While it may not always be practical, controlling your smartphone with air gestures can be pretty awesome. I would bet that if someone in public saw you using gestures to maneuver through your device, they'd be pretty impressed—and also kind of creepy for watching you.

I've already covered how you can automatically save Snapchat photos and videos to your Samsung Galaxy Note 2, and how to take screenshots of Snapchats sent to you without the sender knowing, but there's one other thing about Snapchat that could use some softModding.
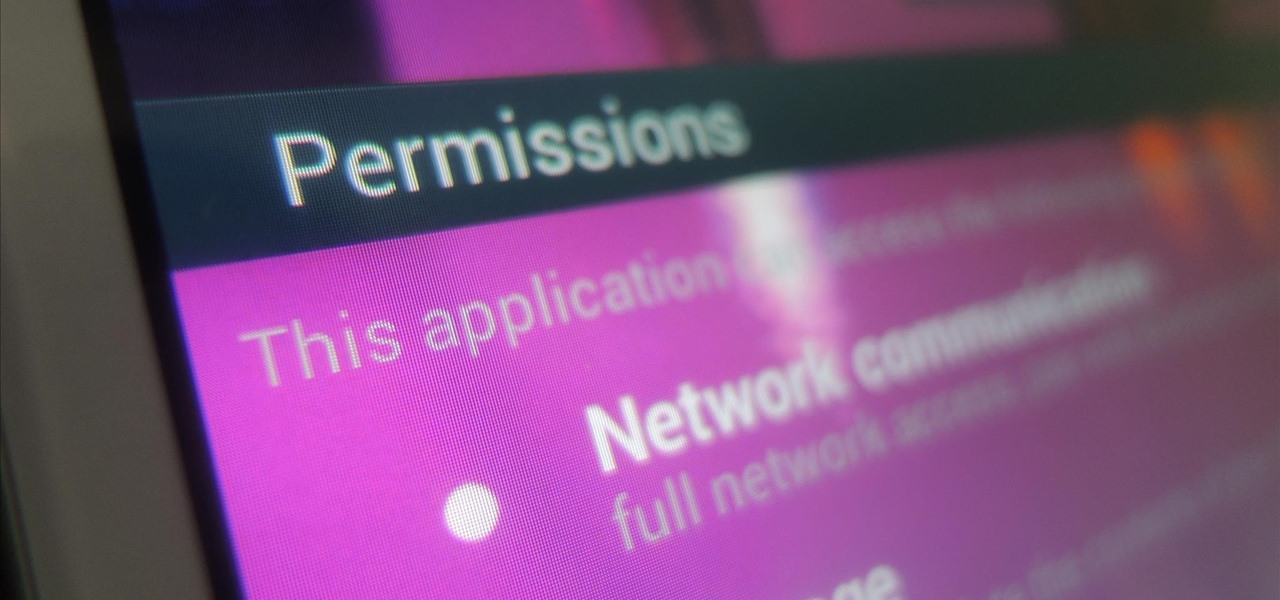
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.
