Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Tired of your Samsung Galaxy S3 being a square? Make it more well-rounded by ditching those 90-degree corners on your screen for new adjustable round corners instead. It may be a minor tweak to your device, but the psychological effects of a more circular screen may help you feel more connected, safe, and, well…perfect. If you're the type that prefers the logic, order, and security of a sharp-cornered screen, then stick with your standard Android interface. Otherwise, keeping reading.
Facebook Home was just released in the Google Play Store a couple days ago, and for those of you eagerly waiting to get it on your Nexus 7, you'll unfortunately be stuck with this message: The new Facebook Home launcher app is blocked on the Nexus 7, because Facebook only released it for a few select Android phones. Home for tablets probably won't appear for months, but that's okay, because you don't have to wait that long! In this article, I'm going to show you how to get Facebook Home insta...

You've probably see this a million times on your Nexus 7 tablet: On some streaming sites it's "You need to upgrade your Adobe Flash Player to watch this video," and on others it may be "You need to install the Adobe Flash plugin." Whatever it is, you have the same problem—Flash does not work on your Nexus 7.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

If you have an iPhone, you probably already updated to iOS 6.1, which was released earlier this week. The new release came with some very subtle updates, including LTE support for more carriers, the ability to purchase movie tickets from Fandango via Siri, some security patches, and more.

The allure of Snapchat is that all pictures and videos sent through the app vanish a few seconds after being sent. They're completely obliterated not only from the phone, but from the Snapchat server, as well. The popularity of the application has even incited Facebook to release its own real-time picture and video messaging application, aptly titled Poke. One of the biggest criticisms (besides the wave of recent security issues) of Snapchat is that even though the messages self destruct and ...

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

Keeping your operating system up to date is essential to keeping it bug-free and running properly. Windows regularly pushes out patches and security fixes through Windows Update, so making sure to turn on Automatic Updates or checking at least once a week is strongly advised.

Free stuff is pretty cool. Free internet is even cooler—and free internet that is actually free is the coolest. If you would rather avoid sitting in a Starbucks and having to listen to hipsters discuss the proper length of cropped jeans, then this should be of interest.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

If you're tired of your roommate stealing your Cheetos out of the pantry or simply want to indulge in something creepy, then keep reading. With the iPhone 5 finally released, many people will soon be selling or giving away their older iPhones. But should they? Instead of ditching your old iPhone, why not use it to engage in some Big Brother type espionage? There are some really awesome ways to use your old iPhone, but spying on people is definitely the most bang for your buck. First, you'll w...

Think your roommate's been using your computer while you're not around, but don't have any proof? Worried your little brother or significant other is snooping through your stuff? Here's how to check on both Windows and Mac OS X so you can catch and confront anyone who's logging onto your computer without your permission.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

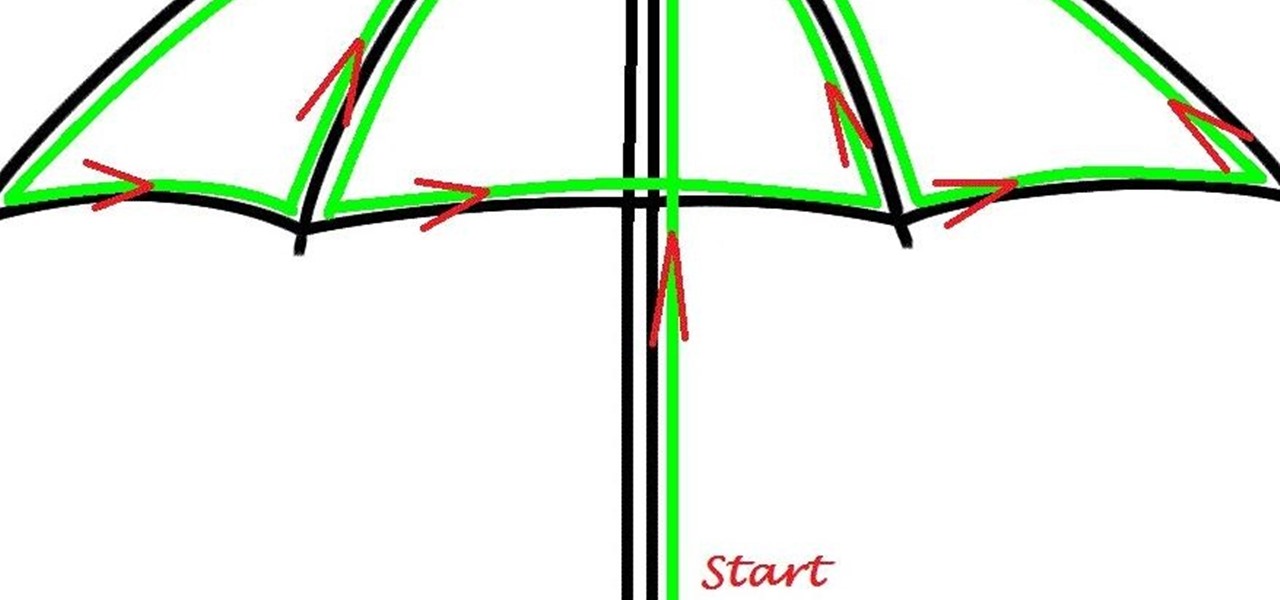
Here's a children's umbrella lined with neon green EL wire. It's definitely an easy and fun project for kids to do with their parents, and more importantly, it keeps the little mischiefs safer if they're out and about on rainy days.

