Every day it seems like new information comes to light about how the National Security Agency creeps into our lives. Knowing that they can backdoor into our seemingly private devices is a scary thought, whether you have information to hide or not.

Snapchat is like that very attractive girl at the bar that has one too many shots and ends up slobbering on the bouncer as she gets led out. Of course she can still recover since she is hot, but you only get so many chances before you just become a complete failure. And that's where Snapchat has been treading these past few weeks.

The internet was ablaze this week after it was found out that evasi0n's newest jailbreak for iOS 7 secretly came bundled with a highly obfuscated Chinese app store. The application, called Taig, was filled with pirated software and was rumored to have permissions capable of tracking your information and sending it elsewhere. It was reported that the team at evad3rs financially benefited from this move, netting them a very high six-figure number close to a million dollars. The controversy incr...
Android's deeply customizable platform has long been the attraction for those of us looking to make our smartphones more unique, but that doesn't mean that it's always easy. Flashing mods and installing custom ROMs can be difficult at times, as well as dangerous.
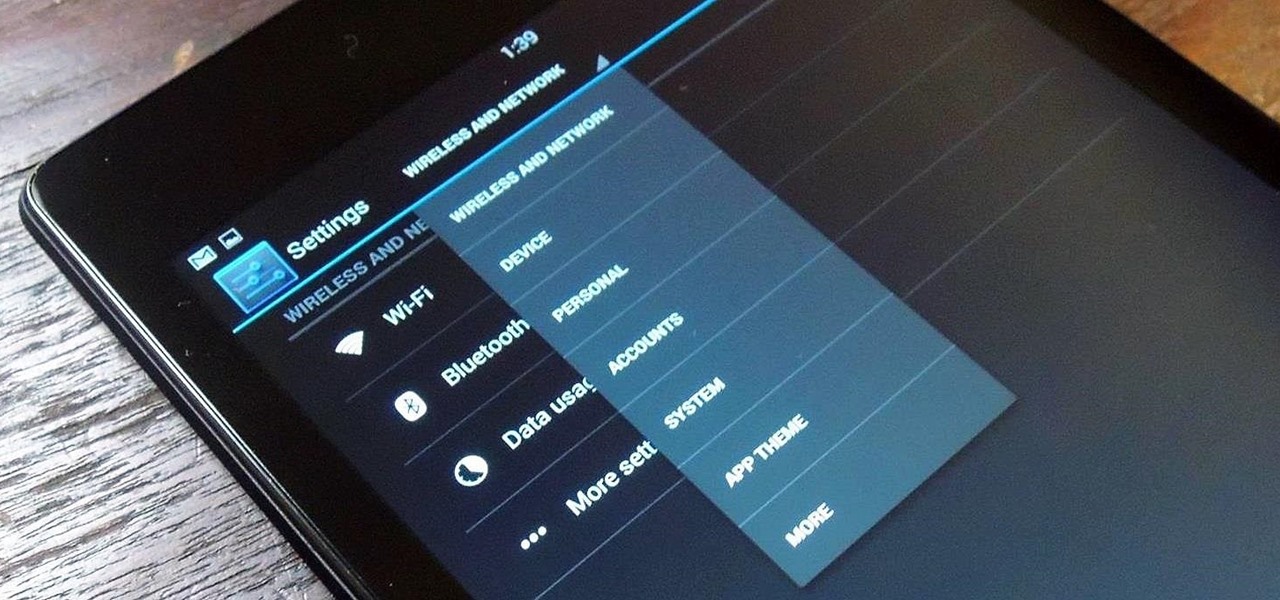
It seems like most of the really cool and interesting modifications you can make to your Android device always require special root access, so when a fun mod comes along that doesn't require root—I feel it's my duty to alert you.
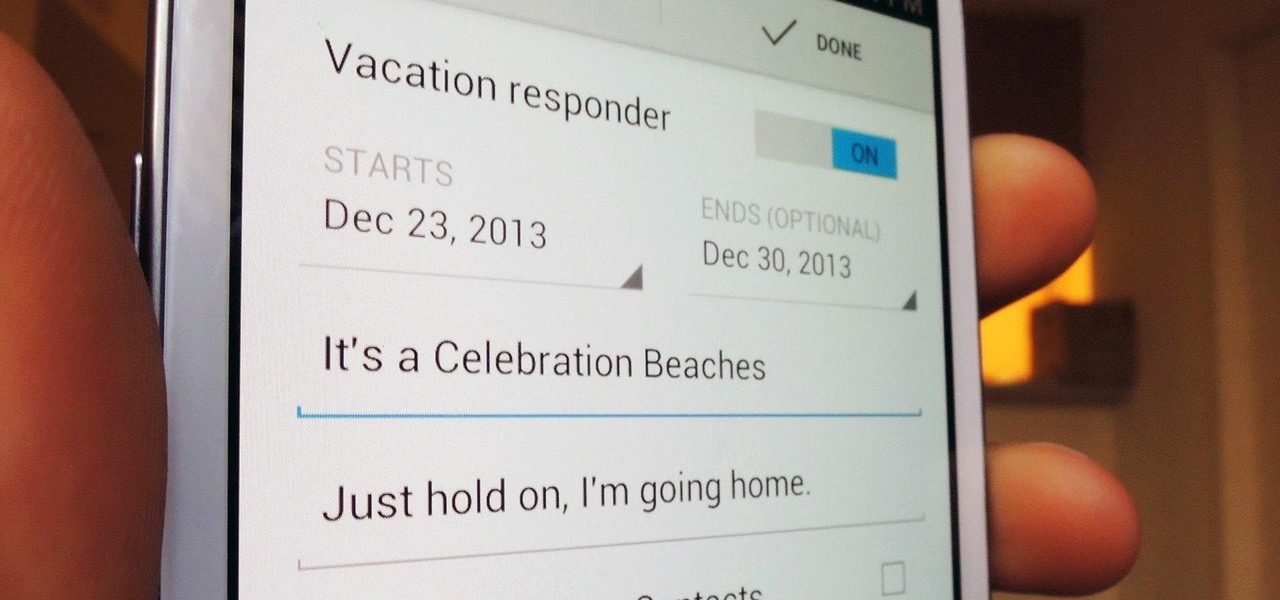
The holiday season brings together three of my favorite things—presents, time off, and drinking. And in order to enjoy all of these things in peace, you have to make sure to put your work behind you.

