The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Apple released the third beta for iOS 11.4 on Tuesday, May 1. This update comes exactly two weeks after the release of the second beta, which, in addition to adding a new wallpaper, fixed issues with AirPlay, Music, and Keychain. The only noticeable change in beta 3 is a fix for unresponsive 3D Touch.

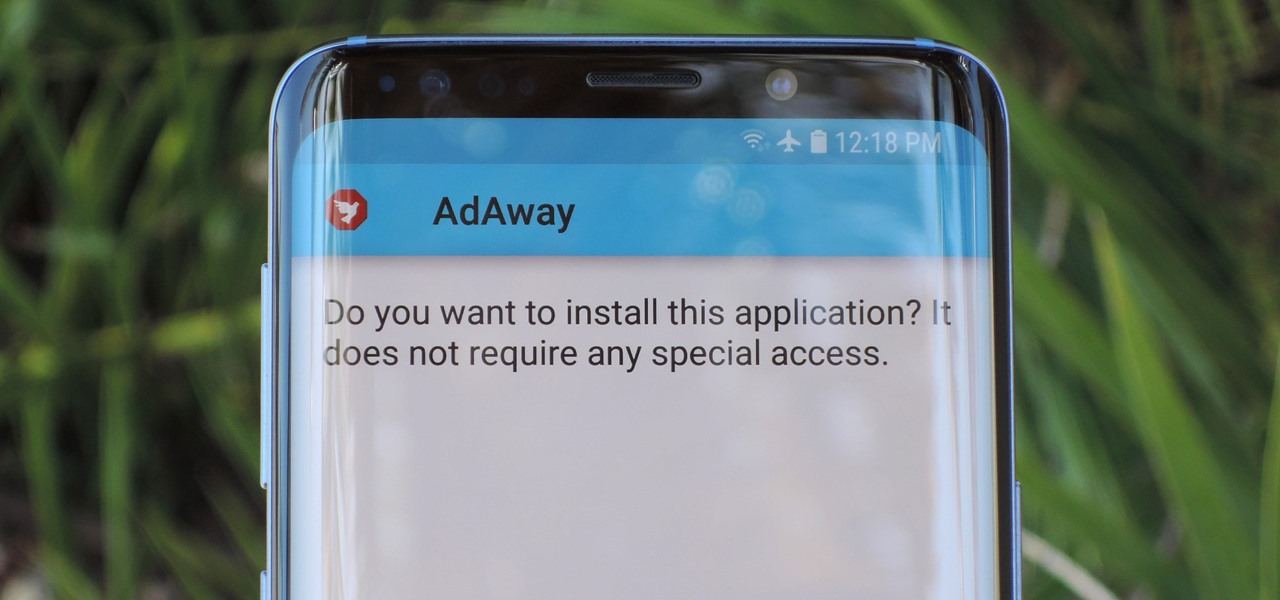
Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.

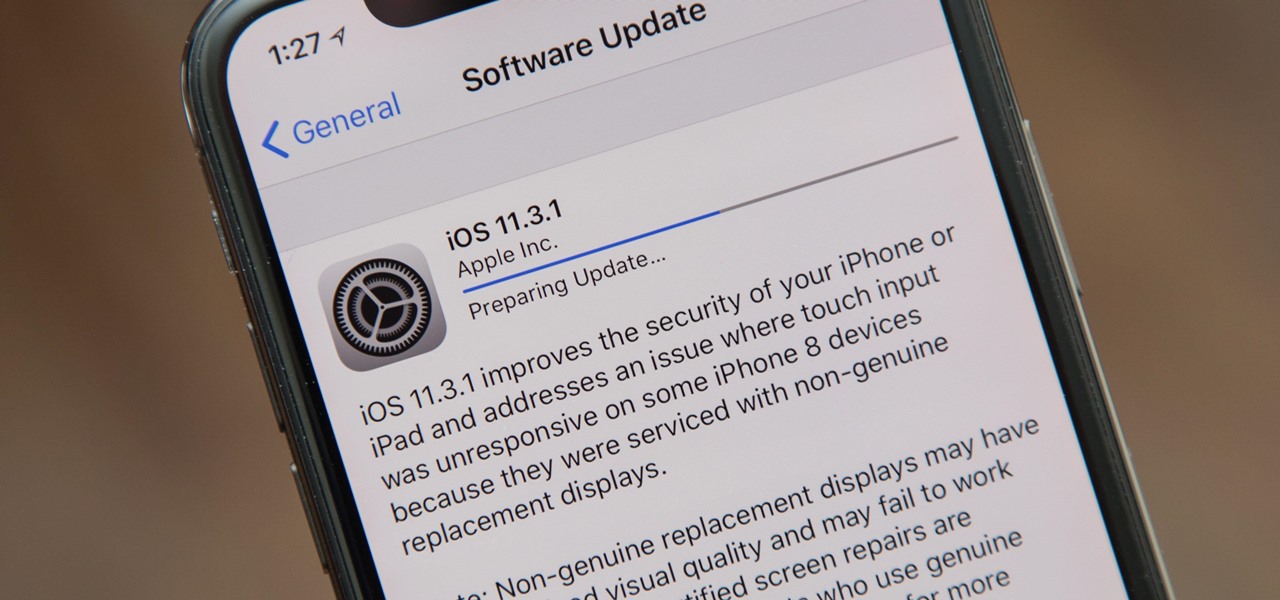
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

