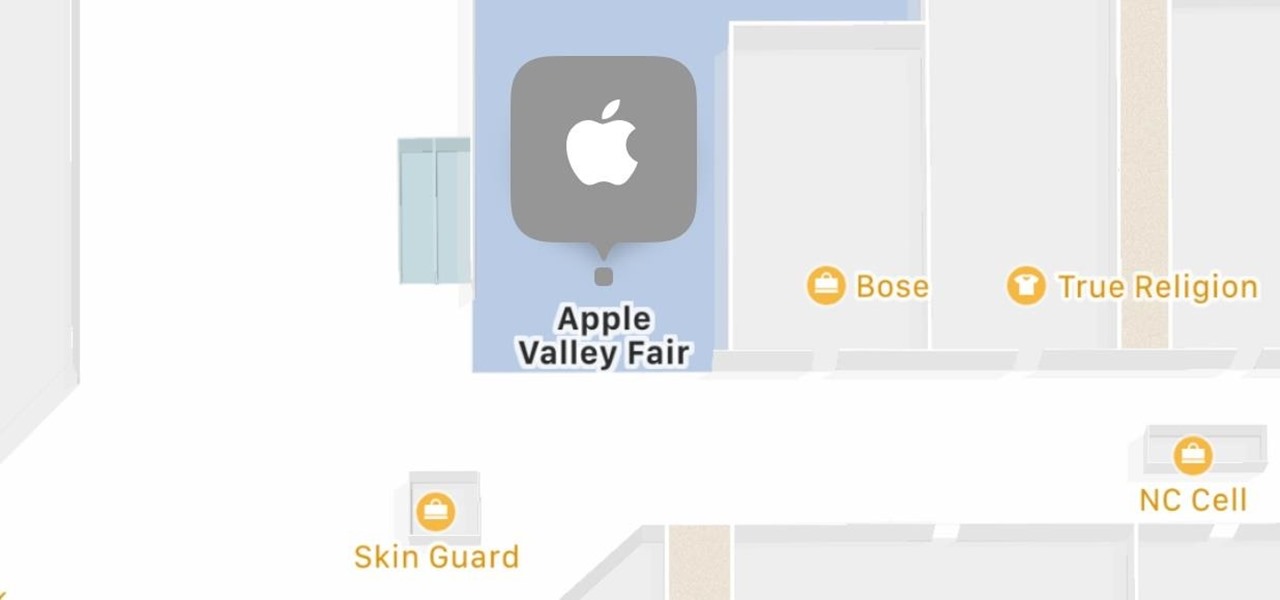
Apple has some great features aimed at making the lives of globetrotters and mall aficionados significantly easier, such as having detailed floor plans for airports and shopping centers in its native Maps app. With this feature available in Apple Maps, you no longer need to rely on publicly posted maps and directions that are often hard to understand.

Ride-hailing services are everywhere nowadays and with new companies developing all the time, it is one of the most convenient ways for people to get around. Companies like Uber make it easy for passengers to call a car to pick them up and drive them to their desired location. These services have been especially helpful for commuters as well as those who might need a ride home after a night at the bar. However, ride-hailing services require driving with a total stranger, which means the safet...

Despite what you may have heard, sleep is NOT for the weak. It's essential, not to mention it makes us feel a hell of a lot better in general. But for some, getting to sleep is easier said than done. In fact, about 50 million to 70 million people in the US have a sleep or wakefulness disorder, according to the CDC.
Yep, Google just put in place a new thing called the dun dun duuuun .... "Device Catalog!" No, not like the Macy's catalog of your smartphone dreams. This is quite the opposite.