While the Play Store has a plethora of apps available for finding lost Android phones, Google came out with its own web-based application, Google Device Manager, earlier this year to help you keep track of all your Android devices and remote lock, erase, ring, and track if need be.

If you didn't already know, Apple is giving away their newest operating system, Mavericks, for most of your computers. While the folks over at Microsoft surely despise this tactic, those of use Mac users still running Snow Leopard surely do appreciate it.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

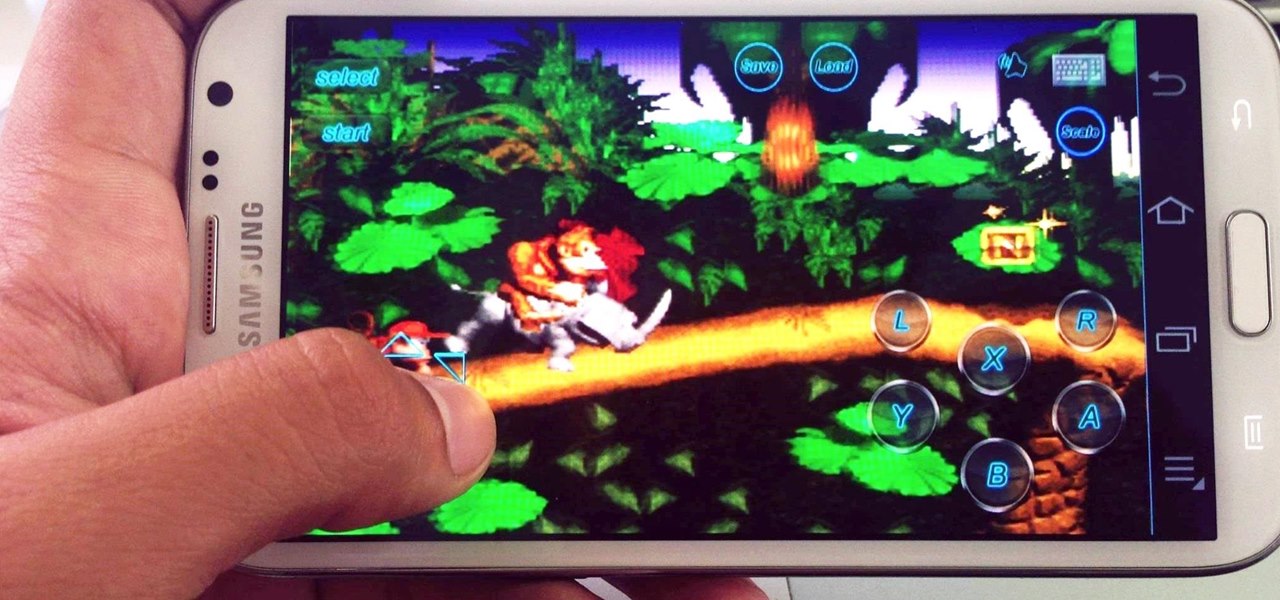
I grew up on SNES. Super Mario, Final Fight, and Contra were just a few of my favorites, and most of my collection is still intact—all I have to do is reach under my bed and pull out all my old games. As proof, I present my original Donkey Kong Country cartridge: Now that I'm older, I don't have as much time to play my SNES as I used to. Hell, I barely have time to play my Xbox. Most of the games I play these days are on my Note 2, but no mobile game can compare to those classics collecting d...

