I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.
Healthcare providers have unique desktop environments that range from "Workstations on Wheels" to nursing stations in

By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe".

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

In this article I am going to take a look at the Google keyword tool, which is one of many keyword tool programs that you can use to find your keywords.

This article is all about creating content and using it to build links to your website. Content, meaning articles, videos, and even podcasts is now really the new advertising. That’s because people go to the internet to look for information, not look at advertising. So you need to create compelling content about your business, your industry in general and any topics connected to your entire field that people will want to read, listen to or watch.

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

The DIY industry is booming, despite the desperate blackmailing of society by finance capitalists. Companies like Adafruit and Makerbot are grossing well over a million dollars a year, and Evil Mad Science Laboratories just recently dedicated themselves to running a full-time kit business. Making kits is fun, but starting a business can be scary. If you already enjoy making gadgets and want to take the plunge into selling your own kits online, this article is for you.
With more and more vehicle owners simply deciding refuse to pay red light camera and speed camera tickets, private, for-profit companies and municipalities are growing increasingly desperate. America’s second-largest city shut down its photo ticketing program last year largely because residents who could not afford the $500 citations did not pay them. On Monday, Las Cruces, New Mexico announced it would shut off the utilities of city residents who refused to pay Redflex Traffic Systems, the A...
Make money promoting yourself, build links and drive traffic. Yes thats is right you can get paid to promote yourself by using free to join sites that let you share revenue, I have included a list of sites that will allow you to build links to your online content or sites. this will aid in building your site authority as well as let you make some revenue to help you pay for your hosting fees ect.

A prolific travel writer can always consider starting his own travel site. If you know a country or a city inside out then you really can start your own site, work on drawing traffic and make money from ads. Not much money, maybe but something. And you get read.

Cyclists and unknowing vehicle participants "collaborated" on a public guerilla graffiti art piece in Berlin this last week.

This clip shows a large double roundabout with traffic lights and how to negotiate the lights as you turn right and then straight.

Begging is a skill. It can be quite helpful in ordinary life situations like traffic court, navigating customer service or getting a babysitter on a Saturday night.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

¬¬Just about every business has a website these days but very few businesses know how to effectively use their websites to get more customers. There are two different things that a business owner needs to do to increase their website traffic: optimize their site so that search engines can find them easier and promote their site on the internet so that they have greater visibility. This article will discuss how to optimize a website.

If you’ve never heard of the term search engine optimization or SEO, then your website probably isn’t optimized for search engines and it’s hindering your site’s ability to get all of the traffic that it should. Read on for an explanation of what this entails and how it can help your website.

+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

It's the most wonderful time of the year. Christmas lights are up, stores are crowded, tacky knit sweaters are making an appearance, and there's the constant smell of something delicious baking in the oven. In this week's Phone Snap Challenge, spread some holiday cheer by showing us your holiday-themed cell phone photos. Post your image to the corkboard by Monday, December 26th at 11:59 pm PST for a chance to win a set of fun Photobooth Props from Etsy store LittleRetreats just in time for th...

Thank you to everyone who entered Phone Snap! and MacPhun's contest for the International iPhoneography Exhibition. There were a lot of impressive entries, and I'm very excited to announce the three photos that will be shown at the exhibition December 18th through the 22nd at the Soho Gallery for Digital Art in New York City.

