Welcome to part 7 of this epic 60-part video series on how to make your own website using Flash CS4 from scratch, no experience necessary! This section details how to use actionscripts and other techniques to make your websites more interactive and appealing to potential traffic.

If you have to change a tire out on the highway make sure that you are well out of the flow of traffic. If you have materials to help people see you put them out and make sure that you only use the jack if you are on a hard flat surface. Using a jack on a soft surface such as sand can lead to the car falling off of the jack. Set your emergency brake and turn on your emergency flashers. Check the owners manual for step by step directions and safety tips for changing the tire. Take out the spar...

Popular Mechanics' Senior Auto Editor Mike Allen shows you how to safely stop your car if you become the victim of sudden unintended acceleration.

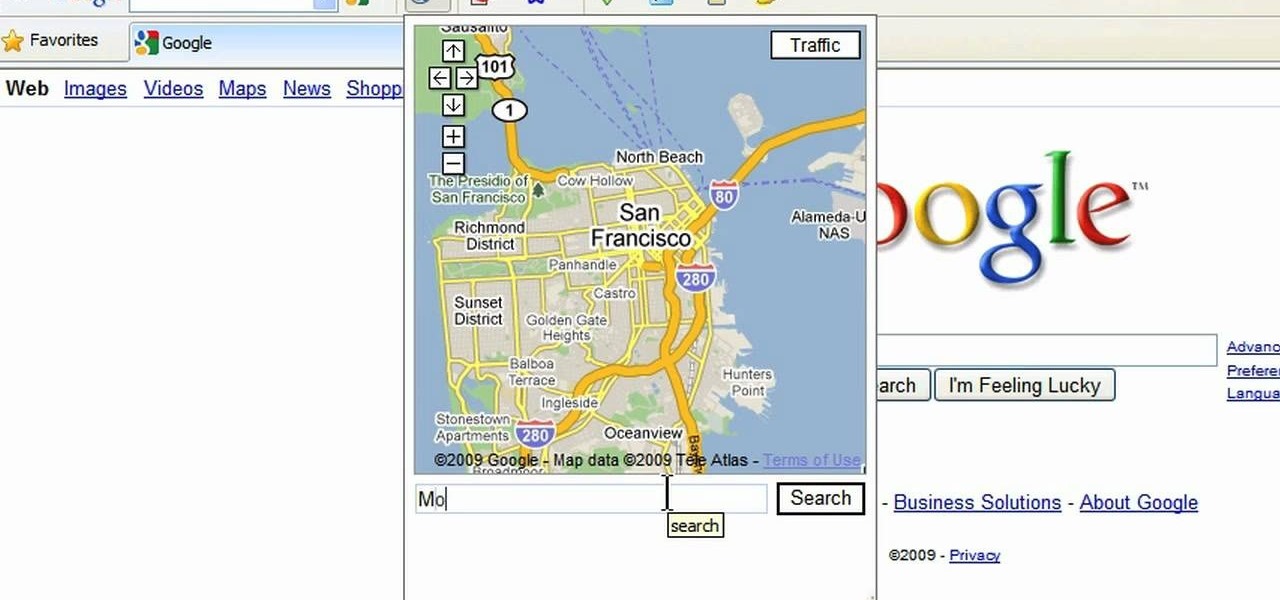
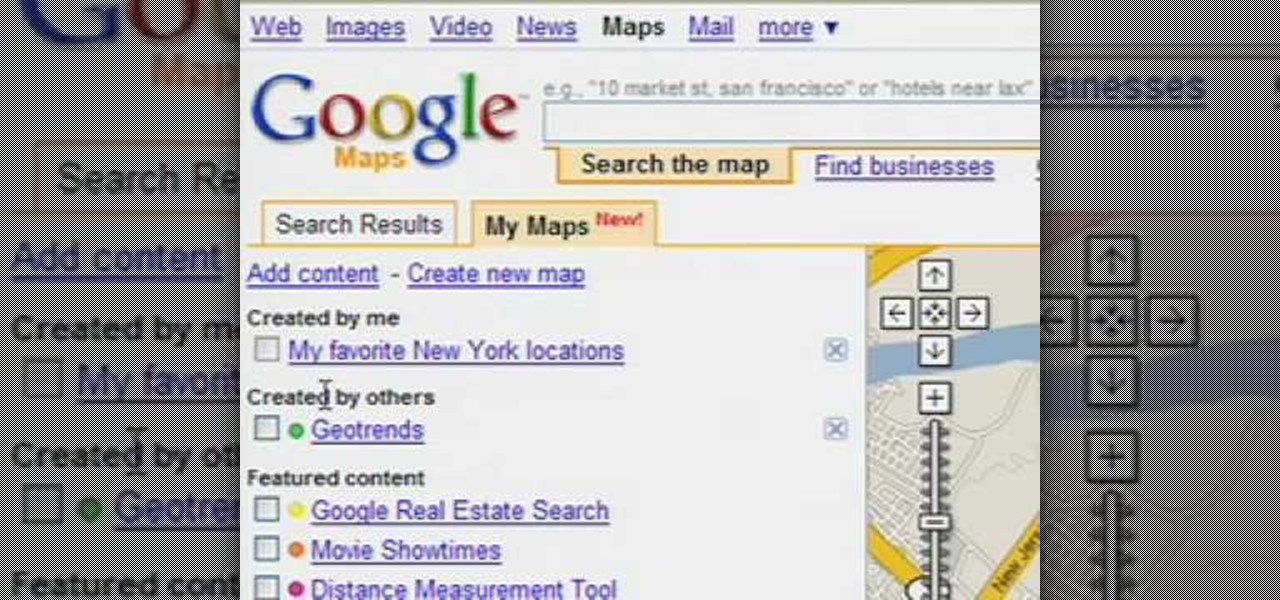
This video tutorial is about using Google Maps and the features in it. Google Maps help us to find the geography and even the traffic situations of a city. Google maps also provide a street view option that helps us to see how a place actually looks like from the ground. Neither of these views are real time. But now, Google Maps has added in a new option, which is the webcam. Just click on the more option in between traffic and map option. In the list that appears, just tick the webcam option...

