Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.
David Blaine has made millions off his magic tricks and mind-bending illusions, so why shouldn't we get in on the action, too? Well, your Samsung Galaxy S3 can do all kinds of things, but magic isn't one of them...yet.

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.
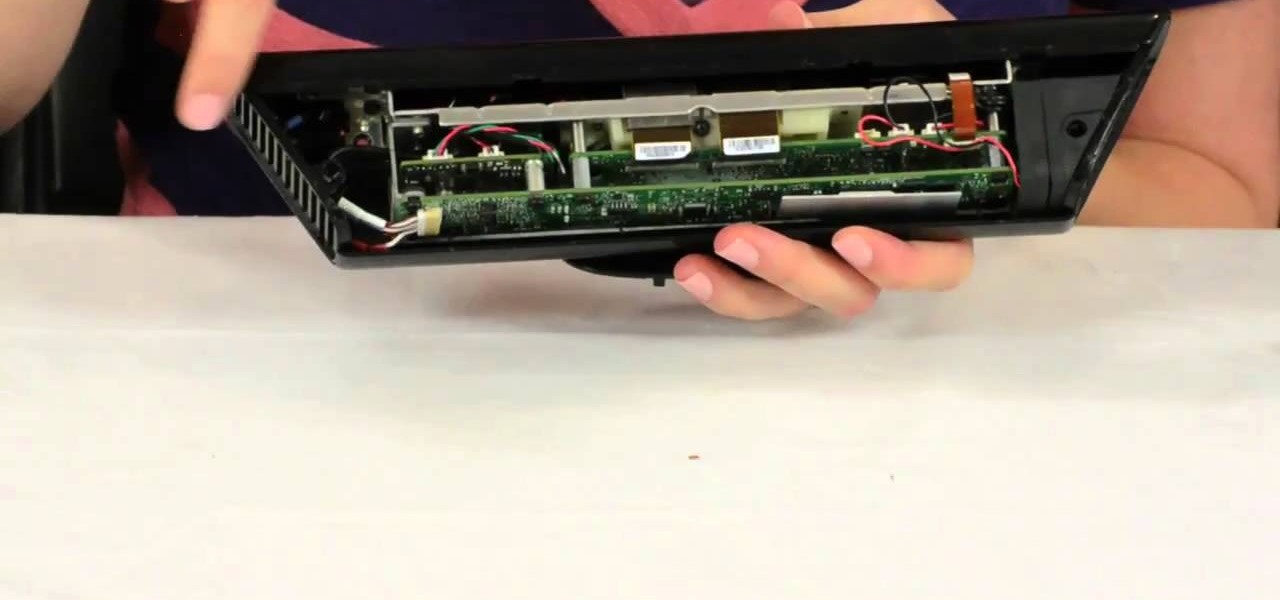
Microsoft's Kinect is gaining popularity with Xbox 360 owners, but what's really more fun? Playing games with this revolutionary hands-free gaming device or gutting the sucker to see what it's all about? We'll take the latter choice.
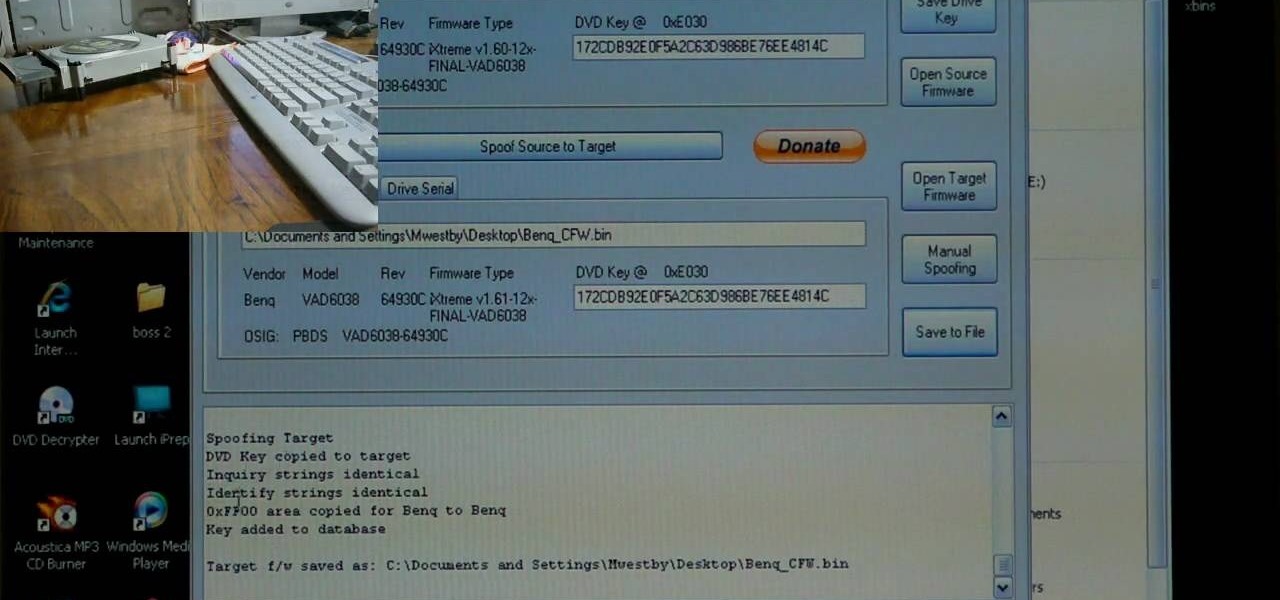
If you've already flashed your XBox 360's disc drive, then congratulations, you've accomplished the most challenging step involved in hacking you XBox. You aren't done though. As Microsoft keeps updating it's firmware to try and fend off hackers, you must keep updating your custom firmware to thwart their efforts. This video will show you how to upgrade your flashed BenQ XBox 360 disc drive's firmware to IXtreme 1.61 using Jungle Flasher 1.61. NOw you can play your burned games with a greater...

Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

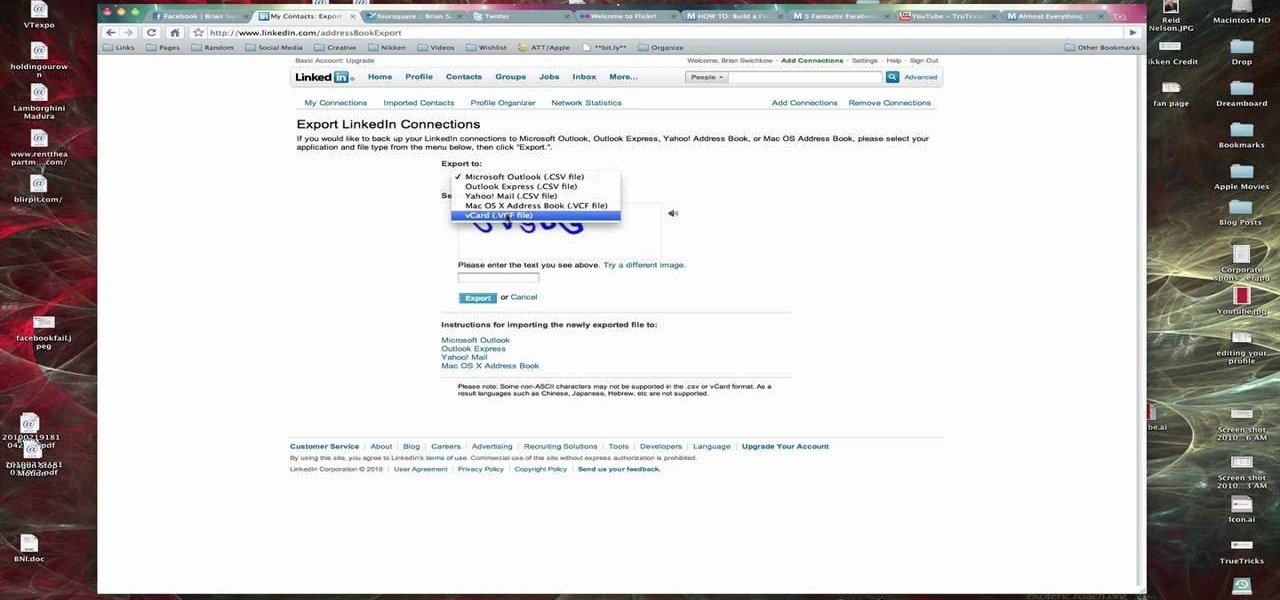
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

Installing a peephole in your home's front door can give you and your family a sense of security knowing who comes to your door before they enter. In this video Barbara K will show us exactly how to install a peephole on your door.