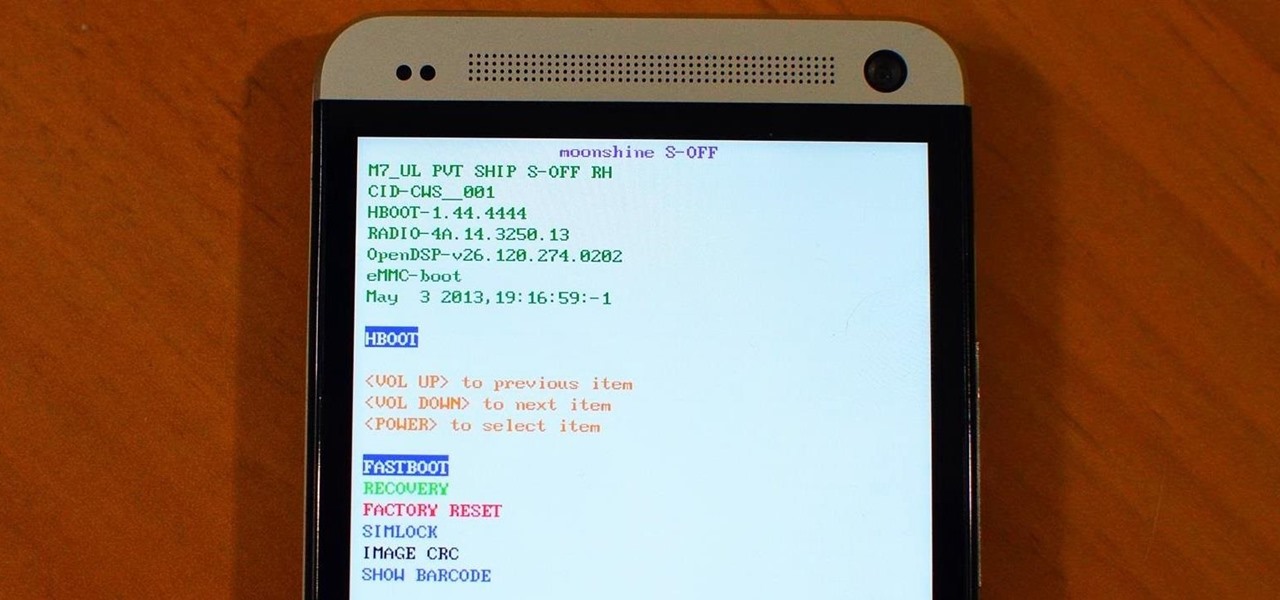
If you still have time left on your warranty, taking your HTC One in for repairs can be a serious pain if you've modified it in any way. To avoid the chance that they'll reject your phone because it's been tampered with, you'll have to return it to stock condition.
While there are many customization options available for the Samsung Galaxy Note 2, they aren't always easy. The large selection of custom ROMs and difficulty implementing certain hacks and mods can be a nightmare for anyone not well versed in all things Android. But the good news is, it doesn't always have to be complicated.