Doorbells are a great idea. They let you know when someone who's not a burglar is trying to enter your house, apartment, or squat. They eliminate the need for lots of noisy yelling and startling door pounding.

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

In this video tutorial, viewers learn how to completely format a hard drive. Begin by downloading the Knoppix Live Boot CD. Then burn the newly download ISO onto a CD as a bootable disc. Use your BIOS to tell your computer to boot from the CD-ROM instead of the hard drive. With the Knoppix CD still in your CD drive, restart your computer to load up Knoppix. Once loaded, use Knoppix to run the “dd” command and reformat your hard drive. This video will benefit those viewers who want to learn ho...

There are few things more relaxing than a hot shower after a long hard day of toil, and there are few times when people are so vulnerable or oblivious to the possibility of a little practical joke. A splash of almost freezing water will feel even colder within the warm security of a good shower. Watch this video pranking tutorial and learn how to ruin someone's hot shower with a hit of ice water. Use this as inspiration for one of your April Fools Day pranks!

Access your computer's BIOS settings

This video will show you how to disable secure virtual memory in Mac OS X. From the top left of your screen click on the apple icon. Click on system preferences from the pull down menu. Click on the security icon. Click on the image of the closed lock from the bottom left of the window so that you can change make changes.

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.

You're probably sharing a ton of information on your iPhone with other people, apps, and services without really realizing it. Now there's a new tool to show you just how much, and it can be an eye-opener as well as a fast way to manage sharing permissions and review your account security.

The newest feature for Pixel smartphones puts a home theater in your pocket. Spatial Audio outputs sound that appears to come from in front of and behind you, adding a new level of immersion to your streaming video and music apps.

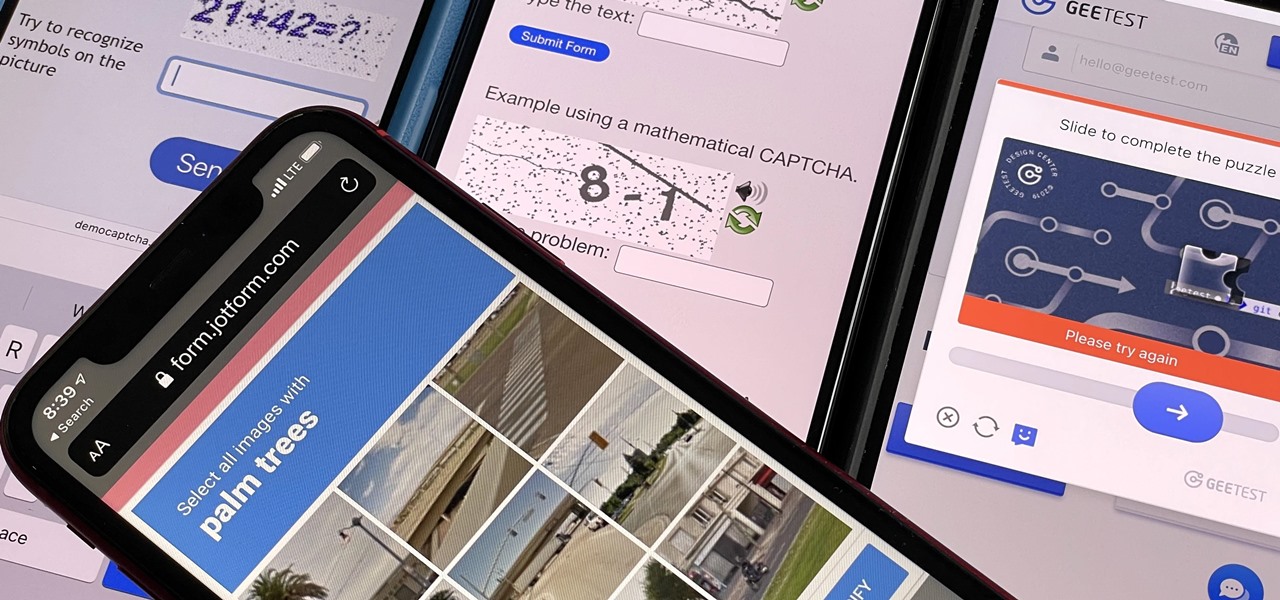
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

The emergence of Microsoft's HoloLens 2 as a cutting-edge US Army tool has focused a spotlight on the marriage between augmented reality and the military.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

Apple released the newest update for iPhone, iOS 14.5.1, today, Monday, May 3. The update (build number 18E212) is the first since iOS 14.5, which Apple made available one week earlier on Monday, April 26.

Apple just rolled out the of iOS 14.5 to developers and beta testers, and one of the headlining features is the ability to keep your iPhone unlocked when your Apple Watch is nearby. As these things tend to go, Android has actually had this same feature for years, though it isn't quite as polished.

