Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

The first augmented reality hardware and software functional requirements guidelines have been released today by UI LABS and the Augmented Reality for Enterprise Alliance (AREA).

Just like in the Spy Kids 3D movie, US soldiers may soon upgrade their mission planning from 2D to 3D. Welcome to the wonderful world of augmented reality, US Army.

Autonomous vehicles, aka self-driving cars, are not yet available to the public (at least not ones SAE Level 3 and higher). However, this doesn't make the jobs any less in demand. In fact, if you meet the right qualifications, you could make a lot of money in this industry.

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.

In an early morning blog post, Microsoft announced the expansion of the Microsoft HoloLens Agency Readiness Partner Program. This announcement comes on the tail of an expanded HoloLens release over the last few months to many countries outside the initial US and Canada.

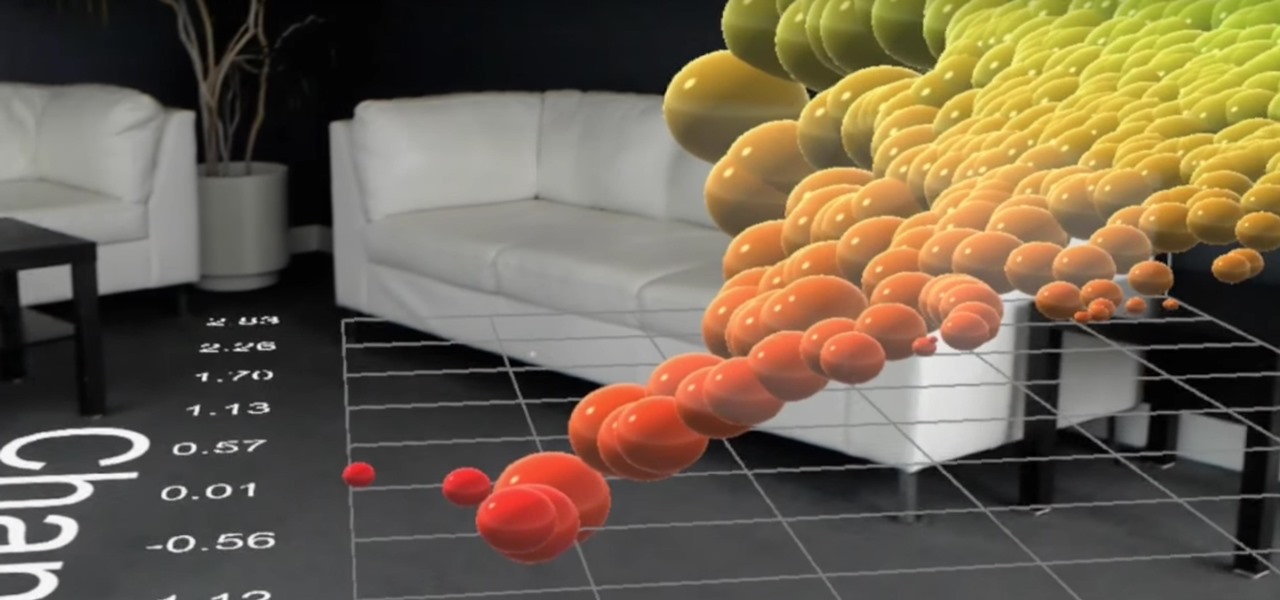
HoloLens developer Michael Peters of In-Vizible has released quite a few videos since receiving his HoloLens last year. Many of his experiments are odd and funny, but some include serious potential approaches to data visualization. In the videos embedded below, you'll specifically see stock market information beautifully rendered in different ways to help understand the data.

Here at NextReality, we talk a lot about the many different ways of controlling holograms in the HoloLens and other augmented and mixed reality devices; New and creative ways are coming more and more every day. Most recently is something called the HoloSuit. In the 25-second clip below, you can see a woman moving the arm of a jacket which in turn moves a 3D model of Darth Vader on the screen. It's a simple idea with big potential.

Dutch police are using a system very similar to Pokémon GO on smartphones, but they aren't walking around trying to catch little pocket monsters. The purpose of this system is to give augmented reality help to first responders who may be less qualified to work a fresh crime scene. If successful, the idea of a contaminated crime scene could be a thing of the past.

