Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

Reports of Samsung's Galaxy Note 8 having an in-display fingerprint scanner have been circulating for the past few days. Fans have been excitedly discussing the potential of the phablet possessing this technology, as it would be the first phone released with these capabilities. Unfortunately, a Samsung official revealed today to Naver — a South-Korean web portal — that Samsung has decided to forgo incorporating the feature into the Galaxy Note 8 due to technical limitations and time constraints.

With the US Department of Homeland Security (DHS) banning laptops and tablets on flights originating from 10 international airports, and the United Kingdom taking similar precautions, international travelers are faced with hours of non-productive — or far less entertaining — flight time.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

Sad news for fans of Google's fantastic Pixel line. Google confirmed today that the Pixel and Pixel XL won't be getting any software or security updates past October 2019. What does that mean for you? Well, your Pixel might start acting a little ... weird soon. Should we run to Georgia and join the ricktatorship before that happens? Get the Pixel 2 when it's ready for launch? Or maybe ... we wait things out and grab the next Pixel after that?

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

If you like having Siri available to answer a quick question every now and again but don't want everyone who picks up your iPhone to also have access to your personal assistant, there's an easy way to disable her from working on your iPhone's lock screen. This is also something you can do if you're always activating Siri accidentally in your pocket.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

To use Apple Pay in iOS 8, you had hold your iPhone to the card reader first, and then you could either switch to a different card or pay with your default one. Now, in iOS 9, you can access your Wallet (which replaces Passbook) on the lock screen before you get to the reader.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Mac keyboards are great when listening to music or watching a movie, since you can control what's playing without going back into iTunes or QuickTime Player. However, when you're using an app like Photoshop that uses the F7, F8, and F9 as shortcuts, it gets pretty annoying to have to hold down the Fn key. Why can't you just hit the back, play/pause, and skip buttons alone?

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

Whether you use a third-party keyboard or the stock offering, your Samsung device keeps a history of the last 20 words you copied on its clipboard. Samsung added this feature to Android to help make multitasking a bit easier, but if you use a password manager like LastPass, this feature quickly becomes a gaping hole in security. While you're copying and pasting your various passwords, the last 20 of them become freely available to anyone that gets their hands on your device.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

Automator takes the work out of common repetitive tasks in Mac OS X. One of my least favorites is resizing images for the web, so I created a drag and drop action to quickly do it for me.

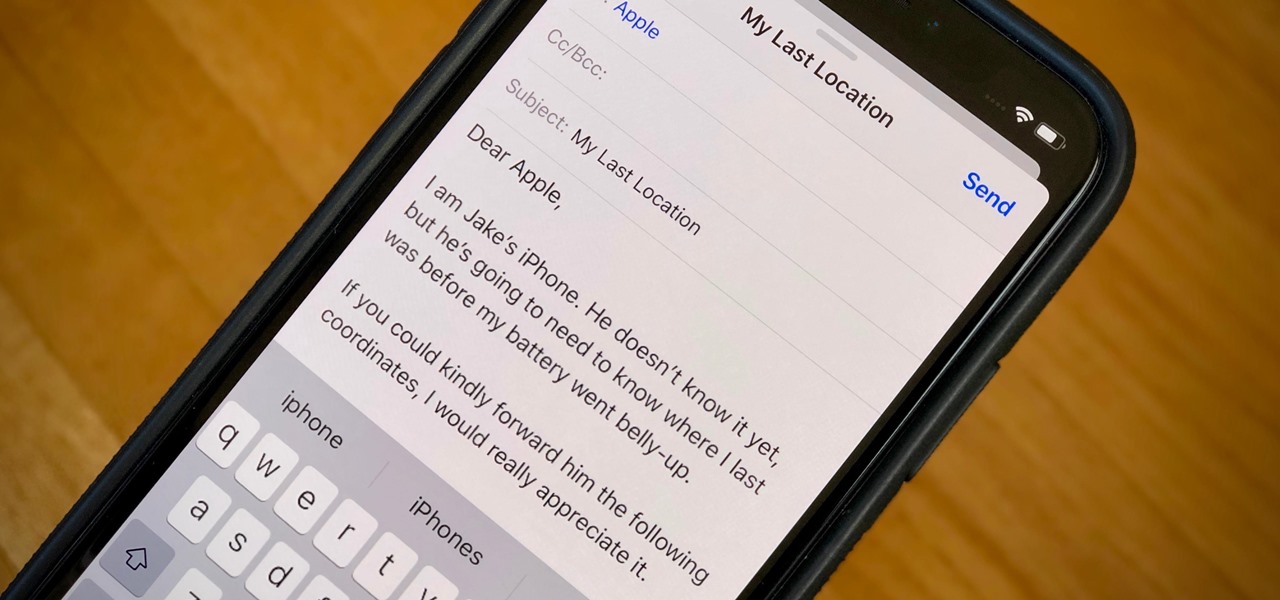
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

Keeping prying eyes off your device isn't always the easiest thing to do, especially once you lend somebody your phone to make a call. Seems that whenever someone is scrolling through your pictures or checking out your new phone, they always end up somewhere you don't want them be. You could always hover over their shoulder to make sure they're not getting into your texts or photos, but that isn't always possible.

