
News: No, You May Not Pumpkin All the Things [DEBATE]
Guys, this has got to stop. It's not funny anymore. I'll defer to one of my all-time favorite people when it comes to my feelings on this unsavory subject:


Guys, this has got to stop. It's not funny anymore. I'll defer to one of my all-time favorite people when it comes to my feelings on this unsavory subject:

When we talk about augmenting our reality, we often first think about vision instead of our other senses—but there's more to an immersive experience than what you see. One inventor figured out how to utilize sound and touch to create a simple, upgraded version of laser tag that you can play with your smartphone.

Emojis, for better or for worse, have essentially taken over online forms of communication. And now, thanks to a recently discovered feature in iOS, they are going to change the way you search for nearby places.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

There's been a whole lot going on at this year's Consumer Electronics Show, from the latest in virtual reality gear to televisions that continue to slim down while producing higher quality images.
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.

Apple's special September event just wrapped up with the company unveiling several new products, including the iPhone 6S, iPhone 6S Plus, iPad Pro, and the new Apple TV set-top box. In addition to hardware, Apple also discussed a couple of its latest software platforms, iOS 9 and watchOS 2. Check out everything that Apple unveiled below.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

Flowers may be beautiful, but they're not usually appetizing. Sure, nasturtiums are hip in fancy restaurants, but they're primarily used as a garnish. Granted, fried squash blossoms are incredible, but the point remains: flowers are usually reserved for looking at, not masticating.
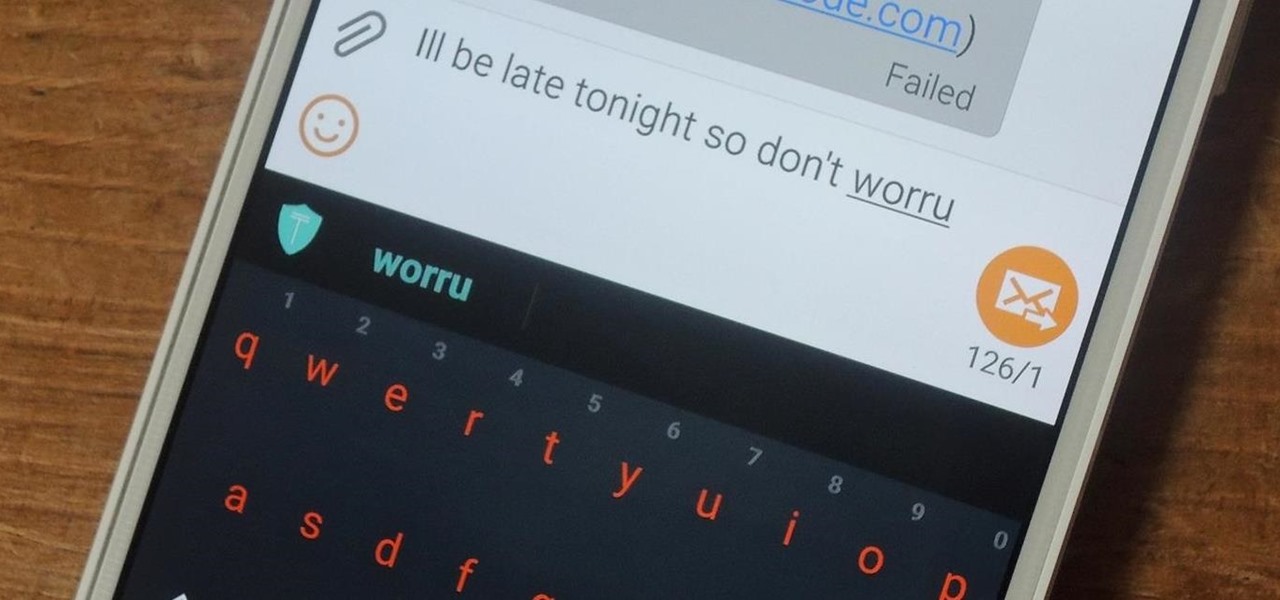
My reliance on autocorrect has made me a horrible speller. I take it for granted that it'll catch all my mistakes, but it only ends up making matters worse (especially when it inadvertently makes correct words wrong). So instead of relying on autocorrect to fix typos, why not try to completely prevent mistakes from happening in the first place?

Welcome back, my hacker novitiates!

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

When you have a parent who cooks—and has you act as sous chef—the kitchen automatically becomes a less intimidating place. In other words, kids who know their way around the kitchen will most likely become adults who cook for themselves, which also means that they'll eat more unprocessed whole foods, save money, and maintain a healthy weight.

After utilizing Spotify's My Year in Music tool, I came to realize that I listened to over 30,000 minutes of music in 2014. Most of that was played while working from my Mac using the desktop version of the service.