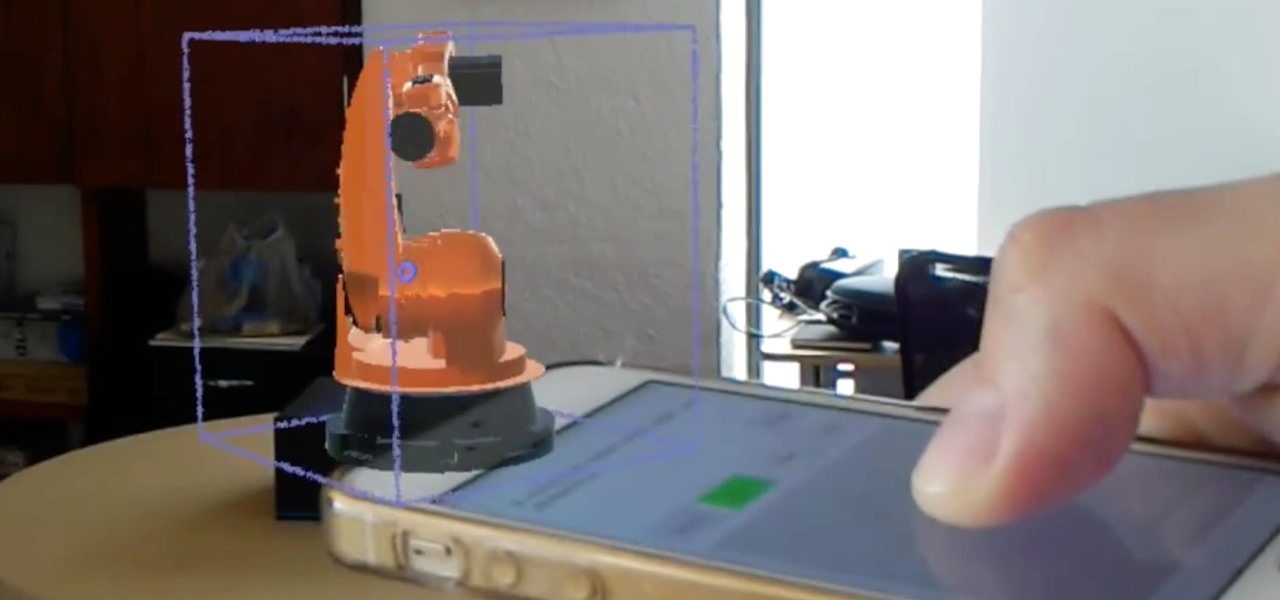
We've highlighted the projects of Wavelength Studios a few times over recent months for their work in the augmented and mixed reality space. Since receiving their HoloLens headsets, they've been hard at work on both development community projects as well as efforts for clients. This brings us to their latest work—a way to control holograms on the HoloLens with our pocket-based modern miracles, also know as smartphones.

Microsoft's HoloLens may the coolest new advancements in technology we've seen in quite some time, and anyone (with deep pockets) can buy one right now. But so far it's been an isolated platform where you experience mixed reality alone and others watch you air tap nothing but air. Developers are working to change that, and we're seeing the first examples crop up online already.

If you've ever built a piece of IKEA furniture, you're familiar with the confusion that some 2D instruction booklets can create. But neuroscience suggests that they're cognitively overloading, as our brains have to translate their basic flatness into physical reality and that's pretty hard to do. Fortunately, augmented reality has come to the rescue.

A 2D film can show you something, but a 3D film in virtual reality can make you feel it. If done right, you'll feel immersed in a new world that surrounds you. If done wrong, you'll get nauseous and uncomfortable. SilVR Thread, a 360-degree VR video company, figured out a few important ways to get the feeling right.

The HTC Vive and Valve's SteamVR make for one of the more compelling virtual reality experiences, mixing in real-world motion tracking with the immersive headset. But third-party manufacturers couldn't tap into the Vive's full potential and make creative new peripherals—until now.

Want to actually catch 'em all? Pokémon GO has long-teased the opportunity to hunt for Pokémon in the real world through augmented reality, but few have had the opportunity to actually see it in action.

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

Juicing fruits and vegetables is very beneficial to your health. For some, it's a trend; but to me, it's a part of my morning routine.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Flashing people in an oversized trench coat is both old-fashioned and exhausting (and also very illegal). But like the evolution from school-yard bullying to cyber-bullying, it seems as if the new trend is "cyber-flashing" (it's even has an official hashtag). In the U.K., police are now investigating what they are calling the first cyber-flashing case.