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.
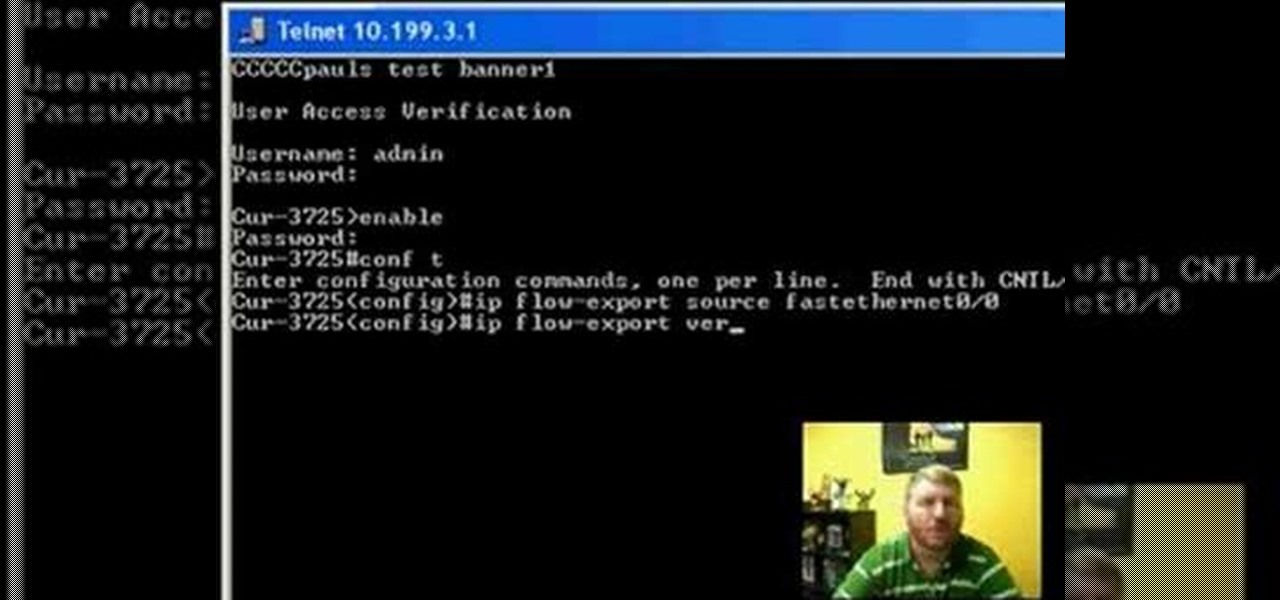
Netflow technology allows you to monitor web traffic to your website - find out who comes to your site, where they're coming from and where they go afterwards. You can configure a Cisco router manually to monitor netflow going through the router.

