Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

Backtrack 5 is a Security Essentials Backtrack is a suite of tools to help with Penetration of any Network, Unix, Linux, or Microsoft Based. Backtrack 5 is good for WEP & WPA hacking and penetration testing.

Screw gaming, let's get to the serious stuff! Here's an amazing video of a Kinect hack that lets one see what its camera sees - in 3D.

Life is getting more and more convenient. You can pick up a wireless signal at nearly any coffee shop these days (Starbucks is now officially free in every location across the nation), as well as airports, libraries, hotels and more. However, along with this convenience comes the risk of security breach. Passwords. Emails. Account numbers.
While following a tutorial on python recon tools, I found a new way to access the command prompt on a school network. While there are other ways of bypassing security, it's nice to learn use Python's OS library.

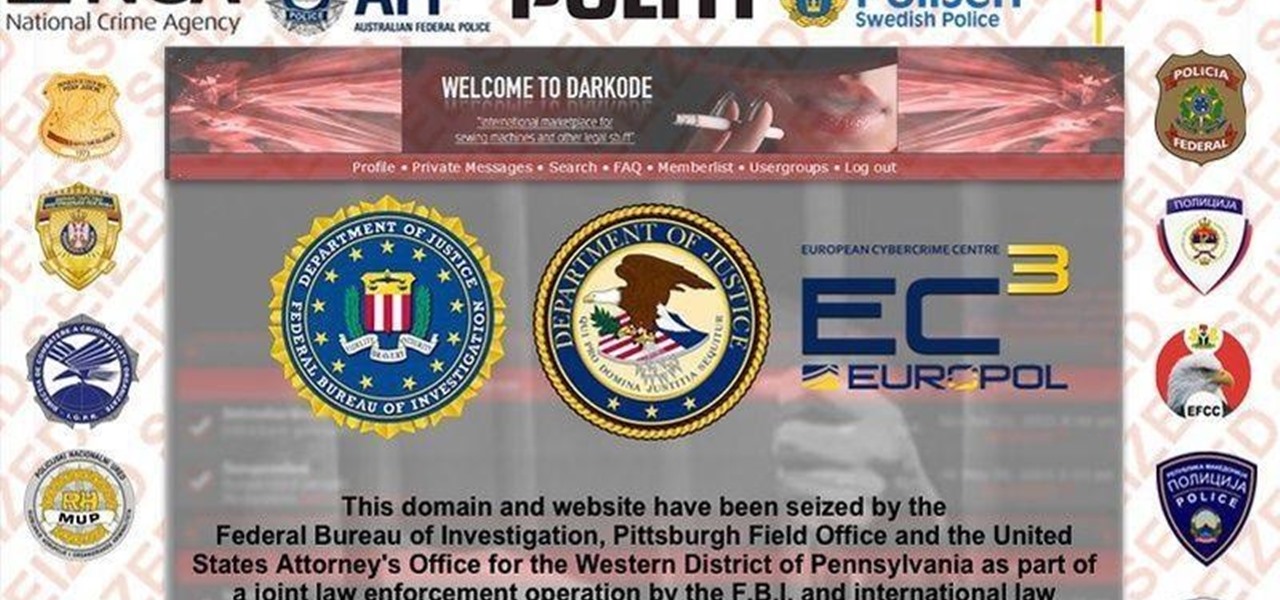
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...

Lorrie Faith Cranor: What’s wrong with your pa$$w0rd? | Talk Video | TED.com.

Two former high-ranking officials at the U.S. National Security Agency (NSA), a federal bureaucracy that collects data and intelligence on foreign communications for national security purposes, have come forward with allegations that the NSA actively monitors Americans as well. According to testimonies from both Thomas Drake, a former NSA senior official, and Kirk Wiebe, a former NSA senior analyst, the agency actively monitors and collects intelligence on every single American as part of a m...

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.

Apple just released iOS 13.5.1, the latest update for iPhone, on Monday, June 1. The update comes 12 days after iOS 13.5, which introduced COVID-19 exposure notifications, a Group FaceTime update, and Face ID improvements when wearing a mask.

Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity.

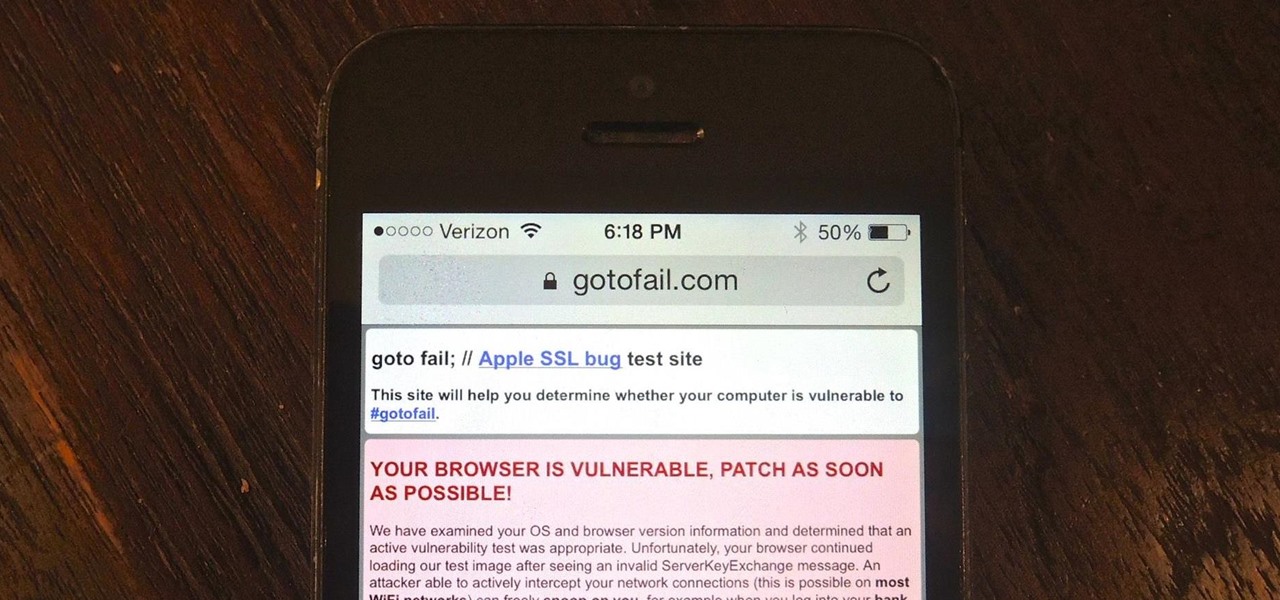
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.

