
How To: Do 3 Strand Twist on Any Type of Hair Easy!! | AKiyia's Method
This Video will show you How to Do Two Strand Twist. I had been practicing looking at different YouTube Videos


This Video will show you How to Do Two Strand Twist. I had been practicing looking at different YouTube Videos

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

How to fight multiple attackers with 5 simple Wing Chun techniques that will help survive a attack by a gang of multiple attackers. These are some of the best tactics on how to fight a group of people while staying safe.

This Video will Show you How I Dyed My Synthetic hair with Acrylic Paint. The Hair I used Was 1 pack of Femi Kinky Braid Marley hair;
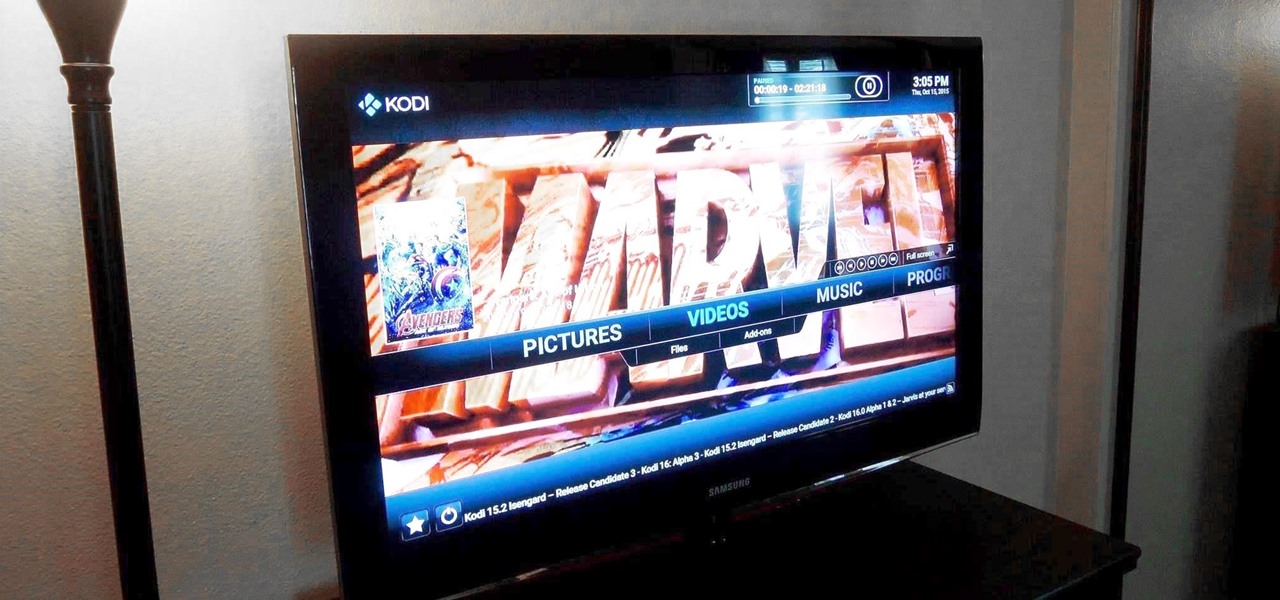
Amazon thinks that by simply removing an app from their Appstore, that they will stop users from accessing it. But with Android OS powering their Fire TV Stick and Fire TV, there really isn't anything they can do to prevent us from sideloading an APK onto the streaming media devices.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

The increased sophistication of smartphones and apps have allowed us the luxury to never leave our homes. Everything from coffee to food to dry cleaning can be delivered straight to your door without ever leaving your couch, which can can be a godsend during the winter months when you'd rather not risk leaving your warm bed. But during the summer, you gotta ditch the comforter and go enjoy outdoors.

Video: . How to Do a No-Knot Invisible Part Crochet Weave.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