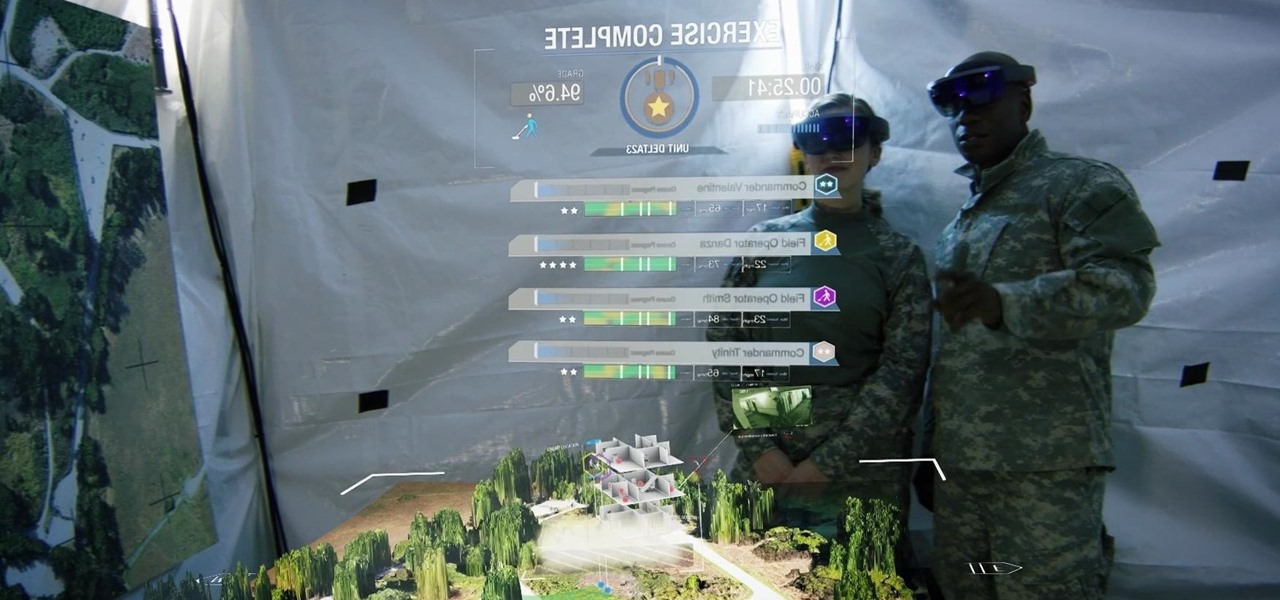
Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.
This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

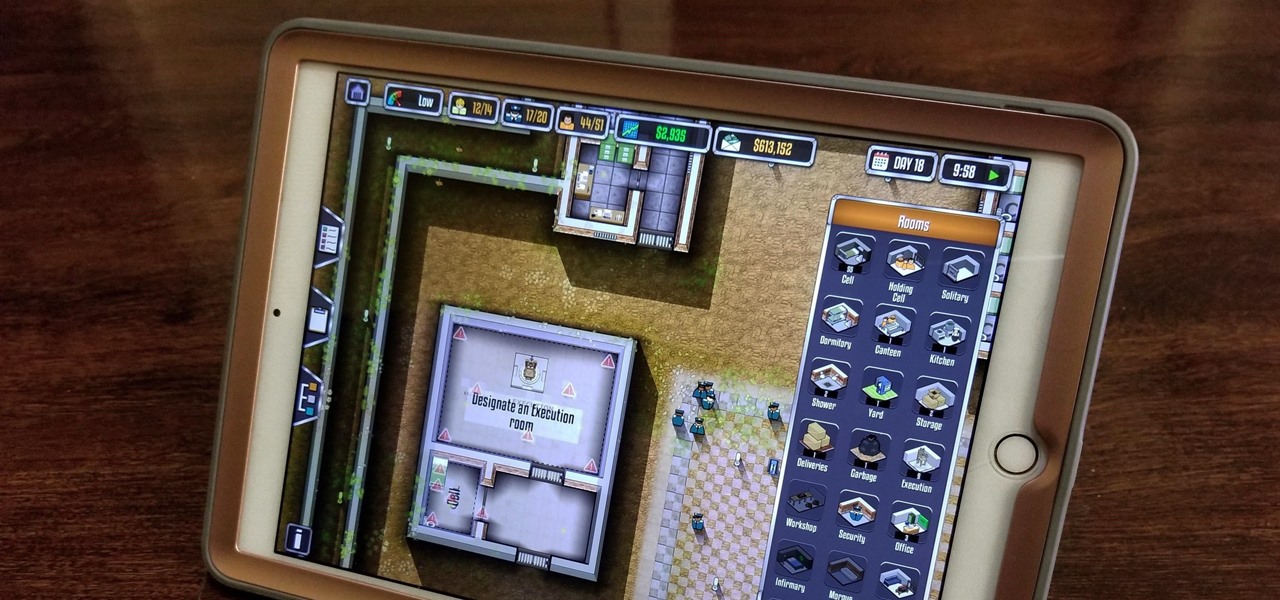
Prison Architect, the BAFTA winner for the Best Persistent Game in 2016, has finally soft launched on iOS. Originally a PC game, Prison Architect lets you build and maintain a maximum security prison. Comparable to running a small city, the game has you manage an ever-expanding correctional facility and contend not only with violent offenders and ever-present prospect of a chaotic riot, but also more mundane affairs like balancing the prison's budget and employee payroll. In addition to the s...

