

Prefer a clear, hand-rubbed, "antique" finish to the shiny or satin sheen of varnishes? Then you will want to use a tung oil-based topcoat applied over an oil-based stain when you are staining or refinishing your special piece of furniture.

These home-made hifi headphones work as well or better than Sony or Bose noise-cancelling headphones. Cost: $2. Time to make:one minute. Difficulty:none. Unlike the commercial products, these block outside noise instead of cancelling it.

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

How to Find Cheap Airfare In a world with a troubled economy and where travel costs climb daily, getting the cheapest ticket for your flight home can be a scary task. Before you buy, check out this guide to help you find the best deal.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

To create an elegant WordPress blog or website from scratch without being noticed that you're a complete beginner, you need that drive and pairs of eyes and ears. It may seem difficult at first but it can truly be fun and exciting.

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

The trend of online video sharing came to the mainstream with popularization of YouTube, which let users view, submit and share video clips. YouTube started off in the year 2005, and quickly became one of the most visited websites on the internet. Sensing the emerging trend, large companies like Google joined the trail and launched their own video sharing sites (Google later bought YouTube).

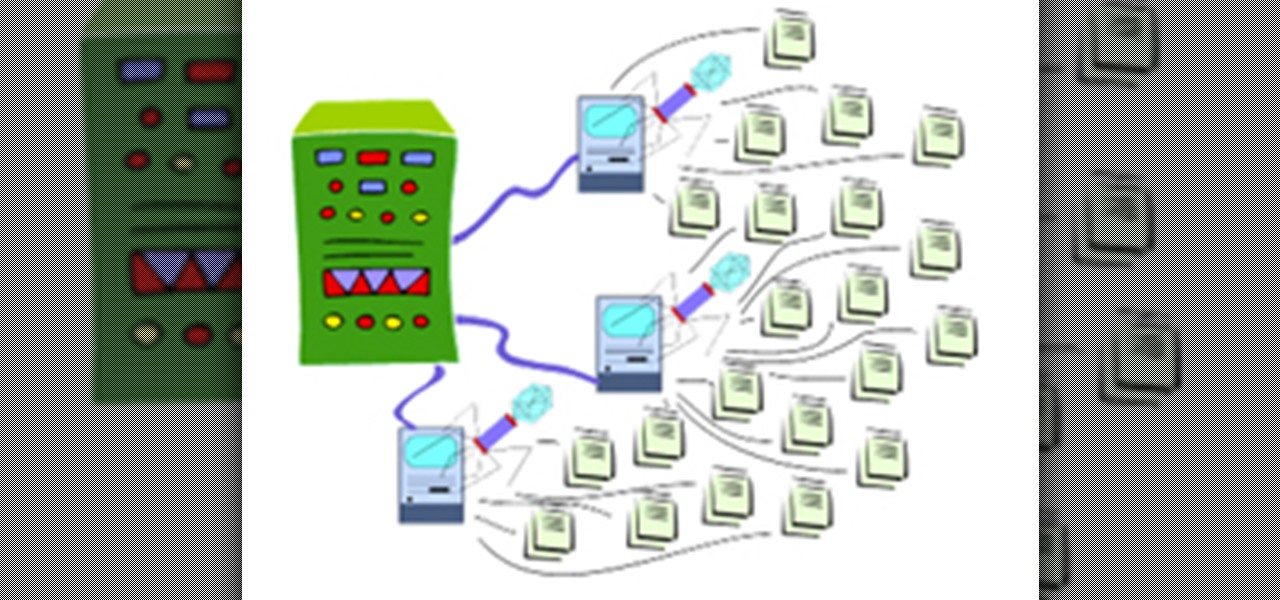
In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

Here's a winner! You have to go to kind of a backwoods ass town where Jackass might not be too known to make this believable. You set up sort of a small "village bar" in the middle of town where there's a lot of foot traffic.You'll bring a gathering of kids with various heights and let them in on the stunt. The "bar" has to be set at just the right height to where some kids can see over the bar counters and some can't. The stunt is to set up an outdoor village "beer bar" that is only served d...

There’s a lot going on in your head when creating a comic book and it doesn’t stop after it’s done. There are other things that you have to do once your comic book goes online. You have to market it, introduce it to the right market, and find a way how to get it published.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

Not every DIY project is as executable as, say, making a potato gun. Occasionally, we observe a quixotic project that is just plain wonderful. Consider rich guy Philip Anschutz and his eponymous Anschutz Entertainment Group (AEG). His ambition to bring an NFL team to Los Angeles is a Fitzcarraldo-sized DIY project that, if the stars align, might happen in time for the 2016 season.

Advertisng is the key of selling products. Internet is one of advertising media, So many websites on the internet just making money from the online advertising. In online advertising the one that play an important part is traffic or page rank, the website is not valued by appearance or designing only, nor the cheap or the special products only, but the most have a role is traffic. Eventhough the appearance and your produst on the site is cheap you can't get buyer or visitor with the weak page...

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Panasonic announced an interesting concept today that could advance millimeter-wave radar technology for automotive safety uses in detecting pedestrians, bicyclists, and other motorists.

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

As you may have seen in your city or town, red light cameras are on the rise in the United States. In many instances in my area, these cameras have sprung up seemingly out of no-where, and mostly without any reason. Over use of these systems can make privacy (even on the road) a fleeting possibility.

This article is all about creating content. This is a very important concept to grasp because the content that you create for a website is going to be the basis for how you will advertise and promote that website. Content, meaning articles, videos, and even podcasts is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

As you may or may not know, the US and France have deployed four nuclear warships on either side of the Strait of Hormuz, which, along with helicopters, scour the area for underwater mines.
The niches are the foundation of a successful marketing strategy. You need to focus on the niches in a market and develop a strategy for each niche. You'll attract more targeted traffic that way, which will result in more sales.

White: the first thing comes to my mind when I see light white is an angel, I think that this color represent the good side of everyone, the angel form of a person, sometimes you can see someone and look at him like he is a real angel, what a wonderful feeling, and even someone who is very gentle with you, you can display him in your mind with a white circle on his head.

China's latest futuristic project is a massive "3D Express Coach", a clever project proposed by Shenzhen Hashi Future Parking Equipment Co. as a solution to traffic in the extremely overpopulated country.

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

On a Wednesday evening when friends are going to a movie or out to dinner, you’re at the dojo training.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!
If the SOPA bill passes, people won't even be able to do things like cover a song on YouTube. Don't let this bill pass. If your ISP is blocking the petition (most are) then, please, tunnel your traffic through another country and continue to sign up. This affects all users of the internet in a negative way. This bill will pass unless it is stopped by the people.