While it may not be an obvious feature, Apple actually built a way into iOS that lets you hide specific pictures and videos in the Photos app that you want to keep on the down-low, for your eyes only. If you show off your photos a lot or stream slideshows to your TV, this is a great way to keep less appealing content private.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

In the not so distant past, you had to actually go meet someone in person to repay money you owed them. Say they covered your half of dinner or picked up movie tickets — they wouldn't get their money back at least until the next time you saw them. Thankfully, Venmo has effectively eliminated this inconvenience.
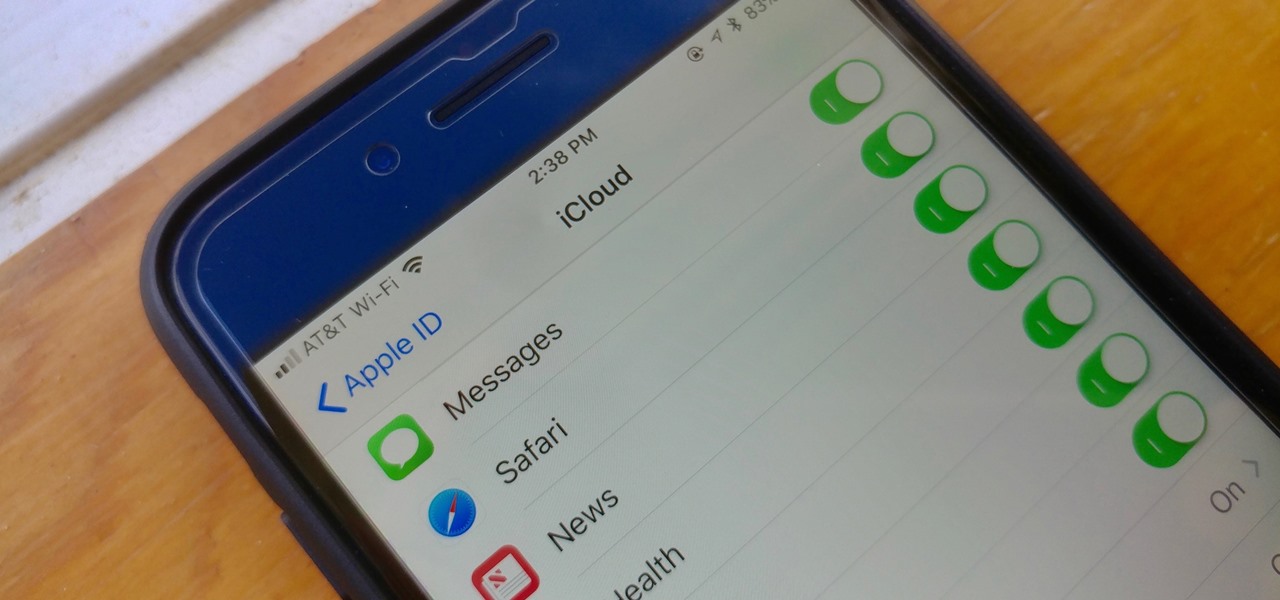
One major problem in previous iOS versions is that there was no way to keep messages in sync between an iPad, iPhone, iPod touch, and Mac. If you deleted a message in the Mac app, it would not be deleted on your iPhone, and vice versa. Apple finally fixed this issue in iOS 11.4 by storing all of the messages in iCloud, not on individual devices.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

It has not been a good year for Apple, as far as software scandals are concerned. From autocorrect nuisances to secret slowdowns of aging iPhones, Apple has had a lot to answer for. iOS users now have another issue to worry about — it's being called "chaiOS," and it's wrecking havoc on iPhones with just a simple URL.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Google, Facebook, and Huawei have made an investment in nurturing the future of augmented and virtual reality through $6 million in contributions to the opening of a new center at the University of Washington.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Both the Galaxy S8 and Galaxy Note 8 have Oreo beta software available in the wild at this point. We devoted a number of articles to covering what's new in Oreo and went into detail about the bugs and hiccups on both the S8 and the Note 8. Still, many people are left wondering — what's the difference between the Oreo builds on these two phones?

It recently came to light that a number of Android phones are unable to stream HD video through services like Netflix, Google Play Movies, and Amazon Prime Video. If you're worried that your phone may be affected, there's a simple tool you can use to find out for sure if you can actually stream video in 720p or higher.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.

Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

One of Android 8.0's central themes was battery improvements. Google implemented background restrictions and a few other under-the-hood changes, but the biggest battery-saving measure was almost user-hostile: A static notification that tells you when any of your apps are running in the background.

OnePlus surprised the mobile industry last year when it revealed the OnePlus 3T in November, an improved version of the OnePlus 3 that came out just months earlier in June. While many thought this was a fluke, history has repeated itself with the arrival of the OnePlus 5T.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

Back to the Future Part II missed wildly on many technological advances for the year 2015, such as flying cars and rehydration ovens. However, it connected on several predictions, such as video calling and biometric security, and it was in the ballpark (pun intended) on others, such as the Chicago Cubs winning the World Series.

Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.

The highly anticipated iPhone X is finally up for preorder, and it's been almost as exciting as we expected. With the dual cameras, bezel-less display, and high-tech facial recognition, there's almost nothing on the iPhone X that won't be liked. But around the same time as the iPhone X's announcement, another phone was revealed, and almost everyone seems to have forgotten about it. We didn't.

In a classic case of one step forward, two steps back, Apple has eliminated the ability to use multiple iCloud accounts for FaceTime and Messages in iOS 11, meaning the primary Apple ID on the account is the only one allowed. As inconvenient as this omission is, there's still a way to use alternate iCloud accounts on your iPhone with a little hackery.

Apple has something big in store for consumers in 2017 to mark the 10th anniversary of the iPhone. One major surprise is that Apple has decided to forgo on releasing a 7S in favor of a redesigned iPhone 8 and 8 Plus. To further commemorate its 10-year milestone, the Cupertino-based company has released the very exclusive iPhone X, garnering much excitement in the process.

CEO (and NR50 member) Tim Cook and Apple unveiled the long-awaited lineup of next-generation iPhones today on stage of the Steve Jobs Theater, packed with hardware improvements to facilitate AR experiences from ARKit, which will arrive with the iOS 11 on Sept. 19.

In the US, law enforcement officials can make you unlock your smartphone with a fingerprint, but they can't force you to input a password or PIN, which would violate your Fifth Amendment rights. To help you from ever being in a scenario where you're forced to put your finger on the Touch ID sensor, Apple has a built-in way for you to disable biometrics on your locked or unlocked iPhone in mere seconds.

It has been an interesting few days in developer news. The Microsoft blog has been busy with information relative to the augmented reality space. Meta 2 has also announced an interesting development this week. Here is a collection of various tidbits that have been collecting up.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

When it comes to watching movies and TV shows in Amazon's Prime Video service on an iPhone, it's as simple as installing the Amazon Prime Video app, signing into it, then playing content. However, on an Android phone, it's a lot more complicated.

General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

If you've accidentally turned on "Read Receipts" for all of your iMessages, there's an easy way to disable it so that no one knows when you're actually reading their incoming messages. You could also pick and choose which conversations can see that you've read their messages if you don't want to kill the feature entirely.

I have spent a good portion of this year traveling between cities and various emergent technology conferences and events. Most of these events have been really good, but in terms of augmented and mixed reality, the Augmented World Expo, in its eighth year running, definitely stood above the rest.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.