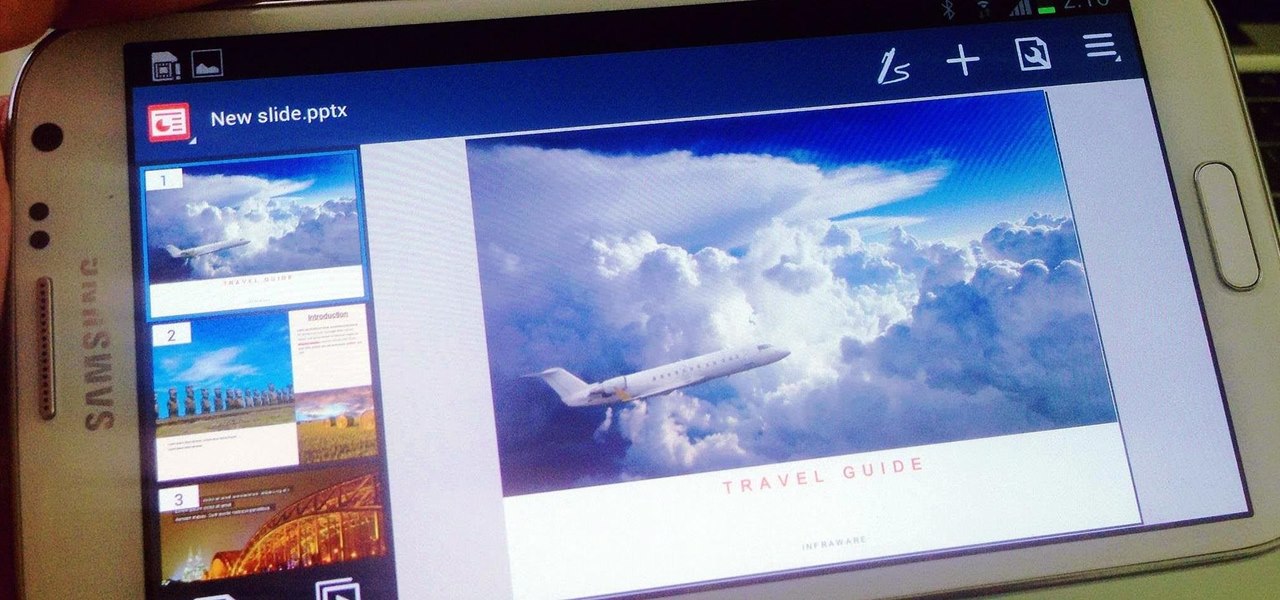
There are a lot of apps in Google Play for your Samsung Galaxy Note 2 that let you create, edit, and view Microsoft Office files on the go, but none match up to the power of an app called Polaris Office for Samsung Galaxy devices.

According to Nielsen, the average American spends about 34 hours per week watching television. That may sound like a lot, but when you factor in multi-screen viewing, it could be even higher—81 percent of Americans use their smartphones or another device while watching TV. It's the new picture-in-picture.