There are countless lock screens you can apply to your Android device, but very few offer more than just quick access to apps or advanced security functionality. Since you probably unlock your device a gazillion times every day, why not use this to your advantage and let it teach you something new?

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

Some of my favorites hacks are the ones that speed up the process of accessing my favorite and most-used apps. So, in this softModder guide, I'll be showing you a super fast way to open those apps straight from your Samsung Galaxy Note 3's lock screen.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

If somebody really wants to gain access to your iPhone, they'll get in. Phone thieves (and mischievous friends) can easily figure out your passcode just from looking over your shoulder or tracing over the oily smudges on the screen. And if you're using popular passcodes, birthdays, and addresses on your iPhone, you might as well disable lock screen security entirely.

The lockout feature in iOS 7, which securely locks your device after a few incorrect passcode entries, can be a real pain in the ass sometimes.

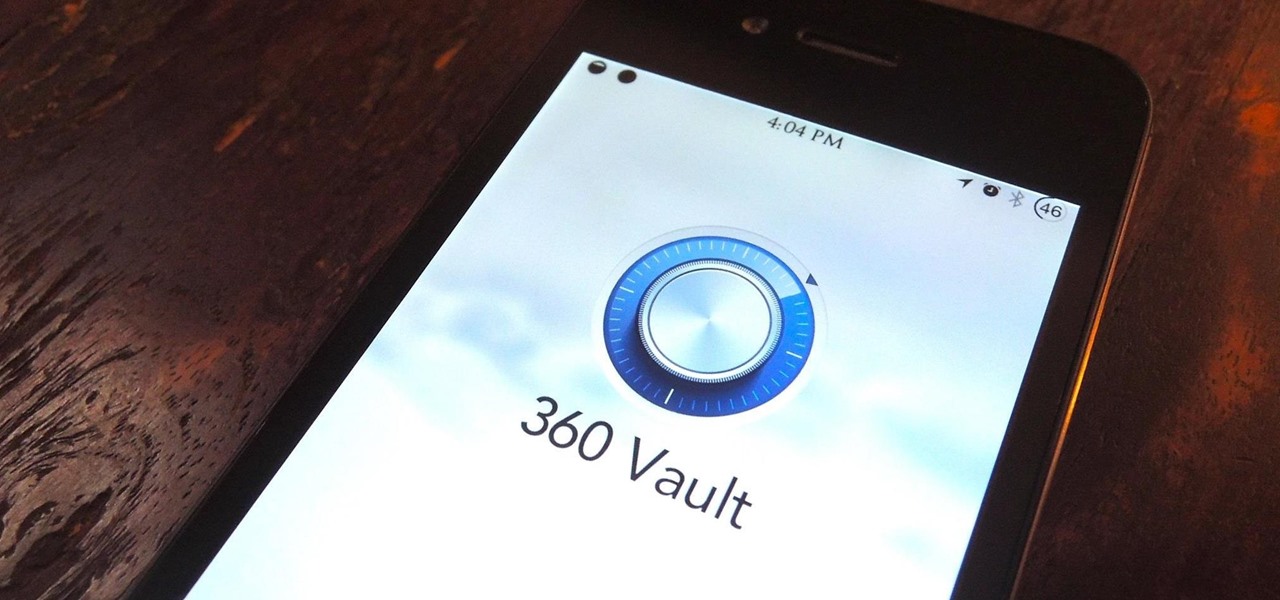
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

#FOMO. If it bugs the living hell out of you that you don't know what that means, you're presently FOMO, as in you've got a Fear of Missing Out.

Samsung just concluded their live unveiling of the Samsung Galaxy S4! A more in-depth look can be found here.

Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four days after its release. Well, now it seems that iOS 6.1 is being taken advantage of again, this time with a simple exploit figured out by YouTube user S1riOS6, which lets you bypass the lock screen on an iPhone running iO...

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

UPDATE: A patch to fix the exploit has been released. Download it here.