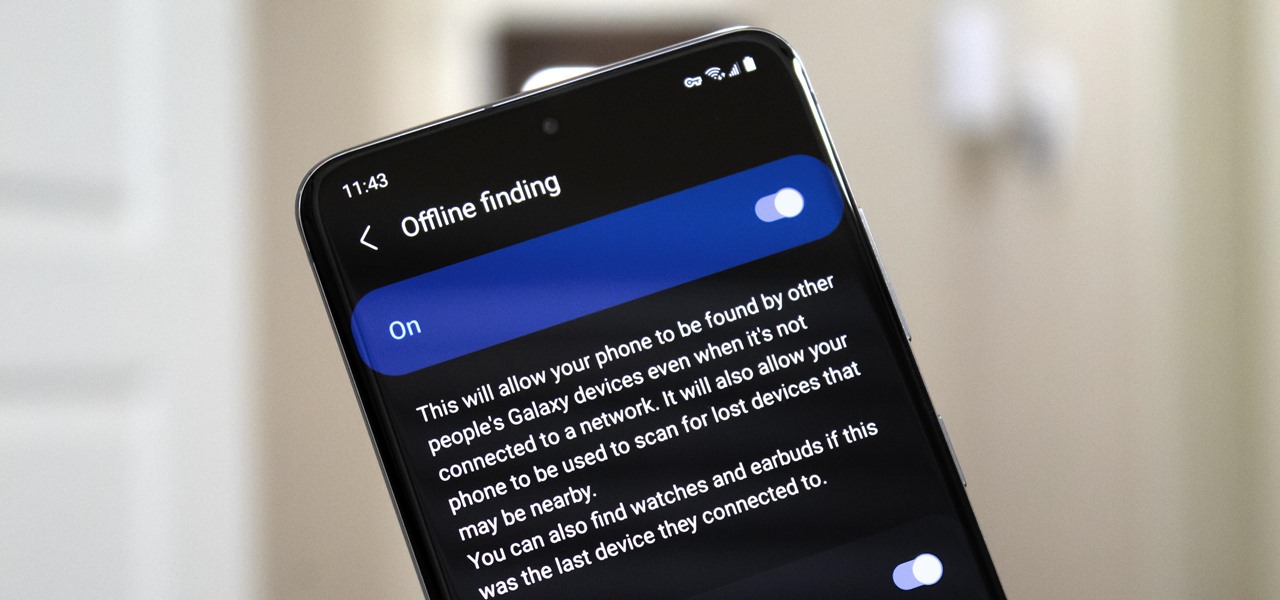
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.

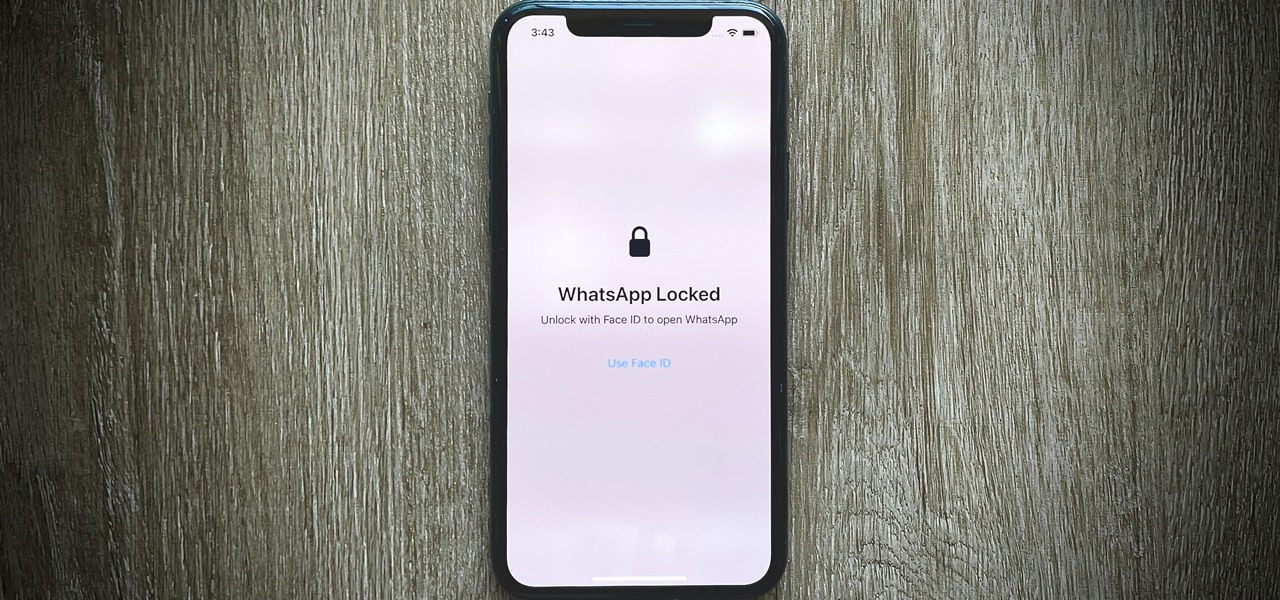
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.