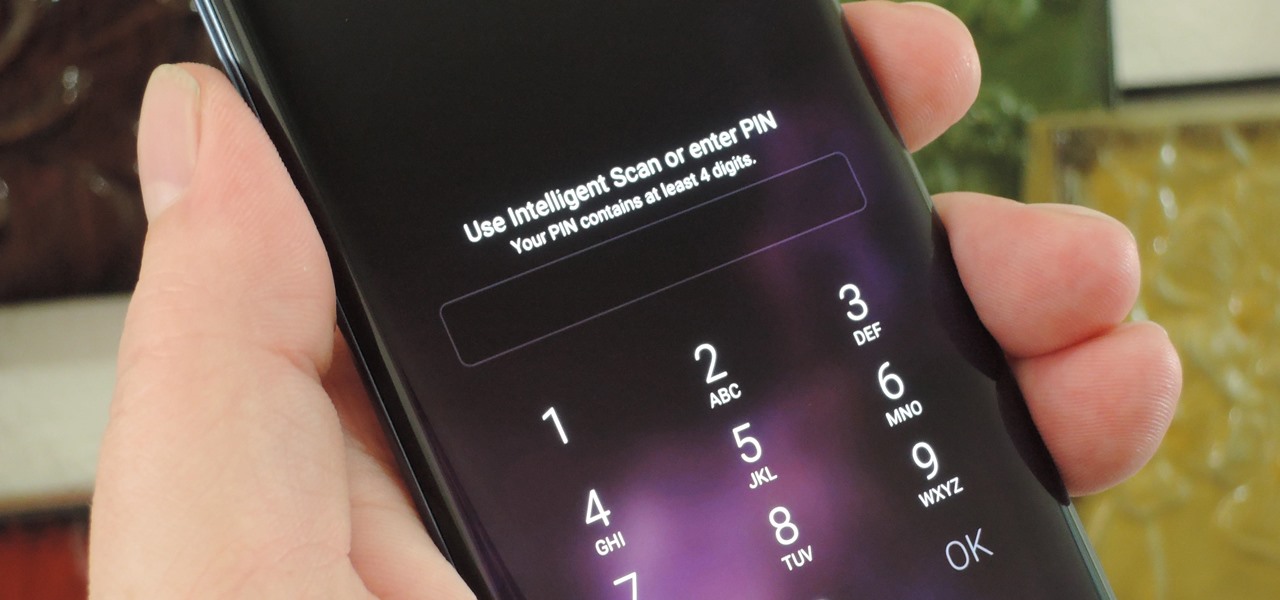
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