The transition from an iPhone to a Samsung Galaxy Note 2 or other Android device can be a tough one. A vastly different operating system and the ability to customize anything and everything might be too much for some people. Taking in all that new, while having to let go of the old, can be as daunting as climbing Mount Everest.

Give me a paintbrush and easel and you'll be sorely disappointed, but give me a Samsung Galaxy S3 and a new app called Let's 8-Bit Art and you might call me the next Picasso.

There are a ton of options available to Android users when it come to messaging, but the problem is that with all of these options, where is the go-to app? The one used by most people? The one that can offer a more unified approach?

Don't always believe the marketing hype. "PlayStation Certified" does not mean anything to a softModder. All this indicates is that a smartphone or tablet labeled as "PlayStation Certified" has met the guidelines and hardware requirements issued by Sony to display PlayStation Mobile (PSM) content from the PlayStation Mobile Store correctly. No Nexus 7 here.

The airline is not your friend. It will do anything it can to gouge your dignity, time, and most of all, money. One of the biggest scams to get a few extra bucks out of you are those dreaded baggage fees. If the lines, security, "random" screenings, and unwanted fondling aren't bad enough, you have to pay them to check your bags (which, most of the time, is done poorly). Flying truly is the most inconvenient way to travel.

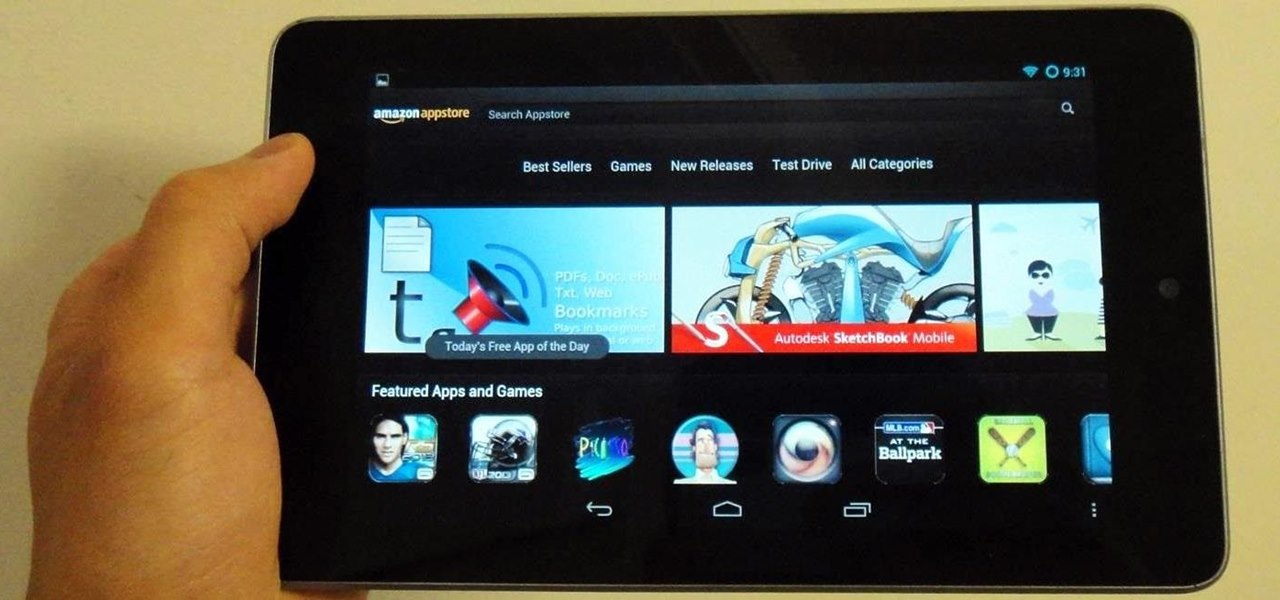
All across the world, Nexus 7s have been secretly living a double life. The clean, simple look of the stock Holo user interface is nice if minimalism is your thing, but to softModders like me, Holo is bare, lacking style, overly blue, and an eyesore. It gets the job done, but I want something more customizable and visually stunning.

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

In a previous article, I pointed out a few criticisms of the Google Play Store, mostly about how unpolished and inefficient it is. To give you a better idea of what I mean, here are just a few of my complaints with the Play Store:

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Something went wrong and your Nexus 7 is freaking out on you. Maybe you flashed a bad ROM or ZIP file, or maybe it's just bugging, and it's time to restore your tablet back to a working condition. Thankfully, you've already made a backup of your Nexus 7!

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

The problem of system freezes is not new to the world of Windows and this has come to light even in the latest Windows 8 release. In the event that your system freezes, you cannot open your desktop files, some controls stop functioning, or you are unable to launch the start screen applications either. You may experience this unusual behavior after updating Apps in the store or due to a driver issue. Sometimes, freezes occur because of video card problems too. In order to do away with these Wi...

The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

The beauty of free apps is that, well, they're free. But as we all know, there is no such thing as a free lunch. Sometimes these "free" applications are only feature-limited mini versions, or they're so littered with ads that opting to pay for it is the only way to actually enjoy it.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

Tripwires are a new mechanic released in Minecraft 1.3, and people are still trying to figure out how best to use them. Minecart returns are a great idea, but what about traps?

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

Hello! This post is not about craft, it's about cyber bullying. If you ever had such an experience, that an unknown hacker was bullying you for no reason at all, please follow my words. Thank you! Step 1: Let All the People You Know That Your Are Being Harassed.