In this Windows 8 Tutorial you will learn how to disable automatic maintenance. Their are really two situations I can think of when you would want to disable automatic maintenance in Windows 8. The first being if your Windows 8 computer came with a Solid State Disk then you will probably want to disable automatic maintenance. The reason being is that a solid state disk does no benefit from defrags and the automatic maintenance automatically defrags your hard drive and this will take away from...

With the release of the Samsung Galaxy S4 right around the corner, us Galaxy S3 users also have reason for excitement. We already know that many of the S4 features will make their way to our devices, but who knew it would be this soon!

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

Want to secure your home? There are plenty of ways to go about it. You can make your doorbell send you a text if someone rings it while you're not home, or build a motion-triggered security camera. Even better, you can beat potential crooks at their own game by installing a door they can't even find.

While the Google Play Store is filled with big name magazines like Time, Forbes, Sports Illustrated and Maxim, it also panders to smaller audiences, like with Coin Prices, Soap Opera Digest, Watch Journal and Quilter's World (which yes, is all about quilting). If you have a select few that you enjoy reading, prices aren't usually a problem; issues range from $1.99 to $4.99 for each one, or from $19.99 to $39.99 for yearly subscriptions. If you're someone that is a magazine connoisseur, prices...

I use Google Chrome every day for my browsing needs, and I had no idea they were hiding something from me. So, I was pretty surprised to see that Chrome has an entire hidden experimental add-ons section. There are add-ons that work for Mac, Windows, Linux, and Chrome OS, so there's something for everybody.

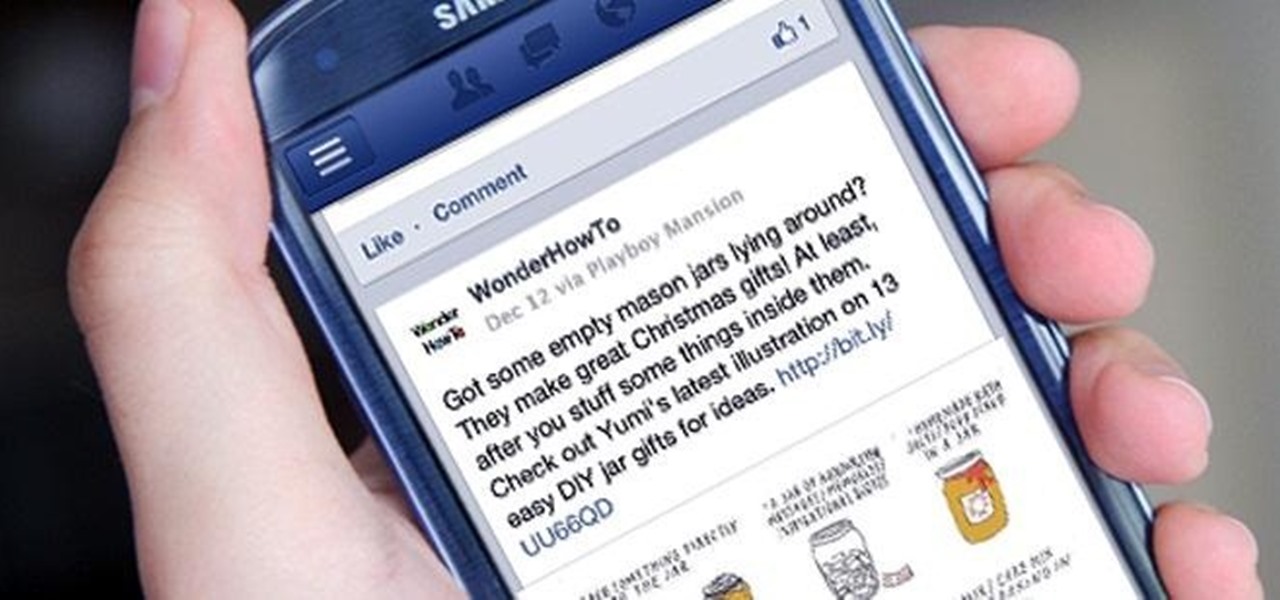
Depending on what mobile device you own, you'll see something that says "via device name" next to the date of your post on Facebook. If you're device is not recognized, you'll simply see a "via Mobile" note, which is what happens when I post from my phone. If you allowed your iPhone to be called iPhone when you logged into the app, it'll show up as a recognized device on Facebook, and will post "via iPhone." Same thing goes if you have a Samsung Galaxy S3 or Nexus 7 or iPad. It could also jus...