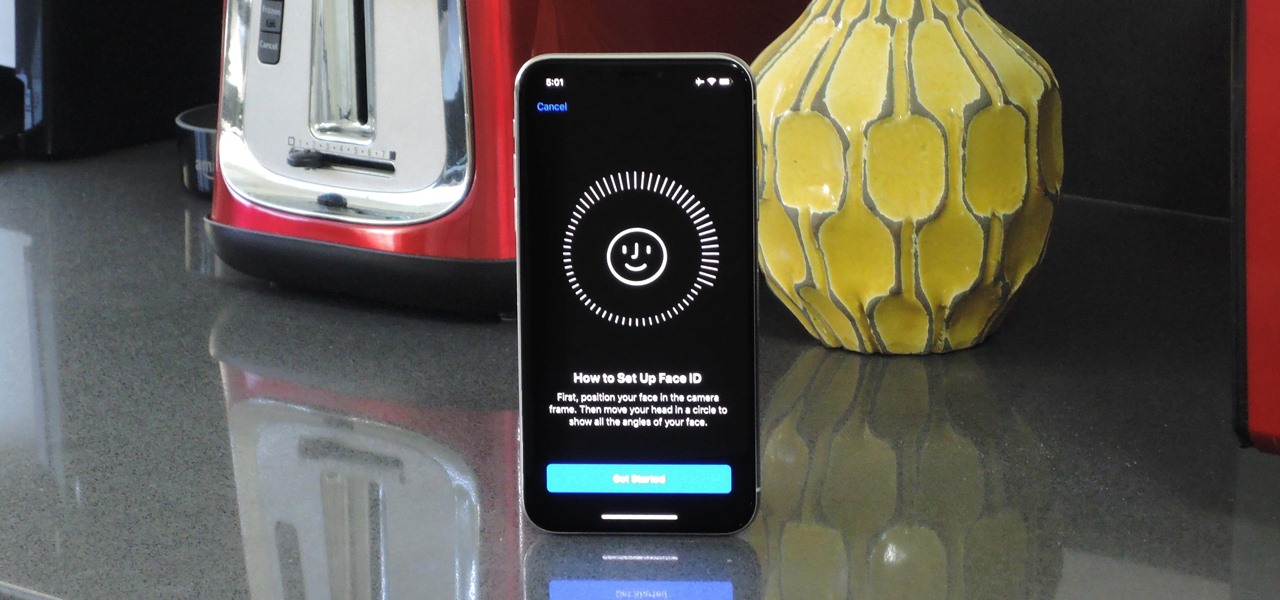
The cutting-edge iPhone X, XS, XS Max, and XR have one-upped their Android competitors when it comes to facial recognition. Apple packed these flagships with an array of front-facing sensors to complement its selfie camera, which allows the new device to more accurately analyze faces, which you need for Face ID, Touch ID's replacement.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

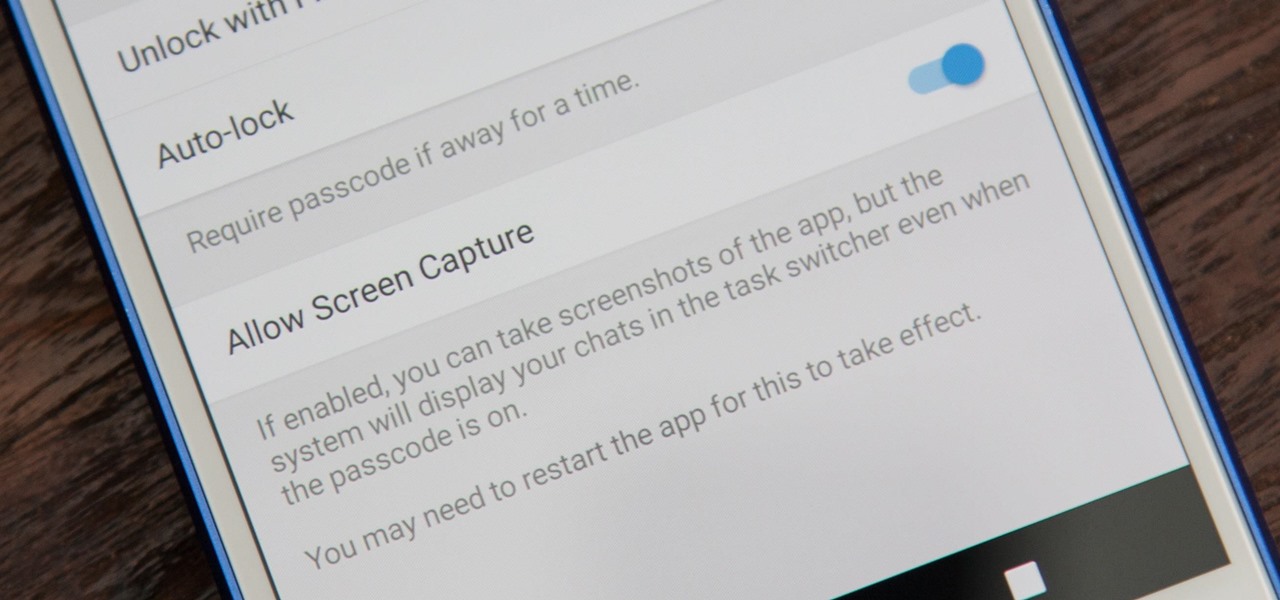
While it's easy enough to take a screenshot of an end-to-end encrypted Telegram chat thread using an iPhone, it's an entirely different story on Android phones. Telegram disables screenshots for Secret Chats by default on Android, and not everyone can turn it on.