When you need a website to showcase your product or service, it can be quite confusing. Follow these easy steps to gather everything you need to have a successful website. Start your search for a domain name in the domain name registrar. (Example: www.companyname.com) Rent space from a hosting company to hold the files for your website. Set up an email account for your company. Create the content for your website (example: products, prices, services, etc). Get internet security to protect sen...

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

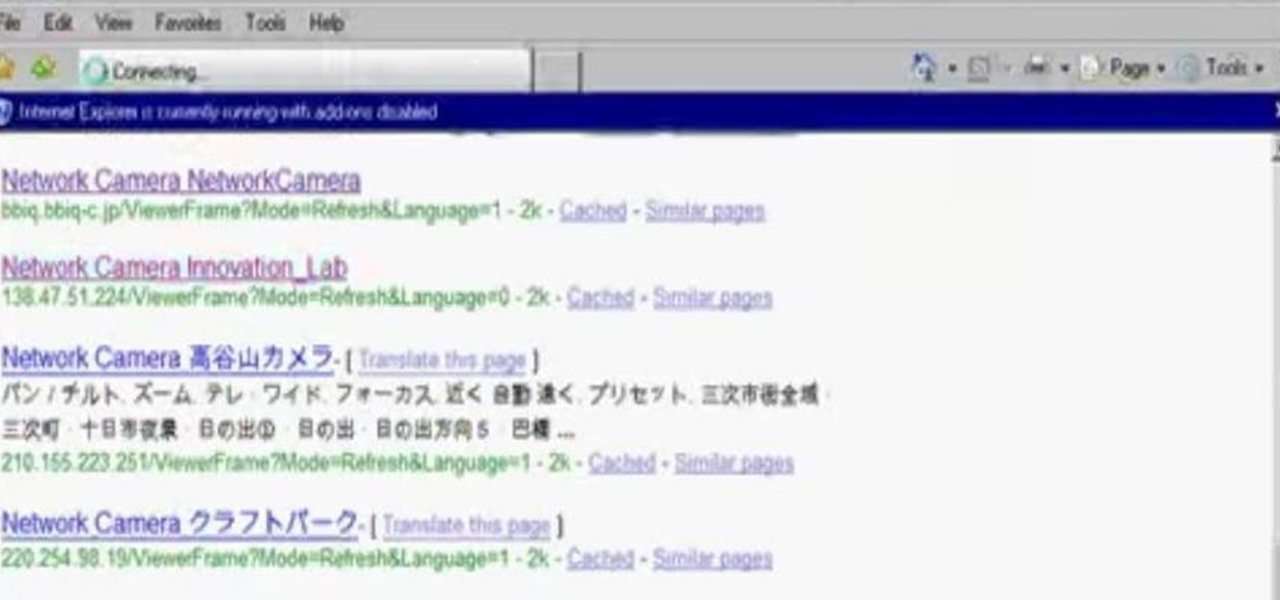
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!

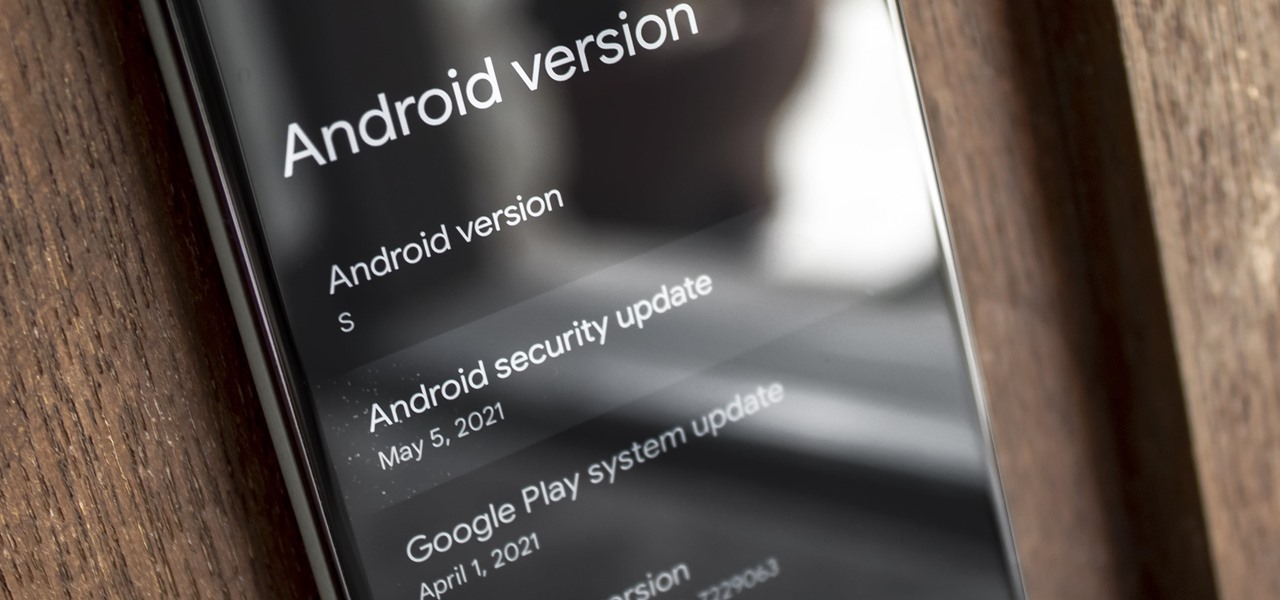
Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

