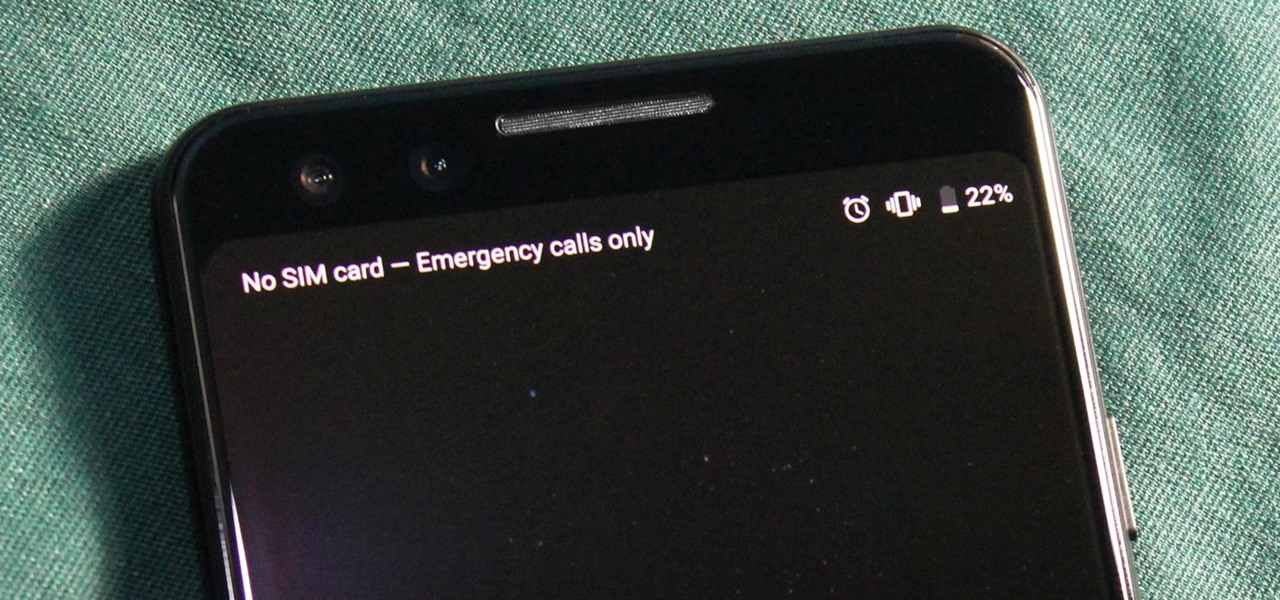
You just brought a brand new Pixel 3 from the Google Store, and you insert your SIM card only to find the phone won't recognize it at all. No matter what you do, the SIM card won't register and your Pixel won't connect to your carrier network. That's what happened to me and several other Pixel 3 owners. The good news is a fix is coming, the bad news is Google doesn't have a date for that fix.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

With each year that we anxiously await Apple's next big version of iOS, there comes the sad reality that the eldest iPhones will not continue to receive support. That's not the case with iOS 12, however, as the software is compatible with all iPhones currently running iOS 11, going back as far as the iPhone 5S.

Accused of violating whistleblower and age discrimination laws by its security director, Magic Leap has taken an internal situation to the US District Court to clear its name of the allegations.

Apple released the fourth beta for iOS 11.2.5 on Tuesday, Dec. 9, to developers and then public beta testers. It comes only one day after the official release of iOS 11.2.2, which addressed the Spectre portion of the chip flaw security risks reported last week.
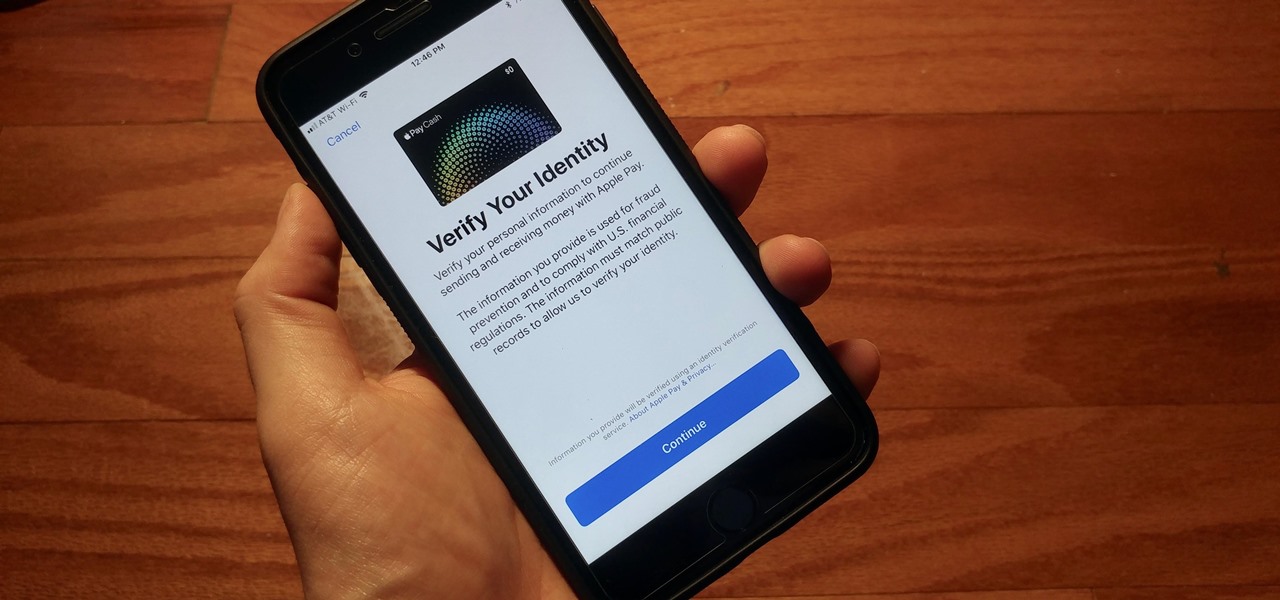
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