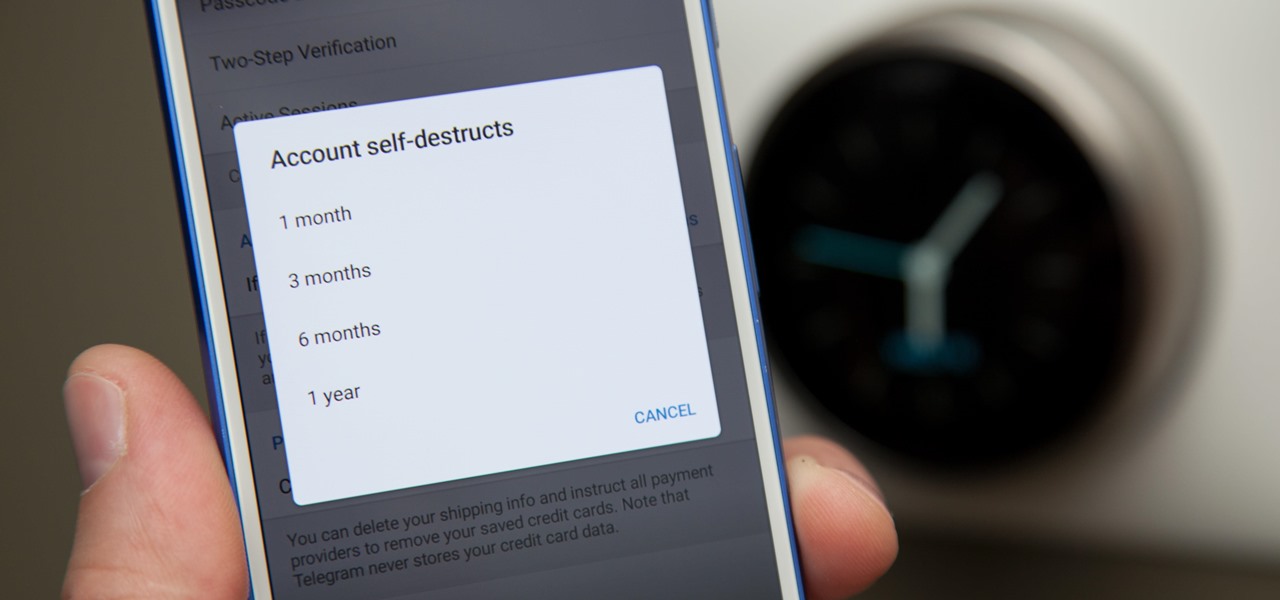
You can send self-destructing messages in Secret Chats, but that's not the only thing that can destroy itself in Telegram after a specified amount of time. Your whole account can disappear after a certain amount of inactivity, so it's important to adjust these settings to give you more time or to kill your account even quicker.

While using end-to-end encryption may be enough security for most of your messages in Telegram, you can go a step beyond this by sending messages that disappear after an allotted amount of time. This prevents you from having to manually delete the message at a later time, so you can send it and forget it without worrying about whether or not it's still out there.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

Google has done it again—they've pushed another broken OTA update for the Nexus 6. Except this time, it almost completely softbricks your Nexus 6 instead of just screwing up Android Pay and SafetyNet. Apps are force-stopping left and right, making the phone practically unusable.

Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already has over 6 million views on YouTube, covered the journey made by a stolen smartphone and how the theft and ensuing tracking affected all parties involved.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