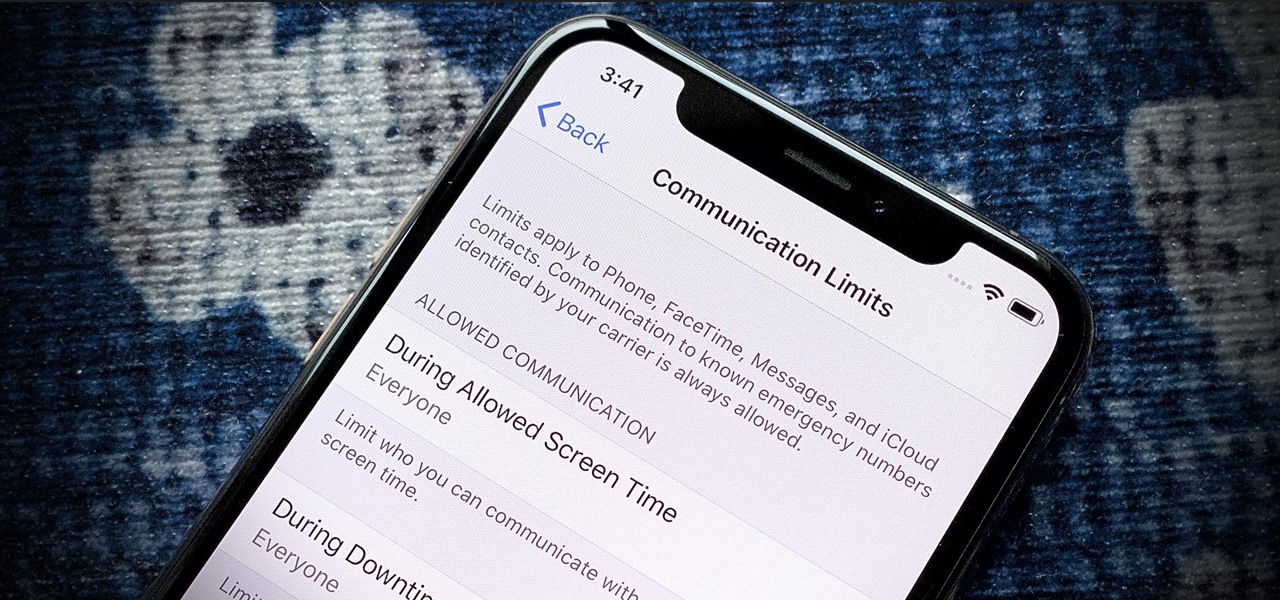
There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Not sure how to enable javascript on your computer? Follow these steps to enable all the functionality javascript provides.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Apple just released iOS 14.4.1 for iPhone today, Monday, Mar. 8. The event marks 41 days since Apple released a public update for iPhones, with iOS 14.4 back on Jan. 26.

Apple released iOS 13.4.1 to the public on April 7 but also pushed out the update for the new second-generation iPhone SE model on April 23, one day before the device's official release. The update fixes a FaceTime bug and Bluetooth quick action failure that appeared in iOS 13.4.