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

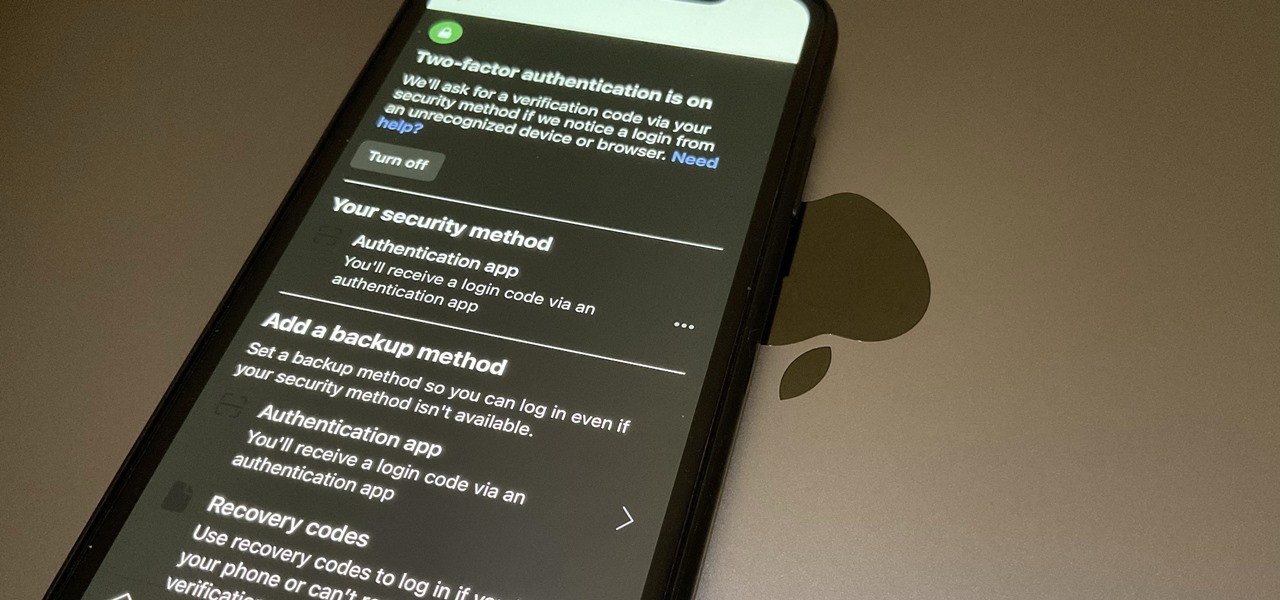
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

Amazon really wants to make itself at home in your home. Like, everywhere in your home, from your doorstep to your kitchen, your kids' rooms, and everywhere in between.

In the tech world, our data is always under attack. When you download and install a new app, it can be difficult to know what information the app is actually accessing. Thankfully, a new emphasis on privacy in iOS 14 changes the game, exposing more of what your apps want access to — and even changing some behavior along the way.

In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools they need to enhance their protection.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

Imagine, never needing to unlock your car door with a key. Actually, it's been around for a while, and it's called keyless remote entry, but on the 2010 Lincoln MKS, it's not remote… it's built directly into the side of the car door. It's a number pad with a programmable security code. This video will show you how to unlock your vehicle without even reaching into your pocket! If you have a MKS.

In this video, Karlyn M. Campbell, an Information Technology student, goes through how to set up and secure a wireless network on a laptop. For a wireless network you will need your computer, a wireless router and its CD, and a USB wire. First the video goes through how to set up the router by using its installation CD. This video uses a Belkin router, and so shows the steps the Belkin installation CD takes the user through. The CD also lets the user decide which security settings he or she w...

Greg French talks to us about the different ways to reboot a computer to resolve issues in the computer. The first way is by pressing F8 key while startup after rebooting the system. When you insert a wrong driver for video card or something, sometimes when you boot the computer, it gives a black screen. Now he says you can resolve this problem by rebooting the computer and pressing the F8 key while startup. This will take you to a menu selection where you should select 'Safe Mode' and hit en...

You look up the screen and see those smiling faces, those excited fans and think, that should be me. Well, it can! Anyone can get a little camera time at football game. You can let it be up to fate or you can get proactive and improve your chances of the camera finding you.

If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.