The first big update to iOS 11 since its release in mid-September just came out, so check your iPhone for a software update to iOS 11.1, because there are a few things you'll want from it. While there's no sight of Apple Pay Cash or Messages in iCloud, there are some significant improvements you'll need to know about.

There have been a number of rumors about the iPhone 8 over the past couple of months, but the latest speculation about the device's dual FaceTime camera, that could take 3D selfies, has definitely grabbed our attention.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

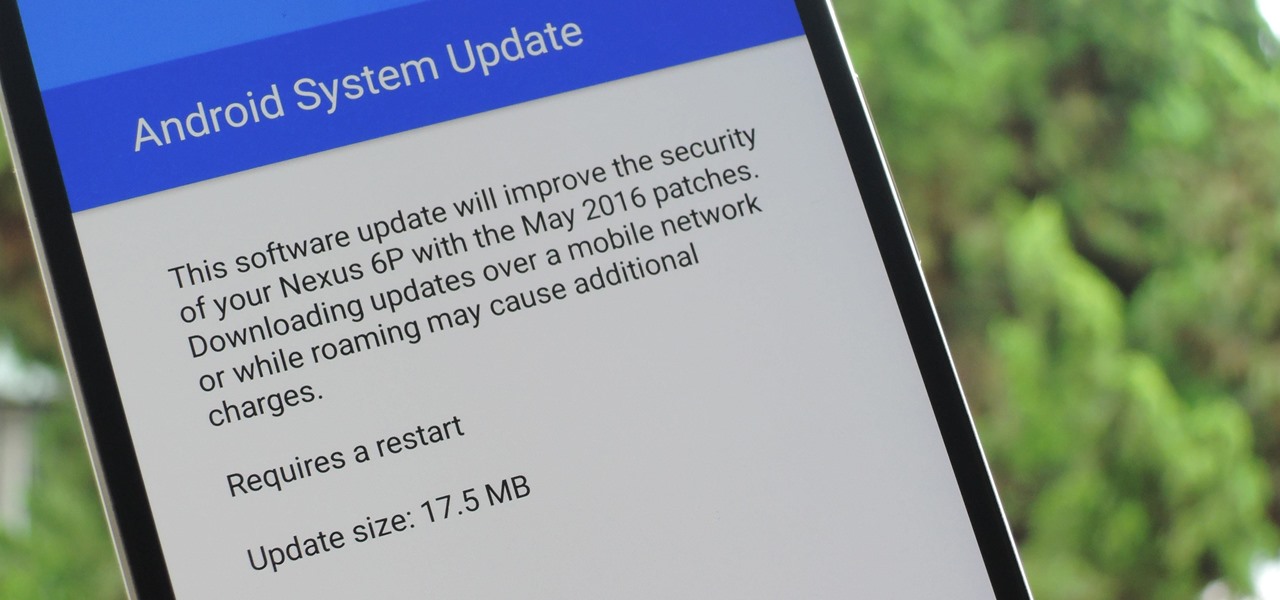
The beauty of Nexus devices is they receive firmware updates faster than any other Android phone, and keep getting updates for years longer than most of the competition. This means that you can always use the great new features that come along with an Android update, and even more importantly, your phone gets monthly security patches to keep hackers and malware at bay.

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Google Maps, in conjunction with the Android operating system, is a powerful tool for navigation that is often underutilized. While it's no secret that it can get you to wherever you're going and back, some of you might not know that you can use Google Maps without even having to touch the screen. Not having to touch your display means you can concentrate on other things, you know, like driving or eating that jelly-filled donut.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches to plug up loopholes exactly like this one. Yeah, it's that big of a deal.