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

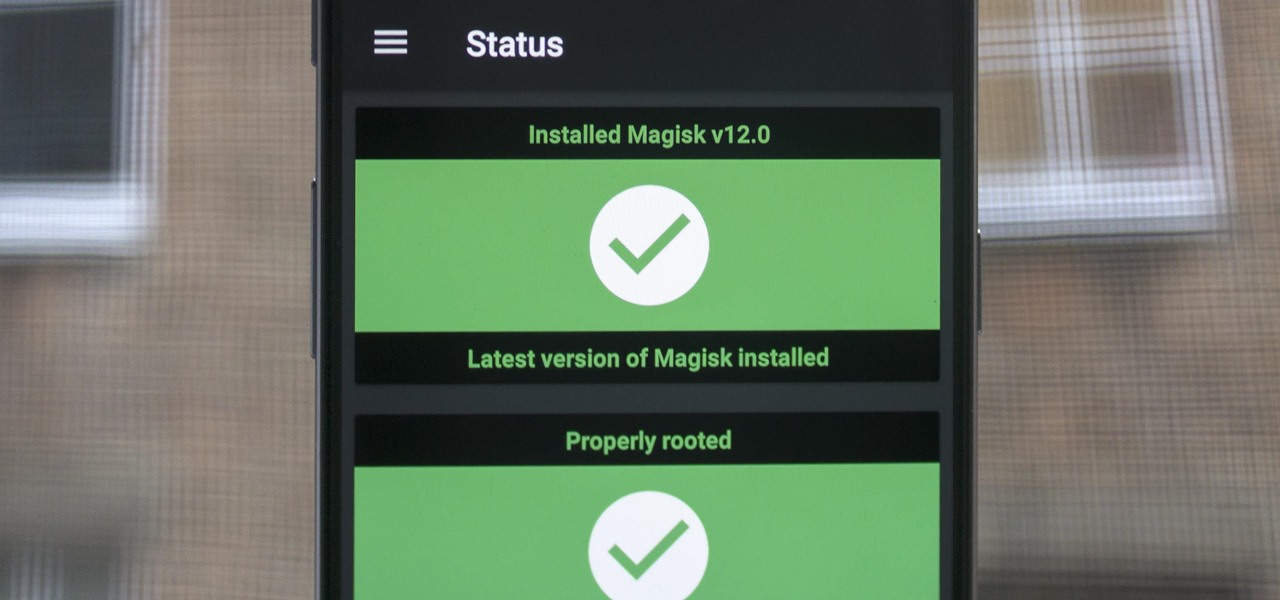
When Google added new security measures to Android Marshmallow, it had a lasting impact on the entire process of rooting. These measures prevent the the Superuser daemon (the process that handles requests for root access) from getting the permissions it needs to do its job at boot. In order to get around these issues, Chainfire created the systemless root method.