Even the most unadventurous eaters can usually be coaxed to take a bite of an exotic fruit (except, perhaps, the notoriously stinky durian). After all, fruit is sweet, juicy, and filled with natural sugars.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

If Detective Alonzo Harris from Training Day taught me anything, it's that "It's not what you know, it's what you can prove." So when items mysteriously go missing from my room or my section of the fridge, it's up to me to figure out and prove which roommate took them.

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

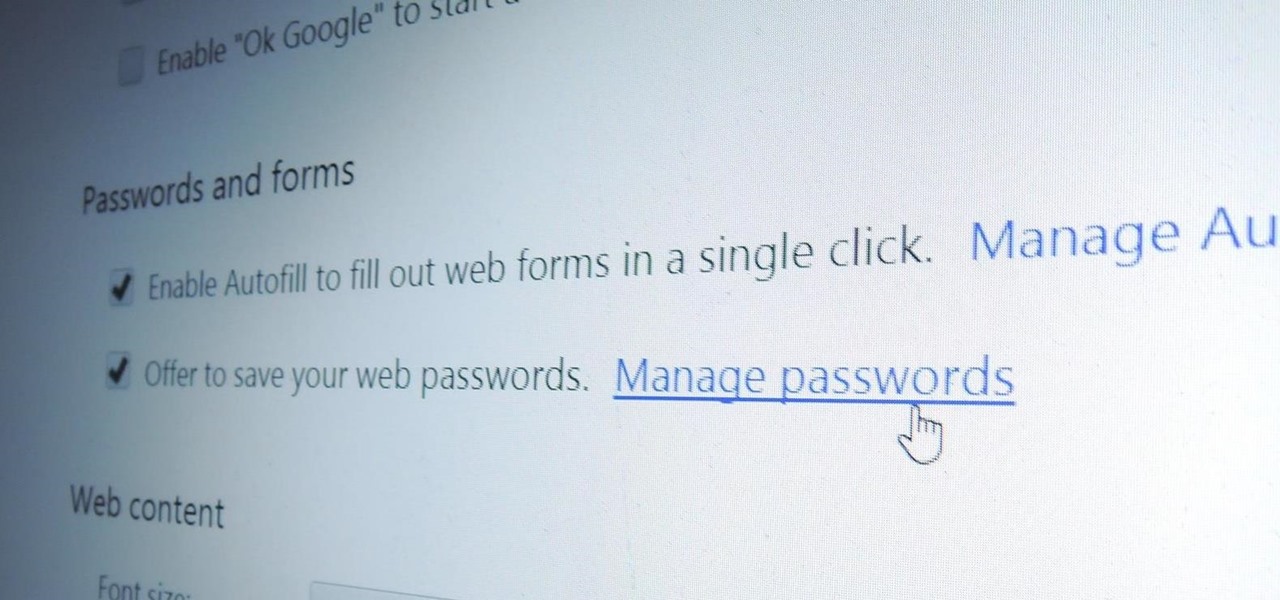
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

We've all been there; waking up in the morning with a stiff, achy back. Maybe you overdid the yard work this weekend. Perhaps you were a bit too enthusiastic on the Nautilus circuit. Could be the long hours spent hunched over your computer are catching up with you. Perhaps your back pain is indicative of something more serious. Unfortunately, unless you've really injured your spine, your doctor isn't going to be much help; the best he can do is offer you pain medications and tell you to rest ...

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

While text messaging has become one of the most frequent ways we communicate with our friends, the missing body language, tone of voice, and eye contact can make it difficult to tell when someone is being dishonest. That said, it's not impossible. There are a number of subtle hints you can train yourself to recognize that will to help you detect written lies hiding in your SMS and iMessages. Here's what you should look out for.

If you're one of the lucky people who received the gift of terrible eyesight from your parents at a young age, chances are you ate an awful lot of carrots growing up. Though carrots are one of the top vision-boosting foods, they don't offer fast results.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Toilet paper isn't the first thing that comes to mind when you want a hot meal, but when you're camping or out in the field (i.e. military training), a little TP is the difference between cold tuna and luxury.

The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve?

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.