This cone drill workout were developed to increase you overall sports performance. This how to video explains the cone drill exercise and how you can incorporate this agility training to develop your flexibility, balance and power.

Watch this instructional magic trick video that reveals how to penetrate a coin through a balloon. This easy magic trick will awe your spectator as you practice your magic skills. This is a great video for magicians in training and magic trick enthusiasts alike.

If you are a firefighter in Alameda, California, chances are you already saw this video tutorial. If not, you're in luck. This will show you how to rescue a downed firefighter out of a window. This is a step-by-step training video for removal of a downed fireman out of a window of a building or house. It's just like Backdraft, folks.

Dogs are pack animals, used to the concept of each family having a leader. For the dogs to be a good pet, they need to understand that the human pet owner is the alpha leader. Learn how to easily establish yourself as the "Alpha" in your dog's eyes by watching this video pet training tutorial.

Perform butterfly low reels for poi with tips from this how-to video. This poi video is for beginners. To perform butterfly low reels, you must first know how to do basic butterfly spinning for poi. This move is very cool and will lead to some wonderful things once you've completed your poi reels training.

This video demonstrates the proper way to put on a hakama for aikido. It is said to be a quick and easy way. This is demonstrated by an aikido club member from Wimbledon, London, UK.

Learn a technique for coring a pineapple taught by a classically trained French chef.

This tutorial shows you how to add a depth of field effect to footage in Sony Vegas. This focus effect example is of a train.

Check out this video to learn how to teach your dog to walk backward using the clicker training method.

This lesson covers six odd-time beats that are played in the 5/4 time signature. Unlike most rock drum beats, that are played in 4/4 with four quarter notes per measure, these beats are played with five quarter notes per measure. Watch the included video for step-by-step training on how to count and play these unique beats.

Learn how to say "Can you drive me to the train station or airport or hotel?" in Polish.

Learn how to say "Can you drive me to the train station or the airport or the hotel?" in Spanish.

Learn how to reinforce proper mechanics and improve your athletic performance with the help of this series of skip and run drills.

Watch this video to learn how to do "hammer training" aka slamming a sledgehammer on a huge tire.

Learn step by step how to do a wall back flip. You must be able to do a back flip before trying this maneuver. Exercise good judgement when doing this move. This videos works best if you've had prior gymnastics training.

Olympic Gold Medal winner Sheila Taormina demonstrates the high elbow catch (HEC) swim stroke using the Halo Swim Training system and as explained by Craig Askins. The high elbow catch is considered a key component in the success of todays best swimmers.

Olympic Gold Medal winner Sheila Taormina demonstrates how to use proper technique for power stroke training in competitive swimming.

Learn how to use weights for working multiple joints through multiple exercises. This video gives some great combo weight training exercises.

Build power and speed with this Plyometrics workout video. These exercises should be done 2-3 times 3 times a week. Of course in order to lose weight with any strength training program it is important to also do cardio workouts at least 3 times a week.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

We all know IT development is a valuable skill to have. But being a certified professional in the world's most in-demand project management and development tools? That's enough to get the promotion or new developer career you've been dreaming about.

Whether you want to build your own website for your business, start your new lucrative career in web development, or gain a wealth of projects to add to your portfolio, this course will help you do it. And right now, "The Complete Web Developer Course" is on sale for just $14.99 — a staggering 92% discount off the regular price of $199.

Always wanted to learn Python but don't know where to start with the high-level programming language? The Basics for Python Development is perfect for beginners — and right now, it's on sale for just $14.99, which is an impressive 92% off its usual price of $199.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

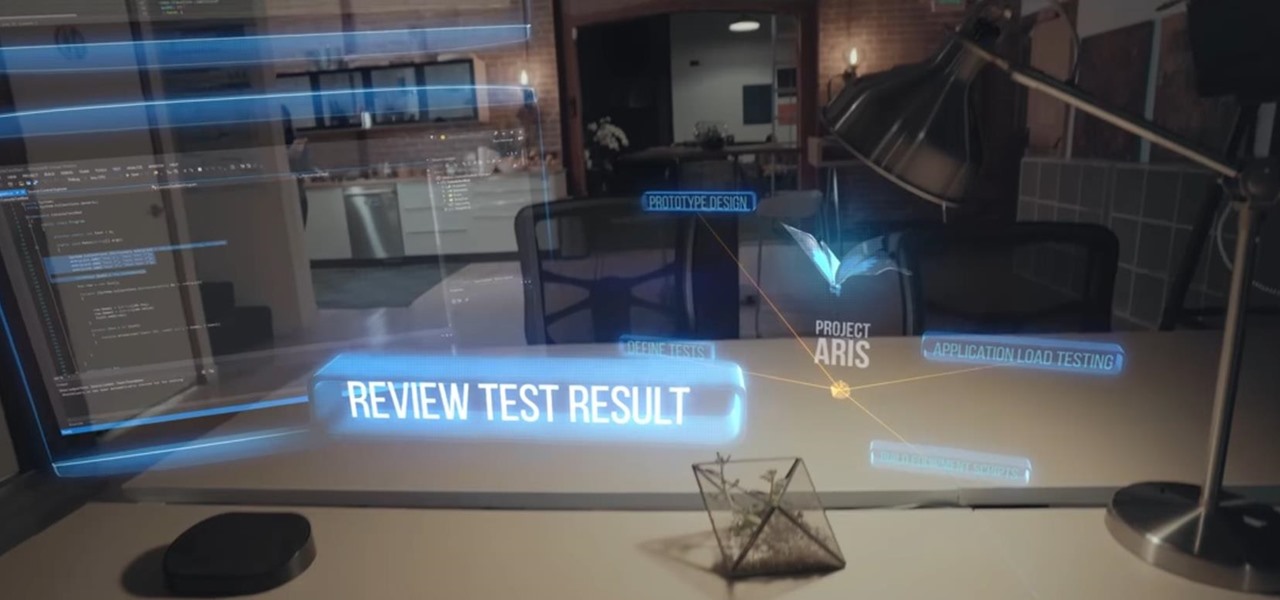
While the big names in augmented reality demonstrated the breadth of opportunities in the industry's landscape this week, one new startup showed off what is possible further in the future.

The recent Oculus conference in California revealed just a bit more about Facebook's secretive plans to compete in the augmented reality space with its own wearable devices.

Developers in the augmented reality industry got a lot of love this week.

Sony Pictures has tapped the powers of augmented reality as provided by startup 8th Wall & the Amazon Sumerian development platform to help it promote the latest motion picture manifestation of Spider-Man.

With would-be unicorns Magic Leap and Niantic among its investments, Google is an active investor in augmented reality technology. This week, the search giant experienced both ends of the investment cycle, with an exit via Lyft's acquisition of Blue Vision Labs, and a funding round for Resolution Games.

This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.