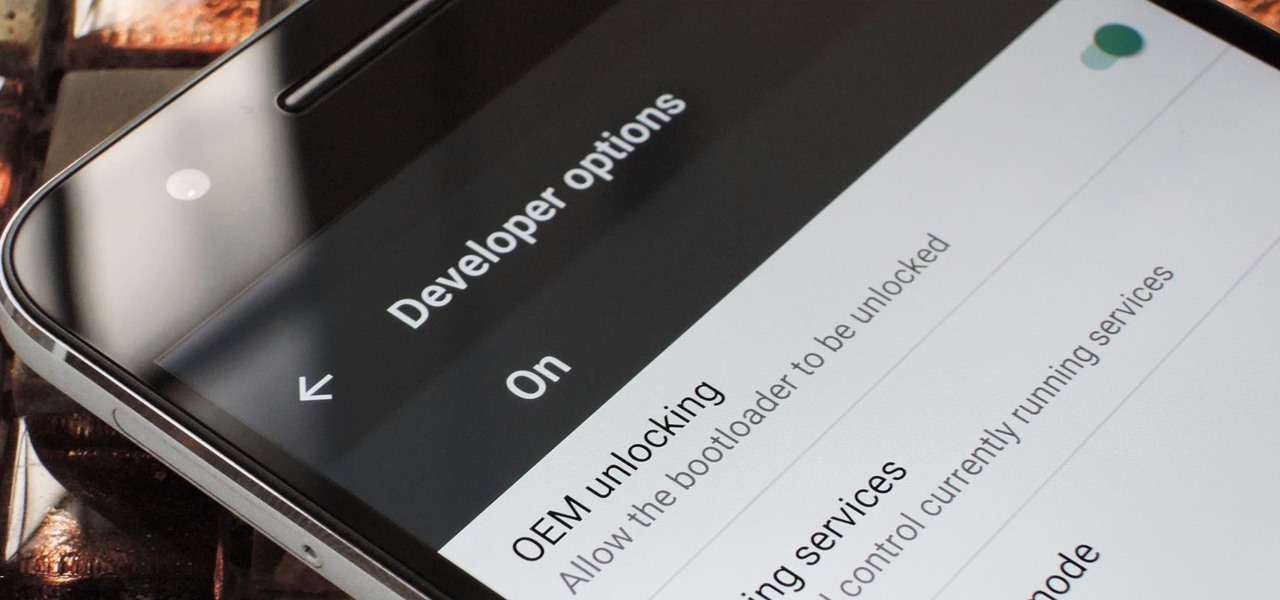
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

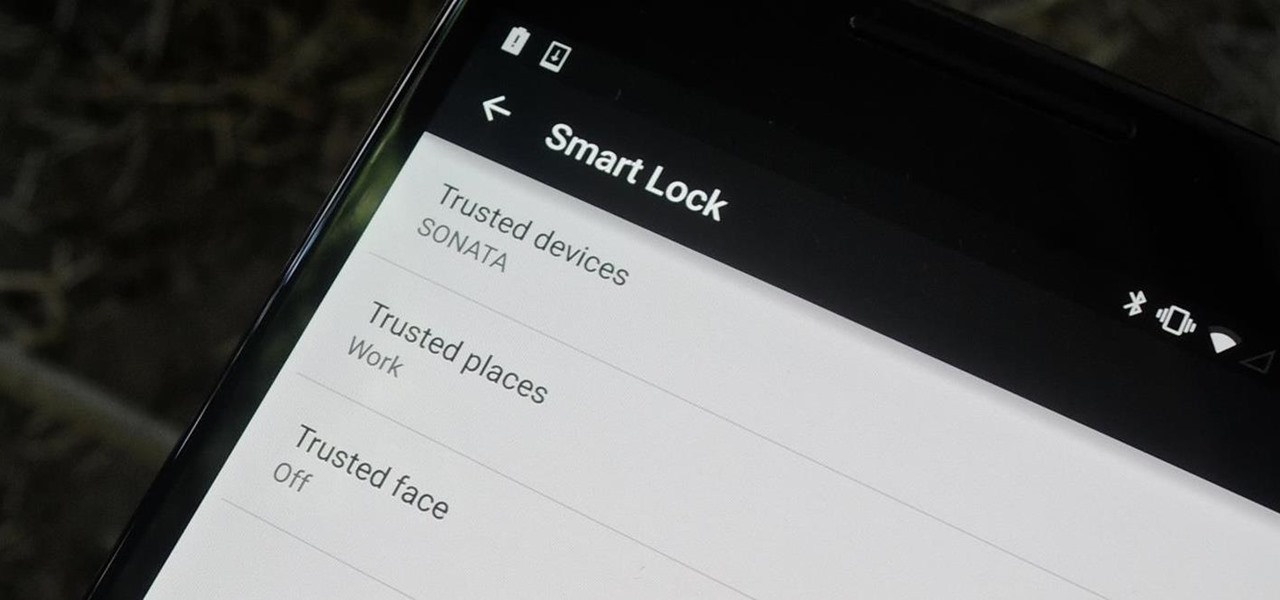
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).