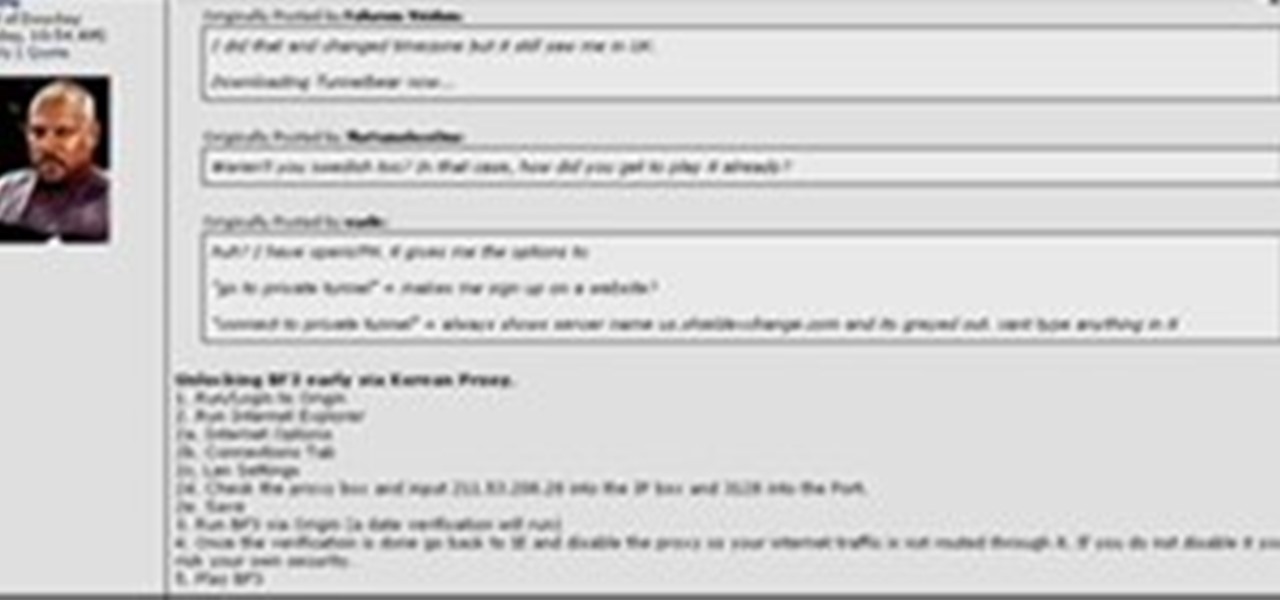
Battlefield 3 officially comes out tomorrow but people have figured out a way to play it today if you have it downloaded (digital pre-install). All you have to do is fake an ip to make it look like your timezone is ready to play. I'll try this when I get home, in the meantime:

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

You're sitting in your favorite café enjoying a hot cup of joe, then you open up your laptop or turn on your tablet computer to get to work, but as always you get sidetracked and head straight for Facebook. Someone just tagged you in a photo, so you check it out, then you see it out of the corner of your eye—your Facebook picture digitally displayed on the wall in a nice, neat digital photo frame.

How about a laser? One that is strong enough to nudge debris out of earth orbit. That's what NASA contractor James Mason wants to do, and his lab simulations suggest that the idea is possible. Mason wants to use a 5kW ground-based laser and a ground-based 1.5 meter telescope to spot potentially hazardous space waste and shove it off, by about 200 meters per day of lasering. It's kind-of like air traffic control for near earth orbit.

According to PlayStation Network @ Home, a new app may allow hackers to ban or unban anyone they please from PSN.

It may look like a modern take on Oliver Twist but, we assure you, this is for real. Before you get too alarmed, however, you should note that the headline reads "how to steal cars" and not simply "to steal cars." We are, after all, dealing with the fine people at Machine Project, a Los Angeles-based non-profit community space organized around the investigation of "art, technology, natural history, science, music, literature, and food."
From LAist: Los Angeles may be gearing up to finalize its master bicycle plan, which would bring some 1,600 miles of bikeways to the city, but that may not be enough for those whose primary location is USC. That's where some 10,000 to 15,000 cyclists roam the campus each day, according to 2009 report.

This prank will involve as many people as you can fit into one car, and you will need to have the majority of your buddies dressed in military outfits. The one exception is that you will need to have one person dress up as the military sergeant, which will be leading most of the prank. You need to rig the car that you are using to smart smoking from the hood, or if you want to make it more realistic you could actually have the wheels fall completely off the vehicle itself once it has entered ...

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.