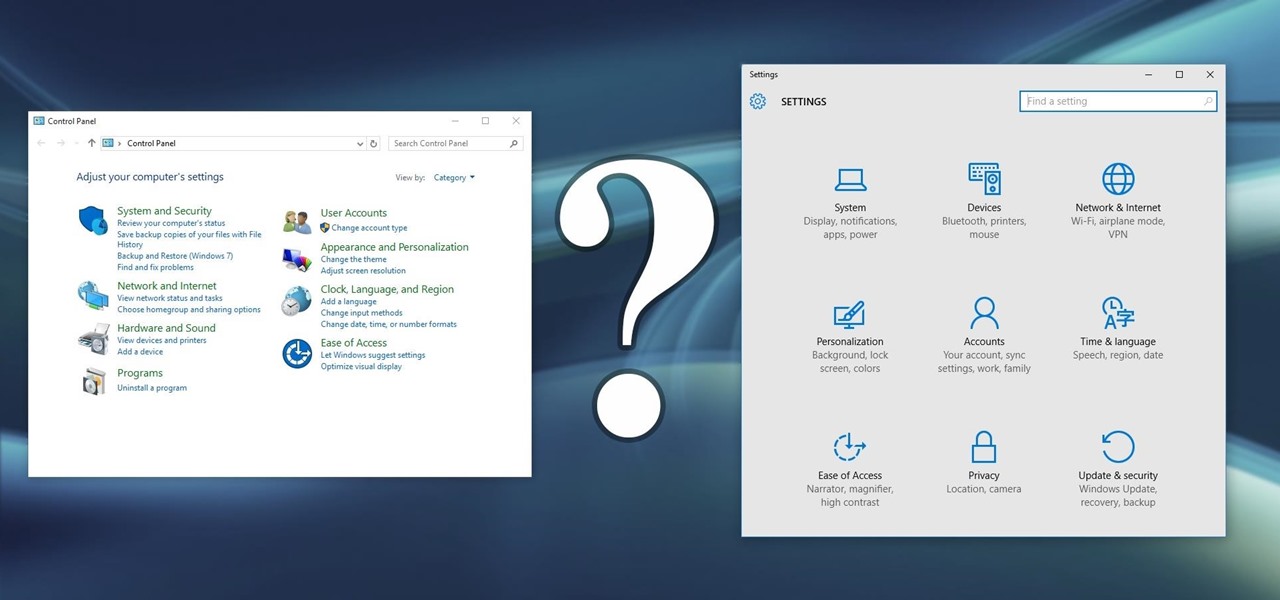
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Welcome back, my hacker novitiates!

The Galaxy S6 Edge comes with a useful feature called Information stream that allows you to view quick tidbits of info with a quick back-and-forth swipe on the edge of your display while the screen is off. Apparently, Samsung left the door open for third-party plugins to use this feature, and now we're starting to see an influx of useful additions.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

Aside from being able to change the wallpaper and add shortcuts, the Galaxy S4's lock screen doesn't offer much in the department of personalization. The lock screen is efficient and practical, but it's also a little bland.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

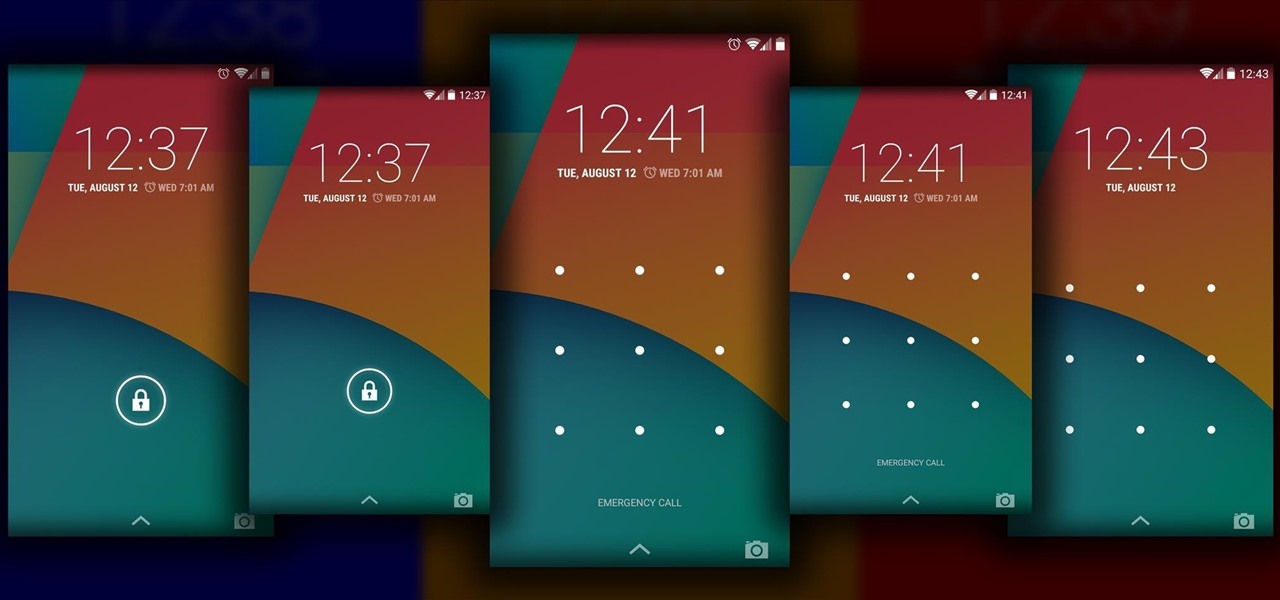
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.