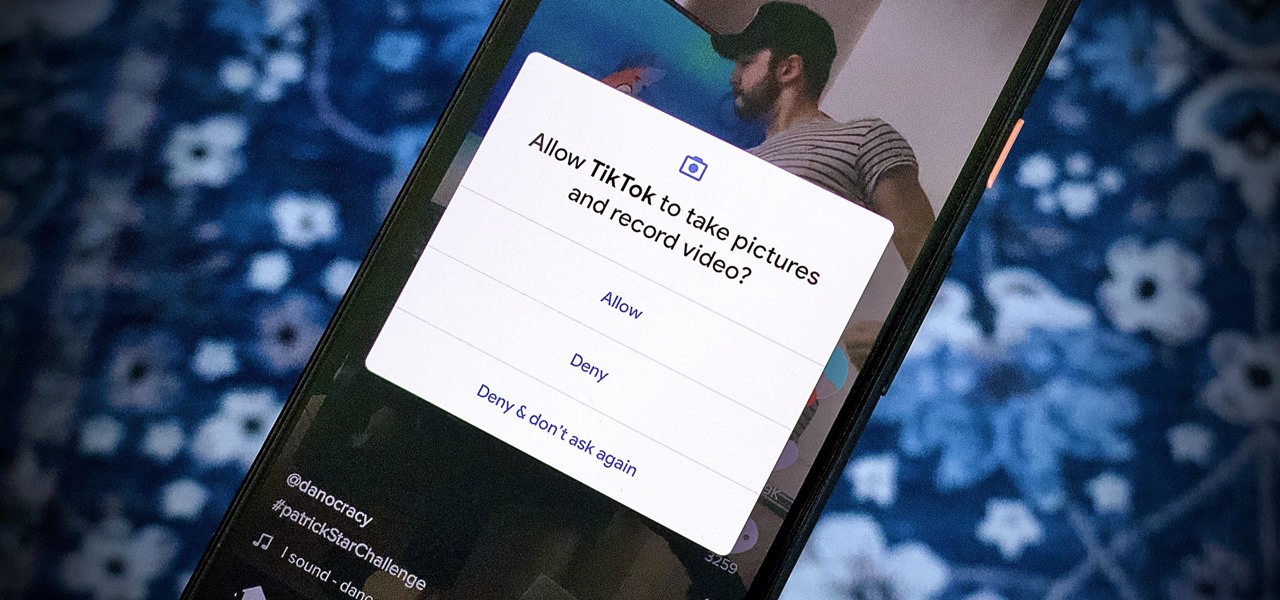
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.

Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.

Just two days ago, on Nov. 18, Apple released iOS 13.2.3 to the general public, which included stability updates for bugs affecting iOS 13.2 and earlier. Today's update isn't for the general public, however. Instead, Apple just pushed out iOS 13.3 developer beta 3 for software testers.

Apple is often unpredictable when it comes to beta releases, especially with public betas. Developers receive their updates first, then public testers have to wait and see if Apple will do the same for us. Sometimes, the iPhone OEM makes us wait until the following day, but not with iOS 13.3 public beta 2. This update is now available to download and install.

We're finally back in the swing of things. For the first 26 days after the release of iOS 13.2, which introduced 22 new features and changes to the iOS 13 era, there wasn't a new beta. Then, Apple released iOS 13.3 developer beta 1, and now we seem to be back on schedule, as Apple just released 13.3 beta 2 to developers.