With all of the advancements in the smartphone world, we can virtually use them for anything. You can use your smartphone as a mobile hotspot, an Xbox controller, a car locator, and a security camera. Heck, you can even turn it into a Swiss Army knife. And now you can even use it as a wireless mouse for your computer!

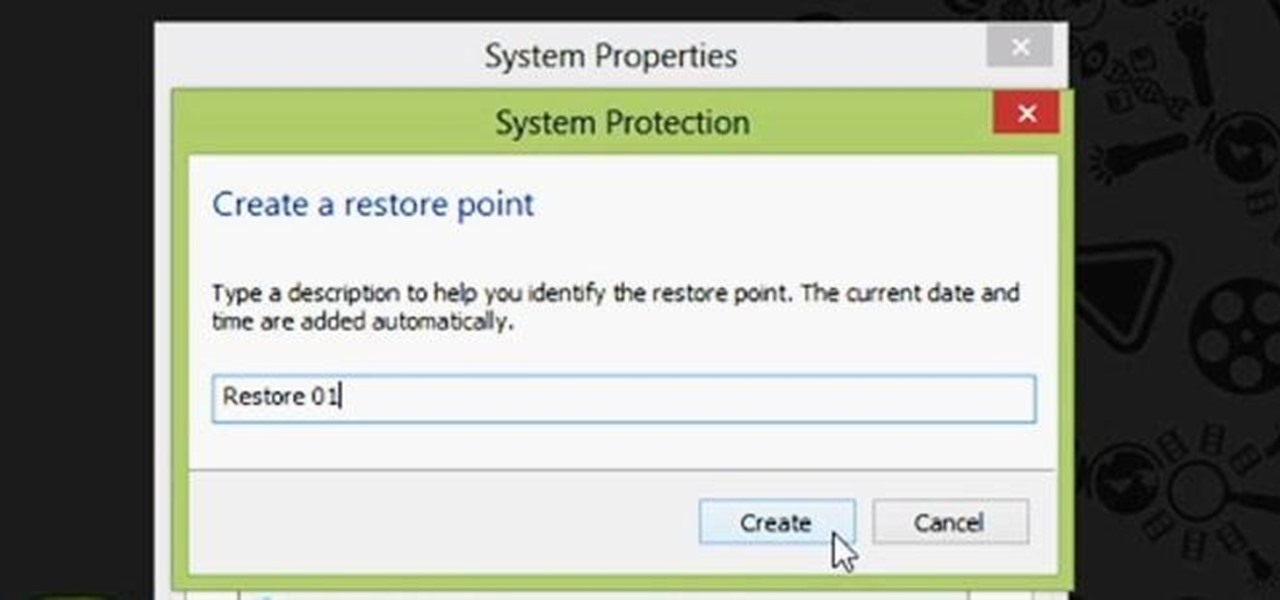
Restoring your computer to a previous point is an extremely important thing if something goes wrong. I've restored my computer at least a dozen times after downloading some suspicious software or running into an error I couldn't remedy on my own.