Have you always dreamed about quitting your day job to pursue your true passion in writing about tips on how to bake your famous cupcake pops? Stop dreaming and start doing! Thanks to the prevalence of the internet, blog writing is more popular than ever, and successful bloggers actually make quite a hefty chunk of change doing what they love.

Ever wonder how to get out of doing the things you don't want to do? Work, relationships, and simply driving in traffic can make you so tired that you're asleep on your feet. Not any more!

In 1998, a Beechcraft Baron was following a Boeing 757, with approximately 3 to 5 miles separation. Air Traffic Control warned the Baron pilot three times with the phrase the phrase pilots hear on a regular basis: "Caution. Wake Turbulence".

Catching sight of a hummingbird floating from flower to flower is one of those rare gifts from nature. In this quick and easy guide, use a little bit of science and learn how to make a hummingbird feeder that will attract all the birds in the yard.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

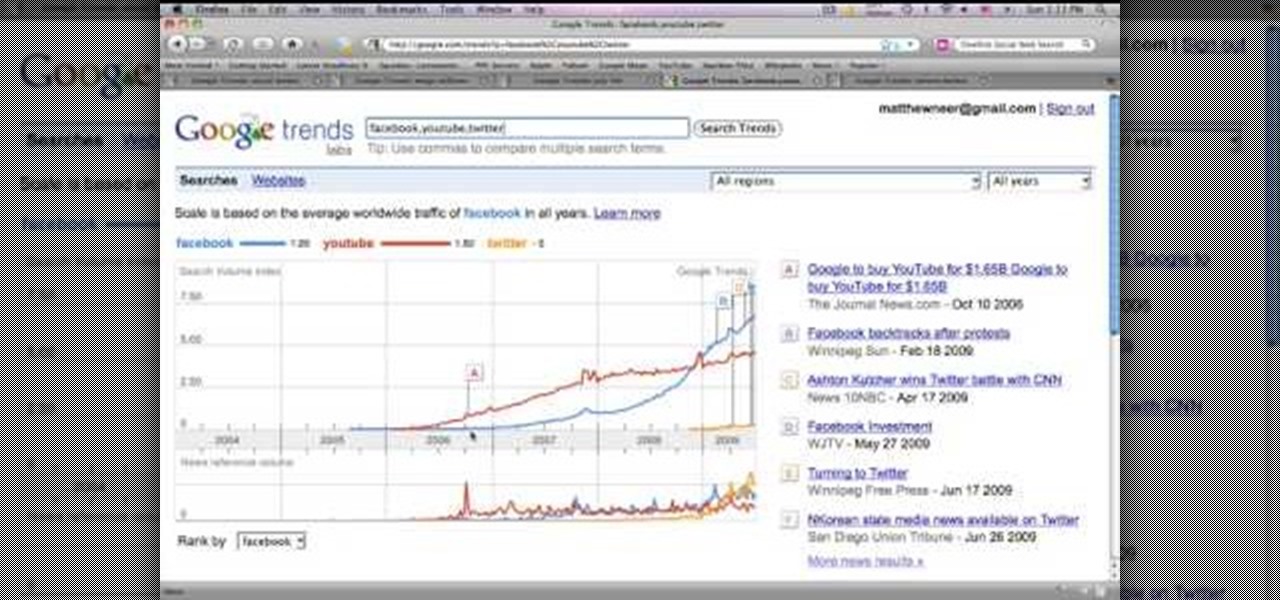
In this Computers & Programming video tutorial you will learn how to track Google's trends features. This will help you find some powerful micro niches and great keywords to create content and get top rankings in search engines. Any trend on the internet first starts with an event. For example ‘mega millions’ gets lot of traffic when someone wins a jackpot or a big lottery draw is coming up. Similarly, ‘July 4th’ traffic spikes around that event and dies down. If you want traffic from this ev...

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Google Analytics is a state of the art barometer of how a website is doing. With this program you can measure traffic, get statistics and anything else you would like to know about your page. This free service is especially useful to business owners and others who depend on site traffic to stay afloat. So, whether you need it for business reasons or are just curious, check out this clip and get started with Analytics.

