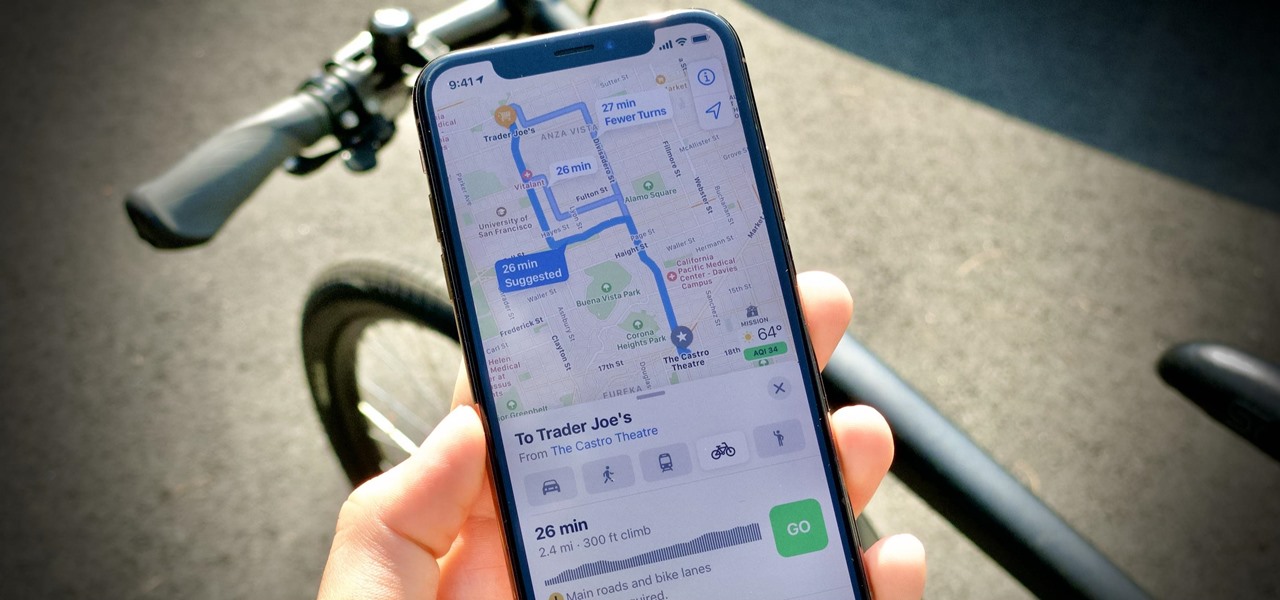
Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.
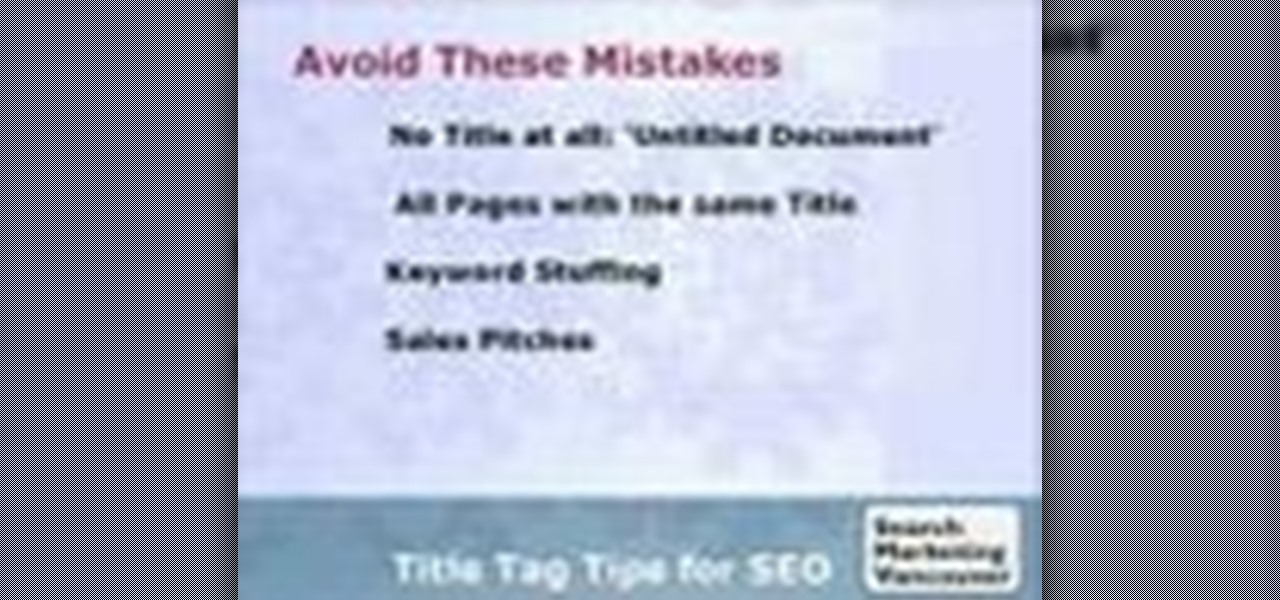
How to write Page Titles for your Title Tags from Search Marketing Vancouver. Learn how effective Title Tags can improve your SEO Results on Google and increase traffic to your website.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you're drawing the most people to your website and affiliate links by utilizing the latest and most powerful SEO tools and methods.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Some of the things that make Waze such a great navigation app are also its biggest downsides. Real-time data shows where individual users are, and the app automatically gathers traffic info that other drivers may encounter. These elements ensure that road conditions are as up-to-date as possible so that everyone gets to their destination safely, but it's certainly not ideal if you're a privacy-minded user.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Geotagging your location on Instagram is one of the most undervalued ways to generate traffic to your profile. The beauty about adding your location to your IG posts is that it allows you to be seen by other users than the ones that already follow you.