The right music can spur you to pick up the pace during an intense workout, pep you up before you hit the treadmill or walking path, and even encourage you to lift for just a few extra reps. Although we all have our favorite workout playlists, scientists have discovered what it is, exactly, that makes you workout harder when certain songs begin.
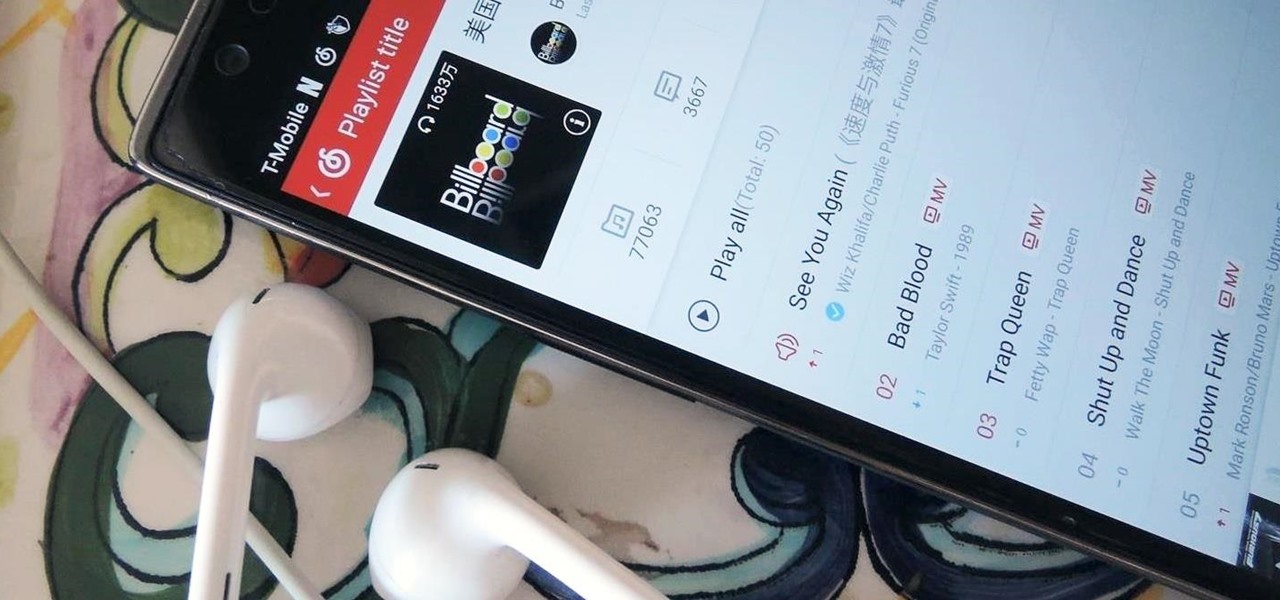
We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my budding hackers!

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Video: . Video: .

Video: . Video: .

How to Reopen a Closed Ear Piercing. This is very Easy and Quick to do.

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

Throughout history, the idea of the future has always promised better days, advanced technology, and of course—hover cars. Although we were correct about the better days (depending on who you ask) and advanced technology, we are still without hover cars, or pretty much any hovercraft vehicles—The Jetsons and Back to the Future were a lie!

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data to third-party advertisers without your consent.

If I could think of one thing the world was missing, it would surely be more tablets. While people struggle between shelling out 200 to 500 dollars for a new iPad, Nexus 7, Kindle Fire, Microsoft Surface, or one of the hundred other tablets on the market, the folks over at DreamWorks have decided to make their own, aptly named the Dreamtab. The Dreamtab will have an 8-inch screen and favor applications with the use of a stylus, for coloring and the like. Total cost is rumored to be under 300 ...

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Cavandoli Macrame (also called Tapestry Knotting) is an intricate form of knotting used to create geometric patterns. The Cavandoli style is done mainly in a single knot, the double half-hitch knot. Reverse half hitches are sometimes used to maintain balance when working left and right halves of a balanced piece.

Samsung introduced a wave of seriously unique and innovative features on the Galaxy S4, including air gestures and weather sensors, but a lot of the features are actually just updated ones from the Galaxy S3. Unfortunately, one of those that returned was the dreaded increasing ringtone. In their increasing ringtone system, the ringtone will start off on a low volume and increase until it reaches your set volume. In theory, this is useful for not shocking the user with a sudden, blaring ringto...

I hate having my picture taken. It's awkward, and I almost always end up thinking, "Is that what I look like all the time?" Most of us think we look awful in photos, probably because we all subconsciously act and carry ourselves a little differently when we know there's a camera on us.

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

You knew that the food you eat gives you energy, but did you know it can actually power a thermal lance with enough heat to burn through steel? A thermal lance, as in, the tool used to demolish buildings and bridges.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

Solving long and extensively complicated equations in grade school was tough to do by hand. Keeping track of which part of the equation to solve first took time, training, and lots of bad grades.

Admit it—at some point or another, you've wished that you had your own personal hovercraft. Don't worry, we've all been there. Well, a company called Aerofex wants to make a hovercraft that's way more than your standard leaf-blower-powered one, taking a queue from the swoop and speeder bikes from the Star Wars franchise, building their own sort of repulsorlift. This hover bike may not be quite as fast as the ones from Star Wars, but if the company has its way, it could be on sale by the end o...

WonderHowTo has seen its fair share of dragon-related projects, from dragon wings, to dragon kites, to less-complicated origami dragons, but we've yet to see anything quite like this. Radio-control plane builder Richard Hamel built this incredible seven-foot-long, fire-breathing dragon using a JetCat P80 turbine and a 50,000 volt stun gun, with a 2.4-gigahertz touchscreen radio controller to fly it.

Stereoblindness is an extremely unfortunate condition where someone cannot perceive depth correctly. Bruce Bridgeman was one such individual, having an eye condition which prevented him from developing functioning binocular vision. In essence, he was living in a "flat" world.