Via WonderHowTo World, LoadSave: Rock Band 3, coming this Fall, was revealed at none other than USA Today. Fully functional 25 key keyboard, 80+ songs including The Doors and Bohemian Rhapsody, Pro mode, updated guitars, and a kitchen sink are included in this new sequel. USA Today:

LEGO Technic builder Peer (Mahjqa) Kreuger has constructed the incredible Stilzkin Bridge Launcher, a vehicle modeled after real life ALVBs (Armoured vehicle-launched bridge).

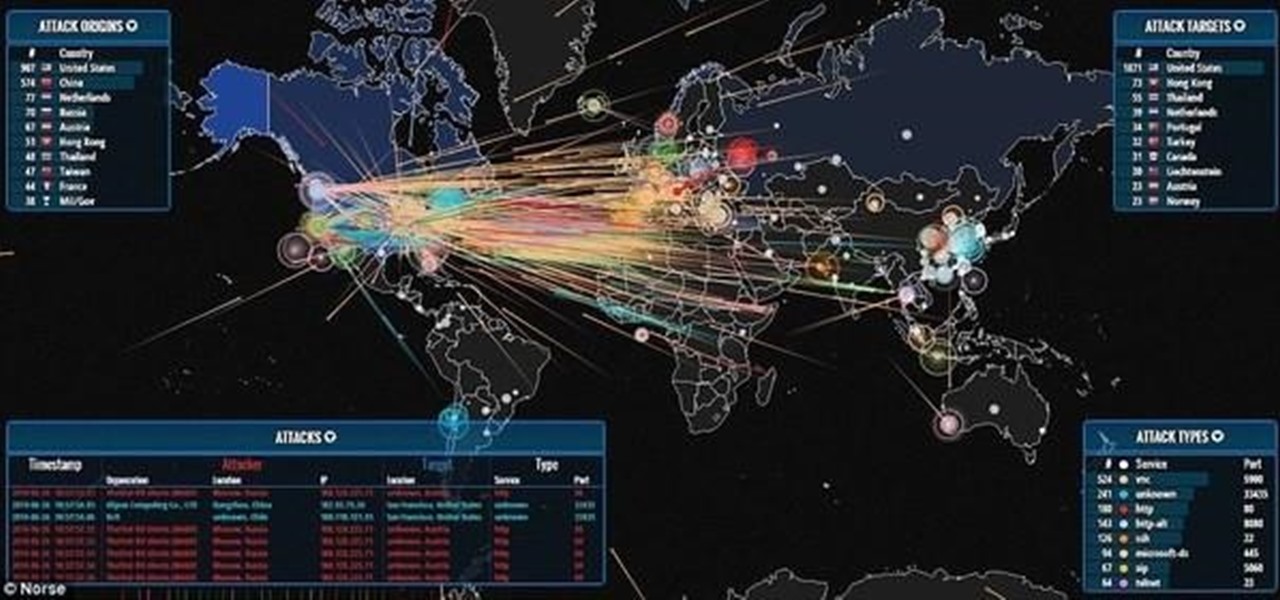
This is a live map feed to current DDoS Attacks globally. Live DDoS MAP Thought I would post this to give you an idea of the size and scope of DDoS Attacks at any given moment. Plus it looks k00l.
Welcome back my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on us all, all the time.

Remember Dan White's "Twinkie defense" in 1979? Well it turns out that the the ability to convert food into glucose is correlated with the ability to control oneself.

Whoa. Someone just got caught this weekend cheating at the 2012 National Scrabble Championship in Florida. He was holding on to some blank tiles, which dropped on the floor mid-game. How did this kid even think he'd get away with hiding blank tiles? Wouldn't it be a little suspicious once his opponent got a third blank tile from the bag? It was the first time anyone has been caught cheating in the National Scrabble Championship, though that can't be said for club, regional, or world tournamen...

By Camilla Cicconetti - Visit LifeStyleWebTV for more travel articles, videos, recipe demos and more.

This is the first official announcement for a new weekly activity on Null Byte for the community to participate in. Starting next week, depending on how much traffic we get doing it, we are going to start doing live social engineering calls via Skype. I've made a list below so that you can get a feel for some of things we'll try to accomplish in these calls.