In the driverless race, technological advances can sometimes just add more tension to an already heated competition, if Waymo suing Uber over their allegedly stolen LiDAR technology is any indication. Now, Sony is offering a new camera sensor, one that should help self-driving cars "see" the road with much more accuracy than any other camera sensors available for vehicles currently.

Greetings my fellow hackers.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

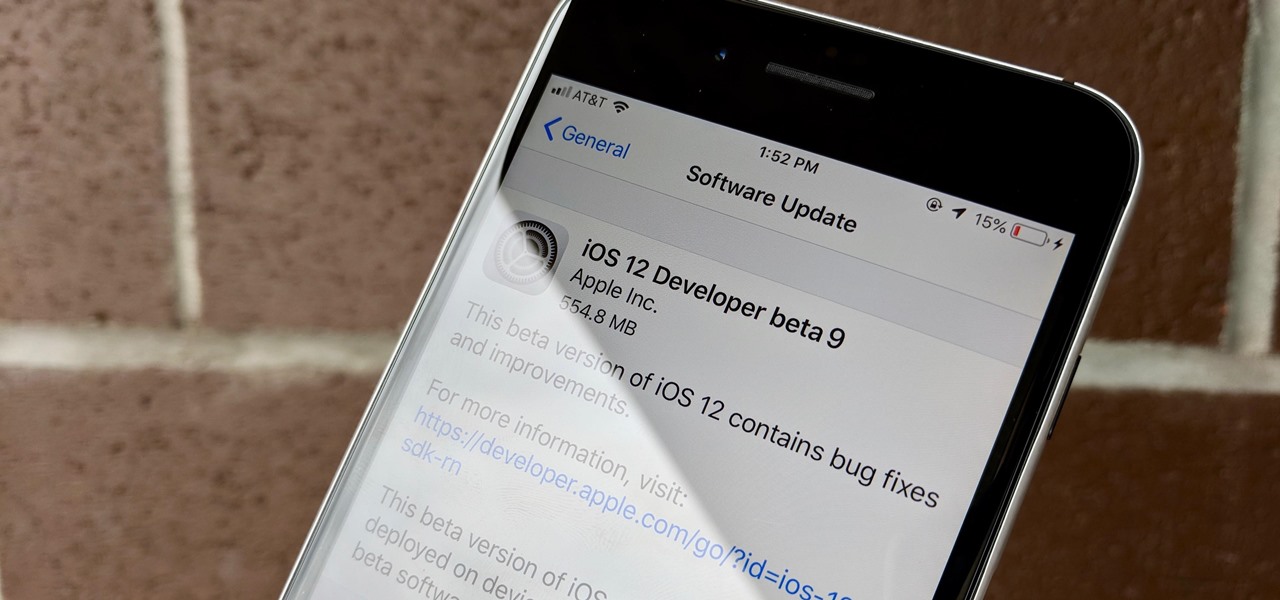
Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Cortana, Microsoft's voice-activated personal assistant, originally launch on Windows Phone, but is now built directly into Windows 10 complete with "Hey Cortana" voice search (take that, Apple). It can help you locate files, set up reminders, control music.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

Once the laughing-stock of the navigation app market, Apple Maps is now a powerful, reliable travel companion. Apple rebuilt the platform from the ground up, placing the app in league with Google Maps. That said, there's always room for improvement, as demonstrated by its impressive new features set in iOS 14.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

The launch of Android 4.1 Jelly Bean was also the launch of Google Now, a service that was supposed to one-up Siri, the resident personal assistant for iOS devices. Google Now offered enticing features, but its launch went unnoticed by a great many Android users.

Tired of your PC pestering you to check this or fix that? Are you sick of all those pop-up balloons? Well, Windows 7 now has a feature called Action Center, and it lets you decide which alerts you see and which ones you don’t. See it in action!

Like driving a car during rush hour traffic or sitting unmoving at your desk, your body is not designed to sit in one position for a long time, which means that if you ride a horse you may encounter back problems.

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Texas has become the 18th state to pass a bill into law regarding autonomous vehicles, the third this month to do so.

So, according to Sprout Social, mentioning an Instagram handle in the caption of your posts increases audience engagement by up to 56 percent. If true, that's pretty impressive.

While Live Photos has been a fun addition to iOS ever since the iPhone 6S and 6S Plus, there hasn't been much practical use for Apple's moving images so far. That was, until iOS 11 added advanced features such as long exposure effects that make a DSLR less and less impressive these days.

After Uber noticed that if you walked to a more convenient pickup spot — instead of your exact location — that it would save you time and money, they decided to make a change to their system.

Disney is gearing up fully autonomous vehicles that will shuttle you and your family from the parking lot to the amusement park, stress-free. Well, as stress-free as you can get while introducing grandma to the concept of a car with no driver. No, grandma, Satan is not "steering this contraption." At least, we don't think he is ...

There's nothing worse than driving up to your destination only to discover that there isn't a parking spot in sight — but thankfully, Google Maps will soon have you covered.