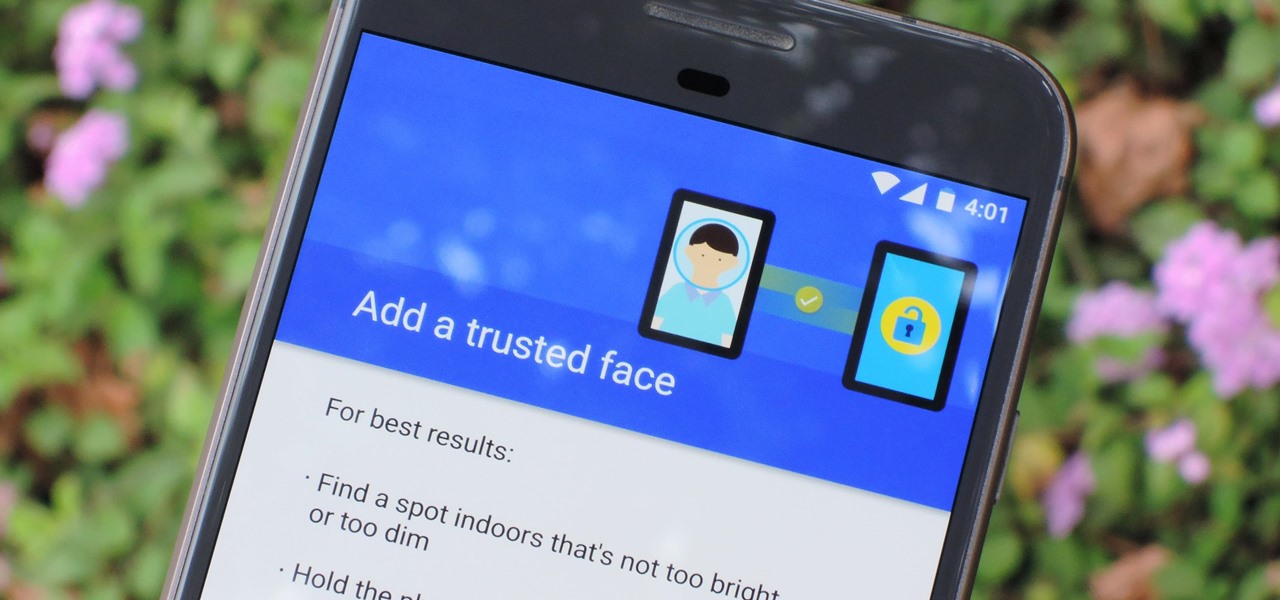
The Pixel 4 and 4 XL are the first Android phones released in the US to support secure facial recognition. You no longer have to hate on your Apple's friends because you now have "Face ID" as well. So I assume you want to set it up right away — here's how.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

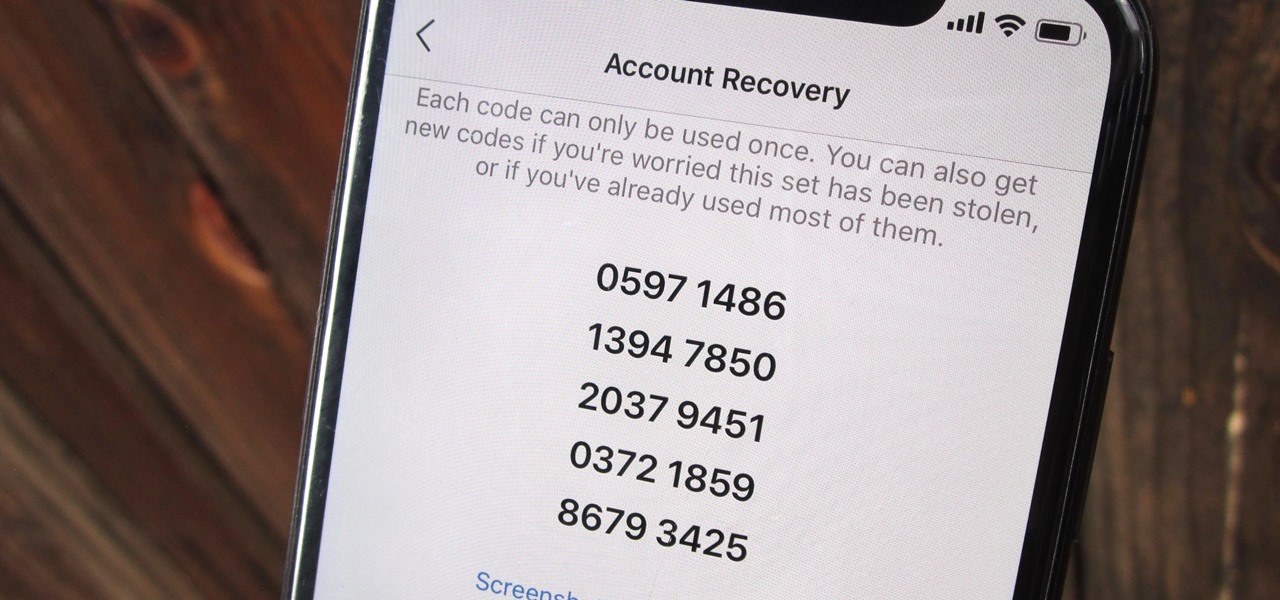
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Apple wastes no time with betas. Right on the heels of the official release of iOS 12.1, Apple released the first beta for iOS 12.1.1 to developers on Wednesday, Oct. 31. The update comes just one day after iOS 12.1, which itself was in beta development for 43 days this year. The denotation for 12.1.1 indicates it's a minor update over 12.1, and there are only a few things in its release notes.