The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:

True story: a friend of mine regularly started a fight with her boyfriend everyday at 4 p.m. Every day. This went on for years until he finally got the bright idea of shoving a granola bar at her the minute she came home from work. Shazam! The fights were a thing of the past.
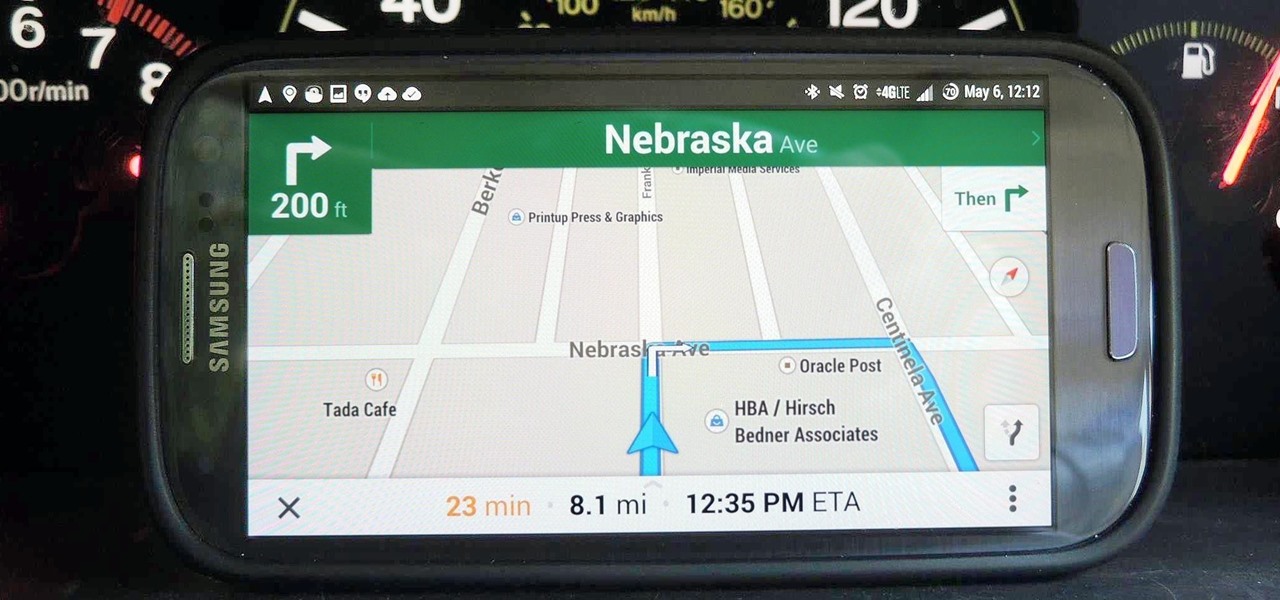
This week, Google sidestepped their usual "Update Wednesday" strategy by dropping a huge update to their Maps app for both Android and iOS. We're accustomed to seeing new features and bug fixes to their stable of apps on Wednesdays, but today's Maps update was presumably big enough to get its own release day (it's Tuesday, folks).

The Galaxy S5 is a flagship-level device with some pretty advanced features, like its 4K video recording capability, water-resistant casing, fingerprint sensor, and KitKat running out of the gate.

Wondering how to get long hair naturally? How do you grow your hair? In this video Rachelle and Sam give you 10 tips to get those long locks naturally!

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

The final chapter of Christopher Nolan's Batman trilogy is here, The Dark Knight Rises, and if you're anything like me, it made you want to immediately don a cowl of your own and run around punching criminals. Don't forget though, one of the most awesome aspects of Batman is his never-ending supply of crazy gadgets. Unfortunately for most of us, we don't have a billion dollars, nor Morgan Freeman, so we'll just have to make do with some good old-fashioned DIY tricks. Read on for a rundown of ...

Learn all about functional training and resistance exercises with expert advice and demonstrations in this free fitness video series on functional training with the kinesis system.

Super Mario is back in another fun-filled Galaxy game! The highly acclaimed game, Super Mario Galaxy 2 for the Nintendo Wii, was released on May 23rd, 2010. And believe it or not, but it has already reached 3rd place (as of 07/22/10) at GameRankings for the best reviewed games, just behind the original Super Mario Galaxy.

Need a new hobby? How about railroad modeling? You can turn a full sized train and rail transport into a scaled model for you to enjoy. Model railroading is a hobby that requires attention to detail, so no slackers here, please.

Tick bites should be treated immediately, the concern being transmission of Lyme disease. If you've received a tick bite, what you should do is to remove the tick promptly and carefully. Use tweezers to grasp the body of the tick near its head and pull out very gently to remove the tick whole without crushing it. Learn more about tick bites and how to treat them in this medical how-to video.

If you want to improve your violin bowing technique then this tutorial is for you. This violin lesson teaches you a great exercise to improve your spiccato bowing technique. This exercise , based on the Yost system, is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should re...

Do you want to improve your violin playing technique? This violin lesson teaches you a great exercise to improve your octave technique. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should relax your fingers, hand ...

Do you want to improve your violin playing technique? This violin lesson teaches you a great exercise to improve your tenths technique. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this tenths exercise you should relax your fingers...

Do you want to improve your violin playing technique? This violin lesson teaches you a exercise in broken octaves in first and third position. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should relax your fingers...

Do you want to improve your violin playing technique? This violin lesson teaches you a great exercise to improve your octave technique in first and third position. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you shou...

Do you want to improve your violin playing technique? This violin lesson teaches you a great exercise to improve your octave technique in thirds in first and third position. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercis...

Do you want to improve your violin playing technique? This violin lesson teaches you a great exercise to play your octaves in broken thirds, seconds, and fourths. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you shoul...

See advanced Aikido techniques to help you learn Aikido in this free martial arts training video series.