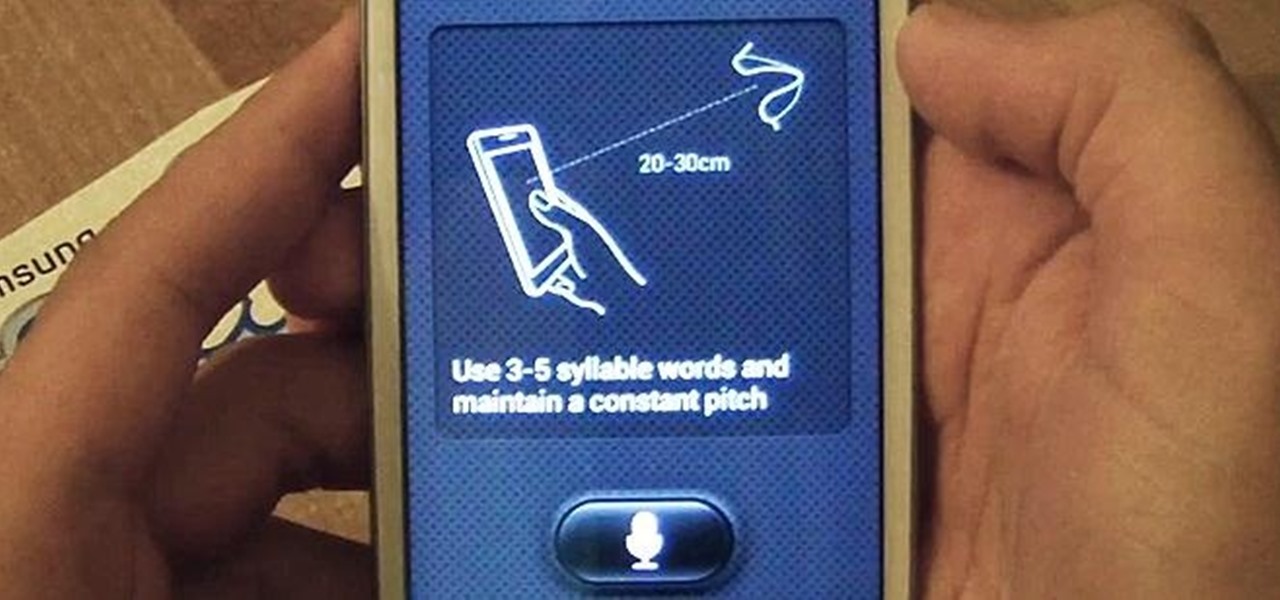
With voice commands becoming conventional on most new smartphones, it's only ideal that their abilities increase as well. Thanks to Apple's Siri, you can do things like update your Twitter account and look up who the president of Costa Rica is.

By default, your Samsung Galaxy S III comes equipped with a few app shortcuts that are available from the lock screen. But what if you don't use those apps very much? Wouldn't you rather customize the lock screen icons on your S3 to your favorite and most used apps?

Samsung's Galaxy Note and Note II phablets have been hailed for their large displays and responsive systems, making them ideal for gaming and movie watching. But if you've recently upgraded to Jelly Bean (Android 4.1) from Ice Cream Sandwich (4.0), you'll be sad to know that some Android devices running Jelly Bean no longer support Adobe Flash Player.

A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

If you bought the new iPhone 5 or upgraded your old one to iOS 6, you may be having issues when you try to upload photos to Facebook. After updating, the first time you try to share an image from the Facebook app, it will ask you to allow access to your Camera Roll.

Want to know when you have a visitor, even if you're not home? You could always set up a security system and live-stream it with your iPhone. But if you don't have a spare iPhone, or just don't want to go to the trouble, this simple hack will add text message alerts to your doorbell so that it lets you know when someone's there.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

In 1958, Patrick Flanagan invented the Neurophone, a device patented in 1962 that allows radio signals to be picked up by the human nervous system. The skin is the organ that receives the signal, converting it into a modulated molecular vibration, which the brain interprets into sound. Basically, it gives one the ability to 'hear' through the skin, making it sound like the audio you're hearing is actually in your head. It's kind of like having headphones in your brain. The only problem was th...

Want an electric car without the price tag? You could always build your own, or maybe just hack your old gas guzzler into an eco-friendly electric machine... This weekend at Defcon, security consultant David Brown showed off his "Voltswagon" project, a 1974 Beetle named Shocky that he converted to electric for only $6,000. He removed the old combustion engine, radiator, and a few other unneeded parts to make it lighter. Then he loaded it with batteries front and back, ten Interstate DC-29, 12...

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Knit blankets are comfortable and scream home and security, but they are expensive and making them is an arduous task. If you want to get started on a major knitting project, watch this video, and learn in general terms how to knit a blanket.

Take a look at this video and learn how to hack into a wireless Linksys router. This hack isn't applicable for all security enabled networks, only ones that use generic passwords.

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

The Thule Snug Tite hitch lock is for carrier to receiver security. This video shows you how it assembles first, then how the lock is applied to a bicycle rack.

This video demonstrates how to install or replace a dead bolt in your door. Having a dead bolt lock gives you a added sense of security, because it is more secure than just the lock on the door handle.

There's a lot of fighting to endure in the Xbox 360 game Bayonetta. In Chapter 1 - The Angel's Metropolis, it's your first real battle. Central Station Platform - Go to the far side of the platform and go through the security gates. The door on the far side of this hall is locked, but on one wall in the hallway you'll see a strange sphere. Walk up to it and start doing combos to open a door.