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Accidents are the worst. They're costly, time consuming and an all around pain in the butt. Rear-end collisions are among the most common types of accidents on the road. Take these simple precautions to avoid a rear-end collision.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

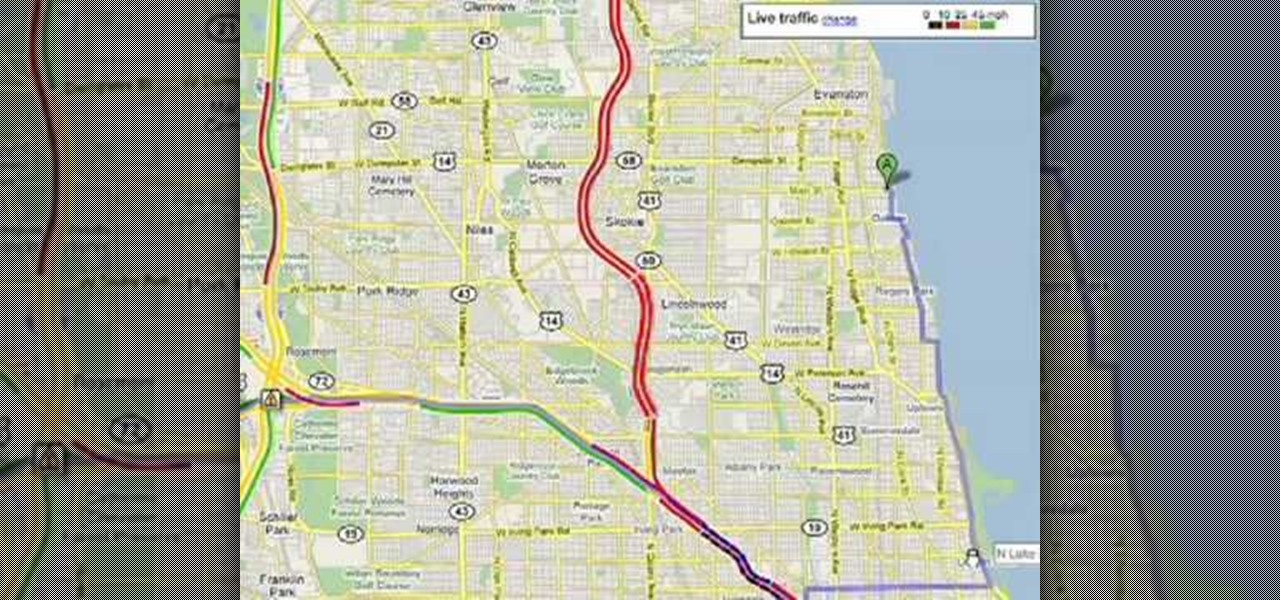
This is a video tutorial in the Computers & Programming category where you are going to learn how to avoid traffic jams using the Google Maps button on the Toolbar. Click on the Google Maps button on the toolbar. This will bring up the maps window. Here you type in the area in the search box, for example, "mountain view, ca" and click 'search'. On the next window click on the 'traffic' button and the map will then show you the roads that are clear of traffic jams in green color. There you go!

In this video, we learn how to use the iPhone map app. First, go to Google Maps and click on the bottom to find your current location. This will show up in a blue button, which you can tap on to find out more information. The map will go in the direction your iPhone is facing and you can zoom in on information about places around you. You can also type in a place you are searching for, and get directions, then save them to your phone if you prefer. The key is the button on the bottom right wh...

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

If you're looking to increase the ranking of your website in Google, and so increase your traffic, you'd do well to at least a rudimentary understanding of what Google looks at when considering the relevance of a web page to a given query. This SEO tutorial offers a cursory explanation of how the Google search robot sees, or spiders, your website. Drive more traffic your website with this SEO how-to.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way.

Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way. Print directions with Street View, photos included.

Needless to say, we're talking minor traffic violations. If you've just led the cops on a high-speed chase down the freeway, you're on your own.

Collin teaches us how to race at Laguna Seca raceway in this tutorial. When coming out of the pit lane, wait for the workers to wave you on. Make sure there is not traffic around you because you will be doing over 100mph. Once you are sure there is no traffic, turn in the late turn so don't dual apex it as you are turning. By this time you will turn four and then turn five after this on the right hand side of the track. Next, turn six with a small amount of braking bringing the car out and ru...

Watch this video tutorial to learn how to use hand signals on a bicycle. Bicycles don't come with turn signals and brake lights. Fortunately, there's already a universal language for indicating turns and stops on a bike.