You may have noticed that the HTC One Google Play Edition has a fancy red live wallpaper added to the list of live wallpapers. This new one is called "Sunbeam," and I'm going to show you quickly how you can get it on your regular HTC One right now.
The Department of Homeland Security has been forced to release a list of keywords and phrases it uses to monitor social networking sites and online media for signs of terrorist or other threats against the U.S.
The top-secret US National Security Agency is not required to reveal any deal it may have with Google to help protect against cyber attacks, an appeals court ruled Friday.

To decipher my password, you need to know my mother's maiden name, where I was born, and what I had for breakfast on August 12th, 1996 (trick question, I was in a food coma).
Stanford is soon supposed to offer free classes in Cryptology, Computer Security and a slew of other intriguing topics! Check out the site to sign up and learn more!

Cool world. Check it out and post your ideas to the forum.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

Here is the Trailer for a new insane movie called 22nd of May 22nd of May Koen Mortier, Belgium World Premiere

Using Embird embroidery software, Rosanne shows us how to use the Basting Stitches control properly, for a perfect design. Rosanne will also show you the bast in a hoop technique for more security. Insert basting stitches in Embird.

Middle-aged man instructs how to mount a rack bolt onto a door to strengthen the security of the door. Great video using subtitles and clear demonstration of how to use a drill when mounting the rack bolt kit. Fit a rack bolt onto a door.

No more Internet Explorer 9 Beta. Not today. Now you can explore the web with Microsoft's new Internet Explorer 9 Release Candidate (RC). It wasn't supposed to be released until tomorrow, February 10th, but it's been leaked a little early, WinRumors reports.
Fascinating, although admittedly highbrow, discussion on the history of cryptography from the BBC. If you are outside of the UK and don't know how to access BBC content you need to spend a bit more time browsing the Null-Byte forums ;-) http://www.bbc.co.uk/programmes/b06mtms8

Startup promises to catch 100% of network attacks - Techworld.com.

A former decorated undercover FBI agent, Mike German, explains how the national security state, in league with local law enforcement, is secretly targeting Americans for political views and activities perceived as a threat to the political establishment. » Former FBI Agent: Surveillance State Trashing Constitutional Protections Alex Jones' Infowars: There's a war on for your mind!.

(CNSNews.com) – There have been 2,527 Department of Homeland Security (DHS) employees and co-conspirators convicted of corruption and other criminal misconduct since 2004, according to a federal auditor Federal Auditor: 2,527 DHS Employees and Co-Conspirators Convicted of Crimes | CNSNews.com.

While US Defense Secretary Leon Panetta attempted to convince top Israeli politicians and security officials not to launch a strike on Iran's nuclear facilities during his visit to Israel last week, his predecessor Donald Rumsfeld, seems more prepared for a possible attack. Rumsfeld: Israel needn't notify US about strike - Israel News, Ynetnews.

In preparing to use surveillance drones for protests and “public safety,” the Department of Homeland Security is following Russia’s lead, where Vladimir Putin has approved a massive expansion of the technology specifically for the purpose of monitoring demonstrators. » U.S. Follows Russia In Using Drones To Spy On Protesters.

The Department of Homeland Security has put out an urgent solicitation for hundreds of items of “riot gear,” in preparation for expected unrest at the upcoming Republican National Convention, Democratic National Convention and next year’s presidential inauguration. » DHS Puts Out Urgent Order For Riot Gear.

In a rare admission that has gone almost completely unreported, the Director of National Intelligence has admitted that the National Security Agency violated the US constitution and abused its power by spying on American citizens and monitoring their communications. » Feds Admit NSA Spying Violated 4th Amendment.

The National Security Agency is storing all electronic communications and analyzing them in real time, according to former NSA employee turned whistleblower William Binney, who warns that the federal agency has a Google-style capability to search all conversations for keywords. » Whistleblower: NSA Analyzing Conversations In Real Time.

The Obama administration has given the Department of Homeland Security powers to prioritize government communications over privately owned telephone and Internet systems in emergencies. DHS emergency power extended, including control of private telecom systems - Washington Times.

Now, that's some whittling. Awesome school-desk-art by Ben Turnbull. See how wood carver Bob Seguin makes a mini navy colt revolver out of basswood here.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

In this video tutorial, viewers learn how to set and encrypt their Wi-Fi password using WPA in Apple Airport. Begin by opening the Airport Admin Utility application from the CD. Then locate your the name of your network and double-click it or press the Configure button at the bottom right of the screen. Now enter your password and click OK. The network should be opened now. Then click on the Airport tab and click on Wireless Security. In the pull-down menu, select WPA2 Personal. Then click on...