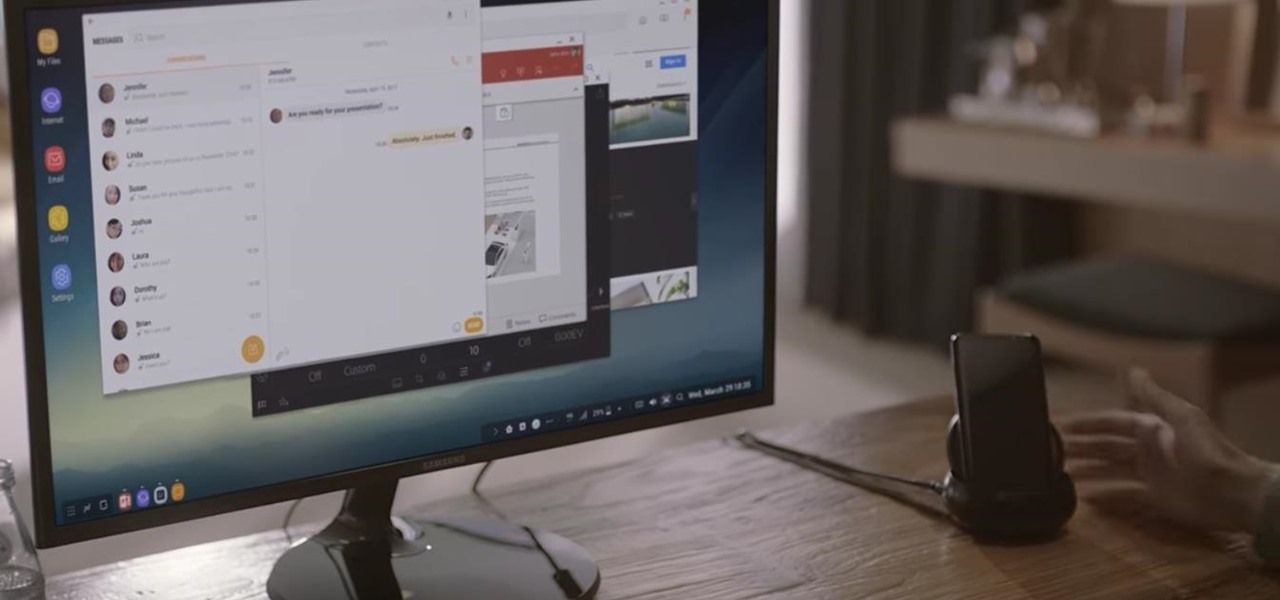
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

Apple's anxiously awaited iPhone 8 with a 5.8-inch OLED display is all set to launch this September, alongside the iPhone 7s variants. However, according to MacRumors, which cites information from a number of Barclays analysts, stock will be very limited, and most won't ship until late in the fourth quarter.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

It's 2017 and finally ordering "fries with that" at McDonald's is an even easier prospect for all you lovers out there ball and chained to the fast food game. The great big golden arches are moving one step closer to making your order as golden as it ought to be through a mobile ordering app using geofencing technology to track your location.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

Nintendo's first ever game for Android has finally touched down (unless you actually count the abomination that is Miitomo). Fire Emblem Heroes, a classic turn-based RPG optimized for mobile gaming, has come out for Android and iOS in Australia, Europe, and Japan, and is due out in North America and other worldwide locales very soon. Due to Nintendo's staggered release, the game isn't available to us in the United States at the time of this writing, but fret not—there's another way to downloa...

The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surgery, and forest fire management are just a few recent examples of ways 3D data visualization can benefit us all.

A few months ago, it was discovered that Verizon was installing an extremely shady app called "DT Ignite" on some of its smartphones—most notably, the Galaxy S7 and S7 Edge. The app, created by Digital Turbine, monitors your smartphone usage, then uses the data it collects to silently install "recommended" apps without notifying you.

No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

Before the iPhone 7 models were released, there were many rumors pointing to the inclusion of wireless charging, which obviously didn't happen. Now the rumor mill is back at it again for Apple's next smartphone, most likely being called the iPhone 8, and the possibility of wireless charging is more certain this time.

As we reported first here on Gadget Hacks, the Google Pixel and Pixel XL have unlockable bootloaders, with the exception of models purchased from Verizon. This means that once the TWRP custom recovery is installed, you can flash ZIPs and even root your device in a few taps—as long as you unlock the bootloader beforehand.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Google's Pixel phones have a feature that lets you swipe down on the fingerprint scanner to open your notification shade and Quick Settings panel. It's one of those features that make you wonder why it wasn't there in the first place, since it gives you another way to interact with your device, and your fingerprint scanner isn't being used while you're screen is on anyway.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums.

An accelerometer/gyro goes onto an Arduino board and transmits the angular motion of the skateboard via Bluetooth to a virtual reality game I made for Android phones and Google Cardboard.

LG got in on the action at Mobile World Congress in Barcelona by unveiling its new G5 handset on Sunday, February 21st. It will be the first publicly available modular smartphone by a top tech giant.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing.